Академический Документы
Профессиональный Документы
Культура Документы
Networking Technologies
Загружено:
Heta DesaiАвторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Networking Technologies
Загружено:
Heta DesaiАвторское право:
Доступные форматы
Primary Network Components: Networks consist of three primary components, servers, clients / workstations and resources.
Servers: Servers come in many shapes and sizes. They are a core component of network, providing a link to perform any task. The link it provides could e to a resource e!isting on the server it self or a resource on a client pc. Servers perform several task servers that provide files to the user on the network are called file servers. Servers that host printing services for users are called print servers. Servers can e multipurpose or single purpose. Server offers network the capa ility of centralizing the control and resources " can reduce administrative difficulties. They can e used to distri ute processes for alancing the load on the computer and can increase speed " performance. They can also offer departmentalizing of files for improved relia ility.
#edicated Server: These are assigned to provide specific application or services for the network ecause a dedicated server is specializing in only a few tasks. $t re%uires fewer resources then non-dedicated server. Non-dedicated Server: These are assigned to provide one or more network services and local access. & non-dedicated server is e!pected to e slightly more fle!i le than a dedicated server.
'lient/(orkstation: (orkstations are computers that the user on a network does their work on, performing activities such as data ase design, graphic design or other computers. &s client they are allowed to communicate with the server in order to use the network resources. $t takes several items to make a workstation into a client. )ou must install a network interface card, a special e!pansion card that allows a pc to talk on a network. )ou must connect it to a ca ling system and you must install some special software called client software which allow the computer to talk to the server. Network *esources: The servers are used to share the resources among other computers on the network. The workstations use the resources from the servers. & resource is any item that can e used on a network. *esources can include a road range of items including following. + ,rinters and other peripherals. + -iles. + &pplications. + #isk storage. v Network $nterface 'ard: The network interface card provides the physical interface etween computer " ca ling. $t prepares data, sends data " control the flow of data. $t can also receive and translate data into ytes for the ',. to understand. The following factors should e taken into consideration when choosing of network interface card, ,reparing data, sending and controlling data, configuration, drivers, compati ility and performance. Types of Networks: Heta J Desai Page 1
/ased on the role of the computer attached to them, networks are divided into three types. Server ased network, peer network and hy rid network. Server /ased Network 0'lient/Server Network1: Server ased networks are also called client/server network. Server ased networks are defined y the presence of dedicated server on a network that provide security " resources. $t divide processing task etween clients and servers. $n windows 2333 server ased networks are organized into what are called active directory domains. #omains are collections of network and clients that share security information. Special server called domain controllers control domain security " logon permission. 'omputer users cannot access the resources of servers in a domain until a domain controller has authenticated them. .ser information is stored centrally so users only need to logon once.
&dvantages: + Strong central security. + 'entral file storage. + They have a ility to pool availa le hardware and software with low cost. + They also have the a ility to share e!pensive e%uipment. + They include optimized dedicated servers which are faster at sharing network resources. + $t needs less intrusive security since a single password allow access to all shared resources on the network. + 4arge num er of users can e managed easily. #isadvantages: + 5!pensive dedicated hardware. + 5!pensive network operating system software " client licenses. + & dedicated network administrator.
,eer Networks: ,eer networks are defined y a lock of central control over the network. There are no servers in peer network. .sers simply share disk space " resources such as printer " fa!es. ,eer networks are organized into workgroups. There is not central login process. $f you have logged into one peer, you will a le to use only resource on the network that are not controlled y a specific password ecause there is not central security. )ou will have to know the individual password for each secured shared resources. This can e %uite inconvenient. ,eers cannot e optimized peers generally have licensing limitations that prevent more than a small num er of from simultaneously accessing resources.
&dvantages: + No e!tra investment in server where hardware, software are re%uired. + 5asy setup. + 4ittle network administration re%uired. + & ility of users to control resource sharing. + 4ower cost for small network.
#isadvantages: + &dditional load on computer ecause of resource sharing. Page 2
Heta J Desai
+ + + + +
$na ility of peers to handle as many network connections as servers. 4ock of central organization. No central point of storage. (eak and intrusive security. 4ock and central management.
Hybrid Networks: 6y rid networks have all three types of computers operating on them and generally have active directory domain and workgroups. This means while most shared resources are located on servers, network user still have access to any resources. $t also means that network users do not have to logon to the domain controller to access workgroup resources eing shared y peers.
&dvantages: + &dvantages of server ased network. + 7any of the advantages of peer ased network. + & ility of user and network administrator to control security ased on the important of the shared resources. #isadvantages: + 5!pensive dedicated hardware. + & dedicated network administrator.
