Академический Документы
Профессиональный Документы
Культура Документы
11.2.4.6 Lab - Accessing Network Devices With SSH
Загружено:
ParthPatelИсходное описание:
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
11.2.4.6 Lab - Accessing Network Devices With SSH
Загружено:
ParthPatelАвторское право:
Доступные форматы
Lab - Accessing Network Devices with SSH
Topology
Addressing Table
Device
Interface
IP Address
Subnet Mask
Default Gateway
R1
G0/1
192.168.1.1
255.255.255.0
N/A
S1
VLAN 1
192.168.1.11
255.255.255.0
192.168.1.1
PC-A
NIC
192.168.1.3
255.255.255.0
192.168.1.1
Objectives
Part 1: Configure Basic Device Settings
Part 2: Configure the Router for SSH Access
Part 3: Configure the Switch for SSH Access
Part 4: SSH from the CLI on the Switch
Background / Scenario
In the past, Telnet was the most common network protocol used to remotely configure network devices.
Telnet does not encrypt the information between the client and server. This allows a network sniffer to
intercept passwords and configuration information.
Secure Shell (SSH) is a network protocol that establishes a secure terminal emulation connection to a router
or other networking device. SSH encrypts all information that passes over the network link and provides
authentication of the remote computer. SSH is rapidly replacing Telnet as the remote login tool of choice for
network professionals. SSH is most often used to log in to a remote device and execute commands; however,
it can also transfer files using the associated Secure FTP (SFTP) or Secure Copy (SCP) protocols.
The network devices that are communicating must be configured to support SSH in order for SSH to function.
In this lab, you will enable the SSH server on a router and then connect to that router using a PC with an SSH
client installed. On a local network, the connection is normally made using Ethernet and IP.
Note: The routers used with CCNA hands-on labs are Cisco 1941 Integrated Services Routers (ISRs) with
Cisco IOS Release 15.2(4)M3 (universalk9 image). The switches used are Cisco Catalyst 2960s with Cisco
IOS Release 15.0(2) (lanbasek9 image). Other routers, switches, and Cisco IOS versions can be used.
Depending on the model and Cisco IOS version, the commands available and the output produced might vary
from what is shown in the labs. Refer to the Router Interface Summary Table at the end of this lab for the
correct interface identifiers.
Note: Make sure that the routers and switches have been erased and have no startup configurations. If you
are unsure, contact your instructor.
2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 1 of 6
Lab - Accessing Network Devices with SSH
Required Resources
1 Router (Cisco 1941 with Cisco IOS Release 15.2(4)M3 universal image or comparable)
1 Switch (Cisco 2960 with Cisco IOS Release 15.0(2) lanbasek9 image or comparable)
1 PC (Windows 7 or 8 with terminal emulation program, such as Tera Term, and Wireshark installed)
Console cables to configure the Cisco IOS devices via the console ports
Ethernet cables as shown in the topology
Part 1: Configure Basic Device Settings
In Part 1, you will set up the network topology and configure basic settings, such as the interface IP
addresses, device access, and passwords on the router.
Step 1: Cable the network as shown in the topology.
Step 2: Initialize and reload the router and switch.
Step 3: Configure the router.
a. Console into the router and enable privileged EXEC mode.
b. Enter configuration mode.
c.
Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as
though they were host names.
d. Assign class as the privileged EXEC encrypted password.
e. Assign cisco as the console password and enable login.
f.
Assign cisco as the VTY password and enable login.
g. Encrypt the plaintext passwords.
h. Create a banner that will warn anyone accessing the device that unauthorized access is prohibited.
i.
Configure and activate the G0/1 interface on the router using the information contained in the Addressing
Table.
j.
Save the running configuration to the startup configuration file.
Step 4: Configure PC-A.
a. Configure PC-A with an IP address and subnet mask.
b. Configure a default gateway for PC-A.
Step 5: Verify network connectivity.
Ping R1 from PC-A. If the ping fails, troubleshoot the connection.
Part 2: Configure the Router for SSH Access
Using Telnet to connect to a network device is a security risk because all information is transmitted in a clear
text format. SSH encrypts the session data and provides device authentication, which is why SSH is
recommended for remote connections. In Part 2, you will configure the router to accept SSH connections over
the VTY lines.
2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 2 of 6
Lab - Accessing Network Devices with SSH
Step 1: Configure device authentication.
