Академический Документы
Профессиональный Документы
Культура Документы
Blocking Facebook PDF
Загружено:
genuinОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Blocking Facebook PDF
Загружено:
genuinАвторское право:
Доступные форматы
Using a static URL filter to block access to a
specific website
When you allow access to a particular type of content, such as the FortiGuard Social
Networking category, there may still be certain websites in that category that you wish to
prohibit. In this example, you will learn how to configure a FortiGate to prevent access to
a specific social networking website, including its subdomains, by means of a static URL
filter. And by using SSL inspection, you ensure that this website is also blocked when
accessed through HTTPS protocol.
This example uses IPv4 security policies, but this method also works with IPv6 policies. Simply substitute any IPv4
configurations with IPv6 configurations.
1. Verifying FortiGuard Services subscription
2. Editing the Web Flter profile
3. Verifying the SSL inspection profile
4. Creating a security policy
5. Results
1. Verifying FortiGuard Services
subscription
Go to System > Dashboard >
Status.
In the License Information widget,
verify that you have an active
subscription to FortiGuard Web
Filtering. If you have a subscription,
the service will have a green
checkmark beside it.
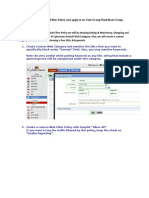
2. Editing the Web Filter profile
Go to Security Profiles > Web
Filter and edit the default Web Filter
profile.
Set Inspection Mode to Proxy.
Enable the FortiGuard Categories
that allow, block, monitor, warn, or
authenticate depending on the type of
content.
Learn more about FortiGuard
Categories at the FortiGuard
Center web filtering rating page:
www.fortiguard.com/static/
webfiltering.html
Under FortiGuard Categories, go to
General Interest - Personal. Right-
click on the Social Networking
subcategory and ensure it is set to
Allow.
To prohibit visiting one particular
social networking site in that category,
go to Static URL Filter, select
Enable URL Filter, and then click
Create New.
For your new web filter, enter the URL
of the website you are attempting to
block. If you want to block all of the
subdomains for that website, omit
the protocol in the URL and enter an
asterisk (*). For this example, enter:
*facebook.com
Set Type to Wildcard, set Action to
Block, and set Status to Enable.
3. Verifying the SSL inspection profile
Go to Policy & Objects > Policy >
SSL Inspection and edit the
certificate-inspection profile.
Ensure that CA Certificate is set to
the default Fortinet_CA_SSLProxy.
Ensure Inspection Method is set
to SSL Certificate Inspection and
SSH Deep Scan is set to ON.
4. Creating a security policy
Go to Policy & Objects > Policy >
IPv4, and click Create New.
Set the Incoming Interface to allow
packets from your internal network
and set the Outgoing Interface
to proceed to the Internet-facing
interface (typically wan1).
Enable NAT.
Under Security Profiles, enable
Web Filter and select the default
web filter.
This automatically enables SSL/SSH
Inspection.
Select certificate-inspection from
the dropdown menu.
After you have created your new
policy, ensure that it is at the top of
the policy list. To move your policy
up or down, click and drag the far left
column of the policy.
5. Results
Visit the following sites to verify that
your web filter is blocking websites
ending in facebook.com:
facebook.com
attachments.facebook.com
upload.facebook.com
camdencc.facebook.com
mariancollege.facebook.com
A FortiGuard Web Page Blocked!
page should appear.
Visit https://www.facebook.com to
verify that HTTPS protocol is blocked.
A Web Page Blocked! page should
appear.
