Академический Документы
Профессиональный Документы
Культура Документы
Distributed Data Mining and Mining Multi Agent Data
Загружено:
abhiwave69Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Distributed Data Mining and Mining Multi Agent Data
Загружено:
abhiwave69Авторское право:
Доступные форматы
Submitted To: - Submitted By: -
~ 1 ~
Abhishek Abhishek
Kumar Kumar
Roll No: - Roll No: -
RD1207B40 RD1207B40
Reg No: - Reg No: -
11210885 11210885
Course: - Course: - MCA 5 MCA 5
th th
Sem. Sem. Section: - Section: -
D1207 D1207
Miss. Kavisha Miss. Kavisha
Duggal Duggal
PAPER
CAP617
ACKNOW!D"!M!N#
The experience that we have gathered during this Design
Problem has been unique .For this we are pleased to express
our deepest sense of gratitude and regards to our respected
teacher Miss. Kavisha Duggal for their guidance, inspiration
and constructive suggestions that helps us in the preparation
of the design problem.
I am also thanful to m! classmate
constant encouragement and support.
"
INDEX
SL. NO. ONTENTS !"#E NO.
$ "bst%a&t '
( I)t%odu&tio) *
+ Dist%ibuted Data Mi)i)g ,
' -hy "ge)t. /
* "ge)t Based DDM 0
, Basi& om1o)e)ts o2 "DDM 0
/ M"DM System a) "%&hite&tu%e "11%oa&h 3
0 "ge)t Se&u%ity Issues $4
3 Se&u%ity Measu%e 2o% "ge)t $$
$4 5utu%e S&o1e $$
#
"BST6"T
Distributed Data $ining pla!s ver! important role in networ problems. In a
distributed environment %such as a sensor or IP networ&, one has distributed
probes placed at strategic locations within the networ. The problem here is to
be able to correlate the data seen at the various probes, and discover
Patterns are in the global data seen at all the different probes. There could be
different models of distributed data mining here, but one could involve a '()
that collects data from the distributed sites, and another in which all sites are
treated equall!. The goal here obviousl! would be to minimi*e the amount of
data shipped between the various sites essentiall!, to reduce the communication
overhead. In distributed mining, one problem is how to mine across multiple
heterogeneous data sources+ multi,database and multi relational mining.
-nother important new area is adversar! data mining. In a growing number of
domains email spam, counter,terrorism, intrusion detection.computer securit!,
clic spam, search engine spam, surveillance, fraud detection, shop bots, and
file sharing. Data mining s!stems face adversaries that deliberatel! manipulate
the data to sabotage them %e.g. mae them produce false negatives&. In this
paper need to develop s!stems that explicitl! tae this into account, b!
combining data mining with game theor!.
/
INT6OD7TION
Data mining technolog! has emerged as a means for identif!ing patterns and
trends from large quantities of data. The Data $ining technolog! normall!
adopts data integration method to generate Data warehouse, on which to gather
all data into a central site, and then run an algorithm against that data to extract
the useful $odule Prediction and nowledge evaluation. 0owever, a single
data,mining technique has not been proven appropriate for ever! domain and
data set. Data mining techniques involving in such complex environment must
encounter great d!namics due to changes in the s!stem can affect the overall
performance of the s!stem.
1
DIST6IB7TED D"T" MININ#
Distributed data mining is originated from the need of mining over
decentrali*ed data sources. The field of Distributed Data $ining %DD$& deals
with these challenges in anal!sing distributed data and offers man! algorithmic
solutions to perform different data anal!sis and mining operations in a
fundamentall! Distributed manner that pa!s careful attention to the resource
constraints. 2ince multi,agent s!stems are often distributed and agents have
proactive and reactive features which are ver! useful for 3nowledge
$anagement 2!stems, combining DD$ with $-2 for data intensive
applications is appealing.
The ob4ective of Distributed data mining is to perform the data mining
operations based on the t!pe and availabilit! of the distributed resources. It
$a! choose to download the data sets to a single site and perform the data
mining operations at a central location.
5
-89 "#ENT.
-gent computing whose aim is to deal with complex s!stems has revealed
opportunities to improve distributed data mining s!stems in a number of wa!s.
$ulti,agent s!stems %$-2& often deal with complex applications that require
distributed problem solving. In man! applications the individual and collective
behaviour of the agents depends on the observed data from distributed sources.
- 2oftware -gent is as user6s personal assistant.
-gent can be programmed as compact as possible.
7ight weight agent can transmitted across the networ rather than data
that is more bul!.
