Академический Документы
Профессиональный Документы
Культура Документы
Cisco ASA Firewall Configuration
Загружено:
Qazi Tahir HussainИсходное описание:
Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Cisco ASA Firewall Configuration
Загружено:
Qazi Tahir HussainАвторское право:
Доступные форматы
1
CCIE Security Workbook
Section 01: Cisco ASA Firewalls
Section 1: Implement secure networks using Cisco ASA Firewalls
Lab1: Perform basic firewall Initialization Configure firewall in single contexts:
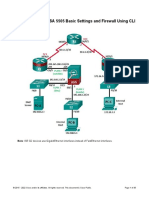
Task 1: Configure firewall with following parameters Hostname ASA1 1. Enable Password Cisco123 2. Domain-name cisco.com 3. Telnet password 123Cisco 4. You may allow any ICMP traffic anywhere in ASA 5. Make sure no device can ping ASA outside interface except R3 IP address 201.1.1.3 6. Configure interface with following parameters Interface Ethernet0/0 Ethernet0/1 Ethernet0/2.40 Ethernet0/2.50 Name Outside Inside DMZ40 DMZ50 Type Physical Physical Logical Logical Security Level 0 100 40 50 IP Address 201.1.1.10/24 10.1.1.10/24 10.40.40.10/24 10.50.50.10/24 VLAN 40 50
Use exact names and numbers as shown in the table
CCIE Security Workbook
Section 01: Cisco ASA Firewalls
Task 2: Configure Routing on ASA Interface Network ID Outside 20.1.1.0/24 Inside 10.1.1.0/24 DMZ40 10.40.40.0/24 DMZ50 10.50.50.0/24
Routing Protocol OSPF RIPv2 RIPV2 OSPF
Area 0 0
1. Run routing protocols on ASA 2. Configure bi-directional redistribution 3. Make sure R2, R3 and R4 can ping R1 Loopback from their Loopbacks Configure Firewall in Multi-context:
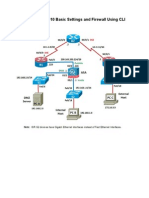
Task 1:Multi-Contexts 1. Convert firewall to multi-mode 2. Use contexts name as C1 and C2, context names are case-sensitive 3. Interface configuration of C1 and C2 is shown in the diagram Admin Context initialization details: Interface Name Type Ethernet0/4 Man Physical
Security Level 100
IP address 1.1.1.1/24
VLAN -
CCIE Security Workbook
Section 01: Cisco ASA Firewalls
Context C1 initialization details: Interface Name Ethernet0/1 Inside Ethernet0/2 DMZ Ethernet0/0.30 Outside Context C2 initialization details: Interface Name Ethernet0/0.40 Inside Ethernet0/0.30 Outside
Type Physical Physical Logical
Security level 100 50 0
IP address 192.168.1.10/24 172.16.2.10/24 201.1.1.10/24
VLAN 30
Type Logical Logical
Security level 100 0
IP address VLAN 192.168.4.10/24 40 201.1.1.20/24 30
Ethernet0/0.30 is shared between contexts Configure Switch to achieve this configuration Use all other parameters as appropriate Task 2: Configure Routing on ASA 1. Dont use default route, use static routes as appropriate in C1 and C2 2. Verify your configuration by running following ping commands from R3 Ping 192.168.2.2 source Loopback 3 Ping 192.168.4.4 source Loopback 3 Ping 10.44.44.4 source Loopback 3 Ping 192.168.1.1 should not pass through (Dont use ACL) 3. Inside interface should only be used to carry management traffic 4. Test PC is placed behind R4, configure Test PC with appropriate default gateway and then access R2 for https management, R4 is pre-configured for https management access use all other parameters as appropriate to accomplish this task. Test your configuration using IE form Test PC.
