Академический Документы
Профессиональный Документы
Культура Документы
PT Activity: Configure AAA Authentication On Cisco Routers - 1%
Загружено:
alb3rtlinИсходное описание:
Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
PT Activity: Configure AAA Authentication On Cisco Routers - 1%
Загружено:
alb3rtlinАвторское право:
Доступные форматы
PT Activity: Configure AAA Authentication on Cisco Routers - 1%
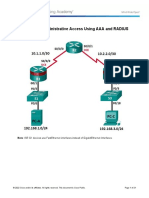
Topology Diagram
Addressing Table
Device Interface IP Address Subnet Mask
R1
Fa0/0 192.1!.1.1 2"".2"".2"".0
#0/0/0 10.1.1.2 2"".2"".2"".2"2
R2
#0/0/0 10.1.1.1 2"".2"".2"".2"2
Fa0/0 192.1!.2.1 2"".2"".2"".0
#0/0/1 10.2.2.1 2"".2"".2"".2"2
R$
#0/0/1 10.2.2.2 2"".2"".2"".2"2
Fa0/0 192.1!.$.1 2"".2"".2"".0
TACAC#% #erver &'C 192.1!.2.2 2"".2"".2"".0
RA(')# #erver &'C 192.1!.$.2 2"".2"".2"".0
PC-A &'C 192.1!.1.$ 2"".2"".2"".0
PC-* &'C 192.1!.2.$ 2"".2"".2"".0
PC-C &'C 192.1!.$.$ 2"".2"".2"".0
A++ contents are Co,yright - 1992.2012 Cisco #yste/s0 'nc. A++ rights reserve1. This 1ocu/ent is Cisco Pu2+ic 'nfor/ation. Page 1 of 3
CC&A #ecurity
Learning Objectives
Configure a +oca+ user account on R1 an1 authenticate on the conso+e an1 4T5 +ines using +oca+
AAA.
4erify +oca+ AAA authentication fro/ the R1 conso+e an1 the PC-A c+ient.
Configure a server-2ase1 AAA authentication using TACAC#%.
4erify server-2ase1 AAA authentication fro/ PC-* c+ient.
Configure a server-2ase1 AAA authentication using RA(')#.
4erify server-2ase1 AAA authentication fro/ PC-C c+ient.
Introduction
The net6or7 to,o+ogy sho6s routers R10 R2 an1 R$. Current+y a++ a1/inistrative security is 2ase1 on 7no6+e1ge
of the ena2+e secret ,ass6or1. 5our tas7 is to configure an1 test +oca+ an1 server-2ase1 AAA so+utions.
5ou 6i++ create a +oca+ user account an1 configure +oca+ AAA on router R1 to test the conso+e an1 4T5 +ogins.
)ser account: Admin an1 ,ass6or1 adminpa!!
5ou 6i++ then configure router R2 to su,,ort server-2ase1 authentication using the TACAC#% ,rotoco+. The
TACAC#% server has 2een ,re-configure1 6ith the fo++o6ing:
C+ient: "# using the 7ey6or1 tacacspa!!
)ser account: Admin# an1 ,ass6or1 admin#pa!!
Fina++y0 you 6i++ configure router R$ to su,,ort server-2ase1 authentication using the RA(')# ,rotoco+. The
RA(')# server has 2een ,re-configure1 6ith the fo++o6ing:
C+ient: "$ using the 7ey6or1 radiuspa!!
)ser account: Admin$ an1 ,ass6or1 admin$pa!!
The routers have a+so 2een ,re-configure1 6ith the fo++o6ing:
8na2+e secret ,ass6or1: ciscoenpa!!
R'P version 2
%ote& The conso+e an1 4T5 +ines have not 2een ,re-configure1.
Task & 'onfigure Local AAA Aut(entication for 'onsole Access on "
Step 1. Test connectivity.
Ping fro/ PC-A to PC-*.
Ping fro/ PC-A to PC-C.