The device name and domain are used as part of the crypto key when it is generated. Therefore, these
names must be entered prior to issuing the crypto key command.
a. Configure device name.
Router(config)# hostname R1
b. Configure the domain for the device.
R1(config)# ip domain-name ccna-lab.com
Step 2: Configure the encryption key method.
R1(config)# crypto key generate rsa modulus 1024
The name for the keys will be: R1.ccna-lab.com
% The key modulus size is 1024 bits
% Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 1 seconds)
R1(config)#
*Jan 28 21:09:29.867: %SSH-5-ENABLED: SSH 1.99 has been enabled
Step 3: Configure a local database username.
R1(config)# username admin privilege 15 secret adminpass
Note: A privilege level of 15 gives the user administrator rights.
Step 4: Enable SSH on the VTY lines.
a. Enable Telnet and SSH on the inbound VTY lines using the transport input command.
R1(config)# line vty 0 4
R1(config-line)# transport input telnet ssh
b. Change the login method to use the local database for user verification.
R1(config-line)# login local
R1(config-line)# end
R1#
Step 5: Save the running configuration to the startup configuration file.
R1# copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
R1#
Step 6: Establish an SSH connection to the router.
a. Start Tera Term from PC-A.
b. Establish an SSH session to R1. Use the username admin and password adminpass. You should be
able to establish an SSH session with R1.
2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 3 of 6
Lab - Accessing Network Devices with SSH
Part 3: Configure the Switch for SSH Access
In Part 3, you will configure the switch in the topology to accept SSH connections. After the switch has been
configured, establish an SSH session using Tera Term.
Step 1: Configure the basic settings on the switch.
a. Console into the switch and enable privileged EXEC mode.
b. Enter configuration mode.
c.
Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as
though they were host names.
d. Assign class as the privileged EXEC encrypted password.
e. Assign cisco as the console password and enable login.
f.
Assign cisco as the VTY password and enable login.
g. Encrypt the plain text passwords.
h. Create a banner that will warn anyone accessing the device that unauthorized access is prohibited.
i.
Configure and activate the VLAN 1 interface on the switch according to the Addressing Table.
j.
Save the running configuration to the startup configuration file.
Step 2: Configure the switch for SSH connectivity.
Use the same commands that you used to configure SSH on the router in Part 2 to configure SSH for the
switch.
a. Configure the device name as listed in the Addressing Table.
b. Configure the domain for the device.
S1(config)# ip domain-name ccna-lab.com
c.
Configure the encryption key method.
S1(config)# crypto key generate rsa modulus 1024
d. Configure a local database username.
S1(config)# username admin privilege 15 secret adminpass
e. Enable Telnet and SSH on the VTY lines.
S1(config)# line vty 0 15
S1(config-line)# transport input telnet ssh
f.
Change the login method to use the local database for user verification.
S1(config-line)# login local
S1(config-line)# end
Step 3: Establish an SSH connection to the switch.
Start Tera Term from PC-A, and then SSH to the SVI interface on S1.
Are you able to establish an SSH session with the switch?
2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 4 of 6
Lab - Accessing Network Devices with SSH
Part 4: SSH From the CLI on the Switch
The SSH client is built into the Cisco IOS and can be run from the CLI. In Part 4, you will SSH to the router
from the CLI on the switch.
Step 1: View the parameters available for the Cisco IOS SSH client.
Use the question mark (?) to display the parameter options available with the ssh command.
S1# ssh
-c
-l
-m
-o
-p
-v
-vrf
WORD
?
Select encryption algorithm
Log in using this user name
Select HMAC algorithm
Specify options
Connect to this port
Specify SSH Protocol Version
Specify vrf name
IP address or hostname of a remote system
Step 2: SSH to R1 from S1.
a. You must use the l admin option when you SSH to R1. This allows you to log in as user admin. When
prompted, enter adminpass for the password.
S1# ssh -l admin 192.168.1.1
Password:
***********************************************
Warning: Unauthorized Access is Prohibited!
***********************************************
R1#
b. You can return to S1 without closing the SSH session to R1 by pressing Ctrl+Shift+6. Release the
Ctrl+Shift+6 keys and press x. The switch privileged EXEC prompt displays.
R1#
S1#
c.
To return to the SSH session on R1, press Enter on a blank CLI line. You may need to press Enter a
second time to see the router CLI prompt.
S1#
[Resuming connection 1 to 192.168.1.1 ... ]
R1#
d. To end the SSH session on R1, type exit at the router prompt.