Server Types: & server in a network is dedicated for performing specific task of other computers on the network. 'ommon server types include following. -ile servers, print servers, application servers, message servers, data ase servers. -ile Servers: -ile servers offer services that allow network users to share files. -ile servers are network application that store, retrieve and move data. This type of service is pro a ly the most important reasons companies invest in a network. There are several popular types of file servers such as (indows NT, Netware and apple share. -ollowing are the services provided y file servers.
-ile Transfer: To transfer a file from one computer to another computer, you could save the file to a floppy disk, put on your sneakers and wait it over to other computer. -ortunately networks ecome more sophisticated and egan to offer file transfer services. 5very network operating system has its own level of file security. -ile security level is needed when all these files transferring taking place. -ile Storage " #ata 7igration: $nformation e!plosion is a huge amount of data that must e stored somewhere. -ile server provide three categories of file storage - online storage, offline storage and near-line storage. The process y which data is moved from online to offline or near-line is called data migration. -iles are selected for migration ased on factors such as the last time the file was accessed, the file owner or the file size. -ile .pdate Synchronization: Page 3
Heta J Desai
-ile update synchronization ensures that each user of a file has the latest version. -ile synchronization works to ensure that changes made to files are organized in the chronological order in which they take place and those files are properly updated. ,rint Servers: ¬her important factor of computer networking was the demand for the a ility to share printers. The advent of networking represented a whole new level of computer printing ecause a network can allow users to share printers. $t allows you to place printer where convenient. $t achieves etter workstation performance y using high speed network data transfer. ,rint services manage and control printing on a network allowing multiple " simultaneous access to printing facilities. Network operating system achieves this y using print %ueues. ,rinting on a network with %ueues can e more efficient way for users to work. Network printing also cost8s y allowing shared access to printing devices. ¬her print service is fa! service. &pplication Servers: &pplication services allow client ,'s to access " use e!tra computing power " e!pensive software applications that reside on a shared computer. )ou can add specialized server to provide specific applications on a network. &pplication servers can e dedicated computers setup specifically for the purpose of providing application services. <hough in the earlier days of networking, application services were not often found on networks they have recently ecome more popular. 7essage Servers: 7essage servers provide message services in a wide verity of communication methods that go far eyond simple file servers with message services, data can take the form of graphics, digitized video or audio as well as te!t and inary data. 7essage services must coordinate the comple! interactions etween users, documents and applications. 7essage servers provide four main services as follow 9 electrical mail, workgroup applications, o :ect oriented applications and directory services. #ata ase Servers: #ata ase services can provide a network with powerful data ase capa ilities that are availa le for use on relatively weak ,'s most data ase systems are client server ased. The client end portion of the application runs on the client providing an interface and handling less intensive functions. The server end portion of application handles the intensive performance of data ase operations. #ata ase servers are ecoming increasingly powerful providing comple! services including security, data ase optimization " data distri ution.
Topologies: Heta J Desai Page 4
Topology is the way networks are physically connected together. Topology determines the comple!ity and therefore the cost of network ca le installation. 'a le installation can often e a ma:or cost factor for network system. Topology also determines the strategy for physically e!panding the network. Linear B s Topology: $n this layout, a single main ca le connects each node, in what amounts to a single line of computers accessing it from end to end. 5ach node is connected to two others e!cept the machines at either end of the ca le, which are connected only to one other node. The network operating system keeps track of a uni%ue electronic address for each node, and manages the flow of data ased on this addressing scheme. This topology has the advantage of not re%uiring that every computer e up and running in order for the network to function. /ut ecause a single ca le is dedicated to all the information traffic, performance can e slow at times. This topology is often found in client/server systems, where one of the machines on the network is designated as a file server meaning that it is dedicated solely to the distri ution of data files, and is not usually used for information processing. (hen the computer wants to send a message to another computer, it would send an addressing message to it and wait for a response. The response would indicate whether that computer is ready to receive the previous computers message. &fter this communication is finished, it goes to the ne!t one and esta lishes a link with it.
!dvantages of T"e B s Topology: Heta J Desai Page 5
;1
The us is simple, relia le in very small networks, easy to use, and easy to understand. 21 The us re%uires the least amount of ca le to connect the computers together and is therefore less e!pensive than other ca ling arrangements. <1 $t is easy to e!tend a us. Two ca les can e :oined into one longer ca le with a connector, making a longer ca le and allowing more computers to :oin the network. #isadvantages of T"e B s Topology: ;1 6eavy network traffic can slow down a us considera ly. /ecause any computer can transmit at any time, and computers on most us networks do not coordinate with each other to reserve times to transmit, a us network with a lot of computers can spend a lot to its andwidth with the computers interrupting each other instead of communicating. The pro lem only gets worse as more computers are added to the network. 21 $t is difficult to trou leshoot a us. & ca le reak or malfunctioning computer anywhere etween two computers or loose connector will also cause reflections and ring down the whole network, causing all network activity to stop. Cir$ lar Topology: This layout is similar to the linear us, e!cept that the nodes are connected in a circle using ca le segments. $n this layout, each node is physically connected to only two others. 5ach node passes information along to the ne!t, until it arrives at its intended destination. Since each computer re-transmits what it receives, a ring is an active network and is not su :ect to the signal loss pro lems which a us topology e!periences. There is no termination ecause there is no end to the ring.