Ping fro/ PC-* to PC-C.
Step 2. Confgure a local username on R1.
Configure a userna/e of Admin an1 secret ,ass6or1 of adminpa!!.
Step 3. Confgure local AAA authentication for console access on R1.
8na2+e AAA on R1 an1 configure AAA authentication for conso+e +ogin to use the +oca+ 1ata2ase.
Step 4. Confgure the line console to use the defned AAA authentication method.
8na2+e AAA on R1 an1 configure AAA authentication for conso+e +ogin to use the 1efau+t /etho1 +ist.
A++ contents are Co,yright - 1992.2012 Cisco #yste/s0 'nc. A++ rights reserve1. This 1ocu/ent is Cisco Pu2+ic 'nfor/ation. Page 2 of 3
CC&A #ecurity
Step . !erify the AAA authentication method.
4erify the user 898C +ogin using the +oca+ 1ata2ase.
Task #& 'onfigure Local AAA Aut(entication for )T* Lines on "
Step ". Confgure a named list AAA authentication method for !T# lines on R1.
Configure a na/e1 +ist ca++e1 T+L%+T,LO-I% to authenticate +ogins using +oca+ AAA.
Step $. Confgure the !T# lines to use the defned AAA authentication method.
Configure the 4T5 +ines to use the na/e1 AAA /etho1.
Step %. !erify the AAA authentication method.
4erify the Te+net configuration. Fro/ the co//an1 ,ro/,t of PC-A0 Te+net to R1.
Task $& 'onfigure Server,.ased AAA Aut(entication /sing TA'A'S0 on "#
Step &. Confgure a 'ac(up local data'ase entry called Admin.
For 2ac7u, ,ur,oses0 configure a +oca+ userna/e of Admin an1 secret ,ass6or1 of adminpa!!.
Step 1). !erify the TACACS* Server confguration.
#e+ect the TACAC#% #erver. Fro/ the Config ta20 c+ic7 on AAA an1 notice that there is a &et6or7
configuration entry for R2 an1 a )ser #etu, entry for A1/in2.
Step 11. Confgure the TACACS* server specifcs on R2.
Configure the AAA TACAC# server 'P a11ress an1 secret 7ey on R2.
Step 12. Confgure AAA login authentication for console access on R2.
8na2+e AAA on R2 an1 configure a++ +ogins to authenticate using the AAA TACAC#% server an1 if not
avai+a2+e0 then use the +oca+ 1ata2ase.
Step 13. Confgure the line console to use the defned AAA authentication method.
Configure AAA authentication for conso+e +ogin to use the 1efau+t AAA authentication /etho1.
Step 14. !erify the AAA authentication method.
4erify the user 898C +ogin using the AAA TACAC#% server.
Task 1& 'onfigure Server,.ased AAA Aut(entication /sing "ADI/S on "$
Step 1. Confgure a 'ac(up local data'ase entry called Admin.
For 2ac7u, ,ur,oses0 configure a +oca+ userna/e of Admin an1 secret ,ass6or1 of adminpa!!.
Step 1". !erify the RA+,-S Server confguration.
#e+ect the RA(')# #erver. Fro/ the Config ta20 c+ic7 on AAA an1 notice that there is a &et6or7 configuration
entry for R$ an1 a )ser #etu, entry for A1/in$.
Step 1$. Confgure the RA+,-S server specifcs on R3.
Configure the AAA RA(')# server 'P a11ress an1 secret 7ey on R$.
A++ contents are Co,yright - 1992.2012 Cisco #yste/s0 'nc. A++ rights reserve1. This 1ocu/ent is Cisco Pu2+ic 'nfor/ation. Page $ of 3
CC&A #ecurity
Step 1%. Confgure AAA login authentication for console access on R3.
8na2+e AAA on R$ an1 configure a++ +ogins to authenticate using the AAA RA(')# server an1 if not avai+a2+e0
then use the +oca+ 1ata2ase.
