Академический Документы
Профессиональный Документы
Культура Документы
Cisco Checklist Configuring Cisco Equipment
Загружено:
Ryan Rosaldo0 оценок0% нашли этот документ полезным (0 голосов)
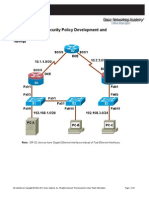
32 просмотров6 страницThis checklist is to be used to audit an environment that includes Cisco routers. The checklist provides the technical security considerations during an audit and excludes manual considerations like physical security considerations.
The checklist excludes the security considerations for Cisco switches.
Prior to using this checklist consideration should be given to the following:
• Location of the router: It is important to ascertain the location of the router in the network as this has an impact on certain security elements e.g. disabling SSL service is not appropriate when the router is routing traffic to an external web server.
• Practicality of security recommendations: The checklist lists numerous security considerations, which may not be practical as it could hinder the performance of the network. It is important to ascertain the risk allocated to not having certain security elements and whether management has decided to accept the risk of not having these elements.
• Mitigating controls: The audit of Cisco routers cannot be performed in a vacuum. The auditor needs to consider the impact of security in other elements e.g. firewalls, host operating system, etc. A weakness in security at the router level may be mitigated by a strong control at the firewall level e.g. filtering out ports which are not 80,23, etc.
• Interoperability: In circumstances when the router uses the functionality of other elements in the environment e.g. a syslog server to log events from cisco routers or an SNMP management station, the auditor must review the security over the other elements. This checklist does not provide the security considerations for these other elements.
• Applicability of security considerations: This checklist attempts to provide a complete listing of all security elements to consider during an audit of Cisco router, however in some environments certain elements may not be applicable e.g. in a windows environment it is not necessary to be concerned about filtering out rlogin or ssh services.
• Network servers: This checklist does not include security considerations for the operating system running TACACS or RADIUS.
1. Ensure that all maintenance on the router is done while logged on locally. Ensure that inbound Telnet is disabled as well as the Telnet listener.
If Telnet is used to maintain the router ensure that access is granted only to specific workstations on the internal network side of the router.
Ensure that all maintenance services that would allow access from outside the network are disabled or restricted.
Ensure that passwords are used where possible.
Ensure that the “service password encryption” command is used on all type 7 passwords.
Ensure that MD5 encryption is used on the “Privileged EXEC Mode” password. Enable secret command.
Ensure that the service password-encryption command is enabled such that when passwords are displayed with the more system:running-config command, they appear in encrypted form.
Ensure that an EXEC password is added to AUX and Console ports.
Ensure that RIP and OSPF protocol on the internet interface both inbound and outbound is stopped.
Ensure that CDP is disabled on all interfaces.
Ensure that a login banner is enabled with the appropriate legal notice. (banner login command) Ensure that the banner contains no information about the router, it’s name, model, software it’s running, or who owns it.
Ensure that SNMP is disabled if possible.
2. Ensure that any modem or network device that gives access to the console port must be secured. For a modem, user should provide a password for dial up access.
Ensure that the transport input none command is applied to any asynchronous or modem line that shouldn’t be receiving connections from network users.
Ensure that the same modem is not used for both dial in and dial out and that reverse telnet connections are not allowed on dial in lines.
For VTY lines ensure that it is configured to only accept connections with
Оригинальное название
Cisco Checklist configuring cisco equipment
Авторское право
© © All Rights Reserved
Доступные форматы
DOC, PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документThis checklist is to be used to audit an environment that includes Cisco routers. The checklist provides the technical security considerations during an audit and excludes manual considerations like physical security considerations.
The checklist excludes the security considerations for Cisco switches.
Prior to using this checklist consideration should be given to the following:
• Location of the router: It is important to ascertain the location of the router in the network as this has an impact on certain security elements e.g. disabling SSL service is not appropriate when the router is routing traffic to an external web server.
• Practicality of security recommendations: The checklist lists numerous security considerations, which may not be practical as it could hinder the performance of the network. It is important to ascertain the risk allocated to not having certain security elements and whether management has decided to accept the risk of not having these elements.
• Mitigating controls: The audit of Cisco routers cannot be performed in a vacuum. The auditor needs to consider the impact of security in other elements e.g. firewalls, host operating system, etc. A weakness in security at the router level may be mitigated by a strong control at the firewall level e.g. filtering out ports which are not 80,23, etc.