R1# exit
[Connection to 192.168.1.1 closed by foreign host]
S1#
2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 5 of 6
Lab - Accessing Network Devices with SSH
What versions of SSH are supported from the CLI?
Reflection
How would you provide multiple users, each with their own username, access to a network device?
Router Interface Summary Table
Router Interface Summary
Router Model
Ethernet Interface #1
Ethernet Interface #2
Serial Interface #1
Serial Interface #2
1800
Fast Ethernet 0/0
(F0/0)
Fast Ethernet 0/1
(F0/1)
Serial 0/0/0 (S0/0/0)
Serial 0/0/1 (S0/0/1)
1900
Gigabit Ethernet 0/0
(G0/0)
Gigabit Ethernet 0/1
(G0/1)
Serial 0/0/0 (S0/0/0)
Serial 0/0/1 (S0/0/1)
2801
Fast Ethernet 0/0
(F0/0)
Fast Ethernet 0/1
(F0/1)
Serial 0/1/0 (S0/1/0)
Serial 0/1/1 (S0/1/1)
2811
Fast Ethernet 0/0
(F0/0)
Fast Ethernet 0/1
(F0/1)
Serial 0/0/0 (S0/0/0)
Serial 0/0/1 (S0/0/1)
2900
Gigabit Ethernet 0/0
(G0/0)
Gigabit Ethernet 0/1
(G0/1)
Serial 0/0/0 (S0/0/0)
Serial 0/0/1 (S0/0/1)
Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many
interfaces the router has. There is no way to effectively list all the combinations of configurations for each router
class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device.
The table does not include any other type of interface, even though a specific router may contain one. An
example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be
used in Cisco IOS commands to represent the interface.
2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 6 of 6
Вам также может понравиться
- 11.2.4.6 Lab - Accessing Network Devices With SSH - ILMДокумент11 страниц11.2.4.6 Lab - Accessing Network Devices With SSH - ILMKevin KimОценок пока нет
- Configure Network Devices With SSHДокумент5 страницConfigure Network Devices With SSHMisael Alarcon VillaОценок пока нет
- Lab - Configure Network Devices With SSH: TopologyДокумент10 страницLab - Configure Network Devices With SSH: TopologyBárbaraОценок пока нет
- 16.4.7 Lab - Configure Network Devices With SSHДокумент6 страниц16.4.7 Lab - Configure Network Devices With SSHFernando AlburquerqueОценок пока нет
- 16.4.7 Lab - Configure Network Devices With SSH - ILMДокумент11 страниц16.4.7 Lab - Configure Network Devices With SSH - ILMMariano Pereyra100% (1)
- 16.4.7 Lab - Configure Network Devices With SSHДокумент6 страниц16.4.7 Lab - Configure Network Devices With SSHCRISTIAN DAVID VIASUS VEGAОценок пока нет
- 11.2.4.5 Lab - Accessing Network Devices With SSHДокумент11 страниц11.2.4.5 Lab - Accessing Network Devices With SSHDragan Filipovic50% (2)
- 11.2.4.6 Lab - Securing Network DevicesДокумент8 страниц11.2.4.6 Lab - Securing Network DevicesHarrison Hayes0% (2)
- 16.5.2 Lab - Secure Network DevicesДокумент5 страниц16.5.2 Lab - Secure Network DevicesFernando AlburquerqueОценок пока нет
- 6.3.1.1 Lab - Securing Layer 2 Switches PDFДокумент23 страницы6.3.1.1 Lab - Securing Layer 2 Switches PDFnganga0% (2)
- 1.1.4.6 CiscoДокумент11 страниц1.1.4.6 CiscoZeratul322100% (2)
- 4.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIДокумент10 страниц4.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIAhmadHijaziОценок пока нет
- 6.3.1.1 Lab - Securing Layer 2 SwitchesДокумент23 страницы6.3.1.1 Lab - Securing Layer 2 Switchesandy last100% (1)
- 6.5.1.1 Lab - Securing Layer 2 SwitchesДокумент29 страниц6.5.1.1 Lab - Securing Layer 2 Switchesxmaryta0% (2)
- Activity Sheet 2 - Securing SwitchesДокумент28 страницActivity Sheet 2 - Securing SwitchesgfdОценок пока нет