Step 1&. Confgure the line console to use the defned AAA authentication method.
Configure AAA authentication for conso+e +ogin to use the 1efau+t AAA authentication /etho1.
Step 2). !erify the AAA authentication method.
4erify the user 898C +ogin using the AAA RA(')# server.
Step 21. Chec( results.
5our co/,+etion ,ercentage shou+1 2e 100%. C+ic7 '(eck "esults to see fee12ac7 an1 verification of 6hich
re:uire1 co/,onents have 2een co/,+ete1.
A++ contents are Co,yright - 1992.2012 Cisco #yste/s0 'nc. A++ rights reserve1. This 1ocu/ent is Cisco Pu2+ic 'nfor/ation. Page 3 of 3
Вам также может понравиться
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3От EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Оценок пока нет
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОт EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОценок пока нет
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОт EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОценок пока нет
- ElectricCalcs R30Документ21 страницаElectricCalcs R30DSAMJ23Оценок пока нет
- Your Student Loan Account Details: For This Month's Billing CycleДокумент3 страницыYour Student Loan Account Details: For This Month's Billing CycleBryanОценок пока нет
- CCNAS v1.1 Skills-Based Assessment Hands On AnswersДокумент18 страницCCNAS v1.1 Skills-Based Assessment Hands On AnswersAdelaide-City South Australia86% (14)
- AnalyzingPISystemDataWorkbook StudentДокумент188 страницAnalyzingPISystemDataWorkbook StudentAmin Hasan AminОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routers - InstructorДокумент6 страниц3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routers - InstructorSalem TrabelsiОценок пока нет
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorДокумент35 страниц3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorSalem TrabelsiОценок пока нет
- Test Strategy DocumentДокумент10 страницTest Strategy DocumentshahidJambagiОценок пока нет
- 1) Configure AAAДокумент5 страниц1) Configure AAAMirko SapiaОценок пока нет
- Comandos Ccna SecurityДокумент26 страницComandos Ccna SecurityMarcelo Nuñez100% (1)
- CCNPv7 ROUTE Lab1-1 RIPng Instructor - I Pv6 - Router (Computing)Документ11 страницCCNPv7 ROUTE Lab1-1 RIPng Instructor - I Pv6 - Router (Computing)taco19933Оценок пока нет
- Configure AAA Authentication On Cisco RoutersДокумент4 страницыConfigure AAA Authentication On Cisco Routersrumors158Оценок пока нет
- Lab 3 - AAA Authentication On Cisco Routers - InstruccionesДокумент6 страницLab 3 - AAA Authentication On Cisco Routers - InstruccionesFelipe Andres Oyarzun QuirozОценок пока нет
- Lab 3 - AAA Authentication On Cisco Routers - InstruccionesДокумент6 страницLab 3 - AAA Authentication On Cisco Routers - InstruccionesFelipe Andres Oyarzun QuirozОценок пока нет
- CCNA Security Packet Tracer Practice SBAДокумент11 страницCCNA Security Packet Tracer Practice SBAOudome Thavong80% (5)
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routers PDFДокумент7 страниц3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routers PDFtuantuan1996Оценок пока нет
- Ccnasv1.1 Chp03 Lab-A Aaa-Radius StudentДокумент25 страницCcnasv1.1 Chp03 Lab-A Aaa-Radius StudentAngel MendozaОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersДокумент7 страниц3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routersabdelkhalek lahfaОценок пока нет
