Академический Документы
Профессиональный Документы
Культура Документы
CCNA Security Instructor Lab Manual v1 - p8
Загружено:
MeMe Amro0 оценок0% нашли этот документ полезным (0 голосов)
192 просмотров1 страницаCCNA Security Instructor Lab Manual v1_p8
Оригинальное название
CCNA Security Instructor Lab Manual v1_p8
Авторское право
© © All Rights Reserved
Доступные форматы
PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документCCNA Security Instructor Lab Manual v1_p8
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
192 просмотров1 страницаCCNA Security Instructor Lab Manual v1 - p8
Загружено:
MeMe AmroCCNA Security Instructor Lab Manual v1_p8
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 1
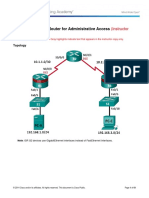
Lab - Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.
Step 3: Configure routing on the routers.
Static and dynamic routing protocols are used in different chapter labs. Please refer to the chapter
instructions to determine which routing protocol is used in each chapter lab.
Step 4: Configure PC host IP settings.
Configure a static IP address, subnet mask, and default gateway for PC-A and PC-C, as shown in the IP
addressing table.
Step 5: Verify connectivity between PC-A and R3.
a. Ping from R1 to R3.
If the pings are not successful, troubleshoot the basic device configurations before continuing.
b. Ping from PC-A on the R1 LAN to PC-C on the R3 LAN.
If the pings are not successful, troubleshoot the basic device configurations before continuing.
Note: If you can ping from PC-A to PC-C, you have demonstrated that static routing is configured and
functioning correctly. If you cannot ping but the device interfaces are up and IP addresses are correct, use the
show run and show ip route commands to help identify routing protocol-related problems.
Part 3: Router Access for CCP
In Part 3 of this lab, you will set up a router for use with CCP by enabling a secure HTTP server, creating a
privileged user account, and configuring a SSH and Telnet access.
Step 1: Connect to your router through Telnet or SSH or the console.
Enter the global configuration mode using the command:
Router> enable
Router# configure terminal
Step 2: Enable the router as a HTTP server.
a. Enable HTTP server.
Router(config)# ip http server
b. For a secure connection, enable the secure HTTP server.
Router(config)# ip http secure-server
% Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 3 seconds)
R1(config)#
*Jan 1 17:23:44.103: %SSH-5-ENABLED: SSH 1.99 has been enabled
*Jan 1 17:23:44.215: %PKI-4-NOAUTOSAVE: Configuration was modified. Issue
"write memory" to save new certificate
Note: A secure HTTP server can only be enabled for cryptography-enabled Cisco IOS Software images. It is
also possible to connect using an unsecure connection if the command ip http server is configured; however,
this is an unsecure connection and not recommended for production environments.
c.
Configure authentication for HTTP access using the local authentication.
Router(config)# ip http authentication local
2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public.
Page 7 of 12
Вам также может понравиться
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (119)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (265)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (399)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2219)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (890)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- Ccna TestДокумент30 страницCcna TestHoang Minh LamОценок пока нет
- Home Lab With Pfsense & VMware Workstation - OutsideSysДокумент13 страницHome Lab With Pfsense & VMware Workstation - OutsideSysnoahkrpgОценок пока нет
- Introduction To VoLTEДокумент30 страницIntroduction To VoLTEFrancisco Avila100% (1)
- CCNA Security Instructor Lab Manual v1 - p14Документ1 страницаCCNA Security Instructor Lab Manual v1 - p14MeMe AmroОценок пока нет
- IMS - Provisioning Guide For Retail v3.1Документ72 страницыIMS - Provisioning Guide For Retail v3.1Felipe Douglas de Paula100% (1)
- Aramex Location API Manual p3Документ1 страницаAramex Location API Manual p3MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p37Документ1 страницаCCNA Security Instructor Lab Manual v1 - p37MeMe AmroОценок пока нет