,erformance is faster on this system ecause each portion of the ca ling system is handling only the data flow etween two machines. This type of topology can e found in peer-to-peer networks, in which each machine manages oth information processing and the distri ution of data files. Some ring networks do token passing. & short message called a token is passed around the ring until a computer wishes to send information to another computer. That computer modifies the token, adds an electronic address and data, and sends it around the ring. 5ach computer in se%uence receives the token and the information and passes them to the ne!t computer until either the electronic address matches the address of a computer or the token returns to its originator. The receiving computer returns a Heta J Desai Page 6
message to the originator indicating that the message has een received. The sending computer then creates another token and places it on the network, allowing another station to capture the token and egin transmission. The token circulates until a station is ready to send and captures the token. !dvantages of %ing Topology: ;1 /ecause every computer is given e%ual access to the token, no one computer can monopolize the network. 21 The fair sharing of the network allows the network to degrade gracefully as more users are added. #isadvantages of %ing Topology: ;1 -ailure of one computer on the ring can affect the whole network. 21 $t is difficult to trou leshoot a ring network. <1 &dding or removing computers disrupts the network.
Star Topology: 5ach computer on a star network communicates with a central hu that re-sends the message either to all the computers or only to the destination computer. The hu in a roadcast star network can e active or passive. &n active hu regenerates the electrical signal and sends to all the computers connected to it. This type of hu is often called a multiport repeater. &ctive hu s and switches re%uire electrical power to run. & passive hu merely acts as a connector point and does not amplify or regenerate the signal. ,assive hu s do not re%uire electrical power to run. )ou can use several types of ca le to implement a star network. 6y rid hu can accommodate several types of ca le in the same star network. )ou can e!pand a star network y placing another star hu where a computer might otherwise go, allowing several more computers or hu s to e connected to that hu . This creates a hy rid star network.
!dvantages of Star Topology: -
Heta J Desai
Page 7
;1
$t is easy to modify and add new computers to a star network without distur ing the rest of the network. )ou simply run a new line from the computer to the central location and plug it into the hu . (hen the capacity of the central hu is e!ceeded, you can replace it with one that has a larger num er of ports to plug lines into. 21 The center of a star network is a good place to diagnose network faults. $ntelligent hu s also provide for centralized monitoring and management of the network. <1 Single computer failures do not necessarily ring down the whole star network. The can detect a network fault and isolate the offending computer or network ca le and allow the rest of the network to continue operation. =1 )ou can use several ca le types in the network with a hu that can accommodate multiple ca le types. #isadvantages of Star Topology: ;1 $f the central hu fails, the whole network fails to operate. 21 7any star networks re%uire a device at the central point to re roadcast or switch network traffic. <1 $t costs more to ca le a star network ecause all network ca les must e pulled to one central point, re%uiring more ca le than other networking topologies. Tree Topology: This is a network topology containing zero or more nodes that are linked together in a hierarchical fashion. The topmost node is called the root. The root may have zero or more child nodes, connected y edges> the root is the parent node to its children. 5ach child node can in turn have zero or more children of its own. Nodes sharing the same parents are called si lings. 5very node in a tree has e!actly one parent node, and all nodes in the tree are descendants of the root node. These relationships ensure that there is always one and only one path from one node to any other node in the tree.
&rap" Topology: $n this method of connection, zero or more nodes are linked together in an ar itrary fashion. &ny two nodes in a graph may e connected y a link. Not all the nodes in a Heta J Desai Page 8
graph need to e connected, ut if a path can e traced etween any two nodes, the graph is a connected one.
Star B s and Star %ing Topology: There are the two most common com ination networks. Star /us Network: The star us topology com ines the us and the star, linking several star hu s together with us trunks. $f one computer fails, the hu can detect the fault and isolate the computer. $f the hu fails, computers connected to it will not e a le to communicate, and the us network will e roken into two segments that cannot reach each other. Star *ing Network: $n the star ring, also called the star wired ring, the network ca les are laid out much like a star network, ut a ring is implemented in the central hu . ?utlying hu s can e connected to the inner hu , effectively e!tending a loop of the inner ring.
