Академический Документы
Профессиональный Документы
Культура Документы
Big Data Cybersecurity Analytics Research Report
Загружено:
Ainul NasihaОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Big Data Cybersecurity Analytics Research Report
Загружено:
Ainul NasihaАвторское право:
Доступные форматы
Big
Data Cybersecurity Analytics
Research Report
Sponsored by Cloudera
Independently conducted by Ponemon Institute LLC
Publication Date: August 2016
Ponemon Institute© Research Report
Big Data Cybersecurity Analytics Research Report
Ponemon Institute: August 2016
Part 1. Introduction
Ponemon Institute is pleased to present the findings of Big Data Cybersecurity Analytics,
sponsored by Cloudera. The purpose of this study is to understand the current state of
1
cybersecurity big data analytics and how Apache Hadoop based cybersecurity applications
intersect with cybersecurity big data analytics.
In this study, we surveyed 592 IT and IT security practitioners in the United States and 10
cybersecurity technology executives at 10 unique organizations that have built applications on
Apache Hadoop. To ensure a knowledgeable respondent, we confirmed that all participants are in
organizations using some form of big data analytics and they are knowledgeable about the
technology. Some of these participants are users of the Apache Hadoop platform.
Following are key findings from the research.
§ Organizations are 2.25X more likely to identify a security incident within hours or minutes
when they are a heavy user of big data cybersecurity analytics.
§ Sixty-five percent of respondents say the use of big data analytics is very important to
ensuring a strong cybersecurity posture.
§ Eighty-one percent of respondents say demand for big data for cybersecurity analytics has
significantly increased over the past 12 months.
§ Apache Hadoop significantly extends big data cybersecurity analytic applications capabilities:
ü 29 percent of these applications use Hadoop to increase data volumes by more than 100
percent
ü 72 percent of them use Hadoop to increase data processing by more than 76 percent
ü 43 percent of them use Hadoop to increase data access for analytics by more than 100
percent
• Heavy users of big data analytics have a higher level of confidence in their ability to detect
cyber incidents than light users. With respect to 11 common cyber threats, the biggest gaps
between heavy and light users concern the organization’s ability to detect advanced
malware/ransomware, compromised devices (e.g., credential theft), zero day attacks and
malicious insiders. The smallest gaps in detection between heavy and light users concern
denial of services, web-based attacks and spear phishing/social engineering.
• Companies represented in this research are allocating an average of $14.50 million to IT
security in fiscal year 2016 and an average of $2.32 million (16 percent) of this budget is
allocated to analytics tools.
1
Hadoop is an ecosystem of open source components that fundamentally changes the way enterprises
store, process and analyze data. Unlike traditional systems, Hadoop enables multiple types of analytic
workloads to run on the same data, at the same time, at massive scale on industry-standard hardware. CDH,
Cloudera’s open source platform, is the most popular distribution of Hadoop and related projects in the world
(with support available via a Cloudera Enterprise subscription).
Ponemon Institute: Private & Confidential Report 1
Part 2. Current state
Most companies in this study have fairly mature cybersecurity programs. According to
Figure 1, 70 percent of respondents say their organizations have many cyber security program
activities deployed (late-middle stage) or most cybersecurity program activities are deployed
(mature stage).
Figure 1. What best describes the maturity level of your cybersecurity program?
Mature stage – most cybersecurity program
30%
activities are deployed across the enterprise
Late-middle stage – many cybersecurity program
40%
activities are deployed across the enterprise
Middle stage – cybersecurity program activities
are planned and defined but only partially 25%
deployed
Early stage – many cybersecurity program
activities have not as yet been planned or 5%
deployed
0% 5% 10% 15% 20% 25% 30% 35% 40% 45%
Big data analytics is key to a strong cybersecurity posture. Sixty-five percent of respondents
say the use of big data analytics is essential (25 percent) or very important (40 percent) to
ensuring a strong cybersecurity posture.