Вам также может понравиться
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityОт EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityОценок пока нет
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3От EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Оценок пока нет
- Advanced ISE Labs PDFДокумент66 страницAdvanced ISE Labs PDFcoolboyasif100% (1)
- Advanced Identity Service Engine (ISE) Labs GuideДокумент66 страницAdvanced Identity Service Engine (ISE) Labs GuidecoolboyasifОценок пока нет
- Advanced ISE LabsДокумент56 страницAdvanced ISE LabsKannanZenithRiderОценок пока нет
- Khawar Butt CCIE Security v3 0Документ191 страницаKhawar Butt CCIE Security v3 0kamleg100% (1)
- Cisco Configuring An Ipsec Tunnel Cisco Secure Pix Firewall To Checkpoint 4.1 FirewallДокумент19 страницCisco Configuring An Ipsec Tunnel Cisco Secure Pix Firewall To Checkpoint 4.1 Firewallzakaria26Оценок пока нет
- Ccnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 AmДокумент35 страницCcnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (2)
- Ccnasecurity Sba FinalДокумент12 страницCcnasecurity Sba FinalBilly Zomg100% (2)
- Ccnasv1.1 Chp10 Lab-E Asa5510-Fw-cli StudentДокумент22 страницыCcnasv1.1 Chp10 Lab-E Asa5510-Fw-cli StudentHarrison HayesОценок пока нет
- Cisco Spiad - LabДокумент48 страницCisco Spiad - LabVicJ1992Оценок пока нет
- Ccnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 AmДокумент52 страницыCcnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 Amclearmoon247Оценок пока нет
- Activity Sheet 2 - Securing SwitchesДокумент28 страницActivity Sheet 2 - Securing SwitchesgfdОценок пока нет
- Lab05 - Configuring ASA Basic Settings and Firewall Using CLIДокумент26 страницLab05 - Configuring ASA Basic Settings and Firewall Using CLIAdrián ChóezОценок пока нет
- Lab 9 - RSS100 - Securing Layer 2 SwitchesДокумент38 страницLab 9 - RSS100 - Securing Layer 2 SwitchessecuopОценок пока нет
- 16.5.2 Lab - Secure Network DevicesДокумент5 страниц16.5.2 Lab - Secure Network DevicesFernando AlburquerqueОценок пока нет
- FirewallДокумент4 страницыFirewallMHUSNAINRОценок пока нет
- 10.1.4.8 Lab - Configure ASA 5505 Basic Settings and Firewall Using ASDMДокумент40 страниц10.1.4.8 Lab - Configure ASA 5505 Basic Settings and Firewall Using ASDMerojasОценок пока нет
- 6.3.1.1 Lab - Securing Layer 2 SwitchesДокумент22 страницы6.3.1.1 Lab - Securing Layer 2 SwitchesJson CañedaОценок пока нет
- 10.1.4.8 Lab A - DONEДокумент40 страниц10.1.4.8 Lab A - DONEDakotaОценок пока нет
- ITNB02 11.2.4.6 Securing Network DevicesДокумент8 страницITNB02 11.2.4.6 Securing Network DevicesShayneNakagawaОценок пока нет
- Configuring ASA Basic Settings and Firewall Using CLIДокумент16 страницConfiguring ASA Basic Settings and Firewall Using CLIGiovanny DíazОценок пока нет
- 10.3.1.2 Lab D - Configure AnyConnect Remote Access SSL VPN Using ASDM - InstructorДокумент38 страниц10.3.1.2 Lab D - Configure AnyConnect Remote Access SSL VPN Using ASDM - InstructorOmar Benigno RodriguezОценок пока нет
- 10.3.1.1 Lab - Configure Clientless Remote Access SSL VPNs Using ASA 5505 ASDMДокумент21 страница10.3.1.1 Lab - Configure Clientless Remote Access SSL VPNs Using ASA 5505 ASDMelizaОценок пока нет
- 6.3.1.1 Lab - Securing Layer 2 Switches PDFДокумент23 страницы6.3.1.1 Lab - Securing Layer 2 Switches PDFnganga0% (2)
- Ccnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 AmДокумент50 страницCcnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (3)
- Idoc - VN Cisco Secure Acs Switch Security For Controlled User AccessДокумент5 страницIdoc - VN Cisco Secure Acs Switch Security For Controlled User AccessTrái Tim Bên LềОценок пока нет
- 10.3.1.1 Lab C - Configure Clientless Remote Access SSL VPNs Using ASDM - InstructorДокумент31 страница10.3.1.1 Lab C - Configure Clientless Remote Access SSL VPNs Using ASDM - InstructorrodrigoduocОценок пока нет