- En - Security - Chp3 - PTActA - AAA - InstructorДокумент5 страницEn - Security - Chp3 - PTActA - AAA - InstructorAntónio CavaleiroОценок пока нет
- ESwitching Basic SwitchingДокумент4 страницыESwitching Basic SwitchingJosé Madonela JúniorОценок пока нет
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFДокумент20 страниц3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFLizSocaZevallos100% (1)
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSДокумент21 страница3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSPauloОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersДокумент4 страницы3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersMahdi MaulanaОценок пока нет
- 3.6.1.2 Packet Tracer Configure AAA Authentication On Cisco RoutersДокумент4 страницы3.6.1.2 Packet Tracer Configure AAA Authentication On Cisco RouterssoufianeОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersДокумент4 страницы3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routerskhouloud BelkhodjaОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersДокумент4 страницы3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersMary KimaniОценок пока нет
- Lab 1 Configuring Basic Routing and SwitchingДокумент12 страницLab 1 Configuring Basic Routing and SwitchingratihwidyastutiОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersДокумент4 страницы3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco RoutersSandoval El MonoОценок пока нет
- E2 Lab 7 5 3 InstructorДокумент15 страницE2 Lab 7 5 3 InstructorFer CastroОценок пока нет
- Lab 1 Configurando AAA en Router Cisco (Instrucciones)Документ4 страницыLab 1 Configurando AAA en Router Cisco (Instrucciones)Cesar ValderramaОценок пока нет
- En Security Chp3 PTActA AAA StudentДокумент4 страницыEn Security Chp3 PTActA AAA StudentFnan KifluОценок пока нет
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSДокумент21 страница3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSOsman SepulvedaОценок пока нет
- Chapter 3 Lab A: Securing Administrative Access Using AAA and RadiusДокумент25 страницChapter 3 Lab A: Securing Administrative Access Using AAA and RadiusfernaleoОценок пока нет
- AAA Authentication LabДокумент4 страницыAAA Authentication LabGregoryОценок пока нет
- PT Activity 2.6.1: Packet Tracer Skills Integration ChallengeДокумент5 страницPT Activity 2.6.1: Packet Tracer Skills Integration Challengebubblybubbles1900Оценок пока нет
- Configuracion Consola Routers 1Документ6 страницConfiguracion Consola Routers 1Maria Fernanda Monroy HernandezОценок пока нет
- PT Activity: Configure AAA Authentication On Cisco Routers: Topology DiagramДокумент4 страницыPT Activity: Configure AAA Authentication On Cisco Routers: Topology DiagramZoomeeeRОценок пока нет
- Ccnas Chp4 Ptacta Acl InstructorДокумент4 страницыCcnas Chp4 Ptacta Acl InstructorSenan AlkaabyОценок пока нет
- Lab A, Securing Administrative Access Using AAA and RADIUS: TopologyДокумент13 страницLab A, Securing Administrative Access Using AAA and RADIUS: TopologyGary Giovanni Cabezas GutierrezОценок пока нет
- Configure AAA AuthenticationДокумент6 страницConfigure AAA AuthenticationHanane EsiОценок пока нет
- CCNAS - Chp2 - PTActA - Syslog-SSH-NTP - InstructorДокумент5 страницCCNAS - Chp2 - PTActA - Syslog-SSH-NTP - InstructorAziz LondonОценок пока нет