Figure 2. How important is the use of big data analytics for ensuring a strong
cybersecurity posture?
45%
40%
40%
35%
30%
25%
25% 23%
20%
15%
9%
10%
5% 3%
0%
Essential Very important Important Not important Irrelevant
Ponemon Institute: Private & Confidential Report 2
The more big data analytics is used, the greater the demand. According to Figure 3, 61
percent of light user respondents say user demand has increased significantly (38 percent) or
increase (28 percent). In contrast, 75 percent of respondents of the heavy user group believe
demand has increased significantly (43 percent) or increased (32 percent).
Figure 3. How has user demand for big data analytics for cybersecurity changed over the
past 12 months?
45% 41%
40%
35%
30%
30%
25%
20%
20%
15%
10% 8%
5% 1%
0%
Significant Increase No change Decrease Significant
increase decrease
The typical deployment of cybersecurity analytics is a challenge for companies. As shown
in Figure 4, deployment is considered very difficult (30 percent of respondents) and difficult (34
percent of respondents).
Figure 4. How difficult is the difficult deployment of cybersecurity analytics within your
organization?
40%
34%
35%
30%
30%
25%
21%
20%
15%
15%
10%
5%
0%
Very difficult Difficult Not difficult Easy
Ponemon Institute: Private & Confidential Report 3
Expertise and technologies are needed for the successful adoption of big data analytics.
Figure 5 presents the challenges companies face in the use of big data analytics. These are: lack
of in-house expertise (65 percent of respondents), insufficient technologies (60 percent of
respondents) and insufficient resources (44 percent of respondents).
Figure 5. What challenges prevent the effective use of big data analytics for
cybersecurity?
Three choices permitted
Lack of in-house expertise 65%
Insufficient technologies 60%
Insufficient resources 44%
Executives do not see cybersecurity as a
35%
significant risk
Lack of collaboration with other functions 31%
No understanding how to protect against cyber
26%
attacks
Not a priority issue 18%
Lack of clear leadership 17%
Other 4%
0% 10% 20% 30% 40% 50% 60% 70%
Traditional systems are not helpful to a strong cybersecurity posture. According to Figure 6,
72 percent of respondents say leveraging big data and advanced analytics to get ahead of threats
is impossible with traditional systems. Other issues with traditional systems include the need for
security operations to constantly offload data as budget constraints and system limits are reached
(66 percent of respondents), threat analysts can’t perform advanced analytics against TBs worth
of data in short order (61 percent of respondents) and it takes days or weeks to access
complementary data incident responders need in order to respond to flagged events (59 percent
of respondents).
Figure 6. Problems with traditional systems
Strongly agree and Agree responses combined
Leveraging big data and advanced analytics to
get ahead of threats is impossible with traditional 72%
systems
Security operations must constantly offload data
as budget constraints and system limits are 66%
reached
Threat analysts can’t perform advanced analytics
(e.g. machine learning) against TBs worth of 61%
data in short order
It takes days or weeks to access complementary
data incident responders need in order to 59%
respond to flagged events
0% 10% 20% 30% 40% 50% 60% 70% 80%
Ponemon Institute: Private & Confidential Report 4
Part 3. The world of big data cybersecurity analytics
In addition to our study of users, we interviewed Cloudera’s partners to learn their perceptions
about building on Cloudera and Apache Hadoop. As noted in Figure 6, they saw an average
increase of 71% in the volume of data their clients are able to store, an average of 80% increase
in data processing speeds and an average of 84 percent increase in the amount of data clients
are able to analyze.
