Академический Документы
Профессиональный Документы
Культура Документы
Part 1: Configure Ipsec Parameters On R1: Version Command
Загружено:
Arun TS0 оценок0% нашли этот документ полезным (0 голосов)
67 просмотров3 страницы.
Оригинальное название
2
Авторское право
© © All Rights Reserved
Доступные форматы
DOCX, PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документ.
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате DOCX, PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
67 просмотров3 страницыPart 1: Configure Ipsec Parameters On R1: Version Command
Загружено:
Arun TS.
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате DOCX, PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 3
2,4,8,
VPN – 8
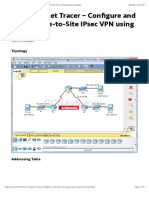
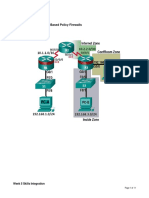
Part 1: Configure IPsec Parameters on R1
Step 1: Test connectivity.
Ping from PC-A to PC-C.
Step 2: Enable the Security Technology package.
a. On R1, issue the show version command to view the Security Technology package license
information.
b. If the Security Technology package has not been enabled, use the following command to
enable the package.
R1(config)# license boot module c1900 technology-package securityk9
c. Accept the end-user license agreement.
d. Save the running-config and reload the router to enable the security license.
e. Verify that the Security Technology package has been enabled by using the show
version command.
Step 3: Identify interesting traffic on R1.
Configure ACL 110 to identify the traffic from the LAN on R1 to the LAN on R3 as interesting. This
interesting traffic will trigger the IPsec VPN to be implemented when there is traffic between the
R1 to R3 LANs. All other traffic sourced from the LANs will not be encrypted. Because of the
implicit deny all, there is no need to configure a deny ip any any statement.
R1(config)# access-list 110 permit ip 192.168.1.0 0.0.0.255
192.168.3.0 0.0.0.255
Step 4: Configure the IKE Phase 1 ISAKMP policy on R1.
Configure the crypto ISAKMP policy 10 properties on R1 along with the shared crypto
key vpnpa55. Refer to the ISAKMP Phase 1 table for the specific parameters to configure.
Default values do not have to be configured. Therefore, only the encryption method, key
exchange method, and DH method must be configured.
Note: The highest DH group currently supported by Packet Tracer is group 5. In a production
network, you would configure at least DH 14.
R1(config)# crypto isakmp policy 10
R1(config-isakmp)# encryption aes 256
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 5
R1(config-isakmp)# exit
R1(config)# crypto isakmp key vpnpa55 address 10.2.2.2
Step 5: Configure the IKE Phase 2 IPsec policy on R1.
a. Create the transform-set VPN-SET to use esp-aes and esp-sha-hmac.
R1(config)# crypto ipsec transform-set VPN-SET esp-aes esp-sha-hmac
b. Create the crypto map VPN-MAP that binds all of the Phase 2 parameters together. Use
sequence number 10 and identify it as an ipsec-isakmp map.
R1(config)# crypto map VPN-MAP 10 ipsec-isakmp
R1(config-crypto-map)# description VPN connection to R3
R1(config-crypto-map)# set peer 10.2.2.2
R1(config-crypto-map)# set transform-set VPN-SET
R1(config-crypto-map)# match address 110
R1(config-crypto-map)# exit
Step 6: Configure the crypto map on the outgoing interface.
Bind the VPN-MAP crypto map to the outgoing Serial 0/0/0 interface.
R1(config)# interface s0/0/0
R1(config-if)# crypto map VPN-MAP
Part 2: Configure IPsec Parameters on R3
Step 1: Enable the Security Technology package.
a. On R3, issue the show version command to verify that the Security Technology package
license information has been enabled.
b. If the Security Technology package has not been enabled, enable the package and reload
R3.
Step 2: Configure router R3 to support a site-to-site VPN with R1.
Configure reciprocating parameters on R3. Configure ACL 110 identifying the traffic from the LAN
on R3 to the LAN on R1 as interesting.
R3(config)# access-list 110 permit ip 192.168.3.0 0.0.0.255
192.168.1.0 0.0.0.255
Step 3: Configure the IKE Phase 1 ISAKMP properties on R3.
Configure the crypto ISAKMP policy 10 properties on R3 along with the shared crypto key
vpnpa55.
R3(config)# crypto isakmp policy 10
R3(config-isakmp)# encryption aes 256
R3(config-isakmp)# authentication pre-share
R3(config-isakmp)# group 5
R3(config-isakmp)# exit
R3(config)# crypto isakmp key vpnpa55 address 10.1.1.2
Step 4: Configure the IKE Phase 2 IPsec policy on R3.
a. Create the transform-set VPN-SET to use esp-aes and esp-sha-hmac.