Heta J Desai
Page 9
Heta J Desai
Page 10
7esh Topology: $t is the most commonly used topology in wan and is often seen in pu lic network link internet. &ccording to mesh network theory every device needs to have point to point connection with every other device on the network, ut in practice, this network is used in a hy rid approach with only the most important devices interconnected in the mesh. This is so ecause it is impractical to do so in normal condition we can say that this is peer 9 to 9 peer networking.
'ategories of Network: -
Heta J Desai
Page 11
There are generally three primary categories of network. $nto which category a network falls is determined y its size, ownership, distance it covers and its physical architecture. -ollowing are the categories of network. 4ocal &rea Network 04&N1: & local area network is usually privately owned " links the devices in a single office, uilding or campus. #epending on the needs of an organization " the type of technology used a local area network can e as simple as for pc and printer, or it can e!tend throughout a company " include voice, sound " video to a few kilometers. 4ocal area networks are designed to allow resources to e shared etween pc and workstations. ?ne of the computers may e given a large capacity disk drive " ecome a server to the other clients. Software can e stored on this central server " ased as needed y the whole group. $n addition to size, local area networks are distinguished from other network y their transmission media " topology. $n general, local area network will use only one type off transmission medium. The most common local area network topologies are us, ring and star. Traditionally, local area networks have data rates in the = to ;@ 7/,S range. Today, however speeds are increasing and can reach ;33 7/,S with giga it systems in developments. 4ocal area network can e defined as a network which does not e!ceed a distance of more than ;.2A mile from one end to other end.
.ses " /enefits of 4ocal &rea Network: 4ocal area network connects users to a set of common resources. Sharing " accessing of information in this way is easier " economical. To access to files in a central storage area, a pointer is shared among a group of users or email access is provided. $n this way, local area networks can improve productivity in an organization. $f a department has ;3 users each re%uiring 2A B/ of storage space. $t would e etter for users to share a single 2A3 B/ hard disk instead of providing each user with their own dedicated 2A B/ hard disk. 'ost per unit of storage is significantly reduced. #isadvantages: $n local area networks the distance is limited. /ecause of distance is limited, the num er of computers are limited.
7etropolitan &rea Network 07&N1: & metropolitan area network is designed to e!tend over an entire city. $t may e single network such as a ca le network or it may e a means of connecting a num er of local area network into a larger network so that resources may e shared local area network to local area network as well as device to device. 5!ample: & company can use a metropolitan area network to connect the local area networks in all of its offices through out the city. & metropolitan area network may e wholly owned " operated y a private company or it may e a service provided y a pu lic company, such as a local telephone company. 7any telephone companies provide a popular metropolitan area network service called Switched 7ulti #ata Service 0S7#S1. (ide &rea Network 0(&N1: Page 12
Heta J Desai
& wide area network provides long distance transmission of data, voice, image and video information over large geographical areas that may comprise a country, a continent or even the whole world. $n contrast to local area networks which depend on their own hardware for transmission, wide area network may utilize pu lic, leased or private communication devices usually in com inations and can therefore span on unlimited num er of miles. & wide area network that is wholly owned " used y a single company is often referred to as an enterprise network. $t is often made up of multiple local area networks :oined together. (ide area network actually consist of two or more different networks. The most commonly known wide area network is internet. (ide area network uses satellites " wireless communications, therefore the information can e shared faster. 'ampus &rea Network 0'&N1: campus area network e defined as a network which is limited in scope to a single geographical location while the size may e!ceed the size defined for local area network.
$nternetworks: (hen two or more networks are connected, they ecome an internetwork or internet. $ndividual networks are :oined into internetworks y the use of internetworking devices. These devices include routers " gateways. The term internet should not e confused with the internet. The first is a generic term used to mean an interconnecting of networks. The second is the name of a specific world wide network thus the internet is the network of networks. T',/$, ,rotocol Suite: The T',/$, protocol suit, used in the internet, was developed prior to the open system interconnection model> therefore the layers in the transmission control protocol suit do not match e!actly with those in the open system interconnection model. The T',/$, protocol suit is made of five layers: ,hysical, #ata 4ink, Network, Transport and &pplication. The first four layers provide physical standards, network interface, internetworking and transport functions that corresponded to the first four layers of the open system interconnection model. The three topmost layers in the open system interconnection model however are presented in T',/$, y a single layer called the application layer. The T',/$, is a hierarchical protocol made up of interactive modules, each of which provides a specific functionality, ut they are not necessarily independent whereas the open system interconnection model specifies which function elong to each of its layers, the layer of the T',/$, protocol suit contain independent protocols that campus area network e mi!ed " matched depending on needs of the system. The term hierarchical means that each upper level protocol is supported y one or more lower level protocols. &t the transport layer, T',/$, defines two protocols: Transmission 'ontrol ,rotocol 0T',1 and .ser #atagram ,rotocol 0.#,1. &t the network layer, the main protocol defined y T',/$, is internetworking protocol 0$,1 although there are some other protocols that support data movements in this layer. $S? C=D< -T, " S7T, normally use T',/$, service. #ata Transmission 7odes: There are three modes of data transmission that corresponds to the three types of circuits availa le. Heta J Desai Page 13
Simple!, 6alf 9 #uple! -ull 9 #uple!.
