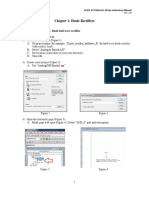
Академический Документы
Профессиональный Документы
Культура Документы
Automation of Detection of Security Vulnerabilities in Web Services Using Dynamic Analysis
Загружено:
Bangsa PEJUANG0 оценок0% нашли этот документ полезным (0 голосов)
6 просмотров3 страницыhiuyhihihiaf
Оригинальное название
Kumar 2014
Авторское право
© © All Rights Reserved
Доступные форматы
PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документhiuyhihihiaf
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
6 просмотров3 страницыAutomation of Detection of Security Vulnerabilities in Web Services Using Dynamic Analysis
Загружено:
Bangsa PEJUANGhiuyhihihiaf
Авторское право:
© All Rights Reserved
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 3
The 9th International Conference for Internet Technology and Secured Transactions (ICITST-2014)
Automation of Detection of Security Vulnerabilities
in Web Services using Dynamic Analysis
Rahul Kumar Indraveni K Aakash Kumar Goel
Project Engineer, CDAC Senior Technical Officer, CDAC Project Engineer, CDAC
Hyderabad, INDIA Hyderabad, INDIA Hyderabad, INDIA
Abstract — The usage of XML in maintaining data over the
web communications has lead to new ways of exploitation which II. PROBLEMS AND RELATED RESEARCH
are dangerous for the data integrity yet can be remediated on the With respect to the vulnerability classifications, the
basis of the vulnerability classification. The approach is reserved automation research is found to be very limited. There is a
for the research scope of unchangeable dynamic vulnerabilities
with the help of WSDL Enumeration and automation script for
huge scope to automate the detection of such vulnerabilities.
detection of the vulnerabilities on analysis of the SOAP Request As per the practical experience of security auditing and
and Response saved in XML Format with different payloads. penetration testing, it has been identified that web applications
uses either a relational database, or an XML Schema to store
Index Terms-Security, Web Service, Testing, Attack, data. The other important part of a web application that
Vulnerability, WSDL, XML, Payload, Dynamic Analysis, accounts for most attacker activity is state management.
Enumeration, Automation, SOAP Request, Response
I. INTRODUCTION Both of the above mentioned important attack vectors of
the web applications are now progressively being managed
Web services are self-contained, self-describing, reusable using web services, thus, making them exploitation proof
web applications components; communicate using open becomes imperative.
protocols that help solve the interoperability problem by giving
different applications a way to link their data. A web service III. APPROACH
uses XML described using a WSDL, to encode and decode In our approach, we will restrict the research scope to the
data and a SOAP message to transport it in a stateless manner. unchangeable dynamic vulnerability type of web service.
Web services are exposed to the internet like any other service Dynamic Vulnerabilities; that can only be detected upon the
but can be used on HTTP, FTP, SMTP, and MQ among other execution of a service, are widely present in generic Web
transport protocols. applications and have been studied more in depth than the
The vulnerabilities in web services are similar to other Static Vulnerabilities and are categorized as: (i) Error on
vulnerabilities, such as SQL injection and information leakage, interface, (ii) SQL and XPath injection (Code Injections).
but web services also have unique XML/parser related
vulnerabilities. The may be classified (Figure 1) as: Static and This approach takes care of the Code injection
Dynamic Vulnerability types based on the type of analysis, Vulnerabilities (SQL, XPath and XXE Injections) and the error
further described as changeable and unchangeable, where on interface issues faced by the web applications using Web
changeable refers to the modification of a Web Service XML Services. The WSDL file, which contains all the public
document by a client. methods on which a web application processes data are the
target inputs in this approach. We apply targeted payloads on
the different methods available in the WSDL file and then
analyze the response generated from a non-legitimate SOAP
request for legitimacy. An automation of the exploitation and
analysis of the response generated would not only reduce the
time and effort put in manual testing of the web services, but
would also give the security community a reliable solution to
integrate in their security tools.
Among the automation steps, we first identify the target
WSDL URL for triggering payloads. Now, with the help of the
Figure 1. Vulnerability classification automation script (Figure 2), we extract all the methods from
that web service component using python’s suds client. When
the WSDL methods are determined from the user input
978-1-908320-39/1/$25.00©2014 IEEE 334
The 9th International Conference for Internet Technology and Secured Transactions (ICITST-2014)
location, a predetermined, intelligent malicious list of payloads true condition, the resulting response (Figure 5) from the server
is sniped with the SOAP request parameter to the web server leaked all possible combinations of data available for the
handling the web service request. The analysis of the requested variable from the XML database, proving that the
vulnerabilities found, further depends on the response received code injection was successful at the server location.
from the server which is stored in an XML format (Figure 3).
