Академический Документы
Профессиональный Документы
Культура Документы
PVT 2012 Lab Cisco Jabber PDF
Загружено:
Sid Ali Oulad SmaneОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
PVT 2012 Lab Cisco Jabber PDF
Загружено:
Sid Ali Oulad SmaneАвторское право:
Доступные форматы
Cisco Jabber Lab
Lab Guide
version 3.2
Collaboration SE VT Meeting
May 2012
Cisco Jabber Lab Page 1
Lab Guide authors
For any feedback or questions please contact the following persons:
Fabio Chiesa (fchiesa@cisco.com) - CSE, EMEAR Theatre Technical Services Team
Tobias Neumann (tneumann@cisco.com) – TSA, EMEAR Central Collaboration Team
Lab Topology
Lab topology is shown on a diagram below. Each student has his own set of terminals in his POD.
Cisco Jabber Lab Page 2
Lab Hosts, IP Addresses, Usernames, Passwords
Servers, PC and Infrastructure - Hostnames and IP addresses
IP address
SERVER Hostname
(Private)
AD DC (WS2008R2) ad01-bc.bootcamp.com 10.52.226.68
CUCM 9.0 cucm01-bc.bootcamp.com 10.52.226.70
IM&Presence 9.0 cup01-bc.bootcamp.com 10.52.226.71
Exchange 2010 exchange01-bc.bootcamp.com 10.52.226.73
PC 1(AADAMS) 10.52.226.76
PC 2(BBANKS) 10.52.226.77
PC 3(CCHUNG) 10.52.226.78
Servers, PC and Infrastructure – Credential to use to logon
SERVER Username Passsword
AD DC (WS2008R2) bootcamp\administrator C1sc0,123
CUCM 9.0 cucmadmin C1sc0,123
IM&Presence 9.0 cucmadmin C1sc0,123
Exchange 2010 bootcamp\administrator C1sc0,123
PC 1(AADAMS) bootcamp\aadams cisco,123
PC 2(BBANKS) bootcamp\bbanks cisco,123
PC 3(CCHUNG) bootcamp\cchung cisco,123
Note: the AD domain is “Bootcamp”, the email domain is “Bootcamp.com”.
Lab Numbering Plan
General principles of lab Dialplan inside each POD
Extension
Device IM address (XMPP) Extension (Private) (E164)
Alice Adams aadams@bootcamp.com 100 +498115543100
Bob Banks bbanks@bootcamp.com 200 +498115543200
Cathy Chung cchung@bootcamp.com 300 +498115543300
Tobias Neumann tneumann@bootcamp.com 400 +498115543400
Fabio Chiesa fchiesa@bootcamp.com 500 +498115543500
Cisco Jabber Lab Page 3
Agenda
1. CUP/CUCM 9.0 - infrastructure configuration
a. CUCM 9.0 and the new Enterprise Licensing Manager
b. Check configuration on IM&Presence node
c. Check configuration on CUCM side
2. DNS configuration
a. Host Names and SRV resolution for automatic client logon
b. How to check SRV record configuration is correct?
3. Basic AD Integration & Tuning
a. Check AD Configuration for Users
b. CUCM AD/LDAP sync and authentication
c. EDI configuration (Default)
d. E164 Number Normalization (Translation Pattern)
4. CUCM/CUP - User & Device configuration
a. Define Service Profile for Policy setting (EDI)
b. Define new CSF devices for the users
c. User activation for IM/Presence/Audio/Video/BFCP
5. Jabber installation and logon
a. Standard client installation on first two PC
b. Client Logon and Test (Buddy list, chat, call, Desktop Sharing using BFCP)
c. MSI Customization during Install on Third PC
d. Client Logon and Test (Buddy list, chat, call, Desktop Sharing using BFCP)
Cisco Jabber Lab Page 4
6. Photo integration Option 1
a. Upload Binary Object in AD using Exchange MMS
b. Binary Object for Photo in AD – default behavior
7. Photo integration Option 2
a. Upload Photo on Web Server
b. Configure URL Substitution method for Photo retrieval
c. Force user Alice Adams to use this method
8. Exchange & Outlook Integration
a. Run AD script for User SIP attribute
9. Directory Lookup Rules to complete Photo Integration in alerting and connected call status.
a. Define Directory Lookup rules and apply to all the users
10. Using CUCM User Data Service (UDS) for Directory Integration and Photo Lookup
a. UDS Service Profile configuration
b. Change Bob Banks’s Service Profile to force the use of UDS
c. Force Bob Banks to use method 2 for photo retrieval customized for UDS
11. Adding Custom Embedded Tab
12. New Provisioning method to enable User for IM&Presence and deploy CSF devices
a. Define Universal Device Template
b. Define Feature Group Template
c. Enable User for IM&Presence and create CSF device using the new provisioning method
Cisco Jabber Lab Page 5
Cisco Jabber Lab – Module 1
CUP/CUCM 9.0 - infrastructure configuration
Important NOTE: Due to small amount of time we have for the lab, this chapter has
been already pre-configured for you so please follow the guide, check the
configuration on the machines but not change or repeat the configuration itself.
CUCM 9.0 Cluster - Enterprise Licensing
CUCM version 9.0 provides a new licensing mechanism called Enterprise Licensing Manager (ELM). ELM
comes as a service which runs on a CUCM node in the cluster. It provides a single place of licensing control
for the entire system. It includes the user licensing for CUCM, CUCM IM & Presence, Cisco Unity Connection.
Accessing ELM and adding feature servers to the license manager
For the purpose of the lab we have a single node CUCM cluster (publisher). This machine also runs ELM. To
access ELM go to the base URL http://cucm01-bc.bootcamp.com (http://10.52.226.70), from there you can
select the ELM web-interface.
1. Main CUCM 9.0 browser interface
ELM can be accessed via the logon screen shown below utilizing the CUCM administrator ID and password.
Cisco Jabber Lab Page 6
2. CUCM 9.0 Enterprise License Manager Logon Screen
After logon the ELM dashboard provides an overview of the configured components and the licenses in use.
3. CUCM 9.0 Enterprise License Manager Dashboard
First task is to add the product instances aka server components such as CUCM clusters or Cisco Unity
Connection servers to the inventory. Select Inventory -> Product Instances from the left navigation menu.
After a fresh install there should not be any entries. Choose Add from the top row to add our CUCM
instance. In the dialog shown below the parameters are entered to define what product is added to ELM and
the required information for ELM to connect to this instance is provided.
Cisco Jabber Lab Page 7
4. Add Product to ELM Dialog
The Test Connection button provides the means to verify that all parameters have been entered correctly.