;.
Simple!: Simple! communications imply a simple method of communicating, which they are. $n simple! communications mode, there is a one way communication transmission. Television transmission is good e!ample of simple! communications. The main transmitter sends out a signal, ut it does not e!pect a reply as the receiving units cannot issue a reply ack to the transmitter. & data collection terminal on a factory floor or a line printer. ¬her e!ample of simple! communication is a key oard attached to a computer ecause the key oard can only send data to the computer. &t first thought it might appear ade%uate for many types of application in which flow of information is unidirectional. 6owever, in almost all data processing applications, communication in oth directions is re%uired. 5ven for a E?ne 9 wayF flow of information from a terminal to a computer, the system will e designed to allow the computer to signal the terminal that data has een received. (ithout this capa ility, the remote user might enter data and never know that it was not received y the other terminal. 6ence, simple! circuits are seldom used ecause a return path is generally needed to send acknowledgement, control or error signals. 6alf 9 #uple!: $n half 9 duple! mode, oth units communicate over the same medium, ut only one unit can send at a time. (hile one is in send mode, the other unit is in receiving mode. $t is like two polite people talking to each other 9 one talk, the other listens, ut neither one talks at the same time. Thus, a half 9 duple! line can alternately send and receive data. $t re%uires two wires. This is the most common type of transmission for voice Page 14
2.
Heta J Desai
communications ecause only one person is supposed to speak at a time. $t is also used to connect a terminal with a computer. The terminal might transmit data and then the computer responds with an acknowledgement. The transmission of data to and from a hard disk is also done in half 9 duple! mode. <. -ull 9 #uple!: $n a half 9 duple! system, the line must e ETurned &roundF each time the direction is reversed. This involves a special switching circuit and re%uires a small amount of time. (ith high speed capa ilities of the computer, this turn-around time is unaccepta le in many instances. &lso, some applications re%uire simultaneous transmission in oth directions, in such cases> a full 9 duple! system is used that allows information to flow simultaneously in oth directions on the transmission path. .se of a full 9 duple! line improves efficiency as the line turn-around time re%uired in a half 9 duple! arrangement is eliminated. $t re%uires four wires.
#igital and &nalog #ata: ;. #igital #ata: Suppose we are standing on the hockey playground, The whistle is elow in short ursts of high pitched sounds like, ,55, ,5, ,5, ,5 or it may have a long urst ,5555555. /oth of these whistles call 'onway different meaning to the players. The first one is an indication to the players to start the game. The second long whistle is to stop the match immediately. The message conveyed y the urst of this sound energy in short pulses is very clear to all the players.
There is no chance of confusion even if the distance of a player is large from the referee. This is an e!ample of #igital #ata transmission. Short urst of sound energy are sent y the sender to the receiver and the receiver is a le to understand it clearly. This type of digital data is as shown particularly in a ove figure.
2.
&nalog #ata: Suppose we are sitting in a concern hall where many musical instruments are eing played y different players. Say one musician is playing Sitar and the other is playing Ta la. The harmony of sound coming out from these two instruments gives you the pleasure of listening. $f there is any mismatch etween the timing of the tune of Sitar and the Ta la, you get the unpleasantness and thus consider it a noise rather than music. Page 15
Heta J Desai
This is an analog data communication. /oth Sitar and Ta la are sending sound waves in the same se%uence and there is a rhythm and harmony etween the two. & pictorial representation of analog signal is shown in elow figure.
T',/$, ,rotocol Suite: The T',/$, protocol suit, used in the internet, was developed prior to the open system interconnection model> therefore the layers in the transmission control protocol suit do not match e!actly with those in the open system interconnection model. The T',/$, protocol suit is made of five layers: ,hysical, #ata 4ink, Network, Transport and &pplication. The first four layers provide physical standards, network interface, internetworking and transport functions that corresponded to the first four layers of the open system interconnection model. The three topmost layers in the open system interconnection model however are presented in T',/$, y a single layer called the application layer. The T',/$, is a hierarchical protocol made up of interactive modules, each of which provides a specific functionality, ut they are not necessarily independent whereas the open system interconnection model specifies which function elong to each of its layers, the layer of the T',/$, protocol suit contain independent protocols that campus area network e mi!ed " matched depending on needs of the system. The term hierarchical means that each upper level protocol is supported y one or more lower level protocols. &t the transport layer, T',/$, defines two protocols: Transmission 'ontrol ,rotocol 0T',1 and .ser #atagram ,rotocol 0.#,1. &t the network layer, the main protocol defined y T',/$, is internetworking protocol 0$,1 although there are some other protocols that support data movements in this layer. $S? C=D< -T, " S7T, normally use T',/$, service.