• Interoperability: In circumstances when the router uses the functionality of other elements in the environment e.g. a syslog server to log events from cisco routers or an SNMP management station, the auditor must review the security over the other elements. This checklist does not provide the security considerations for these other elements.
• Applicability of security considerations: This checklist attempts to provide a complete listing of all security elements to consider during an audit of Cisco router, however in some environments certain elements may not be applicable e.g. in a windows environment it is not necessary to be concerned about filtering out rlogin or ssh services.
• Network servers: This checklist does not include security considerations for the operating system running TACACS or RADIUS.
1. Ensure that all maintenance on the router is done while logged on locally. Ensure that inbound Telnet is disabled as well as the Telnet listener.
If Telnet is used to maintain the router ensure that access is granted only to specific workstations on the internal network side of the router.
Ensure that all maintenance services that would allow access from outside the network are disabled or restricted.
Ensure that passwords are used where possible.
Ensure that the “service password encryption” command is used on all type 7 passwords.
Ensure that MD5 encryption is used on the “Privileged EXEC Mode” password. Enable secret command.
Ensure that the service password-encryption command is enabled such that when passwords are displayed with the more system:running-config command, they appear in encrypted form.
Ensure that an EXEC password is added to AUX and Console ports.
Ensure that RIP and OSPF protocol on the internet interface both inbound and outbound is stopped.
Ensure that CDP is disabled on all interfaces.
Ensure that a login banner is enabled with the appropriate legal notice. (banner login command) Ensure that the banner contains no information about the router, it’s name, model, software it’s running, or who owns it.
Ensure that SNMP is disabled if possible.
2. Ensure that any modem or network device that gives access to the console port must be secured. For a modem, user should provide a password for dial up access.
Ensure that the transport input none command is applied to any asynchronous or modem line that shouldn’t be receiving connections from network users.
Ensure that the same modem is not used for both dial in and dial out and that reverse telnet connections are not allowed on dial in lines.
For VTY lines ensure that it is configured to only accept connections with
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате DOC, PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
32 просмотров6 страницCisco Checklist Configuring Cisco Equipment
Загружено:
Ryan RosaldoThis checklist is to be used to audit an environment that includes Cisco routers. The checklist provides the technical security considerations during an audit and excludes manual considerations like physical security considerations.
The checklist excludes the security considerations for Cisco switches.
Prior to using this checklist consideration should be given to the following:
• Location of the router: It is important to ascertain the location of the router in the network as this has an impact on certain security elements e.g. disabling SSL service is not appropriate when the router is routing traffic to an external web server.
• Practicality of security recommendations: The checklist lists numerous security considerations, which may not be practical as it could hinder the performance of the network. It is important to ascertain the risk allocated to not having certain security elements and whether management has decided to accept the risk of not having these elements.
• Mitigating controls: The audit of Cisco routers cannot be performed in a vacuum. The auditor needs to consider the impact of security in other elements e.g. firewalls, host operating system, etc. A weakness in security at the router level may be mitigated by a strong control at the firewall level e.g. filtering out ports which are not 80,23, etc.
• Interoperability: In circumstances when the router uses the functionality of other elements in the environment e.g. a syslog server to log events from cisco routers or an SNMP management station, the auditor must review the security over the other elements. This checklist does not provide the security considerations for these other elements.
• Applicability of security considerations: This checklist attempts to provide a complete listing of all security elements to consider during an audit of Cisco router, however in some environments certain elements may not be applicable e.g. in a windows environment it is not necessary to be concerned about filtering out rlogin or ssh services.
• Network servers: This checklist does not include security considerations for the operating system running TACACS or RADIUS.
1. Ensure that all maintenance on the router is done while logged on locally. Ensure that inbound Telnet is disabled as well as the Telnet listener.
If Telnet is used to maintain the router ensure that access is granted only to specific workstations on the internal network side of the router.
Ensure that all maintenance services that would allow access from outside the network are disabled or restricted.
Ensure that passwords are used where possible.
Ensure that the “service password encryption” command is used on all type 7 passwords.
Ensure that MD5 encryption is used on the “Privileged EXEC Mode” password. Enable secret command.
Ensure that the service password-encryption command is enabled such that when passwords are displayed with the more system:running-config command, they appear in encrypted form.
Ensure that an EXEC password is added to AUX and Console ports.
Ensure that RIP and OSPF protocol on the internet interface both inbound and outbound is stopped.