1. ELM Add Product Test Connection successful
5. ELM Add Product Test Connection
Product instances now show a new instance of CUCM that is not yet synchronized (Synchronization Status
column).
6. ELM Product Instance overview
Select the row with CUCM01-BC and press the Synchronize Now button to initiate the synchronization.
Cisco Jabber Lab Page 8
7. ELM Product Instance Synchronization complete
CUCM IM & Presence (formerly known as CUP)
With the Cisco Collaboration System Release 9.0 IM and presence functionality are started to be integrated
into the CUCM cluster. Providing a single instance of control for IM, presence, voice and video. In release 9.0
the first steps have been taken to consolidate the server platforms - this will continue in future releases and
further reduce complexity resulting in better ROI and TCO. Certain changes in administrating the Cisco
Collaboration platform have been made to accommodate the architectural changes.
Configuration pre-9.0 and post 9.0 – Certain changes outlined in the following chapters describe how
the Cisco Collaboration platform is administered running version 9.0 and above (CUCM and CUCM
IM & Presence). It needs to be noted that the first version of Cisco Jabber for Windows (9.0.1) will
not fully pickup all the new configuration methods and the corresponding parameters. Full support
for the post-9.0 configuration methods is planned for a future release of Cisco Jabber for Windows.
In this guide where ever possible pre-9.0 and post-9.0 configuration methods are explained.
CUCM IM & Presence – basic post install configuration
In Cisco Unified Communications 9.0 continues to maintain a database synchronization between the CUCM
publisher and the first CUCM IM & Presence node. This is similar to the relationship between CUCM and CUP
in earlier versions.
CUCM Publisher – define CUCM IM & Presence Server, define Application User, Setup & Service
Activation
All nodes in the CUCM cluster utilize IPsec authenticated communication. Each new node has to be added to
the CUCM publisher before it can be activated.
https://cucm01-bc.bootcamp.com/ccmadmin navigate to System -> Application Server and select Add New
Cisco Jabber Lab Page 9
8. CUCM publisher add application server CUCM IM & Presence
Database synchronization utilizes the CUCM AXL API for that reason the service needs to be activated and
started on the CUCM publisher node and an AXL enabled application user must be provided.
Warning!!! The default CUCM administration user created during install does have the required
privileges and could be utilized for this purpose. As a best practice this chapter shows the creation of
a distinct user that ONLY has the required privileges for this purpose.
From https://cucm01-bc.bootcamp.com/ccmadmin navigate to User Management -> Application User
1. CUCM Create Database-Sync AXL Application User
Select Add New and enter the parameters as show in the figure below.
Cisco Jabber Lab Page 10
On the bottom of the page select Add to
Access Control Group
2. User Access Control Group
2. Add New Application User details
Select only the Standard TabSync User
group
CUCM Serviceability – verify that the AXL service is activated (the other services shown are already activated
for other parts of the lab to function).
3. CUCM Services – Activation CM Service
4. CUCM Services – Activation Database and Admin Services
Cisco Jabber Lab Page 11
5. CUCM Services – Directory Services
CUCM IM & Presence – Post Install Dialog
After the installation of CUCM IM & Presence is completed when logging into the administrative web-
interface (https://cup01-bc.bootcamp.com/cupadmin) for the first time the post-install dialog is presented.
Through this dialog the CUCM IM & Presence node is added to the CUCM cluster and synchronization is
established. First to pages of the dialog below show the connectivity parameters and the CUCM cluster
security password needs to be entered.
3. CUCM IM & Presence Post Install Page 2
6. CUCM IM & Presence Post Install Page 1
Next the application user configured in the previous chapter is configured. Final screen shows the summary
of all parameters configured.
7. CUCM IM & Presence Post Install Page 3 4. CUCM IM & Presence Post Install Summary
Cisco Jabber Lab Page 12
Cisco Jabber Lab – Module 2
IMPORTANT NOTE: ….YOU MUST CONFIGURE ALL THE ITEMS OF THIS CHAPTER ON
THE MACHINES!
Service Discovery - DNS Configuration
Cisco Jabber for Windows provides fully automatic service discovery. DNS SRV (Service Location) records are
utilized to provide these capabilities. SRV allows a universal location of services, it can be seen as an
evolutionary step form MX records which are used to locate SMTP (e-mail) hosts for the domains. The client
needs to know the well-known service name (in our case it is _cuplogin) and a protocol (in our case _tcp).
The result of SRV DNS query is a host name (or list of those), with parameters of priority, weight and port
number.
Notice the underscore character is used to avoid collisions in host names as per RFC2872 (“_” is illegal
character for A and PTR DNS records).
In this lab we run DNS Server on the Active Directory Domain Controller. You are supposed to configure it on
that machine
Configuring DNS SRV
Configure the DNS SRV records based on a Microsoft Windows Server 2008 R2, as per example below. As the
lab consists only of a single server deployment there is only one SRV entry. In environments where multiple
servers are deployed additional SRV records provide redundancy.
To do that please go in RDP to the AD/DC server where also DNS is running, launch the DNS management
console. Right click the bootcamp.com domain and select Other New Records…, scroll down the list, select
Service Location (SRV) and click Create Record… In the SRV record window enter the service name will be
_cuplogin, protocol _tcp and port 8443. The port can be left to <Blank> to use the client’s default value
(8443).
In our case, the host offering this service is going to be cup01-bc.bootcamp.com, so please populate the
related field with this value.
Note: Please note that the “service” and “Protocol” field must be manually populated, you will not find
the values pre-configured in the drop down menu items….
Cisco Jabber Lab Page 13
1. Windows Server 2008 R2 DNS SRV configuration
How to verify the DNS SRV configuration
NSLOOKUP can be used to verify that the SRV records are correctly configured. This is particular important in
environments where DNS configuration is handled by different organizational entities.
By default the NSLOOKUP tool queries either DNS A records - mapping a name to an IP address or PTR
records mapping IP address to DNS names.
First start nslookup (in the example for windows start a command prompts and enter nslookup).
Next set the query type to SRV -> set type=SRV
> _cuplogin._tcp.bootcamp.com
This will return the DNS A records pointing to CUCM IM & Presence
Cisco Jabber Lab Page 14
2. DNS SRV records verification
The machine in the example above had IPv6 enabled, which is not required and can be ignored to the
purpose of this exercise.
Cisco Jabber Lab Page 15
Cisco Jabber Lab – Module 3
Basic AD Integration & Tuning
Important NOTE: Due to small amount of time we have for the lab, the first part of
the chapter has been already pre-configured for you so please follow the guide,
check the configuration on the machines but not change or repeat the configuration
itself.
