Академический Документы
Профессиональный Документы
Культура Документы
Scan Session Summary: Web Application Security Report
Загружено:
Mondher GamИсходное описание:
Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Scan Session Summary: Web Application Security Report
Загружено:
Mondher GamАвторское право:
Доступные форматы
N-Stalker Web Application
Security Technical Report
Web Application Security Report
(196.203.190.22)
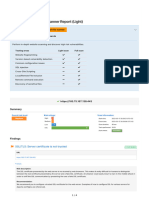
1. Scan Session Summary
1. Scan Statistics by Severity Level
2. Scan Statistics by Vulnerability Type
3. Web Application Information
URL
196.203.190.22
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 1 of
N-Stalker Web Application
Security Technical Report
Port
Protocol
SSLCipher
Server-Type
Detected-Type
Server-Side Technologies Detected
Number of sub-hosts involved
80
HTTP
N/A
Apache/2.2.15 (Red Hat)
Caucho Resin
N/A
4. Scan Statistics
Avg Response Time
Avg Response Size
Total Scan Time
Number of Spidered Links
Number of Cookies
Number of Javascript objects
Number of HTML Comments
Number of e-mails
Number of Broken Pages
Number of hidden fields
Number of Objects Leaked
4430
275
311 mins (18690 secs)
0
0
0
0
0
0
0
0
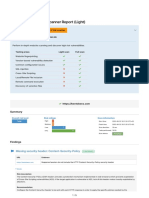
5. Policy Details
Policy Name
Policy Details
Complete Pen-test Assessment
Audit & Pen-test Assessment
Applied Rules
Web Resources Spider and Analysis
Server Vulnerabilities Assessment
Directory Brute-force Discovery
File & Directory Exposure Attacks
Cross-site Scripting Attacks
SQL Injection Attacks
Memory Fault Attacks
Parameter Tampering Attacks
Signature-based HTTP Attacks
Information Leakage Search
Protocol Compliance Check
2. Web Site Structure
1. Published Directories
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 2 of
N-Stalker Web Application
Security Technical Report
Path
Status
3. Application Objects
1. Cookies
Cookie
2. E-mails
E-mail
Count
3. Broken Pages
Page
Reference
4. Hidden Fields
Field name & value
URL & Post Data
5. Information Leakage
Name
Value
6. Web Forms
4. Vulnerabilities
1. Web Server Exposure
Oracle Single Sign-On Login Page Authentication Credential Disclosure Vulnerability
CVE : CVE-2007BID : 24215
OSVDB : 37050
High Level
3304
Target Server : http://196.203.190.22:80/
URL : /
Comments
It has been reported that Oracle Single Sign-On login form is prone to an authentication
credential disclosure vulnerability that that may allow remote attackers to disclose
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 3 of
N-Stalker Web Application
Security Technical Report
authentication credentials such as username and passwords of vulnerable users. Workaround:
The p_submit_url value in the customized login page can be hard-coded. This will mitigate this
issue since it will not be an input value to the page anymore. The p_submit_url URL value in
the 902 SSO server is in the following format:
http(s)://sso_host:port/pls/orasso/orasso.wwsso_app_admin.ls_login Vulnerable versions
includes: Oracle IAS 9.0.3.1 (and previous), Oracle HTTP Server 9.2.0 (and previous).
Solution
Please, download the latest version.
References
http://httpd.apache.org/download.cgi
http://www.kb.cert.org/vuls/id/395412
http://httpd.apache.org/docs/2.2/new_features_2_2.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : PROPFIND (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 4 of
N-Stalker Web Application
Security Technical Report
Target Server : http://196.203.190.22:80/
URL : OPTIONS (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : DELETE (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 5 of
N-Stalker Web Application
Security Technical Report
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use, including
data storage, directory services, mail, messaging, and more. Failure to manage the proper
configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : PROPPATCH (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 6 of
N-Stalker Web Application
Security Technical Report
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : MKCOL (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : COPY (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 7 of
N-Stalker Web Application
Security Technical Report
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use, including
data storage, directory services, mail, messaging, and more. Failure to manage the proper
configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : MOVE (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 8 of
N-Stalker Web Application
Security Technical Report
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : LOCK (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : UNLOCK (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 9 of
N-Stalker Web Application
Security Technical Report
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use, including
data storage, directory services, mail, messaging, and more. Failure to manage the proper
configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : LINK (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 10 of
N-Stalker Web Application
Security Technical Report
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
Possible Insecure HTTP Method found
Information Level CVE : MAP-NOMATCH BID : None
OSVDB : None
Target Server : http://196.203.190.22:80/
URL : UNLINK (http://196.203.190.22:80/)
Comments
An insecure HTTP method has been detected as available in the Web Server side and may be
exploited under certain conditions.