Figure 6. Benefits of Apache Hadoop based applications
Extrapolated values on a percentage scale from 0% to more than 100%
Increase in the amount of data your clients are
84%
able to analyze
Increase in data processing speed your clients
80%
are able to achieve
Increase in the volume of data your clients are
71%
able to store
0% 10% 20% 30% 40% 50% 60% 70% 80% 90%
Ponemon Institute: Private & Confidential Report 5
Machine learning applied to security data and UBA are the most promising features. Figure
7 presents what respondents believe are the top technology features for a strong cybersecurity
posture are: machine learning applied to security data (51 percent of respondents), user behavior
analytics (50 percent of respondents), advance warning about threats and attackers (48 percent
of respondents), intelligence about weak spots or vulnerabilities (47 percent of respondents) and
cyber analytics for pinpointing cyber attacks (45 percent of respondents).
Figure 7. What are the most promising enabling technology features?
Top six choices permitted
Provide machine learning applied to security
51%
data
Provide user behavioral analytics (UBA) 50%
Provide advance warning about threats and
48%
attackers
Provide intelligence about weak spots or
47%
vulnerabilities
Provide cyber analytics for pinpointing cyber
45%
attacks
Minimize insider threats (including negligence) 44%
Provide user network traffic analytics 43%
Prioritize threats, vulnerabilities and attacks 35%
Limit unauthorized access and/or sharing of
30%
sensitive or confidential data
Prevent insecure devices from accessing secure
29%
systems
Enable efficient recovery operations 27%
Simplify the reporting of threats 26%
Secure endpoints including mobile-connected
24%
devices
Enable adaptive perimeter controls 22%
Reduce or eliminate malware from entering the
22%
network
Enable efficient patch management 20%
Slows down or even halts the attacker’s
20%
computers
Neutralizes denial of service attacks before they
17%
happen
0% 10% 20% 30% 40% 50% 60%
Ponemon Institute: Private & Confidential Report 6
Big data analytics strengthens cybersecurity posture. Seventy-two percent of respondents
say the use of big data analytics to detect advanced cyber threats is very important. In fact, 71
Heavy users are more likely to believe in the importance of big data analytics. As shown in Figure
8, 76 percent of high users believe big data analytics is very important as opposed to 67 percent
of light user respondents.
Figure 8. How important is the use of big data analytics to detect advanced cyber threats?
7+ percentage response on a 10-point scale
100%
90%
76%
80%
67%
70%
60%
50%
40%
30%
20%
10%
0%
Light Use Heavy Use
Light Use Heavy Use
Ponemon Institute: Private & Confidential Report 7
Companies are best at detecting web-based attacks. According to Figure 9, organizations
represented in this study have the most confidence in detecting the following cyber incidents:
web-based attacks (67 percent of respondents), application-level attacks such as SQL injection,
cross site scripting or remote file inclusion (63 percent of respondents), denial of services (56
percent of respondents) and network borne threats (54 percent of respondents).
Heavy users are best at detecting cyber threats. As also shown in Figure 9, heavy users of big
data analytics appear to have a much higher level of confidence in their ability to detect cyber
incidents than light users. With respect to 11 common cyber threats, the biggest gaps between
heavy and light users concern the organization’s ability to detect advanced malware/ransomware
(Diff=25 percent), compromised devices (Diff=19 percent), zero day attacks (Diff=18 percent) and
malicious insiders (Diff=18 percent). The smallest gaps in detection between heavy and light
users concern denial of services (Diff=-4 percent), web-based attacks (Diff=4 percent) and spear
phishing/social engineering (Diff=5 percent).
Figure 9. Which cyber incidents are you best at detecting?
More than one choice permitted
69%
Web-based attack 65%
67%
66%
Application-level attacks 59%
63%
54%
Denial of services 58%
56%
57%
Network borne threats 50%
54%
50%
Advanced malware / Ransomware 25%
39%
46%
Compromised devices 27%
38%
34%
Rogue users 25%
30%
36%
Advanced persistent threats 20%
29%
33%
Zero day attacks 15%
25%
21%
Spear phishing and social engineering 16%
19%
23%
Malicious insiders 5%
15%
0% 10% 20% 30% 40% 50% 60% 70% 80%
Heavy Use Light Use Overall
Ponemon Institute: Private & Confidential Report 8
As shown in Figure 9, 9 percent of heavy users of big data analytics can detect threats within
hours or minutes, compared to 4 percent of light users.