- Aramex Location API Manual p1Документ1 страницаAramex Location API Manual p1MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p37Документ1 страницаCCNA Security Instructor Lab Manual v1 - p37MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p36Документ1 страницаCCNA Security Instructor Lab Manual v1 - p36MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p35Документ1 страницаCCNA Security Instructor Lab Manual v1 - p35MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p38Документ1 страницаCCNA Security Instructor Lab Manual v1 - p38MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p22Документ1 страницаCCNA Security Instructor Lab Manual v1 - p22MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p20Документ1 страницаCCNA Security Instructor Lab Manual v1 - p20MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p39Документ1 страницаCCNA Security Instructor Lab Manual v1 - p39MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p13Документ1 страницаCCNA Security Instructor Lab Manual v1 - p13MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p16Документ1 страницаCCNA Security Instructor Lab Manual v1 - p16MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p19Документ1 страницаCCNA Security Instructor Lab Manual v1 - p19MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p15Документ1 страницаCCNA Security Instructor Lab Manual v1 - p15MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p7Документ1 страницаCCNA Security Instructor Lab Manual v1 - p7MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p12Документ1 страницаCCNA Security Instructor Lab Manual v1 - p12MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p11Документ1 страницаCCNA Security Instructor Lab Manual v1 - p11MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p4Документ1 страницаCCNA Security Instructor Lab Manual v1 - p4MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p10Документ1 страницаCCNA Security Instructor Lab Manual v1 - p10MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p9Документ1 страницаCCNA Security Instructor Lab Manual v1 - p9MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p5Документ1 страницаCCNA Security Instructor Lab Manual v1 - p5MeMe AmroОценок пока нет
- CCNA Security Instructor Lab Manual v1 - p6Документ1 страницаCCNA Security Instructor Lab Manual v1 - p6MeMe AmroОценок пока нет
- 6.2.2.5 Lab - Configuring IPv4 Static and Default RoutesДокумент7 страниц6.2.2.5 Lab - Configuring IPv4 Static and Default RoutesultracsokiОценок пока нет
- EX2300-C DatasheetДокумент9 страницEX2300-C DatasheethimmleroОценок пока нет
- 3-1 PROTOCOLS-Transmission Control ProtocolДокумент50 страниц3-1 PROTOCOLS-Transmission Control ProtocolnsadnanОценок пока нет
- VRF Fundamentals: Virtual Arubaos-Cx in Gns3Документ5 страницVRF Fundamentals: Virtual Arubaos-Cx in Gns3estiven gallego castañoОценок пока нет
- Sip Flex PTTДокумент660 страницSip Flex PTTShikha SharmaОценок пока нет
- VPNДокумент8 страницVPNblossomОценок пока нет
- MOCK EXAM 1-IДокумент5 страницMOCK EXAM 1-Irobertz_tolentino014Оценок пока нет
- CS F303 (Computer Networks) : Vishal GuptaДокумент26 страницCS F303 (Computer Networks) : Vishal Guptaabhishek reddyОценок пока нет
- Packet Tracer Troubleshooting Challenge Addressing TableДокумент2 страницыPacket Tracer Troubleshooting Challenge Addressing Tablekds20850Оценок пока нет
- Networking 1Документ28 страницNetworking 1rahul3071Оценок пока нет
- IPFIX Configuration: Maipu Confidential & Proprietary Information 1 of 15Документ15 страницIPFIX Configuration: Maipu Confidential & Proprietary Information 1 of 15vamsisanakaОценок пока нет
- TCP/IP Configuration Lab ActivityДокумент3 страницыTCP/IP Configuration Lab ActivityJuan Glicerio C. ManlapazОценок пока нет
- Connectionless Transport: UDPДокумент13 страницConnectionless Transport: UDPwl.01110111Оценок пока нет
- NethserverДокумент100 страницNethserverAzrael AjeetОценок пока нет
- SCTPДокумент87 страницSCTPHa Dinh ThanhОценок пока нет
- MPLS-TP: Overview and Status: Yoshinori KoikeДокумент45 страницMPLS-TP: Overview and Status: Yoshinori Koikevisakh21Оценок пока нет
- Introduction To SAN and NAS StorageДокумент8 страницIntroduction To SAN and NAS StoragePrashanth ChandranОценок пока нет
- Cisco ASA Oversubscription-Interface Errors Troubleshooting PDFДокумент19 страницCisco ASA Oversubscription-Interface Errors Troubleshooting PDFmasterone1810Оценок пока нет
- MPLS Label Distribution Protocol Configuration Guide, Cisco IOS Release 12.4TДокумент140 страницMPLS Label Distribution Protocol Configuration Guide, Cisco IOS Release 12.4TDouglas SanchezОценок пока нет
- Addressing and VLAN Configuration for HQ and HQ-SwДокумент9 страницAddressing and VLAN Configuration for HQ and HQ-SwAle Vera RossiОценок пока нет
- Parikshit HegdeДокумент4 страницыParikshit HegdeParikshit HegdeОценок пока нет
- FortiADC 4 3 0 Handbook D Series Revision2Документ308 страницFortiADC 4 3 0 Handbook D Series Revision2PabloОценок пока нет
- ALOHAДокумент26 страницALOHApranay639Оценок пока нет
- CCNP Route CheatsheetДокумент2 страницыCCNP Route CheatsheetVictor Cho67% (3)
- Oracle Linux 8 Setting Up NetworkingДокумент56 страницOracle Linux 8 Setting Up NetworkingChristopher KilaОценок пока нет
- Contoh SoalДокумент2 страницыContoh SoalAry Ou Try IIОценок пока нет