- 6.3.1.1 Lab - Securing Layer 2 SwitchesДокумент22 страницы6.3.1.1 Lab - Securing Layer 2 SwitchesJson CañedaОценок пока нет
- 11.2.4.6 Lab - Securing Network DevicesДокумент8 страниц11.2.4.6 Lab - Securing Network DevicesRichardWhitleyОценок пока нет
- Lab - Configuring Switch Security Features: TopologyДокумент9 страницLab - Configuring Switch Security Features: TopologybobОценок пока нет
- Lab 9 - RSS100 - Securing Layer 2 SwitchesДокумент38 страницLab 9 - RSS100 - Securing Layer 2 SwitchessecuopОценок пока нет
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationДокумент8 страниц11.3.4.6 Lab - Using The CLI To Gather Network Device InformationSuen Clarke0% (1)
- 2.2.4.11 Lab - Configuring Switch Security Features - ScribdДокумент9 страниц2.2.4.11 Lab - Configuring Switch Security Features - ScribdstevehrccОценок пока нет
- ITNB02 11.2.4.6 Securing Network DevicesДокумент8 страницITNB02 11.2.4.6 Securing Network DevicesShayneNakagawaОценок пока нет
- CCNA Security: Chapter Two Securing Network DevicesДокумент16 страницCCNA Security: Chapter Two Securing Network DevicesRatnesh KumarОценок пока нет
- 11.2.4.6 Lab - Securing Network DevicesДокумент8 страниц11.2.4.6 Lab - Securing Network DevicesasdfjklОценок пока нет
- 11.2.4.8 Lab - Securing Network DevicesДокумент8 страниц11.2.4.8 Lab - Securing Network DevicesParthPatel60% (5)
- Lab 3 WorksheetДокумент11 страницLab 3 Worksheetpzydf6wjxvОценок пока нет
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationДокумент11 страниц11.3.4.6 Lab - Using The CLI To Gather Network Device InformationRazvan Buicliu0% (4)
- 2.2.4.11 Lab - Configuring Switch Security Features - ILMДокумент15 страниц2.2.4.11 Lab - Configuring Switch Security Features - ILMJose Maria Rendon Rodriguez100% (1)
- 1-1-4-6-Lab-Configuring-Basic-Router-Settings-With-Ios-Cli - PDF EditedДокумент10 страниц1-1-4-6-Lab-Configuring-Basic-Router-Settings-With-Ios-Cli - PDF EditedYeab SraОценок пока нет
- Chapter 2 - CCNA Sec - NDLДокумент95 страницChapter 2 - CCNA Sec - NDLTung Mai Van100% (1)
- 1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIДокумент15 страниц1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIJuan S. MorejónОценок пока нет
- 10.6.11 Lab - Use Tera Term To Manage Router Configuration Files - ILMДокумент11 страниц10.6.11 Lab - Use Tera Term To Manage Router Configuration Files - ILMJoel DolotОценок пока нет
- 11.3.4.6 Lab - Using The CLI To Gather Network DeviДокумент11 страниц11.3.4.6 Lab - Using The CLI To Gather Network DeviRichardWhitley20% (5)
- Cisco CCNP Route - Configure and Verify Device Access ControlДокумент3 страницыCisco CCNP Route - Configure and Verify Device Access ControlŞerif ŞahinОценок пока нет
- Lab 8.3.1.2 Configure Basic AP Security Through IOS CLI: ObjectiveДокумент10 страницLab 8.3.1.2 Configure Basic AP Security Through IOS CLI: Objective2613078Оценок пока нет
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationДокумент8 страниц11.3.4.6 Lab - Using The CLI To Gather Network Device InformationSachinОценок пока нет
- 5.2.2.9 Lab - Configuring Switch Security FeaturesДокумент10 страниц5.2.2.9 Lab - Configuring Switch Security FeaturesShadman SifatОценок пока нет
- 5 2 2 9 Lab Configuring Switch Security Features ILMДокумент16 страниц5 2 2 9 Lab Configuring Switch Security Features ILMJavier FlorianОценок пока нет
- Configure SSHДокумент2 страницыConfigure SSHMaría Raquel Landa CavazosОценок пока нет
- Configure Basic Router Settings LabДокумент11 страницConfigure Basic Router Settings Labumang patnaikОценок пока нет