The Designing of DD$ 2!stems Deals 8ith
9reat Details of -lgorithms used
o :eusabilit!
o ;xtensibilit!
o :obustness
0ence, the agent characteristics are desirable to use in DD$.
<
"#ENT B"SED DDM
-DD$ s!stem concerns three e!s characteristics
o Interoperabilit!
o D!namic )onfiguration
o Performance -spects
-pplications of distributed data mining include credit card
-uthentication, intrusion detection and all this t!pe general and securit!
related applications.
Into this a novel Data $ining Technique inherits the properties of agents.
The DD$ applications can be further enhanced with agents.
=etter Integration polic! with the communication protocols
Provide a view of online parallel processing
B"SI OM!ONENTS O5 "DDM
-n -DD$ s!stem can be generali*ed into a set of components
Figure+ -n (verview of -DD$
>
M"DM S9STEM "N "68ITET76E "!!6O"8
$-D$ is the -DD$ but equipped with several agents which have
particular goal of functionalit! as+
6esou%&e "ge)t: $aintaining $eta Data Information
Lo&al Tas: "ge)t: 7ocated at the local site
B%o:e% "ge)t: 8oring as -dvisor agent
;ue%y "ge)t: 3DD 2!stem -gent
!%e-!%o&essi)g "ge)t: Preparing data for mining
!ost Data "ge)t: ;valuates the performance and accurac!
6esult "ge)t: -ggregate the all local results
I)te%2a&e "ge)t: Provide Interface to the real world applications
Mobile "ge)t: $igrate based on :equest and :esponse
M"DM S9STEM "N "68ITET76"L
?
"#ENT SE76IT9 ISS7ES
Identification and authentication
-uthori*ation and delegation
)ommunication
o confidentialit!+ assurance that communicated information is not
accessible to unauthorised parties@
o data integrit!+ assurance that communicated information cannot be
manipulated b! unauthorised parties without being detected@
o availabilit!+ assurance that communication reaches its intended
recipient in a timel! fashion@
o 'on,repudiation+ assurance that the originating entit! can be held
responsible for its communications.
$obilit!
2ituated ness
-utonom!
-gent ;xecution
1A
Data Source on
Different Sites
SE76IT9 ME"S76E 5O6 "#ENT
Protecting agents
o Trusted hardware
o Trusted nodes
o )o,operating agents
o ;xecution tracing
o ;ncr!pted pa!load
o ;nvironmental e! generation
o )omputing with encr!pted functions
o Bn,detachable signatures
Protecting the agent platform
o 2andboxing and safe code interpretation
o Proof carr!ing code
o 2igned code
o Path histories
o 2tate appraisal
11
57T76E SO!E
Data $ining and web mining is the hot area of research
Integration of 3DD and -gent technolog! can provide a new wa! to both
For several networ securit! researchers it can provide several new wa!
to find the fraud in the networ as provide fast discover!
:eal time confidential transaction can be mae secure b! the integration
of -gent Technolog!
1"
Вам также может понравиться
- Introduction to Information Storage and ManagementДокумент51 страницаIntroduction to Information Storage and Managementabhiwave69Оценок пока нет
- Alice Li Thesis 2011Документ92 страницыAlice Li Thesis 2011abhiwave69Оценок пока нет
- CДокумент8 страницCabhiwave69Оценок пока нет
- 4340 Most Common WordssДокумент124 страницы4340 Most Common Wordssabhiwave69Оценок пока нет
- Term Paper Topics of CAP663 D1E16Документ3 страницыTerm Paper Topics of CAP663 D1E16abhiwave69Оценок пока нет
- ASP IntroductionДокумент36 страницASP Introductionabhiwave69Оценок пока нет
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (399)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (120)
- 4 Lecture 4-Dimensional ModellingДокумент45 страниц4 Lecture 4-Dimensional Modellingsignup8707Оценок пока нет
- Business Consultant SoundaryaДокумент5 страницBusiness Consultant SoundaryasoundryasnОценок пока нет
- IPLOOK EPC Web Operation Manual-20200408-V2.0Документ50 страницIPLOOK EPC Web Operation Manual-20200408-V2.0IPLOOK TechnologiesОценок пока нет