Ensure that CDP is disabled on all interfaces.
Ensure that a login banner is enabled with the appropriate legal notice. (banner login command) Ensure that the banner contains no information about the router, it’s name, model, software it’s running, or who owns it.
Ensure that SNMP is disabled if possible.
2. Ensure that any modem or network device that gives access to the console port must be secured. For a modem, user should provide a password for dial up access.
Ensure that the transport input none command is applied to any asynchronous or modem line that shouldn’t be receiving connections from network users.
Ensure that the same modem is not used for both dial in and dial out and that reverse telnet connections are not allowed on dial in lines.
For VTY lines ensure that it is configured to only accept connections with
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате DOC, PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 6
Cisco Checklist Cisco Checklist
Prepared by Krishni Naidu
References:
Securing your Internet Access Router, Richard Langley, January 2001
Remote Access Security: A layered approach, Lane Melton, Noem!er 2000
"rotecting Net#or$ in%rastructure at the protocol leel, &urt 'ilson, (ecem!er 2000
Implementing and su!erting &isco)s port security, (aid J* +yger, July 2000
Securing your &isco router #hen using SNM", &harles &arter, (ecem!er 2000
Restricting commands on a &isco router #ith "riilege Leels, "eplin &* ,arrameda,
January 2001
Layered Security: An IS" case study #ith &isco and Solaris, Roc$ie ,roc$#ay,
-cto!er 2000
Net#or$ Insecurity #ith S#itches, Aaron .urner, August 2000
"ort Scanning is not al#ays #hat it seems, (arin '* "o#ell, March 2001
.op ten !loc$ing recommendations using A&L)s Securing the perimeter #ith &isco
I-S 12 Routers, Scott 'inters, August 2000
Introduction
.his chec$list is to !e used to audit an enironment that includes &isco routers* .he
chec$list proides the technical security considerations during an audit and e/cludes
manual considerations li$e physical security considerations*
.he chec$list e/cludes the security considerations %or &isco s#itches*
"rior to using this chec$list consideration should !e gien to the %ollo#ing:
Location o% the router: It is important to ascertain the location o% the router in
the net#or$ as this has an impact on certain security elements e*g* disa!ling
SSL serice is not appropriate #hen the router is routing tra%%ic to an e/ternal
#e! serer*
"racticality o% security recommendations: .he chec$list lists numerous
security considerations, #hich may not !e practical as it could hinder the
per%ormance o% the net#or$* It is important to ascertain the ris$ allocated to
not haing certain security elements and #hether management has decided
to accept the ris$ o% not haing these elements*
Mitigating controls: .he audit o% &isco routers cannot !e per%ormed in a
acuum* .he auditor needs to consider the impact o% security in other
elements e*g* %ire#alls, host operating system, etc* A #ea$ness in security at
the router leel may !e mitigated !y a strong control at the %ire#all leel e*g*
%iltering out ports #hich are not 00,21, etc*
Interopera!ility: In circumstances #hen the router uses the %unctionality o%
other elements in the enironment e*g* a syslog serer to log eents %rom
cisco routers or an SNM" management station, the auditor must reie# the
security oer the other elements* .his chec$list does not proide the security
considerations %or these other elements*
Applica!ility o% security considerations: .his chec$list attempts to proide a
complete listing o% all security elements to consider during an audit o% &isco
router, ho#eer in some enironments certain elements may not !e
applica!le e*g* in a #indo#s enironment it is not necessary to !e concerned
a!out %iltering out rlogin or ssh serices*
Net#or$ serers: .his chec$list does not include security considerations %or
the operating system running .A&A&S or RA(I2S*
"age 1 o% 3
Nice to haes 4 .he chec$list attempts to proide security considerations,
#hich may !e nice to hae !ut ho#eer may not !e applica!le to the
enironment and the circumstance in #hich the router is used*
Checklist
No. No. Control Item Control Item
1. 1.