- 9.5.1.2 Packet Tracer - Putting It All TogetherДокумент2 страницы9.5.1.2 Packet Tracer - Putting It All Togetherdaniel50% (2)
- Theory:: Experiment No: 07Документ4 страницыTheory:: Experiment No: 07Md. Humayun KobirОценок пока нет
- B3 - 322070 - Sai Kamble - Assig - 3Документ11 страницB3 - 322070 - Sai Kamble - Assig - 3sai.22220063Оценок пока нет
- 2.3.3.5 Lab - Configuring A Switch Management Address NewportДокумент4 страницы2.3.3.5 Lab - Configuring A Switch Management Address Newportgerardo1028Оценок пока нет
- Lab - Configuring and Verifying VTY RestrictionsДокумент6 страницLab - Configuring and Verifying VTY Restrictionsdaniel ramirezОценок пока нет
- Theory:: Experiment No: 07Документ4 страницыTheory:: Experiment No: 07Md. Humayun KobirОценок пока нет
- 16.4.6-Packet-Tracer - Configure-Secure-Passwords-And-SshДокумент4 страницы16.4.6-Packet-Tracer - Configure-Secure-Passwords-And-Sshjudianto situmorangОценок пока нет
- 2.2.1.4 Packet Tracer - Configuring SSH Instruction - IG PDFДокумент2 страницы2.2.1.4 Packet Tracer - Configuring SSH Instruction - IG PDFDidiОценок пока нет
- Con Gure SSH On Routers and Switches: Updated: June 3, 2022 Document ID: 4145Документ13 страницCon Gure SSH On Routers and Switches: Updated: June 3, 2022 Document ID: 4145ehsan.ghaОценок пока нет
- 7.2.3.4 Lab - Configuring and Verifying VTY Restrictions WB PDFДокумент7 страниц7.2.3.4 Lab - Configuring and Verifying VTY Restrictions WB PDFAriana Olea CortezОценок пока нет
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationДокумент11 страниц11.3.4.6 Lab - Using The CLI To Gather Network Device InformationRuy Pequeno CidОценок пока нет
- Ccnasecurity Sba FinalДокумент12 страницCcnasecurity Sba FinalBilly Zomg100% (2)
- Cisco 16.4.7 Lab - Configure Network Devices With SSH (Answers)Документ8 страницCisco 16.4.7 Lab - Configure Network Devices With SSH (Answers)Marion SabandalОценок пока нет
- Configure Secure Passwords and SSH on Router and SwitchДокумент3 страницыConfigure Secure Passwords and SSH on Router and SwitchMackus Da SilvaОценок пока нет
- 4 Cpe B VillanuevaMiles LabAct3Документ9 страниц4 Cpe B VillanuevaMiles LabAct3laongtingcoОценок пока нет
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОт EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОценок пока нет
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОт EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОценок пока нет
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityОт EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityОценок пока нет
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3От EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Оценок пока нет
- Lab 5 - Configuring A Switch Managment AddressДокумент10 страницLab 5 - Configuring A Switch Managment AddressParthPatelОценок пока нет
- 11.3.2.2 Packet Tracer - Test Connectivity With TracerouteДокумент3 страницы11.3.2.2 Packet Tracer - Test Connectivity With TracerouteParthPatelОценок пока нет
- Lab 7 - Viewing Wireless and Wired NIC InformationДокумент11 страницLab 7 - Viewing Wireless and Wired NIC InformationParthPatelОценок пока нет
- Appendix Packet Tracer - Configuring An Integrated RouterДокумент3 страницыAppendix Packet Tracer - Configuring An Integrated RouterParthPatelОценок пока нет
- 11.3.3.3 Packet Tracer - Using Show CommandsДокумент2 страницы11.3.3.3 Packet Tracer - Using Show CommandsParthPatel0% (1)