Figure 10. How quickly can your organization identify a security incident?
Most security incidents are identified within hours 4%
or minutes 9%
9%
Most security incidents are identified within days
27%
Most security incidents are identified within 42%
weeks 31%
Most security incidents are identified within 37%
months 21%
None of the above (or, we rely on third parties to 8%
identify incidents) 12%
0% 5% 10% 15% 20% 25% 30% 35% 40% 45%
Light Use Heavy Use
Ponemon Institute: Private & Confidential Report 9
Part 3. Methods
A sampling frame of 18,280 IT and IT security practitioners in the United States were selected as
participants in the research. Table 1 shows 656 total returns. Screening and reliability checks
required the removal of 64 surveys. Our final sample consisted of 592 surveys or a 3.2 percent
response.
Table 1. Sample response Freq Pct%
Sampling frame 18,280 100.0%
Total returns 656 3.6%
Rejected surveys 64 0.4%
Final sample 592 3.2%
Pie Chart 1 reports the respondents’ organizational level within participating organizations. By
design, 61 percent of respondents are at or above the supervisory levels.
Pie Chart 1. Current position within the organization
2% 3%
17%
Executive
39% Vice president
Director
Manager
Supervisor
23%
Staff/technician
16%
As shown in Pie Chart 2, 45 percent of respondents report directly to the CIO or head of
corporate IT, 21 percent of respondents report to the business unit leader or general manager
and 18 percent of respondents report to the head of IT security.
Pie Chart 2. Direct reporting channel
3% 2%2%
4%
5% CIO or head of corporate IT
Business unit leader or general manager
Head of IT security
45%
Other
18%
Head of compliance or internal audit
General counsel or head of corporate legal
CFO, controller or head of finance
Head of security
21%
Ponemon Institute: Private & Confidential Report 10
As shown in Pie Chart 3, 56 percent of respondents are from organizations with a global
headcount of more than 5,000 employees
Pie Chart 3. Global employee headcount
8%
23%
11%
< 1,000
1,000 to 5,000
5,001 to 10,000
17% 10,001 to 25,000
25,001 to 75,000
21%
> 75,000
20%
Pie Chart 4 reports the industry classification of respondents’ organizations. This chart identifies
financial services (17 percent of respondents) as the largest segment, followed by health and
pharmaceutical (11 percent of respondents) and public sector (10 percent of respondents).
Pie Chart 4. Primary industry classification
2%2%2%
3% 17% Financial services
3% Health & pharmaceutical
3% Public sector
5% Retail
Industrial & manufacturing
Services
6% 11%
Technology & software
Energy & utilities
Consumer products
8% Entertainment & media
10% Hospitality
Transportation
Communications
9%
Education & research
10%
9% Other
Ponemon Institute: Private & Confidential Report 11
Part 4. Caveats to this study
There are inherent limitations to survey research that need to be carefully considered before
drawing inferences from findings. The following items are specific limitations that are germane to
most Web-based surveys.
! Non-response bias: The current findings are based on a sample of survey returns. We sent
surveys to a representative sample of individuals, resulting in a large number of usable
returned responses. Despite non-response tests, it is always possible that individuals who did
not participate are substantially different in terms of underlying beliefs from those who
completed the instrument.
! Sampling-frame bias: The accuracy is based on contact information and the degree to which
the list is representative of individuals who are IT or IT security practitioners. We also
acknowledge that the results may be biased by external events such as media coverage.
Finally, because we used a Web-based collection method, it is possible that non-Web
responses by mailed survey or telephone call would result in a different pattern of findings.