Вам также может понравиться
- SSL VPN : Understanding, evaluating and planning secure, web-based remote accessОт EverandSSL VPN : Understanding, evaluating and planning secure, web-based remote accessОценок пока нет
- LAB 7 - Web Filtering PDFДокумент19 страницLAB 7 - Web Filtering PDFkaleabОценок пока нет
- FortiGate Security 7.0 Study Guide-Online 5Документ90 страницFortiGate Security 7.0 Study Guide-Online 5Esteban Alvares100% (1)
- ProxyДокумент5 страницProxyRoger ChavezОценок пока нет
- Smart FilterДокумент5 страницSmart FilterRoger ChavezОценок пока нет
- Surf ControlДокумент6 страницSurf ControlRoger ChavezОценок пока нет
- FortigateДокумент92 страницыFortigatekarcy24Оценок пока нет
- Content Filtering SolutionДокумент16 страницContent Filtering SolutionAnonymous NWFB3TОценок пока нет
- Web SenseДокумент5 страницWeb SenseRoger ChavezОценок пока нет
- LAB 6 - Certificate Operations PDFДокумент16 страницLAB 6 - Certificate Operations PDFkaleabОценок пока нет
- FortiGate Cookbook Part2Документ159 страницFortiGate Cookbook Part2m dickyОценок пока нет
- Fortigate Security - Cours-5Документ100 страницFortigate Security - Cours-5chaaben927Оценок пока нет
- How To Block Psiphon 3Документ4 страницыHow To Block Psiphon 3singgihkuntoОценок пока нет
- WAF0201 - Barracuda Web Application Firewall - Advanced Features - Lab GuideДокумент17 страницWAF0201 - Barracuda Web Application Firewall - Advanced Features - Lab GuideneoaltОценок пока нет
- LAb3 Security Firewall PoliciesДокумент18 страницLAb3 Security Firewall PoliciesCarlos MuñozОценок пока нет
- White Paper MS365 Security - Control - ChecklistДокумент5 страницWhite Paper MS365 Security - Control - ChecklistStefan AmarandeiОценок пока нет
- Configure Untangle Using Virtual MachineДокумент14 страницConfigure Untangle Using Virtual MachineRehan KhanОценок пока нет
- FW4010 19.5v1 Configuring Web Protection On Sophos FirewallДокумент32 страницыFW4010 19.5v1 Configuring Web Protection On Sophos FirewallAndré MouraОценок пока нет
- Managing DevicesДокумент14 страницManaging DeviceshoneybeeОценок пока нет
- NSE4 Study G-6Документ70 страницNSE4 Study G-6chaaben927Оценок пока нет
- How To Create Web Filter Policy and Apply It On UsДокумент6 страницHow To Create Web Filter Policy and Apply It On UsAjitОценок пока нет
- Publish OWA Using FortiWebДокумент8 страницPublish OWA Using FortiWebevaОценок пока нет
- Domain and Ip CheckДокумент14 страницDomain and Ip CheckkamalshrishОценок пока нет
- Content Filtering or Parental Control - SpectrumДокумент4 страницыContent Filtering or Parental Control - SpectrumChristian MengeleОценок пока нет
- Vyatta Web FilteringДокумент13 страницVyatta Web Filteringduranduran11Оценок пока нет
- High Performance Security Workshop: - Hands-On LabДокумент23 страницыHigh Performance Security Workshop: - Hands-On LabdanutzitОценок пока нет
- Deep Packet InspectionДокумент4 страницыDeep Packet Inspectionarieu00Оценок пока нет
- FortiGate Deployment Guide - Microsoft Entra ID - Microsoft LearnДокумент13 страницFortiGate Deployment Guide - Microsoft Entra ID - Microsoft LearnteinveniamОценок пока нет
- FortiClient 5.2 CookbookДокумент16 страницFortiClient 5.2 CookbookTrong Oganort GampoulaОценок пока нет
- How To Implement and Test SSL Decryption Palo Alto Networks LiveДокумент14 страницHow To Implement and Test SSL Decryption Palo Alto Networks LiveChau NguyenОценок пока нет
- Custom Response Pages RevCДокумент9 страницCustom Response Pages RevCMark AriasОценок пока нет