In this module, the student will focus on integrating CUCM with the AD infrastructure. First we will configure
the CUCM integration with AD for user sync and authentication and then we will start to configure one of the
two possible mode (EDI/UDS) for contact search in AD from the Jabber client and in particular the default
one (EDI).
Let’s start with a basic AD integration for User Sync and Authentication.
On the CUCM, create a new LDAP system under System -> LDAP -> LDAP System
Cisco Jabber Lab Page 16
Then go to the LDAP Directory configuration (System -> LDAP -> LDAP Directory ) and add a new profile
with the following parameters:
Then go to the LDAP Authentication configuration (System -> LDAP -> LDAP Authentication ) and add a
new profile with the following parameters:
Cisco Jabber Lab Page 17
Once configured go to previous menu (LDAP Directory) and force a manual update.
When the system has finished to sync go to the user page and check that all the users information has been
synced. Check also the information that are synced from AD in the user page (email, Department, etc..)
Cisco Jabber Lab Page 18
Important NOTE: Pre-configured tasks stop here so ….Starting from the next step
you have to configure all the items on the machines!
As you can notice in the AD the phone number are in +E164 format. Being the extension associate to the
users a private one with 3 digits we need to configure a Translation Pattern to translate between the two
formats. This will permit us to use and the number that are in the AD, strip the prefix and map to the internal
extensions assigned to Jabber devices.
Go to the Translation Pattern (TP) menu under Call Routing menu and add a new one:
Cisco Jabber Lab Page 19
Cisco Jabber Lab Page 20
Now next step will be to define the new Service Profiles that will be downloaded from Jabber client and will
include several configuration parameters to be used for contact search and other stuff.
Cisco Jabber Lab Page 21
Cisco Jabber Lab – Module 4
CUCM/CUP - User & Device configuration
In this module, the student will focus on creating the CSF device for the two Jabber users plus creating all the
other Policy and Template needed to pass the right parameters to the clients. Last, all these elements will be
associated to the users.
Let’s start creating the CSF devices needed for Jabber to work in Softphone Mode. Add a new CSF device for
User Alice Adams adding all the following parameters:
NOTE that BFCP is active by default for CSF devices with CUCM 9.0 so you don’t need to modify the
standard SIP Profile assigned to the device itself.
Cisco Jabber Lab Page 22
Cisco Jabber Lab Page 23
Here pay attention to enable/disable CSF for Video if this is a requirement.
Cisco Jabber Lab Page 24
Now you can add a new line (ext. 100) to the CSF device just created, clicking on the “Add a New DN” button
on the top left angle of the page:
You will now see the full Directory Number page configuration, you must change only the parameters
reported in the pages below, leaving the other to the default values:
Cisco Jabber Lab Page 25
After saving the line configuration (Pressing the Save button), scroll down to the end of the page and
associate the end user with the line.
Repeat the same steps for Bob Banks and Cathy Chung. All the related informations are reported in the User
Table at page 3.
Cisco Jabber Lab Page 26
Introduction to Service Profile Concept
A service profile is a logical collection of UC services defined by a UC administrator. A profile can be
comprised of one or more services and assigned to users.
The Administrator defines a service profile that includes voice mail, presence, conferencing, CTI
server information.
The Administrator synchronizes the users from LDAP directory (note this is not mandatory although
it is highly recommended).
For LDAP Synced users in 9.0, the “Home Cluster” and “IM and Presence Enable” flags must be done
manually via the End User Configuration Page or via BAT.
The Administrator should mark one service profile as the default so that all users will get this service
profile without having to do any per-user association.
Users that require profiles other than the default will need to be manually associated from either the
End User Configuration page or via BAT.
Service configuration is done in the UC Service configuration page accessed from the User Management
User Settings UC Service menu. Once services have been defined they can be added to an existing or new
service profile.
Service Profile configuration is done in the Service Profile configuration page accessed from User
Management User Settings Service Profile menu. Once created there is an check-box at the top of the
page to make this the default service profile for the system. It is recommended that this is done for at least
one service profile per cluster.
Therefore, first we need to create all the UC service element that will be inserted into the Service Profile and
at the end assigned to the end users.
Cisco Jabber Lab Page 27
Cisco Jabber Lab Page 28
Please note that in this case we are not defining any specific UC profile for AD integration because we are
using EDI, that is the default behavior and permit the client to connect to AD using native PC’s Domain
Logon information (DC, credential , etc..).
Now we will create the first Service Profile (for EDI users) selecting all the UC Service defined before:
Cisco Jabber Lab Page 29
Set the name of the profile and set it the default service profile for the system.
Make sure you UNCHECK “Use UDS…”
Cisco Jabber Lab Page 30
Now we need to associate the Service Profile just created to the user Alice Adams:
Cisco Jabber Lab Page 31
Here below the main point – we define that this is the CUCM Home cluster for the user, that this user is
enabled for IM and the Service Profile to associate is the one just created (Please note that for a CUCM bug
sometimes the settings are not full saved, the suggestion is to click anywhere on the page after you
selected the IM profile….and check that really have been saved):
At this point we need to associate the users to the csf devices created before. This is needed because:
When the client tries to register to the cucm it asks for the devices “associated” to the userid
transmitted during the logon process
The cucm checks the association that we will configure now and reports back to the client the
device-id.
Last, the client will ask to the TFTP server the configuration of the device-id just received and will
try to register it to the cucm.
To achieve this click on device association button:
Search for available devices and select the CSF “csfaadams” just created:
Cisco Jabber Lab Page 32
Click on “Save Selected Changes”:
Click on “Go” near the “Back to User” links:
Now we need to associate the right line appearance to the user. Note, this is needed because only this line
will be monitored by the Presence Engine and the related “Busy” status will be reflected on the client as
“In A call..”.
To achieve this click on the “Line Appearance Association for Presence” button:
Search for the available extension numbers and select the right one for Alice A. (Directory number 100). Click
then “Save” to confirm the choice:
Cisco Jabber Lab Page 33
In the Directory Number Associations field select the Primary Extension among the possible choices. Note
that in this case we have only one extension associated to the users but we need in any case to select it:
Last we need to assign to the users the right level of authorization to interact with the cucm and register
devices. To do it please select the option “Add to Access Control Group”:
Press “Find” to search for all available pre-defined access level and select “Standard CCM End Users”:
Cisco Jabber Lab Page 34
Click on “Add Selected” button:
Now you will go back to the main page of the user and you will see the following scenario:
Cisco Jabber Lab Page 35
Click on the “Save” Button:
If you scroll down again to the end of the page you should now see the following picture where the specifics
“roles” have been assigned to the user:
Remember you have configured CTI Profile previously. We are not going to control any phones in this lab but
in order to do so you would also need to add the user to Standard CTI Enabled and eventually to Standard
CTI Allow Control of Phones supporting Xfer and conf (if you are using 89xx or 99xx phones) groups.