R3(config)# crypto ipsec transform-set VPN-SET esp-aes esp-sha-hmac
b. Create the crypto map VPN-MAP that binds all of the Phase 2 parameters together. Use
sequence number 10 and identify it as an ipsec-isakmp map.
R3(config)# crypto map VPN-MAP 10 ipsec-isakmp
R3(config-crypto-map)# description VPN connection to R1
R3(config-crypto-map)# set peer 10.1.1.2
R3(config-crypto-map)# set transform-set VPN-SET
R3(config-crypto-map)# match address 110
R3(config-crypto-map)# exit
Step 5: Configure the crypto map on the outgoing interface.
Bind the VPN-MAP crypto map to the outgoing Serial 0/0/1 interface. Note: This is not graded.
R3(config)# interface s0/0/1
R3(config-if)# crypto map VPN-MAP
2 – Logins
Books Marked login
Вам также может понравиться
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3От EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Оценок пока нет
- 3.4.1.2 Lab - Using Wireshark To View Network TrafficДокумент14 страниц3.4.1.2 Lab - Using Wireshark To View Network Trafficleul25% (16)
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОт EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationОценок пока нет
- Cisco Switch Security Configuration GuideДокумент86 страницCisco Switch Security Configuration GuideBen HetrickОценок пока нет
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityОт EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityОценок пока нет
- 8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorДокумент5 страниц8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorSalem TrabelsiОценок пока нет
- ISP Lab Tutorial - GNS3Документ19 страницISP Lab Tutorial - GNS3Ceh0% (1)
- Site To Site IPSEC VPN Troubleshooting - ImpДокумент8 страницSite To Site IPSEC VPN Troubleshooting - ImpAsifОценок пока нет
- Configuring Site To Site Ipsec VPN Tunnel Between Cisco RoutersДокумент6 страницConfiguring Site To Site Ipsec VPN Tunnel Between Cisco RoutersSyed AliОценок пока нет
- RTNДокумент18 страницRTNAwais Tahir100% (7)
- Configure and Verify Site-to-Site IPsec VPNДокумент8 страницConfigure and Verify Site-to-Site IPsec VPNAkram AliОценок пока нет
- ITT300 - Tutorial Chapter 3Документ6 страницITT300 - Tutorial Chapter 3Christopher Johnson91% (11)
- 7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsДокумент5 страниц7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsEncikPandaSiriusОценок пока нет
- Configure and Verify A Site-To-Site IPsec VPN Using CLIДокумент6 страницConfigure and Verify A Site-To-Site IPsec VPN Using CLIMilošKovačevićОценок пока нет
- Yasser Auda CCIEv5 WorkbookДокумент26 страницYasser Auda CCIEv5 WorkbookphamvanhaОценок пока нет
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersДокумент7 страницConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersIwatch YouОценок пока нет
- IPSec VPN LABДокумент7 страницIPSec VPN LABAparna Garg100% (2)
- NR Protocol Stack Architecture and QoS FrameworkДокумент10 страницNR Protocol Stack Architecture and QoS FrameworkVishal VenkataОценок пока нет
- IPSec VPNДокумент5 страницIPSec VPNcciersmanОценок пока нет
- 7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsДокумент6 страниц7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsParitosh KumarОценок пока нет
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersДокумент4 страницыConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarОценок пока нет
- Configuring Point-To-Point GRE VPN Tunnels - Unprotected GRE & Protected GRE Over IPSec TunnelsДокумент7 страницConfiguring Point-To-Point GRE VPN Tunnels - Unprotected GRE & Protected GRE Over IPSec Tunnelsst_kannanОценок пока нет
- Technical ReportДокумент19 страницTechnical ReportUsmanОценок пока нет
- 8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLIДокумент5 страниц8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLITalha Ur RehmanОценок пока нет
- Configure and Verify A Site To Site IPsec VPN Using CLIДокумент4 страницыConfigure and Verify A Site To Site IPsec VPN Using CLICristhian HadesОценок пока нет
- TP8-Configure and Verify A Site-to-Site IPsec VPN Using CLIДокумент11 страницTP8-Configure and Verify A Site-to-Site IPsec VPN Using CLIkaw birthdayОценок пока нет
