Академический Документы
Профессиональный Документы
Культура Документы
Research Report
Загружено:
Elizabeth Aliaz0 оценок0% нашли этот документ полезным (0 голосов)
20 просмотров8 страницwitricity
Авторское право
© © All Rights Reserved
Доступные форматы
PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документwitricity
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
20 просмотров8 страницResearch Report
Загружено:
Elizabeth Aliazwitricity
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 8
Introduction
Wireless electricity or witricity is the transfer of electric energy or power over a
distance without the use of wires. In order for the energy to be transferred safely coupled
resonators are used. Coupled resonators are two objects of the same resonant frequency
that exchange energy efficiently without much leakage. Minimizing energy leakage is
very important because the goal is to have as much energy as possible be transferred from
one object to another. The first experiment to successfully wirelessly transfer energy
consisted of two copper coils that were each a self-resonant system. One of the coils was
connected to an AC power supply and acted as the resonant source. The second coil acted
as the resonant capturing device and was connected to a 60-watt light bulb. The power
source and the capturing device were about 2.5 meters apart and the light bulb was able
to light up. This technology is very useful both in everyday life and for military usage.
An example of a military usage includes sensors on a battlefield that can detect motion.
The sensors would send their information to a base station and the soldiers can use this
information to sense possible attacks. This could give them enough time to move or keep
safe. This would be very beneficial, however; replacing batteries in the sensors can be
dangerous and time consuming. Using witricity there would be no need to replace
batteries because energy could be transferred from one sensor to another. Once a sensor
has reached a predetermined threshold it would shout for help from a neighboring
sensor. If the neighboring sensor had above the determined threshold it would transfer the
necessary amount of energy to the sensor in need. An optimization model has been
created through researching this topic. One optimization solution is as follows; a matrix
represents the amount of energy to transfer from all WiTricity devices to all WiTricity
devices, which combines multiple power transmissions with multi-hop WiTricity
charging as a response to multiple charging requests. Current research is focusing on
solving various optimization problems on WiTricity charging protocols in wireless sensor
networks. Through the use of the CPLEX program a java simulation will be created in
order to find an optimal way to transfer energy with minimal energy leakage.
Questions to be Addressed
This research is going to address the following questions and hypotheses. What
kinds of optimization problems will be useful to solve in the wireless electricity charging
protocol for wireless sensor networks? How each of the optimization problems can be
modeled using mixed integer programming? How each of the optimization models can be
solved using an optimization tool such as CPLEX? The following assumptions must be
made to further investigate the proposed hypotheses: Each sensor has a wireless sensor in
the device to capture and send wireless electricity. The wireless sensor network is a
multi-hop wireless sensor network; the sensors are expected to be an end node as well as
and intermediate node. Sensors use multi-directional transmission and all the sensors
within the transmission range can be reachable. Sensors will use adjustable transmission
power so that the number of reachable neighbors can be changed for a static network
topology and energy consumption of a sensor can be managed.
Conditions
In order for witricity charging to be able to be used there are some conditions that
are necessary. The first condition necessary is that charging must be able to occur
through physical objects. If the witricity cannot be passed through physical objects then
the charging can only occur in a perfect unobstructed environment. This is not realistic
because there are objects all around us that can interfere with the transmission of the
energy. Research thus far has found that witricity can be transmitted through wood,
gypsum wallboard, plastics, textiles, glass, brick, and concrete. The second condition
necessary is that charging must be safe and not pose any sort of threat or safety hazard to
humans or animals. Since this type of energy transfer is non-radioactive it is safe for
humans and animals. The third condition necessary is that witricity charging must be able
to provide electricity to remote objects without the use of wires. Therefore, the energy
must be transferable from the transmitter to the capturing device over a certain distance.
For example, traditional magnetic induction that is used in an electric toothbrush needs
physical contact, or their needs to be a fairly short distance between the energy
transmitter and the energy receiver. Thus, magnetic induction is not a suitable technology
for witricity transfer. According to WiTricity, a company that has developed the wireless
electricity technology, the distance between the power source and the capturing device
can range from a centimeter to several meters between the power source and the
capturing device, depending on the size of the device, how efficient the transfer is
desired, and the amount of power that needs to be transferred. According to a team of
researchers at MIT, two resonant objects of the same resonant frequency tend to
exchange energy more efficiently while dispersing little energy to off-resonant objects,
and a power transfer can be multi-directional and efficient. The team also calculated the
efficiency of wireless power transfer using strong coupled magnetic resonators to be the
amount of useable electrical energy at the power receiving device over the amount of
energy sent by the power sources. The fourth condition necessary is that the witricity is
able to transfer a meaningful amount of energy, or else it would defeat the purpose of the
energy transfer. WiTrcity.com states their technology is able to transfer energy ranging
from miliwatts to several kilowatts of power. The fifth condition necessary is that the
witricity technology should not use a lot of memory. In order for a program to be loaded
on the sensors it cannot take a lot of memory, since the sensors have limited memory
capacity. The final condition necessary is that the witricity charging technology should be
affordable to be able to be apart of a sensor.