- How To Recover The Password For Cisco 2900 Integrated Services RouterДокумент8 страницHow To Recover The Password For Cisco 2900 Integrated Services RouterCassandra ShafferОценок пока нет
- Ccnas Chp2 Ptacta Syslog-Ssh-Ntp StudentДокумент4 страницыCcnas Chp2 Ptacta Syslog-Ssh-Ntp StudentDaniel PatelОценок пока нет
- Comandos Ccna SecurityДокумент26 страницComandos Ccna SecurityRobtech opsОценок пока нет
- DRSEnt PT Practice SBA OSPF PDFДокумент5 страницDRSEnt PT Practice SBA OSPF PDFHarol Matias RamosОценок пока нет
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorДокумент27 страниц3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorAlexander Lapo Cordova0% (1)
- Sic PRACTICALДокумент80 страницSic PRACTICALbhlmallahОценок пока нет
- IT NE 2005 LAB 4 - Securing Administrative Access Using AAA and RADIUS.Документ16 страницIT NE 2005 LAB 4 - Securing Administrative Access Using AAA and RADIUS.ujjwal poudelОценок пока нет
- CCNAS Chp4 PTActC Zone Based Policy Firewall InstructorДокумент5 страницCCNAS Chp4 PTActC Zone Based Policy Firewall InstructorilhamdaniОценок пока нет
- Configuring Frame RelayДокумент5 страницConfiguring Frame RelayArdit MeziniОценок пока нет
- CCNASv1.1 Chp10 Lab-A ASA-FW-CLI StudentДокумент24 страницыCCNASv1.1 Chp10 Lab-A ASA-FW-CLI StudentLan WanОценок пока нет
- Ccnasv1.1 Chp10 Lab-F Asa5510-Fw-Asdm InstructorДокумент54 страницыCcnasv1.1 Chp10 Lab-F Asa5510-Fw-Asdm Instructormyropie100% (1)
- CCNASv1.1 Chp09 Lab-A Sec-Pol StudentДокумент32 страницыCCNASv1.1 Chp09 Lab-A Sec-Pol Studentluisdg93Оценок пока нет
- MIT 504 - Lab - 3 Configuring Basic Router Settings With IOS CLI 11Документ11 страницMIT 504 - Lab - 3 Configuring Basic Router Settings With IOS CLI 11umang patnaikОценок пока нет
- Oracle Server NameДокумент2 страницыOracle Server Namebanala.kalyanОценок пока нет
- Week 5 - Skills ActivityДокумент11 страницWeek 5 - Skills ActivitykonoweОценок пока нет
- Ewan Ptact 5 2 8Документ6 страницEwan Ptact 5 2 8Muhammad HudzaifahОценок пока нет
- Apache Web Server: Service Profile of ApacheДокумент4 страницыApache Web Server: Service Profile of ApacheTushar BotuwarОценок пока нет
- 3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routers AnswersДокумент11 страниц3.6.1.2 Packet Tracer - Configure AAA Authentication On Cisco Routers AnswersSultan100% (3)
- 7.2.6 Packet Tracer - Configure Local AAA For Console and VTY AccessДокумент3 страницы7.2.6 Packet Tracer - Configure Local AAA For Console and VTY AccessGISTSalehuddinОценок пока нет
- Configure Server-Based Authentication With TACACS+ and RADIUSДокумент23 страницыConfigure Server-Based Authentication With TACACS+ and RADIUSestebanОценок пока нет
- Campus Recruiting Timeline: For Accounting ST UdentsДокумент8 страницCampus Recruiting Timeline: For Accounting ST Udentsalb3rtlinОценок пока нет
- ISM210 Midterm Study Guide Winter 2014Документ1 страницаISM210 Midterm Study Guide Winter 2014alb3rtlinОценок пока нет
- CNS 394 - Unit 2: Information Ethics and Codes of ConductДокумент24 страницыCNS 394 - Unit 2: Information Ethics and Codes of Conductalb3rtlinОценок пока нет
- HW1 Design Critique IДокумент2 страницыHW1 Design Critique Ialb3rtlinОценок пока нет
- Syllabus Acc 101-503, 504Документ4 страницыSyllabus Acc 101-503, 504alb3rtlinОценок пока нет
- Asdf Class 3Документ66 страницAsdf Class 3alb3rtlinОценок пока нет
