Академический Документы
Профессиональный Документы
Культура Документы
ADP008 - Authentication Schemes For Session Passwords
Загружено:
Ajay TaradeОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
ADP008 - Authentication Schemes For Session Passwords
Загружено:
Ajay TaradeАвторское право:
Доступные форматы
Authentication Schemes for Session Passwords using Color and Images
ABSTRACT
Textual passwords are the most common method used for authentication. But textual passwords are vulnerable to eves dropping, dictionary attacks, social engineering and shoulder surfing. Graphical passwords are introduced as alternative techniques to textual passwords. Most of the graphical schemes are vulnerable to shoulder surfing. To address this problem, text can be combined with images or colors to generate session passwords for authentication. Session passwords can be used only once and every time a new password is generated. In this paper, two techniques are proposed to generate session passwords using text and colors which are resistant to shoulder surfing. These methods are suitable for Personal Digital Assistants.
EXISTING SYSTEM The most common method used for authentication is textual password. The vulnerabilities of this method like eves dropping, dictionary attack, social engineering and shoulder surfing are well known. Random and lengthy passwords can make the system secure. Studies have shown that users tend to pick short passwords or passwords that are easy to remember. These passwords can be easily guessed or cracked. The alternative techniques are graphical passwords and biometrics. But these two techniques have their own disadvantages. Biometrics, such as finger prints, iris scan or facial recognition have been introduced but not yet widely adopted. Disadvantages Very difficult to remembering the passwords. The major drawback of this approach is that such systems can be expensive and the identification process can be slow.
PROPOSED SYSTEM Personal Digital Assistants are being used by the people to store their personal and confidential information like passwords and PIN numbers. Authentication should be provided for the usage of these devices. Two new authentication schemes are proposed for PDAs. These schemes authenticate the user by session passwords. Session passwords are passwords that are used only once. Once the session is terminated, the session password is no longer useful. For every login process, users input different passwords. The session passwords provide better security against dictionary and brute force attacks as password changes for every session. The proposed authentication schemes use text and colors for generating session passwords. Advantages Having High tolerance levels Security is high
SYSTEM MODELS
HARDWARE REQUIREMENT CPU type Clock speed Ram size Hard disk capacity Monitor type Keyboard type : Intel Pentium 4
: 3.0 GHz : 512 MB : 40 GB : : 15 Inch color monitor internet keyboard
SOFTWARE REQUIREMENT Operating System: Android Language Back End Documentation : JAVA : SQLite : Ms-Office
MODULES Registration Phase User identify the images during Registration phase Login Phase Interface grid Intersection letter for the pair Rating the colors Login Interface Verification Phase Module Description Registration Phase In this Module, user enters his password. Minimum length of the password is 8 and it can be called as secret pass. The secret pass should contain even number of characters. User identify the images during Registration phase The user selects a certain number of images from a set of random pictures during registration the user has to identify the pre selected images for authentication from a set of images. Login Phase In this Module, the user has to enter the password based on the interface displayed on the screen. The user chooses four images of human faces as their password and the users have to select their pass image from eight other decoy images.
Interface grid Session passwords are generated based on this secret pass. The user enters his username an interface consisting of a grid is displayed. The grid is of size 6 x 6 and it consists of alphabets and numbers. These are randomly placed on the grid and the interface changes every time. Intersection letter for the pair User has to enter the password depending upon the secret pass. User has to consider his secret pass in terms of pairs. The session password consists of alphabets and digits. The first letter in the pair is used to select the row and the second letter is used to select the column. The intersection letter is part of the session password. This is repeated for all pairs of secret pass. Rating the colors The User should rate colors from 1 to 8. Same rating can be given to different colors. The user enters his username an interface is displayed based on the colors selected by the user. Login Interface The login interface having the color grid and number grid of 8 x 8 having numbers 1 to 8 randomly placed in the grid. Depending on the ratings given to colors, we get the session password. Verification Phase The system verifies the password entered by comparing with content of the password generated during registration. The authentication techniques should be verified extensively for usability and effectiveness. Then it send verification key on mobile of register user
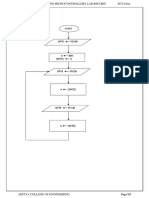
Flow Diagram Registration Phase User identify the images during Registration phase
Login Phase
Interface Grid
Intersection letter for the pair
Rating the colors
Login Interface
Verification phase
CONCLUSION The two authentication techniques based on text and colors are proposed for PDAs. These techniques generate session passwords and are resistant to dictionary attack, brute force attack and shoulder-surfing. Both the techniques use grid for session passwords generation. Pair based technique requires no special type of registration, during login time based on the grid displayed a session password is generated. For hybrid textual scheme, ratings should be given to colors, based on these ratings and the grid displayed during login, session passwords are generated. However these schemes are completely new to the users and the proposed authentication techniques should be verified extensively for usability and effectiveness.