Although it may varies accordingly to the situation, HTTP methods others than GET, POST
and HEAD are not common and should be evaluated before being made public available on
production-level Web Servers.
Some problems may arise because of information leakage problem such as TRACE method
(that may reveal internal private HTTP Headers) or may be used for client-side credentials
stealing attacks. Other methods such as PROPFIND and WebDav-based methods may allow
for arbitrary file uploading and should not be available under normal conditions.
This issue can be considered an Insecure Configuration Management as described in OWASP
Top10 Web Application Vulnerabilities, Section A10: "Web server and application server
configurations play a key role in the security of a web application. These servers are
responsible for serving content and invoking applications that generate content. In addition,
many application servers provide a number of services that web applications can use,
including data storage, directory services, mail, messaging, and more. Failure to manage the
proper configuration of your servers can lead to a wide variety of security problems."
Solution
IT staff must act with an effective Web server hardening control and also establish an effective
Production Planning and Control program to avoid insecure configuration scenario.
Undesired HTTP method can be easily removed from most Web Server Platforms. See more
information below. Microsoft IIS users are advised to use URLscan.
References
http://www.kb.cert.org/vuls/id/867593
http://www.microsoft.com/technet/security/tools/urlscan.mspx
http://www.owasp.org/documentation/topten/a10.html
2. Custom Design Errors
No vulnerabilities.
3. Web Signature Attacks
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 11 of
N-Stalker Web Application
Security Technical Report
Oracle Single Sign-On Login Page Authentication Credential Disclosure Vulnerability
CVE : CVE-2007BID : 24215
OSVDB : 37050
High Level
3304
Target Server : http://196.203.190.22:80/
URL : /
Comments
It has been reported that Oracle Single Sign-On login form is prone to an authentication
credential disclosure vulnerability that that may allow remote attackers to disclose
authentication credentials such as username and passwords of vulnerable users. Workaround:
The p_submit_url value in the customized login page can be hard-coded. This will mitigate this
issue since it will not be an input value to the page anymore. The p_submit_url URL value in
the 902 SSO server is in the following format:
http(s)://sso_host:port/pls/orasso/orasso.wwsso_app_admin.ls_login Vulnerable versions
includes: Oracle IAS 9.0.3.1 (and previous), Oracle HTTP Server 9.2.0 (and previous).
Solution
Please, download the latest version.
References
http://httpd.apache.org/download.cgi
http://www.kb.cert.org/vuls/id/395412
http://httpd.apache.org/docs/2.2/new_features_2_2.html
Oracle Single Sign-On Login Page Authentication Credential Disclosure Vulnerability
High Level
CVE : 0
BID : 10009
OSVDB : 0
Target Server : http://196.203.190.22:80/
URL : /pls/orasso/orasso.wwsso_app_admin.ls_login
Comments
It has been reported that Oracle Single Sign-On login form is prone to an authentication
credential disclosure vulnerability that that may allow remote attackers to disclose
authentication credentials such as username and passwords of vulnerable users. Workaround:
The p_submit_url value in the customized login page can be hard-coded. This will mitigate this
issue since it will not be an input value to the page anymore. The p_submit_url URL value in
the 902 SSO server is in the following format:
http(s)://sso_host:port/pls/orasso/orasso.wwsso_app_admin.ls_login Vulnerable versions
includes: Oracle IAS 9.0.3.1 (and previous), Oracle HTTP Server 9.2.0 (and previous).
Solution
No solution available.
References
No external references available.
4. Confidentiality Exposure
No vulnerabilities.
5. Cookie Exposure
No vulnerabilities.
6. File & Directory Exposure
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 12 of
N-Stalker Web Application
Security Technical Report
No vulnerabilities.
7. Custom Content Inspection
No vulnerabilities.