5nsure that all maintenance on the router is done #hile logged on locally*
5nsure that in!ound .elnet is disa!led as #ell as the .elnet listener*
I% .elnet is used to maintain the router ensure that access is granted only to
speci%ic #or$stations on the internal net#or$ side o% the router*
5nsure that all maintenance serices that #ould allo# access %rom outside the
net#or$ are disa!led or restricted*
5nsure that pass#ords are used #here possi!le*
5nsure that the 6serice pass#ord encryption7 command is used on all type 8
pass#ords*
5nsure that M(9 encryption is used on the 6"riileged 5:5& Mode7 pass#ord*
5na!le secret command*
5nsure that the serice pass#ord;encryption command is ena!led such that
#hen pass#ords are displayed #ith the more system:running;con%ig command,
they appear in encrypted %orm*
5nsure that an 5:5& pass#ord is added to A2: and &onsole ports*
5nsure that RI" and -S"< protocol on the internet inter%ace !oth in!ound and
out!ound is stopped*
5nsure that &(" is disa!led on all inter%aces*
5nsure that a login !anner is ena!led #ith the appropriate legal notice* =!anner
login command> 5nsure that the !anner contains no in%ormation a!out the
router, it)s name, model, so%t#are it)s running, or #ho o#ns it*
5nsure that SNM" is disa!led i% possi!le*
2* 5nsure that any modem or net#or$ deice that gies access to the console
port must !e secured* <or a modem, user should proide a pass#ord %or dial
up access*
5nsure that the transport input none command is applied to any asynchronous
or modem line that shouldn)t !e receiing connections %rom net#or$ users*
5nsure that the same modem is not used %or !oth dial in and dial out and that
reerse telnet connections are not allo#ed on dial in lines*
<or ?.@ lines ensure that it is con%igured to only accept connections #ith
protocols actually needed* I% encryption is supported ensure that only the SSA
protocol is used*
5nsure that the ip access class command is used to restrict the ip)s %rom #hich
the ?.@ #ill accept connections*
5nsure that one ?.@)s ip access;class is restricted to only one administratie
#or$station to preent (oS attac$s*
5nsure that the ?.@ timeouts are con%igured using the e/ec;timeout command*
5nsure that .&" $eepalies on incoming connections are ena!led =serice tsp;
$eepalies;in command> to guard against malicious attac$s and orphaned
sessions*
5nsure that all non;ip !ased remote access protocols are disa!led and that
I"Sec is used %or remote connections to the router*
<or routers that support &5<=&isco 5/press <or#arding> ensure that the
R"<=Reerse path %or#arding chec$ is ena!led =ip eri%y unicast rp%>* .his
preents spoo%ing !y chec$ing the source address o% a pac$et against the
inter%ace through #hich the pac$et entered the router*
"age 2 o% 3
No. No. Control Item Control Item
3. 3.
.A&A&S =terminal access controller access control system>
5nsure that non priilege access pass#ords are stored on the .A&A&S serer*
5nsure that only authorised ip)s o% .A&A&S daemons are speci%ied in the
tacacs;serer host command*
I% the ena!le use;tacacs command is used, ensure that it is used #ith e/tended
.A&A&S* 'ithout the e/tended .A&A&S the ena!le use;tacacs command
allo#s anyone #ith a alid username and pass#ord to access the
priileged 5:5& mode*
5nsure that login tacacs command is ena!led to ena!le pass#ord chec$ing at
login*
5nsure that the tacacs;serer noti%y command is con%igured to send a message
#hen a user:
ma$es a .&" connection
enters the ena!le command
logs out
5nsure that the tacacs;serer attempts command is con%igured to accept three
attempted logins on a line set up %or .A&A&S*
5nsure that e/tended .A&A&S is ena!led 4 tacacs;serer e/tended command
B* 5nsure that the %ollo#ing serices are !loc$ed:
Service Port Type Port Number
(NS Cone .rans%ers
e/cept %rom e/ternal
secondary (NS serers
.&" 91
.<." (aemon 2(" 3D
Lin$ .&" 08
S2N R"& .&" E 2(" 111
,S( 2NI: .&" 912 4 91B
L"( .&" 919
22&"( .&" 9B0
-pen 'indo#s .&" E 2(" 2000
N<S .&" E 2(" 20BD
: 'indo#s .&" E 2(" 3000 4 3299
Small serices .&" E 2(" 20 and !elo#
<." .&" 21
SSA .&" 22
.elnet .&" 21
SM." =e/cept e/ternal
mail relays>
.&" 29
N." .&" E 2(" 18
<inger .&" 8D
A.." =e/cept to e/ternal
#e! serers>
.&" 00
"-" .&" 10D E110
NN." .&" 11D
N." .&" 121
Net,I-S in 'indo#s N. .&" E2(" 119
Net,I-S in 'indo#s N. 2(" 118 E 110
Net,I-S .&" 11D
IMA" .&" 1B1
SNM" .&" 131 E132
SNM" 2(" 131 E132
"age 1 o% 3
,F" .&" 18D
L(A" .&" E2(" 10D
SSL =e/cept to e/ternal
#e! serers>
.&" BB1
Net,I-S in 'in2$ .&" E2(" BB9
Syslog 2(" 91B
S-&+S .&" 1000
&isco A2: port .&" 2001
&isco A2: port =stream> .&" B001
Loc$d =Linu/ (oS
?ulnera!ility>
.&" E2(" B0B9
&isco A2: port =!inary> .&" 3001
&ommon high order
A.." ports
.&" 0000, 0000, 0000