Parameters
Witricity charging protocols have many parameters. The first parameter is the
degree of charging. There are three different degrees in which a sensor can be charged.
The first is perfect charging, this type of charging charges all the batteries of the sensors
until they are all full. This is achieved by using an external power source such as a base
station or using designated power supply devices. The second way is limited charging,
this type of charging charges the batteries of the sensors that are at or above a certain
threshold. It could have an external power source, but if it does not it will try to maximize
the network lifetime without creating a blind spot in the wireless sensor network. The
network lifetime is measured by the amount of data transmissions necessary until the
WSN has its first blind spot or until the WSN has a given percentage of the WSN field in
a blind spot. The third type of charging is no charging this is a wireless sensor network
without charging.
The second parameter is the type of charging algorithm. There are two different
charging algorithms; distributed and centralized. The distributed algorithm calculates the
amount of energy that needs to be transferred between a node and its direct neighbor
based on information received from its direct neighbor. The centralized algorithm
calculates the amount of energy that needs to be transferred between all the sensors in the
network. The amount of energy that needs to be transferred is represented in a matrix. In
a two-dimensional WSN with n sensors, the matrix is n x n for a three-dimensional WSN
with n sensors the matrix is n x n x n.
The third parameter is the type of power supply. There is a base station and either
all of the sensors or some of the sensors are indicated as a percentage between 0 and
100%. It also allows the base station to select a set of certain sensors. There are also
designated power supply devices that are non-sensor power supply devices that are
deployed in the WSN. The next parameter is the type of power capturing device. There is
a base station and the sensors are indicated as percentages too, the difference is the
devices and base station might be a power capturing device or act as an intermediate
power relay device. Another parameter is the mobility of the base station. The base
station can either be stationary or mobile which has a velocity and direction. The mobility
of designated power supply devices is another parameter. The power supply devices can
either be stationary or mobile also with velocity and direction, or a combination of both.
The mobility of the sensors is another parameter. The sensors can be stationary, mobile
with velocity and direction, or a combination of both.
REFEREED JOURNAL, CONFERENCE PAPERS, and PRESENTATIONS
Catherine Greene, Bretny Khamphavong, Chloe Norris, Nancy White, and Hwajung Lee,
Diversity in Computing, Richard Tapia Conference 2011, San Francisco, California,
April 3-6, 2011.
Catherine Greene, Bretny Khamphavong, Chloe Norris, Nancy White, and Hwajung Lee,
Multi-Hop Wireless Electricity Charging Protocol in Wireless Sensor
Networks, 20th Annual Undergraduate/Graduate Student Engagement Forum, Radford
University, Radford, Virginia, April 19-21, 2011.