! Self-reported results: The quality of survey research is based on the integrity of confidential
responses received from subjects. While certain checks and balances can be incorporated
into the survey process, there is always the possibility that a subject did not provide accurate
responses.
Ponemon Institute: Private & Confidential Report 12
Appendix: Detailed Survey Results
The following tables provide the frequency or percentage frequency of responses to all survey
questions contained in this study. All survey responses were captured from lJune through July
2016.
Survey response Freq Pct%
Sampling frame 18,280 100.0%
Total returns 656 3.6%
Rejected surveys 64 0.4%
Final sample 592 3.2%
Part 1. Screening questions
S1. What best describes your organization’s use of big data analytics for
cybersecurity purposes Pct%
None (stop) 0%
Light 20%
Moderate 24%
Heavy 27%
Very heavy 29%
Total 100%
S2. What best describes your level of involvement in using big data
analytics for cybersecurity purposes? Pct%
None (stop) 0%
Low 21%
Moderate 24%
Significant 33%
Very significant 22%
Total 100%
S3. What best describes your level of familiarity with Apache Hadoop or
Cloudera? Pct%
None (stop) 0%
Low 12%
Moderate 40%
Significant 24%
Very significant 24%
Total 100%
S4. What best describes your role as a user of big data analytics for
cybersecurity? Pct%
Business user of analytics 45%
Developer of applications 25%
Both user and developer 30%
None of the above (stop) 0%
Total 100%
Ponemon Institute: Private & Confidential Report 13
Part 2: Security posture
Q1. How important is the use of big data analytics to detect advanced
cyber threats? Pct%
1 or 2 4%
3 or 4 10%
5 or 6 14%
7 or 8 19%
9 or 10 53%
Total 100%
Extrapolated value 7.64
Q2. What challenges prevent the effective use of big data analytics for
cybersecurity? Please choose three top challenges. Pct%
Insufficient resources 44%
Insufficient technologies 60%
Lack of in-house expertise 65%
Lack of clear leadership 17%
No understanding how to protect against cyber attacks 26%
Executives do not see cybersecurity as a significant risk 35%
Lack of collaboration with other functions 31%
Not a priority issue 18%
Other (please specify) 4%
Total 300%
Q3. Who determines the cybersecurity priorities or objectives within your
organization? Please choose only one primary function. Pct%
Board of directors 1%
CEO 3%
COO 0%
CFO 0%
CIO/CTO 25%
CISO/CSO 23%
Enterprise risk officer (CRO) 9%
Managed security service provider (MSSP) 13%
No one function determines cybersecurity priorities 26%
Other (please specify) 0%
Total 100%
Q4a. How has user demand for big data analytics for cybersecurity
changed over the past 12 months? Pct%
Significant increase 41%
Increase 30%
No change 20%
Decrease 8%
Significant decrease 1%
Total 100%
Q4b. If selected increase, what caused this change in demand? Please
select all that apply. Pct%
Response to cyber attacks 63%
Recruitment of expert staff 47%
Improvements in enabling technologies and/or the use of cyber analytics 55%
Changes in leadership, resource availability and organizational
restructuring 30%
Changes in compliance requirements with laws and/or industry initiatives 27%
Total 222%
Ponemon Institute: Private & Confidential Report 14
Q5. Which cyber incidents are you best at detecting? Please select all that
apply. Pct%
Rogue users 30%
Zero day attacks 25%
Network borne threats 54%
Advanced malware / Ransomware 39%
Spear phishing and social engineering 19%
Application-level attacks (SQL injection, cross site scripting or remote file
inclusion) 63%
Advanced persistent threats 29%
Denial of services 56%
Compromised devices 38%
Malicious insiders 15%
Web-based attack 67%
Total 435%
Q6. Where are you seeing the greatest areas for cybersecurity risk?