9* 5nsure that the %ollo#ing types o% I&M" tra%%ic on the internet inter%ace is
!loc$ed:
incoming echo reGuest =ping and 'indo#s traceroute>
outgoing echo replies
time e/ceeded
unreacha!le messages
I&M" redirects
5nsure that in!ound pac$ets on the internal inter%ace haing a source address
o% the internal net#or$ or 128*0*0*/ or resered address spaces are dropped
and logged*
5nsure that out!ound pac$ets on the internal inter%ace hae a source address
o% only the internal net#or$ or 128*0*0*/ or a resered address are dropped
and logged*
5nsure that I" Source routing is disa!led*
5nsure that reGuests %or I" directed !roadcast at all inter%aces o% all routers is
dropped and logged* =no ip directed;!roadcast command>
5nsure that N." is con%igured to allo# updates %rom internal time serers only*
5nsure that N." is disa!led on the internet inter%ace in!ound and out!ound*
3* (etermine ho# o%ten port scanners are used to ascertain unneeded open
ports*
Ascertain i% there is a process to use pac$et sni%%ers to determine #hat pac$ets
ma$e it through the A&L)s*
8* Ascertain i% tools to detect anomalous !ehaiour are used =such as Jinao,
%dget*c and Agilent Adisor>*
0* Ascertain i% #ea$nesses are regularly determined using tools li$e ISS net#or$
scanner* (etermine #hat action is ta$en to %i/ the ulnera!ilities*
D* SNM"
5nsure that SNM" ersion 2 is in use %or the stronger M(9 digest
authentication scheme*
5nsure that string names such as pu!lic and priate are not used*
5nsure that there is a process to periodically change pass#ords %or the
community strings*
Ascertain i% the SNM" !rute %orce attac$ tool %rom Solar#inds or a similar tool
is used regularly to test the strength o% the strings*
5nsure that only authorised management hosts are allo#ed to access SNM"
ena!led routers* =access list>
5nsure that SNM" traps are ena!led and that it is con%igured to send a trap i%
the authentication o% the community string %ails as #ell as #hich host computer
should !e sent the trap*
"age B o% 3
No. No. Control Item Control Item
10. 10.
5nsure that commands on the router are restricted to the correct priilege leel*
11* 5nsure that tcp intercept is ena!led*=ip tcp intercept list command>
12* 5nsure that a Net#or$ I(S is in use such as &isco Secure I(S or Realsecure*
11* (etermine the amount o% processing po#er o% the router and ensure that this
appropriate*
1B* 5nsure that logging is ena!led on the router* Since there may not !e su%%icient
space to log on the router, ideally the log in%ormation should !e logged at a
syslog serer* I% this is not possi!le %or the net#or$ ensure that an I(S or sni%%er
is used to log tra%%ic*
5nsure that log entries are timestamped using serice timestamps log datetime
msecs*
5nsure that access list logging is ena!led*
19* 5nsure that return SSA tra%%ic is allo#ed*
13* I% <." is necessary ensure that passie <." outgoing tra%%ic is allo#ed*
18* &,A& =&onte/t !ased access control>
2se the sho# ip inspection inter%aces command to display the inspection rules
and access lists* Reie# the rules and access lists to ensure that:
Jaa inspection
Application protocols 4 2ni/ R commands, %tp, t%tp
.&"H2(" inspection
5nsure that the inspection rules hae !een applied to the
appropriate inter%aces*
5nsure that the access lists permits tra%%ic only %rom %riendly sites
and denies tra%%ic %rom hostile sites*
5nsure that the audit trail is ena!led 4 ip inspect audit trail*
10* 5nsure that there is a process to test any %ilters using tools li$e nmap prior to
rolling out to the #hole enironment*
1D* I% (NS is necessary ensure that (NS tra%%ic is only allo#ed to the (NS serer*
5nsure that only (NS responses are leaing the screened su!net*
20* I% A.." is necessary ensure that A.." tra%%ic is allo#ed only to the #e! serer*
21* A.." %or management
5nsure that access is restricted using the ip http access;class command to
only authorised addresses*
5nsure that .A&A&SI or RA(I2S serer is used %or authentication o%
interactie logins*
22* Management and interactie access ia untrusted net#or$s
5nsure that encrypted protocols li$e SSA or +er!eriJed .elnet is used %or login*
Alternatiely ensure that I"Sec is used %or all router management tra%%ic*
-r ensure that a one time pass#ord system li$e SH+ey or -"I5 #ith .A&A&SI
or RA(I2S serers is used to control interactie and priileged access to the
router*
5nsure that an alternatie management channel such as a modem is aaila!le
in the eent o% a (oS attac$*
21* 2pdates
Ascertain i% there is a process to test and roll out ne# updates to &isco
so%t#are as #ell as a process to $eep up to date #ith ne# ulnera!ilities and
notices and to ta$e correctie action i% necessary*
"age 9 o% 3
No. No. Control Item Control Item
24. 24.