Heta J Desai
Page 16
Вам также может понравиться
- Presentacion 6 PDFДокумент16 страницPresentacion 6 PDFJose Leonardo Simancas GarciaОценок пока нет
- What Is The Computer NetworkДокумент6 страницWhat Is The Computer NetworkSanjeev KumarОценок пока нет
- 2.2 NOS-Facilities&ServciesДокумент12 страниц2.2 NOS-Facilities&ServciesMOHAMAD IMRAN BIN MOHAMAD YUSRIОценок пока нет
- Unit 1Документ32 страницыUnit 1link7096907539Оценок пока нет
- Simple Network:: Dinesh Singh DhamiДокумент28 страницSimple Network:: Dinesh Singh DhamiMohd Junaid AhmadОценок пока нет
- Computer Network: IBPS SO (IT) Exam 2017Документ19 страницComputer Network: IBPS SO (IT) Exam 2017Narsimha Charya ManthangodeОценок пока нет
- CNF152S - Introduction To NetworkingДокумент54 страницыCNF152S - Introduction To NetworkingBenito KrielОценок пока нет
- Microproject DCCДокумент17 страницMicroproject DCCRiddhi SardesaiОценок пока нет
- Network Operating SystemДокумент7 страницNetwork Operating SystemMuñoz, Jian Jayne O.Оценок пока нет
- NetworkingДокумент86 страницNetworkingKanishka Siriwardana100% (6)
- Unit 1Документ24 страницыUnit 1tarlajainОценок пока нет
- 2 Netwotk Types and ComponentsДокумент35 страниц2 Netwotk Types and ComponentsRashad MahmoodОценок пока нет
- Computer NetworksДокумент59 страницComputer NetworksSimon ChegeОценок пока нет
- Computer Network - KLCДокумент46 страницComputer Network - KLCashishОценок пока нет
- Csa-Unit1 3Документ13 страницCsa-Unit1 3Chhavi GaggarОценок пока нет
- IT1402 MWT Notes - CSE TUBE PDFДокумент112 страницIT1402 MWT Notes - CSE TUBE PDFsiva sekharОценок пока нет
- ServersДокумент8 страницServersjohn bourkeОценок пока нет
- System Infrastructure Part 2Документ9 страницSystem Infrastructure Part 2Charla SuanОценок пока нет
- Best Fit TopologyДокумент191 страницаBest Fit TopologyBikila SeketaОценок пока нет
- Network Operating SystemДокумент45 страницNetwork Operating Systemheidee carpioОценок пока нет
- Lecture OneДокумент42 страницыLecture OneERICK LOUIS ADOKOОценок пока нет
- Puter NetworksДокумент28 страницPuter Networkswaleed.khaldОценок пока нет
- Complete Unit 1Документ14 страницComplete Unit 1rag33100% (1)
- Coc 3 EditedДокумент186 страницCoc 3 EditedYuri AngОценок пока нет
- Computer NetworkingДокумент85 страницComputer NetworkingsiifantkОценок пока нет
- Networking Hardware IGCSE CIE Computer Science Free Material For o LevelДокумент12 страницNetworking Hardware IGCSE CIE Computer Science Free Material For o Levelamartya k singhОценок пока нет
- Computer NetworkДокумент84 страницыComputer Networkahmed raedОценок пока нет
- Report Group 14Документ5 страницReport Group 14ExphyerionОценок пока нет
- 5-Servers and Storage Devices, Content ManagementДокумент36 страниц5-Servers and Storage Devices, Content Managementmalayajay.patel2021Оценок пока нет
- Week 4Документ3 страницыWeek 4arsharm2004Оценок пока нет
- Almas BajiДокумент21 страницаAlmas BajiiamnomandungeОценок пока нет
- 017A039 Unit 1.2.1Документ43 страницы017A039 Unit 1.2.1Ashraya K.C.Оценок пока нет
- Abdu Net Ass.t1Документ5 страницAbdu Net Ass.t1Ahmed KedirОценок пока нет
- ServerДокумент65 страницServerKuhiuhyrfОценок пока нет
- CCNA ProjectДокумент54 страницыCCNA ProjectManan33% (3)
- System AdministrationДокумент85 страницSystem AdministrationAnita SupramaniamОценок пока нет
- An Introduction To Local Area Networks: An Overview of Peer-to-Peer and Server-Based ModelsДокумент20 страницAn Introduction To Local Area Networks: An Overview of Peer-to-Peer and Server-Based ModelsKiana ValdezОценок пока нет
- Understanding Server RolesДокумент32 страницыUnderstanding Server RolesJaspher TarucОценок пока нет
- P2P - Activity 1Документ7 страницP2P - Activity 1Abdullah MohammadОценок пока нет
- ServersДокумент5 страницServersShelby GuerrierОценок пока нет