Use case Diagram:
Registration
Image position of the Digit
User System Password Generation
User Login
Sequence Diagram:
User
Login
Image Database
System
1: Select the Image Position 2: Submitted to System 3: Password is generated from the Table
4: Password Send to User
5: Enter Uname and Pwd
6: Checking the password
7: Password to be correct
Collaboration Diagram:
5: Enter Uname and Pwd User
Login
6: Checking the password 1: Select the Image Position 4: Password Send to User 7: Password to be correct 3: Password is generated from the Table
2: Submitted to System Image Database
System
Activity Diagram:
User
Login No Validate
Yes Image Database
System
Class Diagram:
Table number() void onCreate()
Image Database images() number() submit()
Registration username() password() void onCreate()
Вам также может понравиться
- Library Management System VB Project DocumentationДокумент80 страницLibrary Management System VB Project DocumentationLijo Amal Joy79% (135)
- ROBO K20 2Yr Warranty Powerful Vacuum CleanerДокумент1 страницаROBO K20 2Yr Warranty Powerful Vacuum CleanerAjay TaradeОценок пока нет
- 1Документ1 страница1Ajay TaradeОценок пока нет
- Library Management System VB Project DocumentationДокумент80 страницLibrary Management System VB Project DocumentationLijo Amal Joy79% (135)
- 4Документ56 страниц4Ajay TaradeОценок пока нет
- Privasy PerservingДокумент6 страницPrivasy PerservingAjay TaradeОценок пока нет
- Support search-as-you-type queries using SQLДокумент15 страницSupport search-as-you-type queries using SQLAjay TaradeОценок пока нет
- Chen 2016Документ13 страницChen 2016Ajay TaradeОценок пока нет
- FuzzyДокумент7 страницFuzzyAjay TaradeОценок пока нет
- Search Engine DigramДокумент23 страницыSearch Engine DigramAjay TaradeОценок пока нет
- Base 1Документ12 страницBase 1saravanasОценок пока нет
- The Design and Implementation of FeatureДокумент17 страницThe Design and Implementation of FeatureAjay TaradeОценок пока нет
- Base 1Документ12 страницBase 1saravanasОценок пока нет
- Search Engine DigramДокумент23 страницыSearch Engine DigramAjay TaradeОценок пока нет
- Sudo CodeДокумент4 страницыSudo CodeAjay TaradeОценок пока нет
- Student Reporting SystemДокумент7 страницStudent Reporting SystemAjay TaradeОценок пока нет
- A Cloud Computing Solution For Sharing Healthcare InformationddddДокумент2 страницыA Cloud Computing Solution For Sharing Healthcare InformationddddAjay TaradeОценок пока нет
- Project Report On Sales and Inventory Management SystemДокумент87 страницProject Report On Sales and Inventory Management Systemmdevilishangel82% (222)
- DOS AttackДокумент11 страницDOS AttackAjay TaradeОценок пока нет
- A Cloud Computing Solution For Sharing Healthcare InformationddddДокумент2 страницыA Cloud Computing Solution For Sharing Healthcare InformationddddAjay TaradeОценок пока нет
- Feature GradingДокумент6 страницFeature GradingAjay TaradeОценок пока нет
- DissertationДокумент120 страницDissertationAjay TaradeОценок пока нет
- ID-Based Cryptography For Secure Cloud Data1Документ6 страницID-Based Cryptography For Secure Cloud Data1Ajay TaradeОценок пока нет
- Chapter 9. Goods and Services Account: A. Introduction To The Current AccountДокумент22 страницыChapter 9. Goods and Services Account: A. Introduction To The Current AccountAjay TaradeОценок пока нет
- Multi-Biometrics Recognition for Intelligent House ManagementДокумент111 страницMulti-Biometrics Recognition for Intelligent House ManagementRavi SharmaОценок пока нет
- Chapter 9. Goods and Services Account: A. Introduction To The Current AccountДокумент22 страницыChapter 9. Goods and Services Account: A. Introduction To The Current AccountAjay TaradeОценок пока нет
- Continuous and Transparent User Identity Verification For Secure Internet Services.Документ9 страницContinuous and Transparent User Identity Verification For Secure Internet Services.Ajay Tarade0% (1)
- Data Similarity-Aware Computation Infrastructure For The CloudДокумент14 страницData Similarity-Aware Computation Infrastructure For The CloudAjay TaradeОценок пока нет