- TDC-478 Class 1Документ66 страницTDC-478 Class 1alb3rtlinОценок пока нет
- CNS 320 Week1 LectureДокумент63 страницыCNS 320 Week1 Lecturealb3rtlinОценок пока нет
- 2 - TraceifaceДокумент4 страницы2 - Traceifacealb3rtlinОценок пока нет
- Backtrack Supplement 1Документ6 страницBacktrack Supplement 1alb3rtlinОценок пока нет
- Rosen Et Al 2007Документ15 страницRosen Et Al 2007alb3rtlinОценок пока нет
- CNS 320 Week5 LabДокумент13 страницCNS 320 Week5 Labalb3rtlinОценок пока нет
- Week8 - Group DevelopmentДокумент7 страницWeek8 - Group Developmentalb3rtlinОценок пока нет
- Week2 - Group StructuringДокумент5 страницWeek2 - Group Structuringalb3rtlinОценок пока нет
- 416 Bi Publisher Blob ImageДокумент5 страниц416 Bi Publisher Blob Imagesaikumar padakantiОценок пока нет
- Features of OOPДокумент5 страницFeatures of OOPManish RaneОценок пока нет
- SDCC Compiler User GuideДокумент123 страницыSDCC Compiler User GuideDeepraj BhujelОценок пока нет
- RECRUITMENT AND SELECTION Process Index by MaheshДокумент5 страницRECRUITMENT AND SELECTION Process Index by MaheshUma Mahesh100% (1)
- Ug TRG Prog Fall 2019Документ17 страницUg TRG Prog Fall 2019Muhaamad Haseeb KhokharОценок пока нет
- C Programming Lab Manual by Om Prakash MahatoДокумент7 страницC Programming Lab Manual by Om Prakash MahatoAnonymous 4iFUXUTОценок пока нет
- Bca 204Документ2 страницыBca 204api-3782519Оценок пока нет
- Performance Tuning Waits QueuesДокумент98 страницPerformance Tuning Waits QueuesalexcadimaОценок пока нет
- Purchase Order ProcessingДокумент260 страницPurchase Order Processingjackjill1021Оценок пока нет
- Yoni Miller - Invariance-PrincipleДокумент4 страницыYoni Miller - Invariance-PrincipleElliotОценок пока нет
- GX Work 2Документ9 страницGX Work 2Hanafi HariyantoОценок пока нет
- A Quick and Simple Guide To Crontab Usage - CrontabrocksДокумент3 страницыA Quick and Simple Guide To Crontab Usage - CrontabrocksbaazigarОценок пока нет
- Event LinesДокумент19 страницEvent LinesMohamed AwadОценок пока нет
- PerfectDisk Statistics HPENVYLEAPMOTIO Windows C 2017.06.29 06.03PMДокумент5 страницPerfectDisk Statistics HPENVYLEAPMOTIO Windows C 2017.06.29 06.03PMVlad MusicОценок пока нет
- DS - Unit 3 (PPT 1.1)Документ18 страницDS - Unit 3 (PPT 1.1)19BCA1099PUSHP RAJОценок пока нет
- Chinese Gender Predictor V9Документ3 страницыChinese Gender Predictor V9MOHAN SОценок пока нет
- Peak FitДокумент4 страницыPeak FitPrianurraufikachmadОценок пока нет
- Hightech Product Export Promotion SchemeДокумент5 страницHightech Product Export Promotion SchemeMalay9099Оценок пока нет
- WinForms TrueDBGridДокумент362 страницыWinForms TrueDBGridgusvader100% (1)
- BIM Roadmap - Cheng Tai FattДокумент33 страницыBIM Roadmap - Cheng Tai Fattusernaga84Оценок пока нет
- Bible HistoryДокумент81 страницаBible Historyram ganeshОценок пока нет
- The Adventures of Robinson CrusoeДокумент495 страницThe Adventures of Robinson CrusoeBozica Zeljko MicanovicОценок пока нет
- Dl06 Mighty MicroДокумент1 страницаDl06 Mighty MicroLeonardo Moreira LeiteОценок пока нет
- Unit 2 CST Review InequalitiesДокумент2 страницыUnit 2 CST Review InequalitiesMisterLemusОценок пока нет
- Bond Graph Modeling and Simulation of A FullДокумент6 страницBond Graph Modeling and Simulation of A FullAnirban MitraОценок пока нет
- Class 2 Introduction PythonДокумент2 страницыClass 2 Introduction PythonkunalaОценок пока нет