- Uci 102 Topic 1 NotesДокумент4 страницыUci 102 Topic 1 Notesdeety597Оценок пока нет
- Set-Up Computer ServerДокумент41 страницаSet-Up Computer ServerJsmjc IDОценок пока нет
- Basic Server PPT (THDC)Документ99 страницBasic Server PPT (THDC)repovinodhОценок пока нет
- Configure ServerДокумент5 страницConfigure ServerBikila SeketaОценок пока нет
- Introduction To Computer NetworksДокумент31 страницаIntroduction To Computer NetworksHOD-DIT PSG-PTC100% (1)
- NetworksДокумент2 страницыNetworksSirraj ArvindОценок пока нет
- It4128 AbordoДокумент5 страницIt4128 AbordoJunvy AbordoОценок пока нет
- E6032-CP (Networking)Документ194 страницыE6032-CP (Networking)adin_othmanОценок пока нет
- Networks 2Документ2 страницыNetworks 2Long LeОценок пока нет
- Topic 9 Network Operating SystemДокумент10 страницTopic 9 Network Operating SystemsimonnjauОценок пока нет
- Client:: Server: Servers Are Generally Devices With Files and Databases Stored InsideДокумент2 страницыClient:: Server: Servers Are Generally Devices With Files and Databases Stored InsideabhiОценок пока нет
- Sf1uwfjuu - Medical Image Distribution, Networks, and CommunicationsДокумент17 страницSf1uwfjuu - Medical Image Distribution, Networks, and Communicationsivanne zaideОценок пока нет
- Information Sheet 1Документ20 страницInformation Sheet 1Archie May DegamonОценок пока нет
- Onfigure ND Dminister Erver: C A A SДокумент60 страницOnfigure ND Dminister Erver: C A A Sabenezer abitiОценок пока нет
- Grade 9 Css - Nov 27, 2017 - Pp225-261 Server/S - : Network Operating Systems (Noss)Документ1 страницаGrade 9 Css - Nov 27, 2017 - Pp225-261 Server/S - : Network Operating Systems (Noss)leoj12001Оценок пока нет
- Aces Tagum College: Senior High SchoolДокумент29 страницAces Tagum College: Senior High SchoolOrlando NajeraОценок пока нет
- Cloud Computing Made Simple: Navigating the Cloud: A Practical Guide to Cloud ComputingОт EverandCloud Computing Made Simple: Navigating the Cloud: A Practical Guide to Cloud ComputingОценок пока нет
- Unit 3Документ55 страницUnit 3Heta DesaiОценок пока нет
- Addressing Modes: Heta J Desai SDJДокумент10 страницAddressing Modes: Heta J Desai SDJHeta DesaiОценок пока нет
- TCP - IP Model - Intro NotesДокумент3 страницыTCP - IP Model - Intro NotesAnonymous OsssbjОценок пока нет
- The Stages of Problem-Solving Notes: SYBCA - Heta DesaiДокумент8 страницThe Stages of Problem-Solving Notes: SYBCA - Heta DesaiHeta DesaiОценок пока нет
- Practical Assignment For DBMSДокумент2 страницыPractical Assignment For DBMSHeta Desai100% (2)
- Gateways in NetworkingДокумент2 страницыGateways in NetworkingHeta DesaiОценок пока нет
- Electronic CommerceДокумент87 страницElectronic CommerceHeta DesaiОценок пока нет
- Enterprise Resource PlanningДокумент4 страницыEnterprise Resource PlanningHeta DesaiОценок пока нет
- Network Router: Determine The Best Path For Sending DataДокумент4 страницыNetwork Router: Determine The Best Path For Sending DataHeta DesaiОценок пока нет
- Hardware Equipments HubДокумент2 страницыHardware Equipments HubHeta DesaiОценок пока нет
- E CommerceДокумент48 страницE CommerceHeta DesaiОценок пока нет
- Network Bridges: What Is The Use of BridgeДокумент2 страницыNetwork Bridges: What Is The Use of BridgeHeta DesaiОценок пока нет
- IP Address - What Is IP Address?: ComputerДокумент56 страницIP Address - What Is IP Address?: ComputerHeta DesaiОценок пока нет
- Computer Network NotesДокумент22 страницыComputer Network NotesHeta Desai100% (1)
- For Sybca - Heta Desai: Student Notes On Information SystemДокумент56 страницFor Sybca - Heta Desai: Student Notes On Information SystemHeta DesaiОценок пока нет
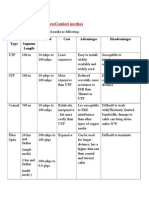