- 11.2.4.6 Lab - Securing Network DevicesДокумент8 страниц11.2.4.6 Lab - Securing Network DevicesHarrison Hayes0% (2)
- CCNA Security PT Practice SBA 1Документ4 страницыCCNA Security PT Practice SBA 1Oscar Patricio Morales RuedaОценок пока нет
- Ism Lab Da1 19bce0833Документ12 страницIsm Lab Da1 19bce0833VardhanОценок пока нет
- 6.3.1.1 Lab - Securing Layer 2 SwitchesДокумент23 страницы6.3.1.1 Lab - Securing Layer 2 Switchesandy last100% (1)
- Configuring ASA Basic Settings and Firewall Using CLIДокумент7 страницConfiguring ASA Basic Settings and Firewall Using CLIMilošKovačevićОценок пока нет
- Template RouterДокумент2 страницыTemplate RouterHart Samuel (DevilMayCry)Оценок пока нет
- CCNA Security 1.1 Laboratorios Instructor Part 2Документ181 страницаCCNA Security 1.1 Laboratorios Instructor Part 2Ricardo Castro TenorioОценок пока нет
- 9.3.1.2 Lab - Configure ASA 5505 Basic Settings and Firewall Using CLIДокумент26 страниц9.3.1.2 Lab - Configure ASA 5505 Basic Settings and Firewall Using CLIJUan ALexis MEna0% (1)
- Configure AAA RADIUS AuthenticationДокумент23 страницыConfigure AAA RADIUS AuthenticationestebanОценок пока нет
- 9.4.1.7 Lab - Configuring ASA 5510 Basic Settings and Firewall Using ASDM - InstructorДокумент56 страниц9.4.1.7 Lab - Configuring ASA 5510 Basic Settings and Firewall Using ASDM - InstructorSalem TrabelsiОценок пока нет
- Laboratorium 1Документ35 страницLaboratorium 1SBX 4LifeОценок пока нет
- Voip - Planet Vip 480 Fs Ip Addres 10Документ12 страницVoip - Planet Vip 480 Fs Ip Addres 10Wahidi KaliriОценок пока нет
- C C C C!C C C: C CCCCCCCCC CCCCC CC C CCДокумент3 страницыC C C C!C C C: C CCCCCCCCC CCCCC CC C CCAnil ShelarОценок пока нет
- 10.3.1.1 Lab - Configure Clientless Remote Access SSL VPNs Using ASA 5505 ASDM - InstructorДокумент30 страниц10.3.1.1 Lab - Configure Clientless Remote Access SSL VPNs Using ASA 5505 ASDM - Instructorcheicktest1Оценок пока нет
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationДокумент8 страниц11.3.4.6 Lab - Using The CLI To Gather Network Device InformationSachinОценок пока нет
- 2.3.1.2 Packet Tracer - Skills Integration Challenge InstructionsДокумент2 страницы2.3.1.2 Packet Tracer - Skills Integration Challenge InstructionsjbleriaguОценок пока нет
- Configuring ASA 5510 Basic Settings and Firewall Using CLIДокумент18 страницConfiguring ASA 5510 Basic Settings and Firewall Using CLIIrfee75% (8)
- CCNA Security v2.0 Chapter 9 Exam AnswersДокумент13 страницCCNA Security v2.0 Chapter 9 Exam AnswersIbrahim ElghawilОценок пока нет
- 2.2.4.11 Lab - Configuring Switch Security Features - ScribdДокумент9 страниц2.2.4.11 Lab - Configuring Switch Security Features - ScribdstevehrccОценок пока нет
- Praktik Ke-6 Lab - Konfigurasi Pengaturan Dasar ASA Dan Firewall Menggunakan CLI - MahasiswaДокумент37 страницPraktik Ke-6 Lab - Konfigurasi Pengaturan Dasar ASA Dan Firewall Menggunakan CLI - MahasiswaIhsan EooiОценок пока нет
- 11.3.1.2 - CCNA Security Comprehensive Lab (Instructor Version)Документ53 страницы11.3.1.2 - CCNA Security Comprehensive Lab (Instructor Version)Krisztián AngyalОценок пока нет
- 2.2.4.11 Lab - Configuring Switch Security Features - ILMДокумент15 страниц2.2.4.11 Lab - Configuring Switch Security Features - ILMJose Maria Rendon Rodriguez100% (1)
- Lab 4.6.2: Challenge Security Configuration: Topology DiagramДокумент4 страницыLab 4.6.2: Challenge Security Configuration: Topology DiagramAnn EstesОценок пока нет
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОт EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОценок пока нет
- Virtualization Security: Protecting Virtualized EnvironmentsОт EverandVirtualization Security: Protecting Virtualized EnvironmentsРейтинг: 3 из 5 звезд3/5 (1)