- LAB 9 - AntivirusДокумент13 страницLAB 9 - AntiviruskaleabОценок пока нет
- How To Implement SSL Decryption PDFДокумент11 страницHow To Implement SSL Decryption PDFvijoynew5233Оценок пока нет
- ???????? ??????? ?????????Документ28 страниц???????? ??????? ?????????jc.ovandoОценок пока нет
- Barracuda TechLibrary - How To Configure Proxy Settings Using Group Policy Management - Barracuda Web Security ServiceДокумент2 страницыBarracuda TechLibrary - How To Configure Proxy Settings Using Group Policy Management - Barracuda Web Security ServiceKamlesh Kumar MishraОценок пока нет
- Content Filter OverrideДокумент5 страницContent Filter OverrideRoger ChavezОценок пока нет
- How To - Configure SSL VPN in CyberoamДокумент9 страницHow To - Configure SSL VPN in CyberoamPeter Mugogo KaranjaОценок пока нет
- Setting Up YouTube For EducationДокумент6 страницSetting Up YouTube For EducationjmbrinesОценок пока нет
- Configure Ad Integration and Captive Portal Authentication. - Tech ZoneДокумент10 страницConfigure Ad Integration and Captive Portal Authentication. - Tech ZoneAkash ThakurОценок пока нет
- Fortinet Fortigate Workspot Configuration Guide 1.0Документ13 страницFortinet Fortigate Workspot Configuration Guide 1.0Abdelilah CharboubОценок пока нет
- Enable Disable VPNДокумент4 страницыEnable Disable VPNiheresalehОценок пока нет
- PAN9 EDU210 Lab 6Документ29 страницPAN9 EDU210 Lab 6GenestapowerОценок пока нет
- Palo Alto Lab Guide Net Dev GroupДокумент23 страницыPalo Alto Lab Guide Net Dev GroupJeevan Teza YadavОценок пока нет
- Pan8 Cybersecurity Essentials Lab 2: Configuring AuthenticationДокумент23 страницыPan8 Cybersecurity Essentials Lab 2: Configuring AuthenticationElbarni MohamedОценок пока нет
- How To - Configure SSL VPN in Cyberoam PDFДокумент13 страницHow To - Configure SSL VPN in Cyberoam PDFabouzinebОценок пока нет
- SANGFOR - IAM - v12.0.42 - Best Practices For Scenarios - SSL Content DecryptionДокумент17 страницSANGFOR - IAM - v12.0.42 - Best Practices For Scenarios - SSL Content DecryptionMelvin FoongОценок пока нет
- FortiClient v5.2.0 Windows Release NotesДокумент19 страницFortiClient v5.2.0 Windows Release NotesnexrothОценок пока нет
- Clientless SSL VPN (Webvpn) On Cisco Ios Using SDM Configuration ExampleДокумент22 страницыClientless SSL VPN (Webvpn) On Cisco Ios Using SDM Configuration ExampleMuhammad AdeelОценок пока нет
- Integration of Cisco - ISE - With - cnPilot-AP'sДокумент19 страницIntegration of Cisco - ISE - With - cnPilot-AP'slacerdatomОценок пока нет
- Fortigate Security - Cours-3Документ100 страницFortigate Security - Cours-3chaaben927Оценок пока нет
- Ad360 Security Privacy and Confidentiality MeasuresДокумент9 страницAd360 Security Privacy and Confidentiality MeasuresPrimeОценок пока нет
- Solutions: Problem DescriptionДокумент4 страницыSolutions: Problem DescriptionAnonymous STGJjklОценок пока нет
- Cuestionario Fortinet 2020 NS4 V6 - 2Документ18 страницCuestionario Fortinet 2020 NS4 V6 - 2Din CessareОценок пока нет
- BCS TB Safe Search - pdf.9Документ2 страницыBCS TB Safe Search - pdf.9Chau LhОценок пока нет
- Mcafee Web Gateway Cloud Service Product Guide 1-26-2022Документ50 страницMcafee Web Gateway Cloud Service Product Guide 1-26-2022migprada91Оценок пока нет
- Fortinet Single Sign On Polling Mode Windows AD Network PDFДокумент6 страницFortinet Single Sign On Polling Mode Windows AD Network PDFRizky WibowoОценок пока нет
