Академический Документы
Профессиональный Документы
Культура Документы
Heap Spray
Загружено:
Matthew Leung-Harrison0 оценок0% нашли этот документ полезным (0 голосов)
6 просмотров1 страницаHeap Sprays in Security
Авторское право
© © All Rights Reserved
Доступные форматы
DOCX, PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документHeap Sprays in Security
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате DOCX, PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
6 просмотров1 страницаHeap Spray
Загружено:
Matthew Leung-HarrisonHeap Sprays in Security
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате DOCX, PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 1
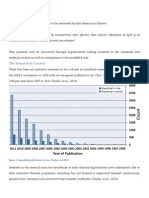
Zero day internet explorer flaw attempts to bypass ASLR (Address Space Layout
Randomisation).
ASLR protects from buffer overflow attacks by randomising the location where system
executables are loaded into memory.
Non-ASLR modules can be loaded when the browser loads a page with ms-help:// in the
URL and is not compiled with ASLR.
This is a known ASLR bypass for Internet Explorer 8/9 on Windows 7.
Heap spray is where you spray a large part of the heap memory with shell code and nops.
That way, when you jump to any part of the heap, most of the heap has been sprayed with nops
and your shell code, so there is a decent probability that youre jumping to a nop followed by
your shell code and then you can execute your shell code.
The whole point of having nops is that you often dont have precise control where your exploit
code can overtake the execution.
As long as your exploit lands somewhere inside this nop sled, then it will just slide straight
into your shell code.
The exploit code utilises a use-after-free vulnerability, which is a type of memory corruption
flaw that accesses memory after it has been freed.
At this point, control is passed over to the heap and then the shell code can be run.
The shell code can drop a malicious payload onto the computer.
The way this exploit gets to the user in the first place is the attack has to be socially engineered
onto the user.
This can be via an email attachment, install file, etc.
Вам также может понравиться
- Composite: Inside The Class, We HaveДокумент2 страницыComposite: Inside The Class, We HaveMatthew Leung-HarrisonОценок пока нет
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- Bad Design Because Hotel Is Iterating Over Rooms Instead Create A Public Method Inside The Rooms Class Called FindroomofsizeДокумент2 страницыBad Design Because Hotel Is Iterating Over Rooms Instead Create A Public Method Inside The Rooms Class Called FindroomofsizeMatthew Leung-HarrisonОценок пока нет
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5795)
- Thesis B InstructionsS12015Документ1 страницаThesis B InstructionsS12015Matthew Leung-HarrisonОценок пока нет
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Literature Review: Research QuestionДокумент14 страницLiterature Review: Research QuestionMatthew Leung-HarrisonОценок пока нет
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- Terran GuideДокумент3 страницыTerran GuideMatthew Leung-HarrisonОценок пока нет
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (345)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (400)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1091)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (121)