- Lab Cisco VPN-GenericДокумент2 страницыLab Cisco VPN-Genericbliss21100% (5)
- 16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersДокумент6 страниц16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersimen loussaiefОценок пока нет
- Configuration On Router1 Set Isakmp Policy Enable (Site To Site VPN)Документ7 страницConfiguration On Router1 Set Isakmp Policy Enable (Site To Site VPN)Varun MalhotraОценок пока нет
- 19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersДокумент5 страниц19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersAna Maria Citlali Diaz HernandezОценок пока нет
- Lab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysДокумент6 страницLab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysKishore Reddy KandiОценок пока нет
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersДокумент6 страницConfiguring Site To Site IPSec VPN Tunnel Between Cisco Routerskymk21Оценок пока нет
- Báo cáo cuối kì môn thực hành an ninh mạngДокумент5 страницBáo cáo cuối kì môn thực hành an ninh mạngDương Thành ĐạtОценок пока нет
- 7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsДокумент5 страниц7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsSergio CastañedaОценок пока нет
- Practical 8Документ8 страницPractical 8riyevas163Оценок пока нет
- Lan2lan VPNДокумент6 страницLan2lan VPNFelix BlasioОценок пока нет
- Configure GRE Tunnels over IPsecДокумент18 страницConfigure GRE Tunnels over IPsecWING KIN LEUNGОценок пока нет
- Apuntes CCNA SecurityДокумент7 страницApuntes CCNA SecuritySantiago Balaguer GarcíaОценок пока нет
- Practical Walk ThroughДокумент9 страницPractical Walk ThroughtjduffieОценок пока нет
- InteropДокумент6 страницInteropSaurav LodhОценок пока нет
- 4.1 4-S2S-IPSecVPN-Tunnel-RouterДокумент6 страниц4.1 4-S2S-IPSecVPN-Tunnel-Routeramit_post2000Оценок пока нет
- S13.s2 - Guia de VPN - IPSec - Acceso RemotoДокумент17 страницS13.s2 - Guia de VPN - IPSec - Acceso RemotoYuri MarroquínОценок пока нет
- Ipsec VPN Requirements: Configure Isakmp (Ike) - (Isakmp Phase 1)Документ4 страницыIpsec VPN Requirements: Configure Isakmp (Ike) - (Isakmp Phase 1)Om PuriОценок пока нет
- Creacion VPN IPSECДокумент2 страницыCreacion VPN IPSECCarlos Amaranti GonzálezОценок пока нет
- 8 4 1 3 Lab Configure Site To Site VPN Using CLI InstructorДокумент15 страниц8 4 1 3 Lab Configure Site To Site VPN Using CLI InstructorMujeeb Rahman DostОценок пока нет
- Lab VPNДокумент9 страницLab VPNhung kungОценок пока нет
- SiC Manual (E-Next - In)Документ71 страницаSiC Manual (E-Next - In)Instagram OfficialОценок пока нет
- Somesh Kale Roll No 630 SICДокумент66 страницSomesh Kale Roll No 630 SICSomesh kaleОценок пока нет
- Convert Serial To IPsec VPNДокумент6 страницConvert Serial To IPsec VPNĐỗ Văn Tùng0% (1)
- Week 5 - Skills ActivityДокумент11 страницWeek 5 - Skills ActivitykonoweОценок пока нет
- 11.3.1.1 Packet Tracer - Skills Integration ChallengeДокумент6 страниц11.3.1.1 Packet Tracer - Skills Integration ChallengeShamsul ArefinОценок пока нет
- 4.3.9 Packet Tracer Configure Site To Site VPN Answer KeyДокумент4 страницы4.3.9 Packet Tracer Configure Site To Site VPN Answer Keymalaklmawt0000Оценок пока нет
- 20.2.1 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ILMДокумент6 страниц20.2.1 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ILMandres.fantinОценок пока нет
- Case Study 1&2 AnswersДокумент12 страницCase Study 1&2 AnswersudnuwanОценок пока нет
- Verifications Lab 6Документ9 страницVerifications Lab 6Shamsa WaqasОценок пока нет
- Vlan SSH ConfigureДокумент7 страницVlan SSH ConfigureДмирий МысовОценок пока нет
- 20.1.2 Lab Configure Secure DMVPN TunnelsДокумент11 страниц20.1.2 Lab Configure Secure DMVPN Tunnelshassa nestor theraОценок пока нет
- Configure Cisco Routers For Syslog, NTP, and SSH OperationsДокумент6 страницConfigure Cisco Routers For Syslog, NTP, and SSH OperationsMilošKovačevićОценок пока нет
- Configure Basic Router Settings LabДокумент11 страницConfigure Basic Router Settings Labumang patnaikОценок пока нет
- 13-F - W Config, VPN Config, IOS IPS Configuration, Hardware F - w-14-03-2024Документ7 страниц13-F - W Config, VPN Config, IOS IPS Configuration, Hardware F - w-14-03-2024Mukund KeshanОценок пока нет