AAA
5nsure that an authentication !anner has !een con%igured %or AAA =command
4 aaa authentication !anner>*
5nsure that the net#or$ access serer is con%igured to reGuest authorisation
in%ormation !e%ore allo#ing a user to esta!lish a reerse .elnet session*
=command 4 aaa authorisation reerse;access Kradius I tacacsIL>
5nsure that accounting has !een ena!led to log net#or$, 5:5&, commands,
connection and system* Ascertain ho# o%ten the sho# accounting command is
used to reie# the accounting in%ormation*
29* .ransit <looding
At a minimum ensure that the %ollo#ing Guality o% serice %eatures are used:
#eighted %air Gueueing ='<M>
committed access rate =&AR>
generalised tra%%ic shaping =F.S>
23* Router %looding
5nsure that &5< is ena!led*
5nsure that the scheduler interal is set to 900 or alternatiely on ne#er
plat%orms the scheduler allocate should !e set to 10000 2000* .his preents
the router %rom spending to much time handling interrupts %rom net#or$
inter%aces and not any #or$ done*
28* Neigh!our authentication
5nsure that M(9 authentication is used to authenticate the neigh!our router
prior to receiing routing ta!le updates*
5nsure that there is appropriate security %or the $eys e*g* during transit and
storage*
20* Internet +ey 5/change
Reie# the policy #ith the %ollo#ing command:
sho# crypto isa$amp policy
<or higher ris$ communications ensure that the stronger settings are applied as
%ollo#s:
Aash algorithm 4 SAA;1
Authentication method ; RSA signatures
(i%%ie hellman group identi%ier 4 102B !it
Security associations li%etime 4 I day 4 03B00 seconds =the shorter the
li%etime the more secure are the communications>
2D* 5nsure that the no pro/y;arp command is con%igured to preent internal
addresses %rom !eing reealed*
10* 5ncryption
2sing the %ollo#ing command 4 sho# crypto cisco algorithms 4 to determine
the type o% (5S algorithm that is in use* 5nsure that the insecure B0 !it
ariations are not used*
5nsure a !ac$up o% the encryption con%iguration is made*
11* &erti%icate Authority
5nsure that the &RL optional is set to no* &erti%icates #ill not !e accepted i% the
&A is unaaila!le*
5nsure that the copy system:running;con%ig nram:startup;con%ig command is
per%ormed to sae the con%iguration*
(etermine ho# o%ten the crypto ca crl reGuest command is run to do#nload the
latest certi%icate reocation list*
"age 3 o% 3
Вам также может понравиться
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3От EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Оценок пока нет
- Installing and Using RSLogix 5000 and RSLogix 500Документ90 страницInstalling and Using RSLogix 5000 and RSLogix 500fsakr2008Оценок пока нет
- Security Testing by OWASP Top 10Документ30 страницSecurity Testing by OWASP Top 10tarellethiel021Оценок пока нет
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОт EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОценок пока нет
- Cisco Router Switch Security HardeningДокумент9 страницCisco Router Switch Security HardeningEuribiades Jose GomezОценок пока нет
- CCNASv1.1 Chp08 Lab A Site2Site VPN InstructorДокумент40 страницCCNASv1.1 Chp08 Lab A Site2Site VPN Instructordotheanhdotramy0% (1)
- Term Paper: Security of Cisco RoutersДокумент11 страницTerm Paper: Security of Cisco RoutersKaran GabaОценок пока нет