- 11.2.4.7 Lab - Examining Telnet and SSH in WiresharkДокумент9 страниц11.2.4.7 Lab - Examining Telnet and SSH in WiresharkParthPatel100% (2)
- 11.4.1.3 Packet Tracer - Troubleshooting ChallengeДокумент3 страницы11.4.1.3 Packet Tracer - Troubleshooting ChallengeParthPatel0% (1)
- 11.2.5.7 Packet Tracer - Backing Up Configuration FilesДокумент2 страницы11.2.5.7 Packet Tracer - Backing Up Configuration FilesParthPatel33% (3)
- Appendix Packet Tracer - Subnetting Scenario 2Документ4 страницыAppendix Packet Tracer - Subnetting Scenario 2ParthPatelОценок пока нет
- 11.2.4.5 Packet Tracer - Configuring Secure Passwords and SSHДокумент2 страницы11.2.4.5 Packet Tracer - Configuring Secure Passwords and SSHParthPatelОценок пока нет
- 11.4.1.2 Packet Tracer - Skills Integration ChallengeДокумент4 страницы11.4.1.2 Packet Tracer - Skills Integration ChallengeParthPatel0% (1)
- 11.2.4.8 Lab - Securing Network DevicesДокумент8 страниц11.2.4.8 Lab - Securing Network DevicesParthPatel60% (5)
- 9.3.1.2 Packet Tracer Simulation - Exploration of TCP and UDP CommunicationДокумент6 страниц9.3.1.2 Packet Tracer Simulation - Exploration of TCP and UDP CommunicationParthPatel0% (1)
- 10.4.1.2 Packet Tracer Multiuser - Tutorial InstructionsДокумент3 страницы10.4.1.2 Packet Tracer Multiuser - Tutorial InstructionsKamijou SekaiОценок пока нет
- 3.3.3.3 Packet Tracer - Explore A Network InstructionsДокумент5 страниц3.3.3.3 Packet Tracer - Explore A Network InstructionsWendhz ÜüОценок пока нет
- 10.2.1.7 Packet Tracer - Web and EmailДокумент5 страниц10.2.1.7 Packet Tracer - Web and EmailParthPatelОценок пока нет
- 10.3.1.4 Packet Tracer Multiuser - Implement ServicesДокумент4 страницы10.3.1.4 Packet Tracer Multiuser - Implement ServicesParthPatel0% (1)
- 10.2.2.7 Packet Tracer - DNS and DHCPДокумент4 страницы10.2.2.7 Packet Tracer - DNS and DHCPParthPatelОценок пока нет
- Configure and Use FTP ServersДокумент4 страницыConfigure and Use FTP ServersParthPatelОценок пока нет
- 10.2.2.9 Lab - Observing DNS ResolutionДокумент5 страниц10.2.2.9 Lab - Observing DNS ResolutionasdfjklОценок пока нет
- 8.4.1.2 Packet Tracer - Skills Integration ChallengeДокумент2 страницы8.4.1.2 Packet Tracer - Skills Integration ChallengeParthPatel0% (1)
- 8.3.1.4 Packet Tracer - Implementing A Subnetted IPv6 Addressing SchemeДокумент3 страницы8.3.1.4 Packet Tracer - Implementing A Subnetted IPv6 Addressing SchemeParthPatel0% (1)
- 8.1.4.7 Packet Tracer - Subnetting Scenario 1Документ5 страниц8.1.4.7 Packet Tracer - Subnetting Scenario 1ParthPatel33% (6)
- 8.1.4.8 Lab - Designing and Implementing A Subnetted IPv4 Addressing SchemeДокумент12 страниц8.1.4.8 Lab - Designing and Implementing A Subnetted IPv4 Addressing SchemeParthPatel90% (31)
- 9.2.1.5 Packet Tracer - Designing and Implementing A VLSM Addressing Scheme InstructДокумент4 страницы9.2.1.5 Packet Tracer - Designing and Implementing A VLSM Addressing Scheme InstructGanti nama100% (1)
- 7.4.1.2 Packet Tracer - Skills Integration ChallengeДокумент2 страницы7.4.1.2 Packet Tracer - Skills Integration ChallengeParthPatel100% (1)
- 7.3.2.9 Packet Tracer - Troubleshooting IPv4 and IPv6 AddressingДокумент5 страниц7.3.2.9 Packet Tracer - Troubleshooting IPv4 and IPv6 AddressingParthPatel0% (3)
- 8.1.4.6 Lab - Calculating IPv4 SubnetsДокумент7 страниц8.1.4.6 Lab - Calculating IPv4 SubnetscgruОценок пока нет
- 7.3.2.8 Lab - Mapping The InternetДокумент8 страниц7.3.2.8 Lab - Mapping The InternetParthPatel0% (5)
- LG Wa Dpe Cloud Paas Aws l1Документ1 страницаLG Wa Dpe Cloud Paas Aws l1Manish KumarОценок пока нет