Confidential report - must not be disclosed without prior authorization
N-Stalker Web Application Security - Page 13 of
Вам также может понравиться
- Analyzing Web TrafficДокумент16 страницAnalyzing Web TraffichugocelaОценок пока нет
- Webappsec IntroДокумент25 страницWebappsec IntrosomendasОценок пока нет
- A Practical Guide To Web Application SecurityДокумент10 страницA Practical Guide To Web Application SecurityStillward Laud Mark-MillsОценок пока нет
- Web Security Interview QuestionДокумент34 страницыWeb Security Interview Questionarunika palОценок пока нет
- Web Security Interview QuestionДокумент8 страницWeb Security Interview Questionvenkat1034Оценок пока нет
- Web Application Attacks - 1Документ36 страницWeb Application Attacks - 1shanthiОценок пока нет
- There Are Several Ways To Manage A Secured SiteДокумент2 страницыThere Are Several Ways To Manage A Secured SiteBatrisyia SainiОценок пока нет
- Attack I: SQL Injection at Telegraph Results in 700,000 Emails StolenДокумент7 страницAttack I: SQL Injection at Telegraph Results in 700,000 Emails StolenranapdpОценок пока нет
- Learn Security Online, Inc. ©Документ17 страницLearn Security Online, Inc. ©aneudyhОценок пока нет
- Report On OWASP What Is OWASP?: Deep Nandu BED-C-48Документ4 страницыReport On OWASP What Is OWASP?: Deep Nandu BED-C-48deep nanduОценок пока нет
- Web App Sec Checklist 2012 enДокумент19 страницWeb App Sec Checklist 2012 enjnaguОценок пока нет
- A Survey of Web Security: Aviel D. Rubin Daniel E. Geer JRДокумент8 страницA Survey of Web Security: Aviel D. Rubin Daniel E. Geer JRNirmal Raj DeivasigamaniОценок пока нет
- Active Page ServerДокумент18 страницActive Page ServerZain Alabeeden AlarejiОценок пока нет
- Ismlabda 4Документ19 страницIsmlabda 4ARYA DUBEY 20BCE0908Оценок пока нет
- OWASP Top 10 - 2010 PresentationДокумент41 страницаOWASP Top 10 - 2010 PresentationCarlos SouzaОценок пока нет
- Ceh Chap8 QuizletДокумент2 страницыCeh Chap8 QuizletlynnverbОценок пока нет
- Module 4Документ47 страницModule 4omwaje2023Оценок пока нет
- Security Testing MatДокумент9 страницSecurity Testing MatLias JassiОценок пока нет
- What Is Web ApplicationДокумент5 страницWhat Is Web ApplicationVixivTomОценок пока нет
- Analysis of Security Issues in Web Applications Through Penetration TestingДокумент7 страницAnalysis of Security Issues in Web Applications Through Penetration Testingabdel_lakОценок пока нет
- PentestTools WebsiteScanner ReportДокумент5 страницPentestTools WebsiteScanner ReportmiguelОценок пока нет
- WAF / ModSec + OWASP CRSДокумент61 страницаWAF / ModSec + OWASP CRSAdzmely MansorОценок пока нет
- PentestTools WebsiteScanner ReportДокумент4 страницыPentestTools WebsiteScanner ReportdeldengcОценок пока нет
- OWASP Top 10 ThreatsДокумент35 страницOWASP Top 10 ThreatsJames Pierce100% (1)
- Developing A Semanic Architechure For Input Validation in E-SystemsДокумент8 страницDeveloping A Semanic Architechure For Input Validation in E-SystemsUbiquitous Computing and Communication JournalОценок пока нет
- Chapter 13: Hacking Web Servers: Technology BriefДокумент1 страницаChapter 13: Hacking Web Servers: Technology BriefKaren GarzaОценок пока нет
- PentestTools WebsiteScanner ReportДокумент4 страницыPentestTools WebsiteScanner Reportcatalina nicolinОценок пока нет
- Parameter Manipulation: Prev NextДокумент5 страницParameter Manipulation: Prev NextMoon XyleОценок пока нет
- Bug ReportДокумент5 страницBug ReportIRFAN SADIK 222-15-6545Оценок пока нет
- Web Browser Features and Risks: TrojanДокумент2 страницыWeb Browser Features and Risks: TrojanKrishna PandeyОценок пока нет
- Vuln ScanДокумент12 страницVuln ScanBrijendra Pratap SinghОценок пока нет
- Detailed Scan ReportДокумент23 страницыDetailed Scan ReportAnas YogieОценок пока нет
- Web Application DevelopmentДокумент15 страницWeb Application DevelopmentKamaljeet Lakhina100% (2)
- OWASP Top 10 - 2010 PresentationДокумент41 страницаOWASP Top 10 - 2010 PresentationThomas FouОценок пока нет