Please select five choices. Pct%
Lack of system visibility 56%
Across 3rd party applications 55%
Negligent insiders 49%
Mobile devices such as smart phones 46%
External threats from social media 44%
Mobile/remote employees 43%
Malicious insiders 42%
Desktop or laptop computers 32%
Network infrastructure environment (gateway to endpoint) 31%
Cloud computing infrastructure and providers 27%
The server environment 24%
Virtual computing environments (servers, endpoints) 23%
Data centers 12%
Within operating systems 10%
Removable media (USB sticks) and/or media (CDs, DVDs) 6%
Total 500%
Ponemon Institute: Private & Confidential Report 15
Q7. What are the most promising enabling security technologies? Please
select six technologies in terms of importance to in meeting your
organization’s security objectives or mission. Technologies that . . . Pct%
Provide machine learning applied to security data 51%
Provide user behavioral analytics (UBA) 50%
Provide advance warning about threats and attackers 48%
Provide intelligence about weak spots or vulnerabilities 47%
Provide cyber analytics for pinpointing cyber attacks 45%
Minimize insider threats (including negligence) 44%
Provide user network traffic analytics 43%
Prioritize threats, vulnerabilities and attacks 35%
Limit unauthorized access and/or sharing of sensitive or confidential data 30%
Prevent insecure devices from accessing secure systems 29%
Enable efficient recovery operations. 27%
Simplify the reporting of threats 26%
Secure endpoints including mobile-connected devices 24%
Reduce or eliminate malware from entering the network 22%
Enable adaptive perimeter controls 22%
Slows down or even halts the attacker’s computers (use of honeypots) 20%
Enable efficient patch management 20%
Neutralizes denial of service attacks before they happen 17%
Total 600%
Q8. What best describes the maturity level of your organization’s
cybersecurity program or initiatives? Pct%
Early stage – many cybersecurity program activities have not as yet been
planned or deployed 5%
Middle stage – cybersecurity program activities are planned and defined
but only partially deployed 25%
Late-middle stage – many cybersecurity program activities are deployed
across the enterprise 40%
Mature stage – most cybersecurity program activities are deployed across
the enterprise 30%
Total 100%
Q9. What best describes your organization’s ability to identify security
incidents? Pct%
Most security incidents are identified within months 28%
Most security incidents are identified within weeks 36%
Most security incidents are identified within days 19%
Most security incidents are identified within hours or minutes 7%
None of the above (or, we rely on third parties to identify incidents) 10%
Total 100%
Q10. In your opinion, how important is the use of big data analytics for
ensuring a strong cybersecurity posture within your organization? Pct%
Essential 25%
Very important 40%
Important 23%
Not important 9%
Irrelevant 3%
Total 100%
Ponemon Institute: Private & Confidential Report 16
Q11. Where is network visibility most important for the detection use
cases you find most valuable? Please select one choice Pct%
Connection data (netflow, flow) 26%
Packet data (IDS/IPS) 23%
Logs data (network device reporting) 20%
Forensic data (PCAP) 17%
Session context data (DPI session data, network meta information) 9%
Statistical data (counts) 5%
Total 100%
Q12. Did your organization’s security posture improve as a result of
greater network visibility? Pct%
Yes 69%
No 21%
Unsure 10%
Total 100%
Q13a. Does your organization have a single cybersecurity platform that
enables analysts to search, analyze and report on all network, user,
endpoint, log, mobile, file/executable and threat intelligence data to
support the incident analysis process? Pct%
Yes 55%
No [go to Q.14] 45%
Total 100%
Q13b. If yes, does the cybersecurity platform support the collection and
analysis of information for an unlimited timeframe? Pct%