- Apex-Mdapi - MetadataServiceExamples - Cls at Master Financialforcedev - Apex-Mdapi GitHubДокумент26 страницApex-Mdapi - MetadataServiceExamples - Cls at Master Financialforcedev - Apex-Mdapi GitHubProlay ChaudhuryОценок пока нет
- Maintenance of Electronic RecordsДокумент4 страницыMaintenance of Electronic RecordsATUHA PETERОценок пока нет
- Auditing Cloud PDFДокумент5 страницAuditing Cloud PDFKrishnakant PvsОценок пока нет
- Computer Hacking Forensic Investigator v10Документ8 страницComputer Hacking Forensic Investigator v10Ankit PandeyОценок пока нет
- Data Analytics for Improving Tax ComplianceДокумент40 страницData Analytics for Improving Tax ComplianceDosen Audit Keuangan Sektor KomersialОценок пока нет
- Blood Bank ManagementeeДокумент58 страницBlood Bank Managementeeshubham mauryaОценок пока нет
- Difference Between Sap Ecc and Sap S4hanaДокумент2 страницыDifference Between Sap Ecc and Sap S4hanaRajEshwer ReddyОценок пока нет
- Online Tailoring Management System Ch1-2Документ21 страницаOnline Tailoring Management System Ch1-2Simegnew TizazuОценок пока нет
- Performing A Custom Installation of ObserveIT PDFДокумент53 страницыPerforming A Custom Installation of ObserveIT PDFJack NguyenОценок пока нет
- Find empty tables in Oracle schema with a single queryДокумент5 страницFind empty tables in Oracle schema with a single querysai_balaji_8Оценок пока нет
- Bj8 s4cld2302 BPD en Us MtoДокумент37 страницBj8 s4cld2302 BPD en Us MtoprajeethОценок пока нет
- Da Notes (Big Data) PDFДокумент32 страницыDa Notes (Big Data) PDFRohit SekarОценок пока нет
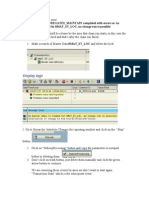
- Report RSDDS - AGGREGATES - MAINTAIN Completed With Errors or As Master Data Is Loaded For 0MAT - ST - LOC, No Change Run Is PossibleДокумент3 страницыReport RSDDS - AGGREGATES - MAINTAIN Completed With Errors or As Master Data Is Loaded For 0MAT - ST - LOC, No Change Run Is PossiblesvrbikkinaОценок пока нет
- Build Process of Embedded SystemДокумент21 страницаBuild Process of Embedded SystemanithaОценок пока нет
- AAE Q&A Exam Review AnswersДокумент7 страницAAE Q&A Exam Review AnswersKevin PratamaОценок пока нет
- Index of Subject Codes and Course TitlesДокумент135 страницIndex of Subject Codes and Course TitlesHarsha GuptaОценок пока нет
- Business Intelligence Maturity Models: Toward New Integrated ModelДокумент9 страницBusiness Intelligence Maturity Models: Toward New Integrated ModelGonzalo ESTEОценок пока нет
- Mis - Unit - 1 NotesДокумент21 страницаMis - Unit - 1 NotesPranshu SahasrabuddheОценок пока нет
- JSP Java Server PagesДокумент22 страницыJSP Java Server PagesFiras ChaabeneОценок пока нет
- Hands Software Architecture GolangДокумент700 страницHands Software Architecture GolangTarun DugarОценок пока нет
- Kamiru - Adoption of Open Source Software by The Telecommunications Industry in KenyaДокумент69 страницKamiru - Adoption of Open Source Software by The Telecommunications Industry in KenyaJoel BiwottОценок пока нет
- Performance Tuning Guidelines For Siebel On Oracle Database December 2010Документ28 страницPerformance Tuning Guidelines For Siebel On Oracle Database December 201094050668100% (1)
- Life Cycle of Source Program Compiler DesignДокумент10 страницLife Cycle of Source Program Compiler DesignTusharОценок пока нет
- College ManagementДокумент20 страницCollege ManagementKmrs Sugapriya1213Оценок пока нет
- Module 9 List Applet PM PRДокумент29 страницModule 9 List Applet PM PRneelabharathyОценок пока нет
- Red Hat Enterprise Linux 8 Administration Master Linux Administration Skills and Prepare For The RHCSA Certification Exam by Miguel Pérez Colino, Pablo Iranzo Gómez, Scott McCartДокумент534 страницыRed Hat Enterprise Linux 8 Administration Master Linux Administration Skills and Prepare For The RHCSA Certification Exam by Miguel Pérez Colino, Pablo Iranzo Gómez, Scott McCartKirti NandanОценок пока нет
- Spares Management Address SetupДокумент24 страницыSpares Management Address SetupCuong Nguyen TanОценок пока нет