- 73 - VLAN Service ManagementДокумент19 страниц73 - VLAN Service ManagementAlexanderОценок пока нет
- Configuracion Swi Del n1524p DatacenterДокумент18 страницConfiguracion Swi Del n1524p DatacentertatianaОценок пока нет
- TCP IP Lan ThermometerДокумент12 страницTCP IP Lan ThermometerBranislav BusovskyОценок пока нет
- Cisco Expressway at The Collaboration EdgeДокумент79 страницCisco Expressway at The Collaboration EdgexkerberosxОценок пока нет
- MICROWAVE NETWORKS DCN DESIGN AND CAPACITY DIMENSIONINGДокумент12 страницMICROWAVE NETWORKS DCN DESIGN AND CAPACITY DIMENSIONINGmmhg82Оценок пока нет
- Qos Extensions To Mobile Ad Hoc Routing Supporting Real-Time ApplicationsДокумент8 страницQos Extensions To Mobile Ad Hoc Routing Supporting Real-Time ApplicationsshivprakashtОценок пока нет
- Informe 5 TelematicaДокумент14 страницInforme 5 TelematicaJose Eduardo BriceñoОценок пока нет
- Voice Over IpДокумент21 страницаVoice Over IpBab RabОценок пока нет
- Cisco Sdwan Design GuideДокумент102 страницыCisco Sdwan Design GuideSheik ShareefОценок пока нет
- Huawei OLT Configuration Step by Step Guide 2023Документ7 страницHuawei OLT Configuration Step by Step Guide 2023Aitsam YounasОценок пока нет
- CCNA Security: Chapter Two Securing Network DevicesДокумент16 страницCCNA Security: Chapter Two Securing Network DevicesRatnesh KumarОценок пока нет
- Nmap The Art of Port Scanning PDFДокумент6 страницNmap The Art of Port Scanning PDFJapari JaporaОценок пока нет
- Configuracion Oscam - ConfДокумент19 страницConfiguracion Oscam - ConfJuanMi AndradaОценок пока нет
- DRG Configuration - Swiping and FaxДокумент10 страницDRG Configuration - Swiping and Faxapi-3743401100% (3)
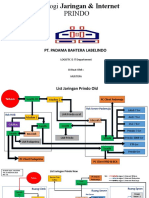
- Pt. Padama Bahtera Labelindo: LOGISTIC & IT DepartementДокумент19 страницPt. Padama Bahtera Labelindo: LOGISTIC & IT DepartementFendi AdriantoОценок пока нет
- Cisco - Pre .300-730.by .VCEplus.60q-DEMOДокумент33 страницыCisco - Pre .300-730.by .VCEplus.60q-DEMOPhúc HồngОценок пока нет
- Prosoft Wireless GatewayДокумент12 страницProsoft Wireless GatewayDave MartinОценок пока нет
- Network Administration Laboratory ManualДокумент322 страницыNetwork Administration Laboratory ManualedrisОценок пока нет
- VSICM6 M05 NetworkingДокумент50 страницVSICM6 M05 Networkinggokhan gokhanОценок пока нет
- TEMS Investigation Video Streaming Client Technical DescriptionДокумент6 страницTEMS Investigation Video Streaming Client Technical Descriptioninfy zazОценок пока нет
- Umts Call FlowsДокумент277 страницUmts Call FlowsNitin Gupta100% (1)
- Anjuman Polytechnic: Micro-Project ReportДокумент5 страницAnjuman Polytechnic: Micro-Project ReportDANISHSHEIKHОценок пока нет
- GETVPNДокумент46 страницGETVPNAndres Ricardo Guillen BedregalОценок пока нет
- Dax Managed FEДокумент8 страницDax Managed FEpktprabhuОценок пока нет
- Alcatel-Lucent 1642 Edge Multiplexer ManualДокумент3 страницыAlcatel-Lucent 1642 Edge Multiplexer ManualAugtron AndersОценок пока нет
- 8.1.2.5 Packet Tracer - Configuring Syslog and NTP InstructionsДокумент3 страницы8.1.2.5 Packet Tracer - Configuring Syslog and NTP InstructionsMuhammadОценок пока нет
- WCDMA Interview Questions and AnswersДокумент14 страницWCDMA Interview Questions and Answersadnangulzar100% (1)
- FortiDDoS 4.5.0 Study Guide-OnlineДокумент211 страницFortiDDoS 4.5.0 Study Guide-OnlineDimitris GiannoulakisОценок пока нет
- CISCO Vs Huawei CommandДокумент2 страницыCISCO Vs Huawei CommandNicolau Nechita Iulian100% (3)