- Continuous and Transparent User Identity Verification For Secure Internet Services.Документ9 страницContinuous and Transparent User Identity Verification For Secure Internet Services.Ajay Tarade0% (1)
- Data Placement and Duplication For Embedded Multicore Systems With Scratch Pad MemoryДокумент9 страницData Placement and Duplication For Embedded Multicore Systems With Scratch Pad MemoryAjay TaradeОценок пока нет
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (399)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (119)
- PowMr Manuals Solar Inverter Charger 24V 220V 100A POW VM3K IIIДокумент50 страницPowMr Manuals Solar Inverter Charger 24V 220V 100A POW VM3K IIIMarco LondonОценок пока нет
- Land Rover e CarPlay enДокумент10 страницLand Rover e CarPlay enDanieleОценок пока нет
- Chapter 4 Agile - DevelopmentДокумент17 страницChapter 4 Agile - DevelopmentMuhammad Alwi BasyirОценок пока нет
- BJT Transistor Characteristics CE ConfigurationДокумент5 страницBJT Transistor Characteristics CE ConfigurationSavithaGnОценок пока нет
- Release NotesДокумент9 страницRelease Notes김준우Оценок пока нет
- c240m4 LFF Spec SheetДокумент102 страницыc240m4 LFF Spec SheetMahmood RobbinsОценок пока нет
- Virtualization - Dark Web Forensics Using Csi Linux: Deborah K. Wells, Lecturer, CWUДокумент48 страницVirtualization - Dark Web Forensics Using Csi Linux: Deborah K. Wells, Lecturer, CWUpicturesbyprathameshОценок пока нет
- 2 F0 F8 D 01Документ17 страниц2 F0 F8 D 01Leo Van PendieОценок пока нет
- IBM I and Related Software Installing, Upgrading, or Deleting IBM I and Related SoftwareДокумент228 страницIBM I and Related Software Installing, Upgrading, or Deleting IBM I and Related SoftwareDavidVX25Оценок пока нет
- Mf1S70Yyx/V1: 1. General DescriptionДокумент41 страницаMf1S70Yyx/V1: 1. General DescriptionPintér SándorОценок пока нет
- Avolites Titan BIOSДокумент2 страницыAvolites Titan BIOSHenry PalОценок пока нет
- Dot Peen Marking Machine: ApplicationsДокумент4 страницыDot Peen Marking Machine: ApplicationsFernando GalindoОценок пока нет
- HS-100B DatasheetДокумент21 страницаHS-100B DatasheetMonica ShuОценок пока нет
- RS232 To DALI User Guide V8Документ16 страницRS232 To DALI User Guide V8Arun DasariОценок пока нет
- EN Spec TU-S9 (V1.1 1.2)Документ2 страницыEN Spec TU-S9 (V1.1 1.2)jusufjОценок пока нет
- Query 400Документ302 страницыQuery 400visuaОценок пока нет
- FFT DFT Digital Signal ProcessingДокумент176 страницFFT DFT Digital Signal ProcessingSabuj AhmedОценок пока нет
- Opamp TesterДокумент2 страницыOpamp TesterbalubobbyОценок пока нет
- LTE trace-ENM-AMOSДокумент3 страницыLTE trace-ENM-AMOSClaudio Deri100% (3)
- Assignment Section-1 1. What Is DFT?Документ18 страницAssignment Section-1 1. What Is DFT?PAVAN KUMAR TAVADABOINA100% (1)
- DevOps Course Curriculum UpgradedДокумент5 страницDevOps Course Curriculum UpgradedNagaraj JalawadiОценок пока нет
- Software Engineering Chapter 2Документ49 страницSoftware Engineering Chapter 2nitin guptaОценок пока нет
- College of Computer Science Dmmmsu - SlucДокумент46 страницCollege of Computer Science Dmmmsu - SlucArchie Cedric GarciaОценок пока нет
- Potentiometer and LVDTДокумент4 страницыPotentiometer and LVDTAbhishek Kumar JaiswalОценок пока нет
- Pridiom Multi-Zone Indoor and Outdoor Units GuideДокумент29 страницPridiom Multi-Zone Indoor and Outdoor Units Guidevizion2k4100% (1)
- 8051 InterfacingДокумент8 страниц8051 InterfacingDr.R.RAMANОценок пока нет
- An Industrial Vision System For Surface Quality Inspection of Transparent PartsДокумент14 страницAn Industrial Vision System For Surface Quality Inspection of Transparent PartsVinicius GoncalvesОценок пока нет
- What Is Rank Indicaton in LTEДокумент13 страницWhat Is Rank Indicaton in LTEdinzo ccsiОценок пока нет
- Lesson 1 Introduction To NetworkingДокумент14 страницLesson 1 Introduction To NetworkingKevin SambuОценок пока нет
- UM2411 User Manual: Discovery Kit With STM32H747XI MCUДокумент61 страницаUM2411 User Manual: Discovery Kit With STM32H747XI MCUFarouk ElОценок пока нет