Please verify user configuration and repeat same steps for the user Bob Banks and Cathy Chung, following
the information reported in the table @ page 3.
Last step is to go on the IM & Presence node (10.52.226.71) and add some the minimal information still
required from the client to logon to presence server and retrieve the IP address of the CUCM for TFTP and
CCMCIP services.
Go to Application – Legacy Client – Setting and add TFTP servers here:
Cisco Jabber Lab Page 36
Leave the other value as standard.
Cisco Jabber Lab Page 37
Now go to the to Application – Legacy Client – CCMCIP Profile and add the CCMCIP hosts as primary and
backup node. Select also the other options showed below:
The Server side configuration for the basic logon of the client is now ended.
Cisco Jabber Lab Page 38
Cisco Jabber Lab – Module 5
Jabber Installation and Logon
In this module, the student will focus on creating the CSF device for the two Jabber users plus creating all the
other Policy and Template needed to pass the right parameters to the clients. Last, all these elements will be
associated to the users.
For the first user (Alice Adams) we will install the client and manually configure the connection parameters:
Logon via RDP to the PC “Alice Adams”, go in the “Lab_Material” folder on the desktop and run the
“CiscoJabberSetup.msi” install file from the installation zip file. When the installation finishes you will receive
this welcome screen, fill in the fields as follows: C
At this point click Save
Cisco Jabber Lab Page 39
and insert the logon credential for Alice Adams:
When the client logs on you will be able to search and add people to the buddy list but you will notice a
red error icon on the right Bottom side on the client – there are issue with CUCM registration!
At this point go to Options – Phone Accounts and fill with CUCM userid and Password for Alice Adams:
Note: go to “Advanced” and check that the CUCM IP address is reported there (from where has it been
taken?)
Cisco Jabber Lab Page 40
Click ok and you should go back to main buddy list view without the error notification received before.
At this point this client is active both for IM/Presence and Voice/Video.
Repeat now the same step for Bob Banks and when also Bob’s client is active you can start to make
some test of chat and audio/video calls. But for Bob, at the login screen you can now use the “use
default server” option for the “Login Server” menu because we configured the DNS SRV record before
so the client should be able to take the info from there, enhancing the logon user experience. In any case
remember to select the “Presence Server” as “Server Type”:
Please note that we are using VM and the Webcams are simulated using a Virtual Driver so you will only
get a sequence of photo rotated regularly as video on both side. To obtain this result you need to launch
the related program “VirtualCam” after the logon on the Jabber clients.
Last step is to install Jabber on the third PC (Cathy Chung). In this case we will test the new capability to
customize the MSI installation giving specific parameters.
You can in fact specify command line arguments to apply properties to Cisco Jabber for Windows during
installation. Please follow the following steps to test it:
Open a command line window.
Change the directory to the one where the Jabber MSI installation file is located
Specify the following command to install Cisco Jabber for Windows:
msiexec.exe /i CiscoJabberSetup.msi TYPE=CUP ADDRESS=10.52.226.71 DOMAIN=bootcamp.com
/quiet
Cisco Jabber Lab Page 41
Where:
TYPE=CUP specifies Cisco Unified Presence as the presence server type.
ADDRESS=10.52.226.71 specifies the IP address of the Presence Server
DOMAIN=bootcamp.com specifies the domain name of the presence server.
When the installation finish launch the client and verify that the parameters configured are there. Go to
File – change Connection Setting :
Cisco Jabber Lab Page 42
Cisco Jabber Lab – Module 6
Photo integration using Binary Object in AD
In this module, the student will focus on the first method to retrieve photo – “Binary Object” information
inserted in one of the AD attribute (thumbnailPhoto). Microsoft Office 2010 uses this attribute to display the
user picture in the contact cards. Utilizing this attribute to store the pictures i.e. for use with Microsoft Office
2010 will automatically enable Cisco Jabber for Windows to consume these pictures without any
configuration (in the default EDI mode).
!!! WARNING !!! Adding large binary objects to Active Directory could have far reaching consequences as it
affects the replication in distributed environments where consuming bandwidth and in certain scenarios
over slow speed WAN links can impact other mission critical transmissions. Storage of large objects could
also significant increase the directory partition size. All these aspects should be taken into account when
considering this possible deployment method.
Uploading binary Pictures into Active Directory
In the past 3rd party tools where required to upload pictures in binary format into Active Directory. With
Exchange 2010 there is now a command available from the Exchange management shell that allows an
administrator to directly upload pictures into AD. The thumbnailPhoto directory attribute is used to store
the picture information. Using the Exchange management shell method to upload the objects into AD, the
maximum object size is 10k - pictures have to format to that limit.
Verifying Status of Pictures in Active Directory
Before uploading pictures into AD one might want to verify if there is already data in the thumbnailPhoto
object. ADSIEdit does provide the means to very the status of directory attributes.
!!! WARNING !!! Using ADSIedit does pose certain risks especially when used against a production
environment. It provides object level access to components in Active Directory with only limited protection
against “unintended consequences”! It’s strongly advised to ask a directory administrator to perform any
changes or verification in none lab environments!
So just for educational purposes here are the steps to operate ADSIedit:
Logon to via RDP to the AD DC server (RDP Shortcut on Windows 7 Desktop) and search for “ADSI
edit”…
Cisco Jabber Lab Page 43
1. Launch ADSIedit
In the lab setup all users are in the container my-user. Right click on Alice Adams and select
Properties
2. ADSIedit select user
The following dialog shows all the attributes configured for this user.
5. ADSIedit show all attributes
Cisco Jabber Lab Page 44
3. ADSIedit show user properties
By default ADSIedit only shows the attributes that have a value associated – if you can’t see
thumbnailPhoto in the list of attributes there is no data associated. The previous figure shows how
to change the filter settings to show all attributes.
Upload pictures with Exchange 2010 Management Shell
Logon to via RDP to the Exchange 2010 server (RDP Shortcut on Windows 7 Desktop) and launch the
Exchange management shell.
Use the Import-RecipientDataProperty command to upload the pictures into Active Directory. The format
and parameters of the command are as follows:
Import-RecipientDataProperty –identity <username> -picture –filedata ([Byte[]]$(Get-Content –Path “<full
qualified path to picture file>” –encoding byte –readcount 0))
Please modify the command according to the example below.
4. Example Exchange management shell upload picture
Cisco Jabber Lab Page 45
Verify Picture Upload in Active Directory
Depending on the structure and size of the Active Directory topology it can take some time to replicate to all
domain controllers. To verify that the pictures are stored in the Active Directory object we can utilize again
ADSIedit (please see previous paragraph for details). Figure below shows the thumbnailPhoto object
populated with binary data.