- DRSEnt PT Practice SBA OSPF PDFДокумент5 страницDRSEnt PT Practice SBA OSPF PDFHarol Matias RamosОценок пока нет
- Connecting Networks Chapter 3 v5.0 Exam Answers 2014Документ8 страницConnecting Networks Chapter 3 v5.0 Exam Answers 2014adrian743842Оценок пока нет
- Data Comm TechДокумент48 страницData Comm Techiwc2008007Оценок пока нет
- It1402 - Mobile Computing Unit Iv: Vasantha Kumar .V Lecturer CSEДокумент10 страницIt1402 - Mobile Computing Unit Iv: Vasantha Kumar .V Lecturer CSEVignesh Manicka DiwakarОценок пока нет
- Chapter 4 Lab 4-2, Mixed Layer 2-3 Connectivity Chapter 4 Lab 4-2, Mixed Layer 2-3 ConnectivityДокумент13 страницChapter 4 Lab 4-2, Mixed Layer 2-3 Connectivity Chapter 4 Lab 4-2, Mixed Layer 2-3 ConnectivityKarina Herrera YzaguirreОценок пока нет
- Ccnasv1.1 Chp03 Lab-A Aaa-Radius StudentДокумент25 страницCcnasv1.1 Chp03 Lab-A Aaa-Radius StudentAngel MendozaОценок пока нет
- Resueltos Ccna2Документ139 страницResueltos Ccna2Mauricio SalazarОценок пока нет
- Ewan Ptact 5 2 8Документ6 страницEwan Ptact 5 2 8Muhammad HudzaifahОценок пока нет
- Idoc - Tips Soal MikrotikДокумент10 страницIdoc - Tips Soal MikrotikBack HeheОценок пока нет
- Exploration Routing Chapter 4Документ33 страницыExploration Routing Chapter 4Nuruel AzmieОценок пока нет
- Chapter 3 Lab A: Securing Administrative Access Using AAA and RadiusДокумент25 страницChapter 3 Lab A: Securing Administrative Access Using AAA and RadiusfernaleoОценок пока нет
- CCNA Guide To Networking - Ch7 - Quiz SolutionsДокумент4 страницыCCNA Guide To Networking - Ch7 - Quiz SolutionsNickHenryОценок пока нет
- Welcome!: Red Hat Network Services and Security AdministrationДокумент24 страницыWelcome!: Red Hat Network Services and Security AdministrationVibhor SharmaОценок пока нет
- Ewan Ptact 5 3 4Документ8 страницEwan Ptact 5 3 4Sandra CortésОценок пока нет
- 2006 02 01 Wireless SeminarДокумент34 страницы2006 02 01 Wireless SeminarAshish Rajendra MasihОценок пока нет
- CCNA Guide To Networking - Ch6 - Quiz SolutionsДокумент5 страницCCNA Guide To Networking - Ch6 - Quiz SolutionsNickHenryОценок пока нет
- D09IntrodToSerComs 28augДокумент5 страницD09IntrodToSerComs 28augP_leeОценок пока нет
- Connecting Networks Chapter 8 v5.0 Exam Answers 2014Документ6 страницConnecting Networks Chapter 8 v5.0 Exam Answers 2014adrian743842Оценок пока нет
- UNIT-1 Introduction To Embedded Systems Two Mark Questions and AnswersДокумент30 страницUNIT-1 Introduction To Embedded Systems Two Mark Questions and AnswersBharath RamanОценок пока нет
- Cisco ISO and Boot Process PDFДокумент10 страницCisco ISO and Boot Process PDFsystems_sgОценок пока нет
- CCNA Practice Certification Exam # 2Документ23 страницыCCNA Practice Certification Exam # 2Mauricio Rodriguez FigueroaОценок пока нет
- Take Assessment - Enetwork Final Exam - Ccna Exploration: Network Fundamentals (Version 4.0)Документ20 страницTake Assessment - Enetwork Final Exam - Ccna Exploration: Network Fundamentals (Version 4.0)Raphael AlmeidaОценок пока нет
- Final NДокумент6 страницFinal Napi-242570998Оценок пока нет
- The Feature of Huawei MA5600Документ10 страницThe Feature of Huawei MA5600Elizabeth Rich100% (2)
- Telnet ConfigДокумент2 страницыTelnet ConfigswadeshsxcОценок пока нет