Jon Carter Farmer, Trent Lugar, and Hwajung Lee, Computer Aided Rescue Systems
with Mobile Robot Agents, Big South Undergraduate Research Symposium, Radford,
Virginia, April 9~10, 2010. [Abstract and Presentation], Undergraduate Research
Jon Carter Farmer and Hwajung Lee, Wireless Sensor Networks without Energy
Constraint using WiTricity, Big South Undergraduate Research Symposium, Radford,
Virginia, April 9~10, 2010. [Abstract and Presentation], Undergraduate Research
Hwajung Lee, Optimization Issues under a New Paradigm on Wireless Sensor Network
(WSN) Research: WSN with Witricity, the 2009 US Korea Conference on Science,
Technology and Entrepreneurship, Raleigh, North Carolina, July 16~19, 2009. [Abstract
and Presentation]
Eileen Balci, Stephanie Reese, Shannon Seefeld, and Hwajung Lee, Rescue Support
System with Wireless Sensor Networks in an Unsafe Territory, the 18th
Undergraduate/Graduate Student Engagement Forum, Radford University, April 20-23,
2009. [Abstract and Presentation], Undergraduate Research
Shawn Dixon and Hwajung Lee, Executing 3rd Party Code on iPod & iPhone through
Jail breaking, the 18th Undergraduate/Graduate Student Engagement Forum, Radford
University, April 20-23, 2009. [Abstract and Presentation], Undergraduate Research
Eric Ballance and Hwajung Lee, Proactive Information Delivery System in Ubiquitous
Networks, International Journal of Hybrid Information Technology, 2009,
Undergraduate Research
Hwajung Lee, PKI Vulnerability and x-Cryptography in Grid Computing Networks,
the 2008 International Conference on High Performance Computing, Networking and
Communication Systems (HPCNCS-08), Orlando, Florida, July 7-10 2008, Invited
Paper
Eric Ballance and Hwajung Lee, Developing Proactive Information Delivery System
through Bluetooth in Ubiquitous Networks, the International Conference on Multimedia
and Ubiquitous Engineering (MUE2008), IEEE Computer Society, Seoul Korea, April
24-26, 2008, Undergraduate Research
Eric Ballance and Hwajung Lee, On-demand Awareness through Ubiquitous
Computing using Bluetooth and WI-FI, 15th Annual UG/G Student Engagement Forum,
Radford University, April 16-18, 2008. [Abstract and Presentation], Undergraduate
Research
Dennis P. Groth,,Betty Lauer, Helen H. Hu, and Hwajung Lee, Improving Computer
Science Diversity through Summer Camps, ACM SIGCSE 2008, Portland, Oregon,
March 12-15, 2008. Proposal, Presentation, and Panel
Eric Ballance, Hwajung Lee, and Joe Derrick, Investigating Ubiquitous Computing
Through the Use of IR, Wi-Fi, and Bluetooth Technologies to Enhance Microsoft
Onenote for the Tablet PC, the 22nd National Conference on Undergraduate Research
(NCUR 2008), Salisbury University, Maryland, April 10-12, 2008, [Abstract and
Presentation], Undergraduate Research
James Jones and Hwajung Lee, Application-Oriented and Hardware-Constraint-
Oriented Routing Protocol Selection in Mobile Ad-hoc Networks, the 22nd National
Conference on Undergraduate Research (NCUR 2008), Salisbury University, Maryland,
April 10-12, 2008, [Abstract and Presentation], Undergraduate Research
H. Lee, Distributed Reconfiguration Algorithm in Survivable Grid Computing
Networks, Abstract and Presentation in Proc. of US-Korea Conference on Information
Technology 2007, Reston, Virginia, August 9~12, 2007
H. Lee, Uninterruptible Reconfiguration for Dynamic Resource Management in a Grid
Computing Network against a Single Link Attack/Failure, Proc. of International
Conference on High Performance Computing, Networking and Communication Systems,
Orlando, FL, July 9-12, 2007
H. Lee and D. Allen, Dynamic Reconfiguration of User Controlled Lightpath
Management in Survivable Grid Computing Network against a Single Link
Attack/Failure, Abstract and Poster, TeraGrid 2007 Conference, Madison, Wisconsin,
June 4-8, 2007, Undergraduate Research
H. Lee, Quality of Service in Grid Computing Network, Abstract and Presentation in
Proc. of US-Korea Conference on Communication and Networking Technology 2007,
Teaneck, New Jersey, August 10-13, 2006.
H. Lee, Resilient Topology Control using Energy-balanced Sleeping Sensors in
Multihop Wireless Sensor Network using Fixed Transmission Power, Proc. of the 10th
World Multiconference on Systemics, Cybernetics and Informatics (WMSCI 2006),
Orlando, FL, July 16-19, 2006
H. Lee, SEEMLESS: Distributed Algorithm for Topology Control of Survivable Energy
Efficient Multihop Wireless Sensor Networks Using Adjustable Transmission Power,
Proc. Sixth ACIS International Conference on Software Engineering, Artificial
Intelligence, Networking, and Parallel/Distributed Computing (SNPD05), Towson,
Maryland, May 2005.
N. Yoo, H. Lee, and H. Choi, XML-BASED Information Assurance Vulnerability
Management for System Safety, the 22nd International System Safety Conference (ISSC
2004), Providence Rhode Island, 2 - 6 August, 2004.
N. Yoo, H. Lee, and H. Choi, An XML-Based Impact Analysis Using Security
Management With IAVN, The 2004 International Conference on Security and
Management (SAM'04), Las Vegas, Nevada, June 21-24, 2004.