5. ADSIedit thumbnailPhoto populated
Verify picture are downloaded by the Jabber client
Now, to verify that Jabber clients are able to download the Photos you should go in RDP to one of the PC and
follow these steps:
Logout from Jabber client
Login to Jabber client
Select the users in the buddy list, right click on it and force a profile update using the “view profile”
option
Cisco Jabber Lab Page 46
Cisco Jabber Lab – Module 7
Photo integration using Web Server and URI substitution
In this module, the student will focus on configuring Photo Search from Jabber client with the second
possible method called “URL substitution”.
Some additional info before jumping to config side:
Client will dynamically build a URL to a photo based on an admin defined URL template and the
contents of a directory attribute
Client can read a number image types including JPG,PNG& BMP
Recommended size is 128x128 pixels but client will resize images and crop images to display them
This method can the used only when the client is connected to a CUP server
Cisco Jabber Lab Page 47
As for the other configuration analyzed until now, the goal is to have everything configurable via policy
using CUCM. In this moment the CUCM and Jabber client are not ready yet to have this info passed using
inband policy so we will have to use the backup behavior of using an XML file created ad-hoc for this
reason. The Jabber client, at the startup will ask by default for a file with the name “Jabber-config.xml”.
Here below an example of the file:
In our case we are taking the photo from a web server co-resident with the Exchange machine (URL is
http://exchange01-bc.bootcamp.com/photo/photo_file_name.png).
The AD attribute used to make the search and match the photo’s file name is the “company”. The XML
file that we will use is the following:
<?xml version="1.0" encoding="utf-8"?>
<config version="1.0">
<Directory>
<PhotoURISubstitutionEnabled>True</PhotoURISubstitutionEnabled>
<PhotoURISubstitutionToken>company</PhotoURISubstitutionToken>
<PhotoURIWithToken>http://exchange01-bc.bootcamp.com/photo/company.png</PhotoURIWithToken>
</Directory>
</config>
Cisco Jabber Lab Page 48
In our case the goal is to enable only Alice Adams’s clients to retrieve and show the photo for the users
in the buddy list using this method instead of the default one (binary Object in AD). To be able to do it
only for Alice we will configure the client to download a specific xml file called “jabber-config-
group2.xml”:
To do this we will need to upload the xml file first to the CUCM so please logon on PC1, go to directory
“Lab Material” on the desktop and you will find the XML file (“Jabber jabber-config-group2.xml”) ready
to be uploaded. Go to the cucm console, select “Cisco Unified OS administration” from the right menu
and follow instructions to upload the xml file:
At this point you will need to restart the TFTP service on the CUCM so that CUCM “read” the new file.
Cisco Jabber Lab Page 49
Only thing missing now is to force the csf associate to Alice to download this file. To do this go to the CSF
device “csfaadams”:
Then in the Desktop Client Setting insert the following string that is telling to the client to download a
specific xml file called “jabber-config-group2.xml”:
Cisco Jabber Lab Page 50
For your reference the xml file is the following:
Now, to test the new integration go in RDP to Alice’s PC and follow these steps:
Logout from Jabber client
Clean the Photo cache going to the Photo shortcut folder that you find on the desktop and deleting
all the photos
Clean the Jabber Client History going to the related directory under the CSF shortcut you find on the
desktop and deleting the files under “CSF\History” folder
Login to Jabber client
Select the users in the buddy list and force a profile update using the “view profile” option
You should notice that compared with other clients Pictures are different because in this case we are
forcing the use of an attribute (company) to make the URL substitution and we created on the web
server (Exchange machine) different picture files from the one uploaded in AD as binary object, with
names mapped to this attribute. The names of the photo files are “userid_corp” and the “company”
AD attribute is filled with this type of string.
Cisco Jabber Lab Page 51
Cisco Jabber Lab Page 52
Cisco Jabber Lab – Module 8
Outlook Integration for Presence and Click to X
In this module, the student will focus on mandatory steps required to have a full working integration
scenario with Outlook 2007 and 2010 for Presence and Click to X functionality.
To enable Cisco Jabber for Windows integration with Microsoft Office, you must configure an attribute in
Microsoft Active Directory to enable Cisco Jabber for Windows users to share presence. You need to add a
new value to the proxyAddress attribute in the following format:
SIP:user_sip_uri
Example:
SIP:msmith@cisco.com
To apply this change to multiple users (full organization if needed) very quickly we released a bulk update
tool called “Cisco AD Wizard”. It is included in the Jabber administration pack, downloadable from CCO.
To use in the lab please RDP to AD DC using administrator account, go to the “MSO10ADSWizard” folder that
you can find on the desktop and you will find the tool to launch. At this point follow the wizard and you
should receive a notification without errors:
Cisco Jabber Lab Page 53
NOTE: As you are about to perfom that action from AD DC, it will refer to the administrator user, instead of
the aadams user shown in the screenshot above.
Cisco Jabber Lab Page 54
(The LDIF filename is auto-generated and will be different, that’s fine) You can check the log files under the
MSO10ADSWizard\LDIF_Files to see the users that has been found and changed:
To verify that the changes have been applied correctly open outlook, display a contact card, select the
“outlook properties” option as reported in the following screen shot. You should receive a list of two
elements in the Proxy Attribute field – one for SMTP email address and one for SIP address.
NOTE: It can take time to sync the new contact info so you can force the Outlook Offline Address Book
creation on Exchange and the download from the client:
1. RDP to Exchange Server using Administrator account, open the Exchange Management Console and go
to the option to re-create the Offline Address Book
Cisco Jabber Lab Page 55
Select the Offline Address Book Tab, select the only item you find in the list, right click on it and select
update:
2. After some minutes Open Outlook in the first client and go into the related option in the following menu
(File – Info – Account Setting – Download Address Book…):
Cisco Jabber Lab Page 56
Once download finishes repeat the previous check in the contact card. Now you can do the same process for
the other users.
Cisco Jabber Lab Page 57
Note: an alternative way to check the script result would be to use the AD tool called “ADSI Edit”. To use it
please do the following steps:
1. Logon on AD DC.
2. Start the ADSI Edit tool.
3. Expand the appropriate domain.
4. Open the organizational unit (OU) that contains the appropriate users.
5. Select one of the users
6. Right click on properties and search for the proxyAddress attribute
7. Verify the values associated to this attribute.
Cisco Jabber Lab Page 58
Cisco Jabber Lab – Module 9
Directory Lookup Rules to complete Photo Integration in alerting
and connected call status.