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОт EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОценок пока нет
- 25th MuharramДокумент8 страниц25th MuharramQazi Tahir HussainОценок пока нет
- Kashaful HijjabДокумент173 страницыKashaful Hijjabshianews100% (1)
- Kashaf Ul SalaatДокумент80 страницKashaf Ul Salaatshianews100% (1)
- Exam Objective: Configure FailoverДокумент6 страницExam Objective: Configure FailoverQazi Tahir HussainОценок пока нет
- Ahsan Ul HadithДокумент395 страницAhsan Ul HadithShia Books For Download83% (6)
- Exam Objective: Configure FailoverДокумент6 страницExam Objective: Configure FailoverQazi Tahir HussainОценок пока нет
- CurlДокумент35 страницCurlOjhaОценок пока нет
- Switch 1 Multilayer Router VlansДокумент6 страницSwitch 1 Multilayer Router VlansErnesto MamaniОценок пока нет
- Gpover Ip FormatДокумент61 страницаGpover Ip FormatGaurav SethiОценок пока нет
- Transferring Outbound Internet Mail To An SMTP Server Over Notes RoutingДокумент2 страницыTransferring Outbound Internet Mail To An SMTP Server Over Notes RoutingedymaradonaОценок пока нет
- MicrosoftOpenSpecPoster - Accessiblility VersionДокумент12 страницMicrosoftOpenSpecPoster - Accessiblility Versionobad2011Оценок пока нет
- Nodeb Data Configuration: InternalДокумент57 страницNodeb Data Configuration: InternalOsama El MesalawyОценок пока нет
- What Is OspfДокумент29 страницWhat Is OspfUmar SiddiqueОценок пока нет
- Rfc4028 Session TimerДокумент25 страницRfc4028 Session TimerEliakim Feliciano MoraisОценок пока нет
- Difference Between AT89C51 and AT89S51Документ2 страницыDifference Between AT89C51 and AT89S51santosa.priyo75% (4)
- CS8581 - NETWORKs LAB EXAM QUESTIONSДокумент4 страницыCS8581 - NETWORKs LAB EXAM QUESTIONSLakshmi NarayananОценок пока нет
- TemplateДокумент533 страницыTemplateanilОценок пока нет
- TCP Connection EstablishmentДокумент10 страницTCP Connection EstablishmentfrtessОценок пока нет
- LAN Switching Part 2Документ43 страницыLAN Switching Part 2renjithkalaОценок пока нет
- Week 11 - Wireshark Lab 10Документ10 страницWeek 11 - Wireshark Lab 10davaughnОценок пока нет
- DNSintegration5 01Документ44 страницыDNSintegration5 01Gerardo ReyesОценок пока нет
- Configuracion InbternetДокумент3 страницыConfiguracion Inbternetlorenzo2501Оценок пока нет
- DHCP CCNPДокумент9 страницDHCP CCNPKumari PriyankaОценок пока нет
- Brkucc 2006Документ287 страницBrkucc 2006Darwin VanegasОценок пока нет
- CycloneTCP DatasheetДокумент3 страницыCycloneTCP DatasheetmusatОценок пока нет
- C ZTE MSAN Configuration ScriptДокумент10 страницC ZTE MSAN Configuration ScriptGamal AhmedОценок пока нет
- Modul B - Network Systems - Itnsa - LKSN 2021Документ5 страницModul B - Network Systems - Itnsa - LKSN 2021DEMERIA BUTARBUTARОценок пока нет
- Day - 23 DHCPДокумент5 страницDay - 23 DHCPठलुआ क्लबОценок пока нет
- Questions On Transport LayerДокумент6 страницQuestions On Transport LayerSiddhant AltОценок пока нет
- Webservice security using Username/Password authentication and HTTPSДокумент8 страницWebservice security using Username/Password authentication and HTTPSswapnil_bankarОценок пока нет
- DNS: Understanding the Domain Name SystemДокумент6 страницDNS: Understanding the Domain Name SystemRaghunath MudirajОценок пока нет
- Lecture 22 - FTPДокумент25 страницLecture 22 - FTPAji Kurniawan RahmanОценок пока нет
- TRAMARSA CALLAO GLBP CONFIGURATIONДокумент2 страницыTRAMARSA CALLAO GLBP CONFIGURATIONKrimo KhОценок пока нет
- 508 VishalChaurasiya Assignment-01Документ11 страниц508 VishalChaurasiya Assignment-01Vishal ChaurasiyaОценок пока нет
- ACN NotesДокумент78 страницACN NotesFatema TahaОценок пока нет
- IP Layer Network Administration With LinuxДокумент193 страницыIP Layer Network Administration With LinuxErnesto LabanОценок пока нет