Figure 2. Automation Steps
Figure 5. SOAP Response of the Web Service
In another case, when “’” (' ) was sent as the
payload to the SOAP Request (Figure 6) of the same web
service, it resulted in an exception in the SOAP Response
(Figure 6) confirming the unhandled error on the web server
upon triggering a malicious payload.
Figure 3. XML Format
For demonstration purpose, we tried our automation
technique on a sample web service, for testing purposes. A
custom payload like “1 or 1=1” was sent in the SOAP Request
(Figure 4) for the web service invocation.
Figure 6. SOAP Request - Response of Web Service
The findings were tested (see Table I) with several in-house
and public testing domains and it was found that the
experimental results proved to be successfully aligned with the
Figure 4. SOAP Request for the Web Service problem statement.
As the payload sent was malicious in nature, which intends
to extract the information from an XML database using an all-
978-1-908320-39/1/$25.00©2014 IEEE 335
The 9th International Conference for Internet Technology and Secured Transactions (ICITST-2014)
Table I. Experimental Results
S. No. Application Tested Results
1 Phpwsdl Success
2 xml-webservice Success
3 Esikshak Success
5 Webgoat Success
6 Bwapp Fail
IV. CONCLUSION
The research work is promising in nature with a great deal
of XML Analysis for security testing on Web Services based
applications. It not only throws light on the vulnerable injection
points in the public methods, but also gives insights on payload
types, affecting the web service execution without breaking the
XML Schema and hence the web application. The resulting
automation script is well tested on trusted platforms and open
application security test-beds and has out-performed major
existing solutions. This would not only account to additions in
the security framework, but also would be useful for further
research into unidentified XML related security issues in the
next iterations.
The next value addition challenge to the ongoing research
is, taking vulnerable samples of web services to test, without
breaking the XML Schema. As the XML Schema forms the
core for a web service based interaction, any disturbance in it,
would not only mal-form the XML, but would also lead to
maligned application behavior. In this approach, the focus is to
keep the XML Schema intact while testing, so that the false
positives relating to code injections that actually mal-form the
XML, could be minimized.
REFERENCES
[1] “Towards Automated WSDL-Based Testing of Web Services”, Cesare
Bartolini, Antonia Bertolin, Eda Marchetti, and Andrea Polini
[2] “Anatomy o f a Web Services Attack”, Forum Systems Inc.
[3] “Web Services Vulnerabilites”, Nishchal Bhalla, Sahba Kazerooni,
Security Compass
[4] “An Approach for WSDL-Based Automated Robustness Testing of Web
Services”, Samer Hanna and Malcolm Munro
[5] “Detecting Security Vulnerabilities in Web Applications Using Dynamic
Analysis with Penetration Testing”, Andrey Petukhov, Dmitry Kozlov
[6] “In the Wild: a Large Scale Study of Web Services Vulnerabilities”,
Sushama Karumanchi and Anna Cinzia Squicciarini
[7] “Web Services – Attacks and Defense”, NetSquare.
978-1-908320-39/1/$25.00©2014 IEEE 336
Вам также может понравиться
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5794)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (344)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (121)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (400)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- TorquesДокумент108 страницTorquesnaruxzОценок пока нет
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- Softening N Penetration Test (Bitumen)Документ11 страницSoftening N Penetration Test (Bitumen)Thamilaarasan SonOf Nathan29% (7)
- Rendering An Exterior Scene - V-Ray 2.0 For SketchUp - Chaos Group HelpДокумент9 страницRendering An Exterior Scene - V-Ray 2.0 For SketchUp - Chaos Group HelpRapha RachoОценок пока нет
- Xin Wang 2010Документ5 страницXin Wang 2010Bangsa PEJUANGОценок пока нет
- Common Requirements For Web Application Vulnerability Scanners For The Internet of ThingsДокумент1 страницаCommon Requirements For Web Application Vulnerability Scanners For The Internet of ThingsBangsa PEJUANGОценок пока нет