H. Lee, H. Choi, S. Subramaniam, and H.-A. Choi, Survival Embedding of Logical
Topology in WDM Ring Networks, to appear in Journal of Information Science, Special
Issue on Photonics, Networking and Computing, Elsevier Science, Inc., January 2003.
H. Lee, H. Choi, S. Subramaniam, and H.-A. Choi, Preserving Survivability During
Logical Topology Reconfiguration in WDM Ring Networks, Proc. 31st ICPP Workshop
on Optical Networks, IEEE Computer Society Press, Vancouver Canada, August 2002.
I nvited Paper.
H. Lee, H. Choi, and H.-A. Choi, Reconfiguration of Survivable Logical Topologies in
WDM Ring Networks, Proc. 36th Conference of Information Science and Systems
(CISS), Princeton University, March 2002.
H. Lee, H. Choi, S. Subramaniam, and H.-A. Choi, Survival Embedding of Logical
Topology in WDM Ring Networks, Proc. Symposium on Photonics, Networking and
Computing, The 6th Joint Conference on Information Sciences (JCIS), Duke University,
March 2002.
H. Lee, H. Choi, S. Subramaniam, and H.-A. Choi, Survival Logical Topology Design
in WDM Optical Ring Networks, Proc. 39th Allerton conference on communications,
control, and computing, Univ. of Illinois at Urbana-Champaign, Oct. 2001. I nvited
Paper.
H. Choi, H. Lee, and H.-A. Choi, Design Issue on IP over WDM Networks, Proc. US-
Korea Conference on Science, Technology and Entrepreneurship 2001, Boston, August
10-12, 2001.
H. Lee, H. Choi, and H.-A. Choi, Restoration in IP over WDM Optical Networks,
Proc. 30th ICPP Workshop on Optical Networks, IEEE Computer Society Press, pages
263-268, September 2001. I nvited Paper.
H. Lee, H. Choi, and H.-A. Choi, IP Restoration on WDM Optical Networks, Proc.
35th Conference of Information Science and Systems (CISS), vol 1, page 268, The Johns
Hopkins University, March 2001.
Вам также может понравиться
- 1B5B9BDB 12345678 Abcdef90 657483FFДокумент1 страница1B5B9BDB 12345678 Abcdef90 657483FFpretty15Оценок пока нет
- DC and Transient Characteristics TableДокумент1 страницаDC and Transient Characteristics Tablepretty15Оценок пока нет
- Seminor TopicsДокумент24 страницыSeminor Topicspretty15Оценок пока нет
- Kuhns Wustl SummaryofcДокумент51 страницаKuhns Wustl SummaryofcSyedОценок пока нет
- Witricity 2 IeeeДокумент10 страницWitricity 2 Ieeepretty15Оценок пока нет
- Forbidden Items ListДокумент2 страницыForbidden Items Listpretty15Оценок пока нет
- How Night Vision WorksДокумент10 страницHow Night Vision Workspretty15Оценок пока нет
- Witricity 2 IeeeДокумент10 страницWitricity 2 Ieeepretty15Оценок пока нет
- IEEEpaper Wireless Charging of Mobile Phone Using Microwaves 2014 02-16-14!50!20 627Документ5 страницIEEEpaper Wireless Charging of Mobile Phone Using Microwaves 2014 02-16-14!50!20 627pretty15Оценок пока нет
- Us 7825543Документ41 страницаUs 7825543Paco PascuaОценок пока нет
- IEEEpaper Wireless Charging of Mobile Phone Using Microwaves 2014 02-16-14!50!20 627Документ5 страницIEEEpaper Wireless Charging of Mobile Phone Using Microwaves 2014 02-16-14!50!20 627pretty15Оценок пока нет
- Ch5 DigitalДокумент177 страницCh5 DigitalSaba WasimОценок пока нет
- Ch5 AnalogДокумент104 страницыCh5 Analog15prettyОценок пока нет
- 1300 Math Formulas - Alex SvirinДокумент338 страниц1300 Math Formulas - Alex SvirinMirnesОценок пока нет
- Frequency Spectrum GuideДокумент2 страницыFrequency Spectrum GuideSachin GhodkeОценок пока нет
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (265)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (119)
- ICT2219 Intro to IT Test Multiple ChoiceДокумент5 страницICT2219 Intro to IT Test Multiple ChoiceJIN TEHОценок пока нет