- 15067CEM ResitДокумент20 страниц15067CEM Resithoney arguellesОценок пока нет
- Owasp Top10 and Security FlawsДокумент60 страницOwasp Top10 and Security FlawsAndy WillamsОценок пока нет
- Barracuda WAFДокумент58 страницBarracuda WAFHoanghung Tran100% (1)
- WP Hacme Bank v2 User GuideДокумент74 страницыWP Hacme Bank v2 User GuideCesar Fabian MlОценок пока нет
- Ai Web Report 1 1Документ25 страницAi Web Report 1 1Suraj TheekshanaОценок пока нет
- Building Multi Tenant Java ApplicationsДокумент20 страницBuilding Multi Tenant Java ApplicationsTrần Đoàn Anh Quân100% (1)
- Assignment No 4Документ18 страницAssignment No 4Jusil T. GaiteОценок пока нет
- It Audit Chapter 8Документ16 страницIt Audit Chapter 8jmcverzola1004Оценок пока нет
- PCIDSS Over AWSДокумент5 страницPCIDSS Over AWSDaniyal SuriОценок пока нет
- Owasp Nist sp800 118 ResponseДокумент4 страницыOwasp Nist sp800 118 Responsememoona bibiОценок пока нет
- Web Application HackingДокумент9 страницWeb Application HackingAbraham ZelekeОценок пока нет
- WEB Application Security: Cse-AДокумент12 страницWEB Application Security: Cse-ASantoshi AlekhyaОценок пока нет
- Web Application Firewalls: Defense in Depth For Your Web InfrastructureДокумент6 страницWeb Application Firewalls: Defense in Depth For Your Web InfrastructureitscustomerОценок пока нет
- Penetration Test Result Summary - Web Site VulnerabilitiesДокумент17 страницPenetration Test Result Summary - Web Site Vulnerabilitiespride ezraОценок пока нет
- Developer ReportДокумент7 страницDeveloper ReportRaheelОценок пока нет
- PentestTools WebsiteScanner ReportДокумент5 страницPentestTools WebsiteScanner ReportSunil Kumar SharmaОценок пока нет
- ReportДокумент17 страницReportJay SoniОценок пока нет
- Suip - Biz: Localbitcoins Vds Donation FeedbackДокумент1 страницаSuip - Biz: Localbitcoins Vds Donation Feedbackryo020288Оценок пока нет
- Devouring Security: Marudhamaran Gunasekaran Dot Net Bangalore 3 Meet Up May 16 2015 at Prowareness, BangaloreДокумент40 страницDevouring Security: Marudhamaran Gunasekaran Dot Net Bangalore 3 Meet Up May 16 2015 at Prowareness, Bangaloressda103Оценок пока нет
- Final Project CYB 5665Документ14 страницFinal Project CYB 5665rhemacs3Оценок пока нет
- Securing Web PortalsДокумент12 страницSecuring Web PortalsPietro VivoliОценок пока нет
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldОт EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldОценок пока нет
- Guide BCP Labs Research FacilitiesДокумент60 страницGuide BCP Labs Research FacilitiesMondher GamОценок пока нет
- El Cristianismo y La EsclavitudДокумент422 страницыEl Cristianismo y La EsclavitudDaniel GLОценок пока нет
- Nsmxpress Quick Start PDFДокумент50 страницNsmxpress Quick Start PDFMondher GamОценок пока нет
- BCM Automation Guide: 5 Steps For Automating Your BC ProgramДокумент11 страницBCM Automation Guide: 5 Steps For Automating Your BC ProgramMondher GamОценок пока нет
- BIA Methodology - Sample Executive Summary - CДокумент21 страницаBIA Methodology - Sample Executive Summary - CMondher GamОценок пока нет
- Adding The Devices To NSMДокумент11 страницAdding The Devices To NSMMondher GamОценок пока нет
- Network Services J Series SRX Series Installation OverviewДокумент1 страницаNetwork Services J Series SRX Series Installation OverviewMondher GamОценок пока нет
- Book SRX Series Interfaces Hardware GuideДокумент214 страницBook SRX Series Interfaces Hardware GuideMondher GamОценок пока нет
- Nsmxpress Quick Start PDFДокумент50 страницNsmxpress Quick Start PDFMondher GamОценок пока нет
- 3500175-Implementing Policy-Based IPsec VPN Using SRX Series Services GatewaysДокумент27 страниц3500175-Implementing Policy-Based IPsec VPN Using SRX Series Services GatewaysPaul ChanОценок пока нет
- Email Greatest Advanced Threat InfographicДокумент1 страницаEmail Greatest Advanced Threat InfographicMondher GamОценок пока нет
- Web Filtering enДокумент16 страницWeb Filtering enbogatoffОценок пока нет
