Академический Документы
Профессиональный Документы
Культура Документы
CCNA Security Study Guide
Загружено:
clearmoon247Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
CCNA Security Study Guide
Загружено:
clearmoon247Авторское право:
Доступные форматы
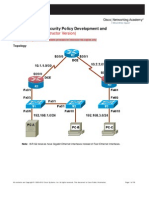
VPN Configuration Implement IKE (Internet Key Exchnage) parameters R1(config)# crypto isakmp enable Must be done on both
routers Establish ISAKMP (Internet Security Association and Key Management Protocol) R1(config)# crypto isakmp policy <policy number> Must be done on both routers Configure policy parameters R1(config)# crypto isakmp policy <policy number> R1(config-isakmp)# authentication pre-share R1(config-isakmp)# encryption aes 256 R1(config-isakmp)# hash sha R1(config-isakmp)# group 5 R1(config-isakmp)# lifetime 3600 R1(config-isakmp)# end Verify IKE policy R1# show crypto isakmp policy Configure pre-shared keys R1(config)# crypto isakmp key <preshared key> address <R3 ip address> R3(config)# crypto isakmp key <preshared key> address <R1 ip address> Configure IPsec transform set R1(config)# crypto ipsec transform-set <tag number> <parameters> Must be done on both routers e.g. R1(config)# crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac R1(cfg-crypto-trans)#exit Change IPsec security association lifetime R1(config)# crypto ipsec security-association lifetime seconds 1800 Define traffic for VPN R1(config)# access-list 101 permit ip <source network> <dest network> Create and apply crypto map R1(config)# crypto map <name> <policy num> <type> R1(config-crypto-map)# match address <acl number> R1(config-crypto-map)# set peer <remote ip address> R1(config-crypto-map)# set pfs <type> R1(config-crypto-map)# set transform-set <tag number> R1(config-crypto-map)# set security-association lifetime seconds <time> R1(config-crypto-map)# exit e.g. R3(config)# crypto map CMAP 10 ipsec-isakmp R3(config-crypto-map)# match address 101 R3(config-crypto-map)# set peer 10.1.1.1 R3(config-crypto-map)# set pfs group5 R3(config-crypto-map)# set transform-set 50 R3(config-crypto-map)# set security-association lifetime seconds 900 R3(config-crypto-map)# exit Apply crypto map to interface R1(config)# interface S0/0/0 R1(config-if)# crypto map <name>
Вам также может понравиться
- Cisco Cheat SheetДокумент1 страницаCisco Cheat Sheetclearmoon247Оценок пока нет
- Ccnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 AmДокумент35 страницCcnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (2)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (890)
- Items GameДокумент1 917 страницItems Gameclearmoon247Оценок пока нет
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- 3 - CCNA TipsДокумент63 страницы3 - CCNA TipsJhon Lipa MazaОценок пока нет
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (399)
- CCNASv1.1 Chp09 Lab-A Sec-Pol Instructor 8.25.37 AMДокумент59 страницCCNASv1.1 Chp09 Lab-A Sec-Pol Instructor 8.25.37 AMclearmoon247Оценок пока нет
- Ccnasv1.1 Chp10 Lab-D Asa-Isr-s2s-VPN Instructor 8.25.37 Am 8.25.57 AmДокумент45 страницCcnasv1.1 Chp10 Lab-D Asa-Isr-s2s-VPN Instructor 8.25.37 Am 8.25.57 Amclearmoon247Оценок пока нет
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- Ccnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 AmДокумент50 страницCcnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (3)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Ccnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 AmДокумент52 страницыCcnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 Amclearmoon247Оценок пока нет
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- CCNASv1.1 Chp08 Lab C RMT Acc VPN InstructorДокумент26 страницCCNASv1.1 Chp08 Lab C RMT Acc VPN Instructorclearmoon247Оценок пока нет
- CCNASv1.1 Chp07 Lab-A Explor-Encrypt InstructorДокумент9 страницCCNASv1.1 Chp07 Lab-A Explor-Encrypt Instructorclearmoon247Оценок пока нет
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- CCNASv1.1 Chp08 Lab B RMT Acc VPN InstructorДокумент33 страницыCCNASv1.1 Chp08 Lab B RMT Acc VPN Instructorclearmoon247Оценок пока нет
- Ccnasv1.1 Chp04 Lab-A Cbac-Zbf InstructorДокумент43 страницыCcnasv1.1 Chp04 Lab-A Cbac-Zbf Instructorclearmoon247Оценок пока нет
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (119)