- Online Voting System A ASP Net ProjectДокумент47 страницOnline Voting System A ASP Net Projectspatade7Оценок пока нет
- 1510 LabManual OPNK2004Документ52 страницы1510 LabManual OPNK2004Thang TranОценок пока нет
- Connecting Networks Chapter 9 v5.0 Exam Answers 2014Документ6 страницConnecting Networks Chapter 9 v5.0 Exam Answers 2014adrian743842Оценок пока нет
- Quiz 2Документ5 страницQuiz 2cyonconОценок пока нет
- CCNA2 Chapter 1 Practice Test Questions: SW 23/10/2007 /var/www/apps/conversion/tmp/scratch - 6/226630909.doc 1Документ8 страницCCNA2 Chapter 1 Practice Test Questions: SW 23/10/2007 /var/www/apps/conversion/tmp/scratch - 6/226630909.doc 1Jacek KlosОценок пока нет
- RIP Version 1 PracticeДокумент7 страницRIP Version 1 PracticeaennekОценок пока нет
- Cisco ChecklistДокумент6 страницCisco ChecklistDema PermanaОценок пока нет
- Network FundamentalsДокумент69 страницNetwork Fundamentalsatul012Оценок пока нет
- Lab 5.3.7 Configuring DHCP With SDM and The Cisco IOS CLIДокумент15 страницLab 5.3.7 Configuring DHCP With SDM and The Cisco IOS CLIArba SudiatmikaОценок пока нет
- Bastion HostДокумент3 страницыBastion HostIan E ComingsОценок пока нет
- What Is The Difference Between WCF and ASMX Web Services?Документ4 страницыWhat Is The Difference Between WCF and ASMX Web Services?rosysanchezloeraОценок пока нет
- Introduction To Routing and Packet ForwardingДокумент83 страницыIntroduction To Routing and Packet ForwardingJulio Cesar EMОценок пока нет
- Unit 2Документ41 страницаUnit 2jayaprasanna123Оценок пока нет
- CCNASv1.1 Chp09 Lab-A Sec-Pol StudentДокумент32 страницыCCNASv1.1 Chp09 Lab-A Sec-Pol Studentluisdg93Оценок пока нет
- TEI480T+ User GuideДокумент82 страницыTEI480T+ User GuidePeter SerranoОценок пока нет
- Preparation of Transformer SpecДокумент57 страницPreparation of Transformer SpecboopelectraОценок пока нет
- What Is A Firewall?: The WordДокумент5 страницWhat Is A Firewall?: The WordKrishna ForuОценок пока нет
- Tutorial 10Документ18 страницTutorial 10Andres FelipeОценок пока нет
- Erouting Ospf PT Practice Sba: Device Interface Address Subnet Mask Default GatewayДокумент3 страницыErouting Ospf PT Practice Sba: Device Interface Address Subnet Mask Default GatewayJose Linares InfanteОценок пока нет
- CCNA Guide To Networking - Ch8 - Quiz SolutionsДокумент6 страницCCNA Guide To Networking - Ch8 - Quiz SolutionsNickHenryОценок пока нет
- Enumeration TechniquesДокумент21 страницаEnumeration TechniquesShafeeque Olassery KunnikkalОценок пока нет
- Chapter 5 Exercises and Answers: Answers Are in BlueДокумент5 страницChapter 5 Exercises and Answers: Answers Are in BluemalikhassangulОценок пока нет
- Industrial-IJIET - SecurityДокумент6 страницIndustrial-IJIET - SecurityTJPRC PublicationsОценок пока нет
- Visibility - Acceleration - Security: Harri KurronenДокумент31 страницаVisibility - Acceleration - Security: Harri KurronenGuy PoakaОценок пока нет
- Connecting Networks Chapter 6 v5.0 Exam Answers 2014Документ5 страницConnecting Networks Chapter 6 v5.0 Exam Answers 2014adrian743842Оценок пока нет
- Configuring Frame RelayДокумент5 страницConfiguring Frame RelayArdit MeziniОценок пока нет
- Proxy ChainДокумент5 страницProxy ChainFrancisco DiazОценок пока нет