- 3500175-Implementing Policy-Based IPsec VPN Using SRX Series Services GatewaysДокумент27 страниц3500175-Implementing Policy-Based IPsec VPN Using SRX Series Services GatewaysPaul ChanОценок пока нет
- AV Gateway On SRX FirewallsДокумент16 страницAV Gateway On SRX FirewallsMondher GamОценок пока нет
- Junos Security Swconfig SecurityДокумент1 046 страницJunos Security Swconfig SecurityMondher GamОценок пока нет
- Juniper STRM Selling GuideДокумент2 страницыJuniper STRM Selling GuideMondher GamОценок пока нет
- Digital Resilience Seven Practices in Cybersecurity Digital McKinseyДокумент3 страницыDigital Resilience Seven Practices in Cybersecurity Digital McKinseyJohn evansОценок пока нет
- BitGo Keycard For My BitGo WalletДокумент2 страницыBitGo Keycard For My BitGo Walletangel80% (5)
- 1 CryptoДокумент313 страниц1 Cryptogarg0% (1)
- Phishing Demonstration Using GophishДокумент7 страницPhishing Demonstration Using GophishSandip DhitalОценок пока нет
- ICICI Bank PO Exam 2010 - Computer General Awareness Banking and CareerДокумент7 страницICICI Bank PO Exam 2010 - Computer General Awareness Banking and Careerkapeed_sup29% (7)
- Hcia Security Mock PDFДокумент5 страницHcia Security Mock PDFIct lab0% (1)
- Top 10 Internet Safety RulesДокумент1 страницаTop 10 Internet Safety RulesAnnie AntaranОценок пока нет
- PGP EncryptionДокумент10 страницPGP EncryptionKeerthana MОценок пока нет
- Protect Application or System SoftwareДокумент66 страницProtect Application or System SoftwareJaleto sunkemo75% (4)
- Signum Soft KeyloggerДокумент12 страницSignum Soft KeyloggerLukaRaterОценок пока нет
- Informative Speech - The Dark Web (Ali Ridzuan)Документ3 страницыInformative Speech - The Dark Web (Ali Ridzuan)Mohd Ali Ridzuan100% (1)
- CryptoДокумент15 страницCryptoNihar Ranjan PandaОценок пока нет
- Use of Honey-Pots To Detect Exploited Systems Across Large Enterprise NetworksДокумент22 страницыUse of Honey-Pots To Detect Exploited Systems Across Large Enterprise NetworksJohnBusigo MendeОценок пока нет
- Alienvault: I.T Security Vulnerabiliy Report Scan Time Generated Profile Job Name Hostname Host Ip ServiceДокумент10 страницAlienvault: I.T Security Vulnerabiliy Report Scan Time Generated Profile Job Name Hostname Host Ip ServiceOlga Lucia Rondon PerezОценок пока нет
- CEH BroucherДокумент2 страницыCEH BroucherManal SaeedОценок пока нет
- CCNA Security v20 Final Exam Answers 100Документ14 страницCCNA Security v20 Final Exam Answers 100JonathanОценок пока нет
- SOC AnalystДокумент28 страницSOC Analystcyberlearnhub24Оценок пока нет
- Network Security AssignmentДокумент3 страницыNetwork Security AssignmentJohn WirthОценок пока нет
- Gmail Login PageДокумент4 страницыGmail Login PagevidyaОценок пока нет
- Defend Against Web Attacks and Achieve Regulatory ComplianceДокумент15 страницDefend Against Web Attacks and Achieve Regulatory ComplianceTaryar OoОценок пока нет
- 8 Ways To Tweak and Configure Sudo On UbuntuДокумент9 страниц8 Ways To Tweak and Configure Sudo On UbuntuVictor Alexandru BusnitaОценок пока нет
- 11e Chp5 IMДокумент34 страницы11e Chp5 IMSrinivas AdityaОценок пока нет
- Computer Security ManualДокумент68 страницComputer Security ManualAlfred NjobvuОценок пока нет
- How To Report A Cyber Crime ComplaintДокумент15 страницHow To Report A Cyber Crime ComplaintSrinivas Reddy MaramОценок пока нет
- Key Establishment Protocols: Maithili NarasimhaДокумент50 страницKey Establishment Protocols: Maithili NarasimhaAnurag PandayОценок пока нет
- CNS SyllabusДокумент2 страницыCNS SyllabuslekhaОценок пока нет
- AnexGATE AG25Документ2 страницыAnexGATE AG25suman1410Оценок пока нет
- WRK6sol - PDF 3031Документ2 страницыWRK6sol - PDF 3031Munatsi Zimai0% (2)
- ISO27k Information Security Program Maturity Assessment ToolДокумент55 страницISO27k Information Security Program Maturity Assessment ToolalfarisiОценок пока нет
- IFS CHP 1Документ9 страницIFS CHP 1Sachin SinghОценок пока нет