- SIC Practical1 by STUD - TalksДокумент9 страницSIC Practical1 by STUD - TalksPradeep PrajapatiОценок пока нет
- Lab 3 WorksheetДокумент11 страницLab 3 Worksheetpzydf6wjxvОценок пока нет
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОт EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkОценок пока нет
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingОт EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingОценок пока нет
- Configure NTP, OSPF, logging and SSH on routers R1, R2 and R3Документ2 страницыConfigure NTP, OSPF, logging and SSH on routers R1, R2 and R3Lars Rembrandt50% (2)
- Configuring Switch To Use SSHДокумент1 страницаConfiguring Switch To Use SSHArun TSОценок пока нет
- Changing Switch HostnameДокумент2 страницыChanging Switch HostnameArun TSОценок пока нет
- Selecting An Erp Whitepaper PDFДокумент14 страницSelecting An Erp Whitepaper PDFamer_wahОценок пока нет
- ITECH SolutionsДокумент1 страницаITECH SolutionsArun TSОценок пока нет
- BDA-Lunch-Learn-PPT-2018 With MAPДокумент48 страницBDA-Lunch-Learn-PPT-2018 With MAPculeros1Оценок пока нет
- # Cellphones - The Evolution of Communication and ConnectivityДокумент3 страницы# Cellphones - The Evolution of Communication and ConnectivityMax AladjemОценок пока нет
- A Multi-Channel Electromyography ElectrocardiograpДокумент27 страницA Multi-Channel Electromyography ElectrocardiograpVizaОценок пока нет
- Sap Netweaver Process Orchestration, Business-To-Business Add-On 1.0 For (New and Changed)Документ5 страницSap Netweaver Process Orchestration, Business-To-Business Add-On 1.0 For (New and Changed)subraiОценок пока нет
- Lab Report FinalДокумент23 страницыLab Report FinalSampath ReddyОценок пока нет
- Codan Envoy HF Smart Radio EN2Документ3 страницыCodan Envoy HF Smart Radio EN2dot16eОценок пока нет
- Schematic MTK8223L1Документ9 страницSchematic MTK8223L1Sunil Malik100% (3)
- HP 2920 Switch Series StackingДокумент17 страницHP 2920 Switch Series StackingAlexander GarcíaОценок пока нет
- Infoblox Ecosystem - Solution NoteДокумент5 страницInfoblox Ecosystem - Solution NoteCse 2k17Оценок пока нет
- BIG-IP Link Controller ImplementationsДокумент80 страницBIG-IP Link Controller ImplementationsmlaazimaniОценок пока нет
- BroadcastingProclamation 533,2007Документ22 страницыBroadcastingProclamation 533,2007Segniwork LemmaОценок пока нет
- Wi-Fi - The Wireshark WikiДокумент3 страницыWi-Fi - The Wireshark Wikidsr321Оценок пока нет
- CUCM BK C95ABA82 00 Admin-Guide-100 Appendix 01101101Документ8 страницCUCM BK C95ABA82 00 Admin-Guide-100 Appendix 01101101Richard BIDZOUEОценок пока нет
- TAPPIT SERVER NETWORK ARCHITECTUREДокумент1 страницаTAPPIT SERVER NETWORK ARCHITECTUREHarun ParamasivamОценок пока нет
- Asus m50vm - SCДокумент96 страницAsus m50vm - SCAbubakar SidikОценок пока нет
- PpoeДокумент6 страницPpoeionizareОценок пока нет
- MAC LTD - CRIBS (TM) TETRA Walk-Test and Drive-Test SolutionДокумент2 страницыMAC LTD - CRIBS (TM) TETRA Walk-Test and Drive-Test SolutionFederico MaggiОценок пока нет
- La 76832Документ39 страницLa 76832carbalin5622Оценок пока нет
- 4.2.1.3 Packet Tracer - Configuring EtherChannelДокумент11 страниц4.2.1.3 Packet Tracer - Configuring EtherChannelTdd SanaОценок пока нет
- Internet of Things Iot 4 Converted (2) PPTДокумент3 страницыInternet of Things Iot 4 Converted (2) PPTdivya jainОценок пока нет
- L (G) M (X) M4 (X) 6 60 (24 58)Документ7 страницL (G) M (X) M4 (X) 6 60 (24 58)Christopher MendesОценок пока нет
- Infoblox Deployment Guide Infoblox Network Insight Integration With Cisco Aci PDFДокумент17 страницInfoblox Deployment Guide Infoblox Network Insight Integration With Cisco Aci PDFoscarledesmaОценок пока нет
- Cost Current Coverage Capacity Four C's of LPWA : Standards-Based AdvantagesДокумент1 страницаCost Current Coverage Capacity Four C's of LPWA : Standards-Based Advantagesrene_brookeОценок пока нет
- Uniden Bearcat Scanner BC365CRS Owners ManualДокумент32 страницыUniden Bearcat Scanner BC365CRS Owners ManualBenjamin DoverОценок пока нет
- Supernetting Tutorial - Supernetting Explained With ExamplesДокумент17 страницSupernetting Tutorial - Supernetting Explained With ExamplesHadi FahdОценок пока нет