- Extracting Information About Security Vulnerabilities From Web TextДокумент4 страницыExtracting Information About Security Vulnerabilities From Web TextBangsa PEJUANGОценок пока нет
- The Appilication of Fuzzing in Web Software Security Vulnerabilities TestДокумент4 страницыThe Appilication of Fuzzing in Web Software Security Vulnerabilities TestBangsa PEJUANGОценок пока нет
- Rational Unified Treatment For Web Application Vulnerability AssessmentДокумент5 страницRational Unified Treatment For Web Application Vulnerability AssessmentBangsa PEJUANGОценок пока нет
- Web Application Vulnerabilities - The Hacker's TreasureДокумент5 страницWeb Application Vulnerabilities - The Hacker's TreasureBangsa PEJUANGОценок пока нет
- High-E Ciency Class E/F Power Ampli Fiers With Extended Maximum Operating FrequencyДокумент10 страницHigh-E Ciency Class E/F Power Ampli Fiers With Extended Maximum Operating FrequencyBangsa PEJUANGОценок пока нет
- Using The Low Cycle Fatigue Approach When KT Nominal Stress Exceeds The Yield Strength: A Fundamental Mistake!Документ2 страницыUsing The Low Cycle Fatigue Approach When KT Nominal Stress Exceeds The Yield Strength: A Fundamental Mistake!VigneshwaraОценок пока нет
- Flange DimensionsДокумент7 страницFlange DimensionsDave DonohueОценок пока нет
- Magnetic Abrasive Finishing A Review IJERTV2IS3010Документ9 страницMagnetic Abrasive Finishing A Review IJERTV2IS3010Saketh ReddyОценок пока нет
- Low Density Parity Check CodesДокумент21 страницаLow Density Parity Check CodesPrithvi Raj0% (1)
- Highway Planning Manual Volume 8 PDFДокумент72 страницыHighway Planning Manual Volume 8 PDFHanz Maca-ayanОценок пока нет
- API 510 Questions Amp Answers Closed Book 1 PDF FreeДокумент12 страницAPI 510 Questions Amp Answers Closed Book 1 PDF Freejakariya100% (2)
- BMS-HSS-F-113 - Lift Plan Rev 03Документ11 страницBMS-HSS-F-113 - Lift Plan Rev 03Fariz SafarullaОценок пока нет
- DM Automatic Irrigation System SpecsДокумент56 страницDM Automatic Irrigation System SpecsSarfraz AhmadОценок пока нет
- Bearing SPM Condition Analyser BVT 111Документ2 страницыBearing SPM Condition Analyser BVT 111industrialindiaОценок пока нет
- ELEC 4170 1 Diode Rectifiers Fall 2022Документ14 страницELEC 4170 1 Diode Rectifiers Fall 2022Tafheem AlphaОценок пока нет
- JavaScript and XHTML DocumentsДокумент40 страницJavaScript and XHTML Documentstech2click100% (3)
- Flocculation and ClarifiersДокумент17 страницFlocculation and ClarifiersOnelОценок пока нет
- Aerospace Material SpecificationДокумент7 страницAerospace Material SpecificationAnonymous T6GllLl0Оценок пока нет
- N Queen ProblemДокумент2 страницыN Queen ProblemManikandanОценок пока нет
- Design of Seismic Force On BuildingДокумент12 страницDesign of Seismic Force On BuildingAjay DalviОценок пока нет
- Mbackpaper 18Документ6 страницMbackpaper 18Aakash PathakОценок пока нет
- EN VEGASWING 63 Two WireДокумент48 страницEN VEGASWING 63 Two WireLucas FiordelisiОценок пока нет
- Lecture-14 Sheet Metal Forming ProcessesДокумент34 страницыLecture-14 Sheet Metal Forming ProcessesDida KhalingОценок пока нет
- The Visual Basic Editor: School of ConstructionДокумент43 страницыThe Visual Basic Editor: School of Constructionavdesh7777Оценок пока нет
- Asterix Adsbtr Cat021 Part12 v2 6Документ91 страницаAsterix Adsbtr Cat021 Part12 v2 6DAI XUANLINGОценок пока нет
- Metallographic Sample Preparation Techniques: BackgroundДокумент8 страницMetallographic Sample Preparation Techniques: BackgroundQA LAB ISMОценок пока нет
- Multipass Ring Oscillator Based Dual Loop PLL For High Frequency SynthesizersДокумент7 страницMultipass Ring Oscillator Based Dual Loop PLL For High Frequency SynthesizersInternational Journal of Application or Innovation in Engineering & ManagementОценок пока нет
- Extended Cell ConfigurationДокумент31 страницаExtended Cell Configurationrfabre76Оценок пока нет
- FTM-3100R: Operating ManualДокумент36 страницFTM-3100R: Operating ManualMarcos Chiorato100% (1)
- C Library Math.h Functions - GeeksforGeeksДокумент11 страницC Library Math.h Functions - GeeksforGeeksSoumadip Banerjee100% (1)
- Territory ManagementДокумент52 страницыTerritory ManagementAjay Tyagi100% (1)
- GSX ManualДокумент69 страницGSX ManualSalazar SantiagoОценок пока нет