In this module, the student will focus on some additional and optional configuration to complete the Jabber
integration with Photo retrieval method. As you have noticed in the alerting pop-up and in the session
window the photo and the additional user information are not showed. This is mainly because Jabber makes
lookup search of the contact based on the calling number received during the alerting and connected phase
of the call signaling setup. In our case the extensions are 3 digits long while the numbers in AD are full +E.164
so Jabber is not able to find the contacts….
Jabber need therefore a Directory Lookup Rules set to make a translation between the Private number that
is receiving from the signaling path (XXX format) and the E164 number assigned to the users in AD
(+498115543XXX). So we will need a Rules that add the Prefix “+498115543“ to the 3 digit extensions. To
implement this step go to the CUCM admin page under Call Routing – Dial Rules – Directory Lookup Dial
Rules:
Now create a dial rule for number 1XX, adding the prefix +498115543 as reported here:
Cisco Jabber Lab Page 59
Repeat the same steps for prefix 2XX, 3XX.
At this point we need to apply a specific “.cop” file to tell cucm to “read” the application dial rules and public
them on the TFTP to be downloaded by Jabber client. We already uploaded this file to a local FTP server, you
would normally find it as part of the Jabber Admin pack available on CCO.
To install the file, go to the CUCM interface - Cisco OS Administration section and follow the steps below.
Use 10.52.226.73 as Server, “administrator” as username and “C1sc0,123” as password. There should only
be one valid .cop.sgn file available to install.
Cisco Jabber Lab Page 60
Click next to access the FTP server. Now, from the list of file existing on the ftp server select the one related
to the Dial Rules:
Select next and wait for the installation to finish. When is done you can go on the three PC, logout and login
to the Jabber client and the client will download the rules just created. Try to make a call between the two of
them and you will see alerting popup window and session window with name, roles and photo:
Cisco Jabber Lab Page 61
Cisco Jabber Lab Page 62
Cisco Jabber Lab – Module 10
Using CUCM User Data Service (UDS) for Directory Integration and
Photo Lookup
In this module, the student will focus on an alternative method to enable Jabber integration with AD using
CUCM User Data Service (UDS).
To test this scenario we need to force one of the clients to use the new UDS Service Profile to make lookup
search in AD for contact resolution and photo retrieval. Now we will create the second Service Profile (for
UDS users) selecting all the UC Service defined before and changing only one parameter, related to UDS
obviously:
Cisco Jabber Lab Page 63
Here below you will see the important parameter to flag…the one called “Use UDS for contact resolution”:
Cisco Jabber Lab Page 64
Cisco Jabber Lab Page 65
Now we need to associate the Service Profile just created to the user Bob Banks:
NOTE: in the current deployment stage of Jabber the client is not able to retrieve this info from the cucm
so we will need to create and force the download of a specific xml file to Bob’s client. Same scenario will
be in any case needed for cucm version older then 9.X
Upload the file “jabber-config-group1.xml” from the Lab_Materials directory of Alices’ Win7 machine to TFTP
directory of CUCM & restart the TFTP server.
Cisco Jabber Lab Page 66
The xml file looks like this:
The File will tell to client to use the “uid” attribute of UDS (mapped to user’s userid) to make the complete
URL and will search on the specified Web Server for a file name “userid.png” to be used like photo image for
the users (note that the images here are different from the others we used until now for the same user….you
will discover which one are the new….).
Only thing missing is to force the csf associate to Bob to use it. To do this go to the CSF device “csfbbanks”:
Cisco Jabber Lab Page 67
Then in the Desktop Client Setting are please insert the following string that is telling to the client to
download a specific xml file called “jabber-config-group1.xml”:
Now, to test the new integration go in RDP to Bob’s PC and follow these steps:
Logout from Jabber client
Clean the Photo cache going to the Photo shortcut folder that you find on the desktop and deleting
all the photos
Login to Jabber client
Select the users in the buddy list and force a profile update using the “view profile” option
You should notice a couple of differences compared with other clients
o we are missing some information due to fact that some attribute are not synced from AD
into CUCM Directory
o Pictures are different because in this case we are forcing the use of another attribute to
make the URL substitution (“userid” instead of “company”) and we created on the web
server (again the Exchange machine in our case) different picture files with names mapped
to userid attribute instead of company attribute.
Cisco Jabber Lab Page 68
Cisco Jabber Lab Page 69
Cisco Jabber Lab – Module 11
Adding Custom Embedded Tab
Embedded tabs allow to include a web page inside Jabber client. They can be useful for quick information or
a content which may be used by Jabber client to establish a communication (e.g. corporate directory).
In this example we will include a Twitter inside Jabber. Again the configuration is provided by XML file.
For your reference the file contains this:
<?xml version="1.0" encoding="utf-8"?>
<config version="1.0">
<Client>
<jabber-plugin-config>
<browser-plugin>
<page refresh="true" preload="false">
<tooltip>Twitter</tooltip>
<url>https://mobile.twitter.com</url>
</page>
</browser-plugin>
</jabber-plugin-config>
</Client>
</config>
Upload the file jabber-config-group3.xml to CUCM's TFTP directory and restart the TFTP server. Then go to
the Cathy Chung's CSF device and set the Cisco Support Field to configurationfile= jabber-config-
group3.xml.
Then exit from the Jabber client (do not just sign out) and start it again.
Cisco Jabber Lab Page 70
Cisco Jabber Lab – Module 12
New Provisioning method to enable User for IM&Presence and
deploy CSF devices
In this module, the student will focus on a new and alternative method to deploy Jabber. This new
Provisioning Method is based on the definition and utilization of two templates:
Universal Device Template
Feature Group Template
Once defined these two templates, we will be able to enable a specific user for Jabber and create in
automatic way also the CSF device to associate to him, with the correct extension number assigned to
the line.
First of All we have to define a new Universal Device Template, to do that you have to go to the menu
option “User Management – Universal Device Template”:
Click on “Add new”…..
Cisco Jabber Lab Page 71
Insert the appropriate info in the different fields, as reported in the following screen shot:
Cisco Jabber Lab Page 72
We can also pre-populate some information regarding the lines that will be created following this
device template:
Cisco Jabber Lab Page 73
As you can note it is possible to associate to some field a list of pre-defined parameter…these will be
substitute with real value taken from User’ info when the template will be used:
Change the device setting as reported below, leave the other field as default and then press “Save”:
Cisco Jabber Lab Page 74
Now we can jump back and start creating the “Feature Group Template”. To do it please go to the menu
reported below:
Cisco Jabber Lab Page 75
Now you can insert all the information that will be used as “Feature Template” later when we will create
users from scratch or we will enable users just imported from AD. Please follow the example below:
Cisco Jabber Lab Page 76
UDT_Template_1
With this step we have done with the template creation. Next step will be using these templates for a
“new” user just imported from AD into CUCM.