- 5g Vision DocumentДокумент37 страниц5g Vision DocumentPramaОценок пока нет
- Advanced AnalyticsДокумент14 страницAdvanced AnalyticsPraveen B ChandranathОценок пока нет
- Gapco Tanzania Limited: Industrial Practical Training Final ReportДокумент23 страницыGapco Tanzania Limited: Industrial Practical Training Final ReportDady Dadee AmryОценок пока нет
- GTU M.E. Dissertation ScheduleДокумент160 страницGTU M.E. Dissertation Schedule113314Оценок пока нет
- B7 Comp Tsol 2 1Документ4 страницыB7 Comp Tsol 2 1Amatu AbukariОценок пока нет
- Si5395 94 92 FamilyДокумент237 страницSi5395 94 92 Familythe_citizen89Оценок пока нет
- CYS-503 Lab Manual Analyzes Network SecurityДокумент20 страницCYS-503 Lab Manual Analyzes Network SecurityZahida PerveenОценок пока нет
- DC/DC Converters: Isolated Point-of-Load Bus Converters Processor Support Memory SupportДокумент36 страницDC/DC Converters: Isolated Point-of-Load Bus Converters Processor Support Memory SupportРуслан МайбородаОценок пока нет
- Unit 2 - Advance Computer Networks - WWW - Rgpvnotes.inДокумент21 страницаUnit 2 - Advance Computer Networks - WWW - Rgpvnotes.inprince keshriОценок пока нет
- Internal Test - II II Year RT (NMEC)Документ4 страницыInternal Test - II II Year RT (NMEC)P.Jermi Arockia PravinОценок пока нет
- 6117 SAF Package-RevA MДокумент4 страницы6117 SAF Package-RevA MIbrahim Sabry RehabОценок пока нет
- To Rectifiers: Micronote Series 301Документ1 страницаTo Rectifiers: Micronote Series 301Usman AslamОценок пока нет
- Bias Controller of Mach-Zehnder Modulator For Electro-Optic Analog-to-Digital ConverterДокумент10 страницBias Controller of Mach-Zehnder Modulator For Electro-Optic Analog-to-Digital ConverterJorge GuerreroОценок пока нет
- Presentation 5162 1523282068 PDFДокумент87 страницPresentation 5162 1523282068 PDFFreddy BeltranОценок пока нет
- Service Manual: MT1192 19" Color TelevisionДокумент54 страницыService Manual: MT1192 19" Color TelevisionHamilton MoranОценок пока нет
- Data Structure and Input ProcessingДокумент13 страницData Structure and Input ProcessingPrabakar DОценок пока нет
- Motherboard Block DiagramДокумент9 страницMotherboard Block DiagramJay Zala0% (1)
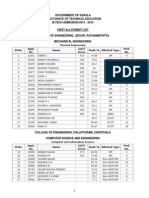
- Mtech 2015 First Allotment ListДокумент57 страницMtech 2015 First Allotment ListArjun T PОценок пока нет
- Cisco Residential Signal Box USC3331Документ8 страницCisco Residential Signal Box USC3331sssОценок пока нет
- Introduction To CourseДокумент17 страницIntroduction To CoursefarooqbhuttoОценок пока нет
- Lab NetworkДокумент99 страницLab Networkahmed raedОценок пока нет
- Sophos Superintendencia de Electricidad CcsДокумент4 страницыSophos Superintendencia de Electricidad Ccsingeduardo23Оценок пока нет
- The Role of Mist in IotДокумент21 страницаThe Role of Mist in IotldmoОценок пока нет
- HCIA H35-660: True of FalseДокумент24 страницыHCIA H35-660: True of FalseRudi Arif candra100% (3)
- Two Ray Path Loss ModelДокумент35 страницTwo Ray Path Loss ModelAnushka PandeyОценок пока нет
- Sony PJ 410 ManualДокумент36 страницSony PJ 410 Manualpangkalandatapariaman padangОценок пока нет
- Pendidikan Agama Islam Dan Industri 4.0Документ21 страницаPendidikan Agama Islam Dan Industri 4.0puji kurniaОценок пока нет
- Xpol 1710 2170Mhz 65° 17.8dbi Adjustable Electrical Downtilt Antenna, Manual or by Optional Rcu (Remote Control Unit)Документ1 страницаXpol 1710 2170Mhz 65° 17.8dbi Adjustable Electrical Downtilt Antenna, Manual or by Optional Rcu (Remote Control Unit)ИгорьОценок пока нет
- RX-397 Block Diagram and Operation SchematicДокумент5 страницRX-397 Block Diagram and Operation SchematicJosep Almirall perezОценок пока нет