- Comparing Media Types (Guided Media) : Media Type Max. Segment Length Speed Cost Advantages DisadvantagesДокумент1 страницаComparing Media Types (Guided Media) : Media Type Max. Segment Length Speed Cost Advantages DisadvantagesHeta DesaiОценок пока нет
- Is Called A Protocol.: Protocol Is A Standard Procedure and Format That Two Data Communication DevicesДокумент7 страницIs Called A Protocol.: Protocol Is A Standard Procedure and Format That Two Data Communication DevicesHeta DesaiОценок пока нет
- IP Address - What Is IP Address?: ComputerДокумент56 страницIP Address - What Is IP Address?: ComputerHeta DesaiОценок пока нет
- Welltech P101 201 SIP 102Документ63 страницыWelltech P101 201 SIP 102stroemmmaОценок пока нет
- MTB 1 Lesson 1Документ17 страницMTB 1 Lesson 1Oscar Hogan BaldomeroОценок пока нет
- Chapter Ii-2020Документ16 страницChapter Ii-2020Muhammad Firmal KusyandiОценок пока нет
- Resume Keeley FaithДокумент3 страницыResume Keeley Faithapi-579883161Оценок пока нет
- Introduce The Present PerfectДокумент7 страницIntroduce The Present PerfectSanjay JhaveriОценок пока нет
- Key Features - eSRVCC SolutionДокумент1 страницаKey Features - eSRVCC SolutionabdulqaderОценок пока нет
- Lesson Plan Form Sekolah Alam Insan MuliaДокумент2 страницыLesson Plan Form Sekolah Alam Insan MuliaCahyo Setiyo BudionoОценок пока нет
- Exit Interview QuestionnaireДокумент2 страницыExit Interview QuestionnaireCirce ManunulatОценок пока нет
- Chapt 2 AsuuДокумент9 страницChapt 2 AsuuNReqko SomosaОценок пока нет
- Computers VocabularyДокумент1 страницаComputers VocabularyedithОценок пока нет
- Reading Remediation ActivitiiesДокумент36 страницReading Remediation ActivitiiesAisa Ordonez Galo-Castro100% (1)
- Choreographer Research RubricДокумент2 страницыChoreographer Research Rubricapi-328604194Оценок пока нет
- Switching Basics and Intermediate Routing: CNAP Semester 3Документ36 страницSwitching Basics and Intermediate Routing: CNAP Semester 3Vo Ngoc HoangОценок пока нет
- TikTok For Concrete Coating Companies CleanДокумент2 страницыTikTok For Concrete Coating Companies CleanelijahОценок пока нет
- Appendix B IFE-EFE SpreadsheetsДокумент12 страницAppendix B IFE-EFE SpreadsheetsradislamyОценок пока нет
- Westwood Publishing CaseДокумент33 страницыWestwood Publishing CasePrinsesa Ni PrinsipeОценок пока нет
- SN 1 RevisedДокумент3 страницыSN 1 Revisedapi-550355013Оценок пока нет
- Top 10 Internet Safety RulesДокумент1 страницаTop 10 Internet Safety RulesAnnie AntaranОценок пока нет
- Addresses - National Crime CheckДокумент7 страницAddresses - National Crime CheckNadil AminОценок пока нет
- QuestioningДокумент11 страницQuestioningCrisnelynОценок пока нет
- Microteaching Reflection Paper Ivana Milutinović 201400697Документ2 страницыMicroteaching Reflection Paper Ivana Milutinović 201400697Yu KiОценок пока нет
- Nature of Technical WritingДокумент12 страницNature of Technical WritingNix Csr AmrОценок пока нет
- It Infrastructure BusinessContinuityPlanandMaintenanceДокумент10 страницIt Infrastructure BusinessContinuityPlanandMaintenanceEka SatriaОценок пока нет
- Analog E&M Voice Signaling OverviewДокумент4 страницыAnalog E&M Voice Signaling OverviewsopencoОценок пока нет
- Kylene Beers ResponsesДокумент4 страницыKylene Beers Responsesapi-272817792Оценок пока нет
- Abstract of Low Energy Efficient Wireless Communication NetworkДокумент2 страницыAbstract of Low Energy Efficient Wireless Communication NetworkSushmitha yadavОценок пока нет
- Intermediate Arabic For DummiesДокумент541 страницаIntermediate Arabic For DummiesFot-li Gasto100% (1)
- Cultural Studies in The Framework of English Language TeachingДокумент7 страницCultural Studies in The Framework of English Language TeachingVlora KupinaОценок пока нет
- Lesson Plan Get To Know The NeighboursДокумент3 страницыLesson Plan Get To Know The NeighboursccyecОценок пока нет