Go to the alternative “End Users” option under the “User management - Quick User/Phone Add” sub-
menu:
In the list of imported users from AD you will have to select “Luca Pellegrini” that has never been
configured until now:
Cisco Jabber Lab Page 77
Insert the following information, verifying that the values are really saved:
Cisco Jabber Lab Page 78
Now we have to assign one of the free extension numbers that are available to the Primary Extension
field (this value will be assigned to the line that will be created):
Cisco Jabber Lab Page 79
NOTE: if there are not free extension numbers in your POD you will have to create some
in the range 101-105 going to the following menu “Call routing – Directory Number”:
Cisco Jabber Lab Page 80
Cisco Jabber Lab Page 81
Click on “Add new”:
Once inserted you will be able to select in the user previous user page the extension 101:
Cisco Jabber Lab Page 82
Click anywhere on the page to be sure that all the value are maintained in the fields (possible cucm bugs
here..) and then Click on “Manage Device” to add a new device associated to this user:
The following empty table will appear:
Cisco Jabber Lab Page 83
Click on “Add new Phone” and insert the info related to the CSF device that will be created:
Click on the “Add Phone” blue button and verify that the device info has been saved:
Cisco Jabber Lab Page 84
At this point you can select the “Back to the User” menu option on the right side of the page and click the
Save Button.
Now what will happen is that all the info inserted will be used to modify the parameters associated to
the user Luca Pellegrini, create a CSF device, associate it to the same user, create a line on the device,
enable user for IM&Presence.
You can therefore go now around the menus verifying what the system has done automatically
for you!
Cisco Jabber Lab Page 85
Cisco Jabber Lab – Reference
Configure Automatic logon to CUCM using same credential as
IM&Presence Node
In this module we will quickly describe how to enhance the logon user experience removing the secondary
manual logon needed to give the correct credential to CUCM for CSF registration. In our specific case, that is
also a very common scenario for the customer, the same logon credential used for the IM&Presence node
can be used to logon to the CUCM because both are synced from AD.
Mainly, to instruct Jabber to use the same credential for both services we need to give to the client a specific
parameter using again the xml file. Here below you can see the specific lines that we need to insert in the
XML files that we created already for other reasons:
<?xml version="1.0" encoding="utf-8"?>
<config version="1.0">
<CUCM>
<PhoneService_UseCredentialsFrom>presence</PhoneService_UseCredentialsFrom>
</CUCM>
</config>
So, if you have still time left, you could now use one of the two xml files you have on the Pod’s PC under the
“Lab_material” folder, add the lines just commented, save the file with the same name and upload it again
on the CUCM using TFTP file upload menu.
Once done you can logout and login again in the Jabber client associated to the XML file configuration that
you modified (Alice or Bob) and you will notice the difference going in the “File – Option” Menu. Please look
at the following two screen shots:
Cisco Jabber Lab Page 86
On the Left you see the standard view with the tab “Phone Account” where you must insert the
CUCM credential, this is the view you had BEFORE the configuration change
On the Right you see the view you should have on the PC you have modified, where the “Phone
Account” tab is not present anymore but the CSF device is still registered on the cucm correctly. You
can see that everything is working fine because the icon in the right bottom angle of the client is
without red alert….
Cisco Jabber Lab Page 87
You are done. Congratulations !
Cisco Jabber Lab Page 88
Вам также может понравиться
- Tao PDFДокумент206 страницTao PDFJean Roland AngohОценок пока нет
- RFP 18-017, Bidding DocumentsДокумент52 страницыRFP 18-017, Bidding DocumentsSid Ali Oulad SmaneОценок пока нет
- CUCM 11.5 To 12.5 Upgrade Guide (FLEX)Документ10 страницCUCM 11.5 To 12.5 Upgrade Guide (FLEX)Sid Ali Oulad SmaneОценок пока нет
- Removing Items From CUCM With UCS HDSДокумент18 страницRemoving Items From CUCM With UCS HDSSid Ali Oulad SmaneОценок пока нет
- Local Switching DatasheetДокумент4 страницыLocal Switching DatasheetSid Ali Oulad SmaneОценок пока нет
- CUCM Trace CollectionДокумент6 страницCUCM Trace CollectionSid Ali Oulad SmaneОценок пока нет
- PVT 2012 Lab CUCM9 X PDFДокумент110 страницPVT 2012 Lab CUCM9 X PDFSid Ali Oulad SmaneОценок пока нет
- Tecucc 3000Документ449 страницTecucc 3000Sid Ali Oulad SmaneОценок пока нет
- Local Switching DatasheetДокумент4 страницыLocal Switching DatasheetSid Ali Oulad SmaneОценок пока нет
- Ccna Voice Portable Command GuideДокумент43 страницыCcna Voice Portable Command GuideIgnacio Fagalde100% (1)
- IntelePeer CUCM 11.5 Sansay UDPДокумент57 страницIntelePeer CUCM 11.5 Sansay UDPSid Ali Oulad SmaneОценок пока нет
- CJAB BK D6497E98 00 Deployment-Installation-guide-ciscojabberДокумент14 страницCJAB BK D6497E98 00 Deployment-Installation-guide-ciscojabberSid Ali Oulad SmaneОценок пока нет
- Cisco Unified Communications Manager 7.X Vol 1 V10.12.23Документ298 страницCisco Unified Communications Manager 7.X Vol 1 V10.12.23Sid Ali Oulad SmaneОценок пока нет
- Voice Over Ip (Voip) Over Satellite: February 2008Документ3 страницыVoice Over Ip (Voip) Over Satellite: February 2008Sid Ali Oulad SmaneОценок пока нет
- Configuring Cisco Unified Im Presence Server 9x PDFДокумент38 страницConfiguring Cisco Unified Im Presence Server 9x PDFSid Ali Oulad SmaneОценок пока нет
- Char Jabber 23Документ1 страницаChar Jabber 23Sid Ali Oulad SmaneОценок пока нет