- Fortinet Single Sign On Polling Mode Windows AD NetworkДокумент6 страницFortinet Single Sign On Polling Mode Windows AD NetworkRicky WallaceОценок пока нет
- HGFFDDДокумент2 страницыHGFFDDKatraj NawazОценок пока нет
- Silabus ArcGIS Server TutorialsДокумент2 страницыSilabus ArcGIS Server Tutorialswilly filkosima100% (1)
- 01 Appd SPSCLT Piller Drawings 28-04-2010Документ41 страница01 Appd SPSCLT Piller Drawings 28-04-2010cayunk7145Оценок пока нет
- PC-ITP-001 - Backfilling and ExcavationДокумент2 страницыPC-ITP-001 - Backfilling and ExcavationHusam zayedОценок пока нет
- Seminar Presentation On Cable Stayed BridgeДокумент26 страницSeminar Presentation On Cable Stayed BridgeSijan ShresthaОценок пока нет
- Skid ResistanceДокумент7 страницSkid Resistanceebinsams007Оценок пока нет
- Weld PreparationДокумент4 страницыWeld PreparationHelier Valdivia GuardiaОценок пока нет
- 02 - Theory of Architecture2 - Historic and Classical StylesДокумент29 страниц02 - Theory of Architecture2 - Historic and Classical Styleskyle vincentОценок пока нет
- Liquid Process Piping Design Strategy R2Документ16 страницLiquid Process Piping Design Strategy R2Masood Khan100% (1)
- Proposal FINALДокумент23 страницыProposal FINALGaming with cristineОценок пока нет
- Transformer Sizing CalculationДокумент6 страницTransformer Sizing CalculationAvijnan Mitra100% (3)
- Design Principles For Sarda Type and Straight Glacis FallДокумент12 страницDesign Principles For Sarda Type and Straight Glacis Fallshweta0% (1)
- HousekeepingДокумент45 страницHousekeepingSoriano D'cruz Rosanne100% (3)
- Case Study 1 2Документ12 страницCase Study 1 2Nishant KautilyaОценок пока нет
- New Text DocumentДокумент2 страницыNew Text DocumentNaj Kriztopher NoicnamaracОценок пока нет
- Designingbuildings Co - UkДокумент5 страницDesigningbuildings Co - UkbetraveОценок пока нет
- DG43NB Product BriefДокумент4 страницыDG43NB Product Briefign_handokoОценок пока нет
- Eaton Memguard Distribution System 160312 - UpdateДокумент32 страницыEaton Memguard Distribution System 160312 - UpdateKing RoodОценок пока нет
- The Wasatch Front Green Infrastructure PlanДокумент12 страницThe Wasatch Front Green Infrastructure PlanRick LeBrasseurОценок пока нет
- Tty10 02 TBДокумент26 страницTty10 02 TBDessy Safira SariОценок пока нет
- NCHRP W35-AДокумент152 страницыNCHRP W35-AJobz Pacleb100% (1)
- Smart Phone: An Embedded System For Universal InteractionsДокумент12 страницSmart Phone: An Embedded System For Universal InteractionsraghueshОценок пока нет
- SBOP PC 10 M AdminДокумент102 страницыSBOP PC 10 M Admintririna2002Оценок пока нет
- Building A SQL Server Test LabДокумент18 страницBuilding A SQL Server Test LabFazal Ur Rehman ShahОценок пока нет
- CMS Implementation PlanДокумент16 страницCMS Implementation PlanpranaypaiОценок пока нет
- File:///C:/Users/Asus Vivobook/Downloads/Article - For - Tas - Bit - Arsi PDFДокумент6 страницFile:///C:/Users/Asus Vivobook/Downloads/Article - For - Tas - Bit - Arsi PDFMuhammad LitilolyОценок пока нет
- Diskless CloningДокумент8 страницDiskless CloningArvie CaagaoОценок пока нет
- A. The Beginning of The PACO PNR Station, Rizal-The Paco Railroad Station Was BuiltДокумент8 страницA. The Beginning of The PACO PNR Station, Rizal-The Paco Railroad Station Was BuiltchristianОценок пока нет
- Focus 40 Keystroke Commands FINALДокумент30 страницFocus 40 Keystroke Commands FINALn1kskeОценок пока нет
- Final Annual Report 2018Документ31 страницаFinal Annual Report 2018Nirmal Kumar SharmaОценок пока нет