- CST Jabber 11 0 Lab GuideДокумент257 страницCST Jabber 11 0 Lab GuideSid Ali Oulad SmaneОценок пока нет
- Cisco Configuration Guide: Updated March 17, 2016Документ18 страницCisco Configuration Guide: Updated March 17, 2016Sid Ali Oulad SmaneОценок пока нет
- CST Jabber 11 0 Lab GuideДокумент257 страницCST Jabber 11 0 Lab GuideSid Ali Oulad SmaneОценок пока нет
- Cisco Prime Network Registrar 8.2 User GuideДокумент800 страницCisco Prime Network Registrar 8.2 User GuideSid Ali Oulad SmaneОценок пока нет
- CST Jabber 11 0 Lab GuideДокумент257 страницCST Jabber 11 0 Lab GuideSid Ali Oulad SmaneОценок пока нет
- PVT 2012 Lab CUCM9 X PDFДокумент110 страницPVT 2012 Lab CUCM9 X PDFSid Ali Oulad SmaneОценок пока нет
- WX Siteadmin WBS27 SP10 PDFДокумент236 страницWX Siteadmin WBS27 SP10 PDFSid Ali Oulad SmaneОценок пока нет
- Configuring Cisco Unified Im Presence Server 9x PDFДокумент38 страницConfiguring Cisco Unified Im Presence Server 9x PDFSid Ali Oulad SmaneОценок пока нет
- CJAB BK D6497E98 00 Deployment-Installation-Guide-Ciscojabber PDFДокумент426 страницCJAB BK D6497E98 00 Deployment-Installation-Guide-Ciscojabber PDFSid Ali Oulad SmaneОценок пока нет
- Lab Guide Version 2.6. Meeting Server LabДокумент171 страницаLab Guide Version 2.6. Meeting Server LabSid Ali Oulad SmaneОценок пока нет
- CST Jabber 11 0 Lab GuideДокумент257 страницCST Jabber 11 0 Lab GuideSid Ali Oulad SmaneОценок пока нет
- Cisco UC On UCSДокумент17 страницCisco UC On UCSmstepp100% (3)
- Accelerator Cisco Jabber Integration GuideДокумент17 страницAccelerator Cisco Jabber Integration GuideSid Ali Oulad SmaneОценок пока нет
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (399)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (121)
- Timing Sync Lte SecДокумент9 страницTiming Sync Lte SecLakshmikishore NittalaОценок пока нет
- LCSI Media Converter ST CMC-U011FST-MM 2kmДокумент1 страницаLCSI Media Converter ST CMC-U011FST-MM 2kmramyheshmatОценок пока нет
- REF542plus IEC61850 ConfStatement 756361 ENd Rel3.0SP1Документ74 страницыREF542plus IEC61850 ConfStatement 756361 ENd Rel3.0SP1josleinyОценок пока нет
- FORTIGATE - Identity - FSSO - Installation and ConfigurationДокумент14 страницFORTIGATE - Identity - FSSO - Installation and ConfigurationJulio OliveiraОценок пока нет
- Common Network Attacks: David J. MarchetteДокумент107 страницCommon Network Attacks: David J. MarchetteJorge López FernándezОценок пока нет
- ZXUR 9000 Product DescriptionДокумент7 страницZXUR 9000 Product DescriptionSulman ismailОценок пока нет
- DNS Best PracticesДокумент165 страницDNS Best PracticesBhasker ReddyОценок пока нет
- Parallel Registry Internet Explorer Registry (DC - GPO)Документ6 страницParallel Registry Internet Explorer Registry (DC - GPO)Samer BellarОценок пока нет
- Automated Smart Pillow For All Age GroupДокумент2 страницыAutomated Smart Pillow For All Age GroupInternational Journal of Innovative Science and Research TechnologyОценок пока нет
- Fortios v5.6.6 Release NotesДокумент30 страницFortios v5.6.6 Release NotesMohsin AliОценок пока нет
- Midterm Examination - IT 312 I. Subnetting Scenario-Fill All The Blanks With The Appropriate Answer From The Topology, Tables and QuestionsДокумент2 страницыMidterm Examination - IT 312 I. Subnetting Scenario-Fill All The Blanks With The Appropriate Answer From The Topology, Tables and QuestionsAldrin MarianoОценок пока нет
- NW RouterДокумент13 страницNW Routerhem777Оценок пока нет
- Esmpro Customer PresentationДокумент65 страницEsmpro Customer PresentationSerge StasovОценок пока нет
- XPAIB006EN K InstrSW Lyza 5000 WebДокумент20 страницXPAIB006EN K InstrSW Lyza 5000 Webdixisa9055 kkoup.comОценок пока нет
- Seminar Report On Internet: Submitted in Partial Fulfillement For The Degree of Masters of Business AdministrationДокумент24 страницыSeminar Report On Internet: Submitted in Partial Fulfillement For The Degree of Masters of Business AdministrationVikash BhanwalaОценок пока нет
- Oracle Filesafe ErrorsДокумент102 страницыOracle Filesafe ErrorsirfanyellОценок пока нет
- Lecture 6: Radio Duty Cycling For Wireless Sensor NetworksДокумент32 страницыLecture 6: Radio Duty Cycling For Wireless Sensor NetworksKumar SarthakОценок пока нет
- Cisco Premium 200-301 by VCEplus 167q PDFДокумент86 страницCisco Premium 200-301 by VCEplus 167q PDFhiepleeОценок пока нет
- FortiOS-6 4 4-Administration - GuideДокумент1 852 страницыFortiOS-6 4 4-Administration - GuideGabriel RosОценок пока нет
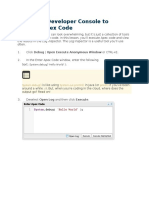
- Using The Developer Console To Execute Apex CodeДокумент5 страницUsing The Developer Console To Execute Apex Codeksr131Оценок пока нет
- Link Access ProcedureДокумент3 страницыLink Access ProcedureMadiha WajeehОценок пока нет
- The 8086 Pin ConfigurationДокумент32 страницыThe 8086 Pin ConfigurationTeo JavaОценок пока нет
- Microsoft 365 For Enterprise OverviewДокумент994 страницыMicrosoft 365 For Enterprise OverviewionОценок пока нет
- HPUG UA08 V05.04 Preliminary ExtДокумент639 страницHPUG UA08 V05.04 Preliminary ExtAlselawi AhmadОценок пока нет
- Web SecurityДокумент17 страницWeb Securitykejriwal_itОценок пока нет
- Avaya Network-DesignДокумент346 страницAvaya Network-DesignAFS AssociatesОценок пока нет
- Simatic: STEP 7 V5.5 Programming Software For SIMATIC S7 / M7 / C7Документ36 страницSimatic: STEP 7 V5.5 Programming Software For SIMATIC S7 / M7 / C7Hoàng HảiОценок пока нет
- Mod - Python ManualДокумент113 страницMod - Python ManualJeff Pratt100% (3)
- iDS-7200HQHI-M2/S SERIES Turbo Acusense DVR: Key FeatureДокумент4 страницыiDS-7200HQHI-M2/S SERIES Turbo Acusense DVR: Key Featuresony_w200Оценок пока нет
- GM868 Gas Ultrasonic FlowmeterДокумент4 страницыGM868 Gas Ultrasonic FlowmeterDikranОценок пока нет