Yes 38%
No 62%
Total 100%
Q13c. If yes, does the cybersecurity platform support any data types (files,
databases, binaries, video, images and documents)? Pct%
Yes 40%
No 60%
Total 100%
Q13d. If yes, does the cybersecurity platform offer analytic flexibility to
perform all the necessary analytics approaches your organization requires
(statistical, correlation, behavioral and machine learning)? Pct%
Yes 44%
No 56%
Total 100%
Q13e. If yes, does the cybersecurity platform offer integration with the
datasets with other applications (commercial, open source or custom
developed)? Pct%
Yes 48%
No 52%
Total 100%
Ponemon Institute: Private & Confidential Report 17
Part 3. Budget Questions
Q14. Who within your organization has funding authority for investment in
cybersecurity solutions? Pct%
CIO 27%
CTO 5%
CISO/CSO 21%
Data center management 3%
Compliance and legal 2%
LOB management 23%
Shared among various functions 19%
Total 100%
Q15a. What dollar range best describes your organization’s IT security
budget in the present fiscal year? Pct%
Less than $2 million 2%
Between $2 to $4 million 1%
Between $4 to $6 million 3%
Between $6 to $8 million 5%
Between $8 to $10 million 9%
Between $10 to $12 million 20%
Between $12 to $14 million 13%
Between $14 to $16 million 10%
Between $16 to $18 million 12%
Between $18 to $20 million 12%
Between $20 to $25 million 7%
Over $25 million 6%
Total 100%
Extrapolated value 14.45
Q15b. What dollar range best describes your organization’s IT security
budget for analytic tools in the present fiscal year? Pct%
Less than $2 million 77%
Between $2 to $4 million 6%
Between $4 to $6 million 6%
Between $6 to $8 million 4%
Between $8 to $10 million 3%
Between $10 to $12 million 1%
Between $12 to $14 million 2%
Between $14 to $16 million 1%
Between $16 to $18 million 0%
Between $18 to $20 million 0%
Between $20 to $25 million 0%
Over $25 million 0%
Total 100%
Extrapolated value 2.32
Ponemon Institute: Private & Confidential Report 18
Q16a. In terms of a percentage of the current IT security budget, how
much would your organization be willing to spend to reduce anomalous
and potentially malicious traffic by 10 percent? Pct%
Less than 5% 18%
Between 5% to 10% 36%
Between 10% to 20% 19%
Between 20% to 30% 12%
Between 30% to 40% 7%
Between 40% to 50% 3%
Between 50% to 60% 2%
Between 60% to 70% 2%
Between 70% to 80% 1%
Between 80% to 90% 0%
Between 90% to 100% 0%
Total 100%
Extrapolated value 16.0%
Q16b. In terms of a percentage of the current IT security budget, how
much would your organization be willing to spend to reduce anomalous
and potentially malicious traffic by 90 percent? Pct%
Less than 5% 3%
Between 5% to 10% 5%
Between 10% to 20% 5%
Between 20% to 30% 12%
Between 30% to 40% 19%
Between 40% to 50% 18%
Between 50% to 60% 11%
Between 60% to 70% 12%
Between 70% to 80% 9%
Between 80% to 90% 6%
Between 90% to 100% 0%
Total 100%
Extrapolated value 45%
Q17. With respect to the typical IT security budget, please rank where
Spending Spending in
your organization spends the most today and will spend 24 months in the
today the future
future, 1 = spending the most and 7 = spending the least.
Governance, compliance and reporting 1.97 2.31
Data loss detection and prevention 3.89 4.03
Perimeter controls 1.56 2.54
Identity management 2.75 3.34
Correlation of security information from multiple sources 6.55 4.15
Anomaly detection 4.66 3.90
Advanced persistent threat (APT) detection/prevention 5.63 4.88
Part 4. Analytics for cybersecurity
Q19. How difficult is the typical deployment of cybersecurity analytics
within your organization? Pct%
Very difficult 30%
Difficult 34%
Not difficult 21%
Easy 15%
Total 100%
Ponemon Institute: Private & Confidential Report 19
Q20. What best describes the level of involvement of third-party
consultants (experts) in the deployment of cybersecurity analytics within
your organization? Pct%
None 10%
Low 13%
Moderate 19%
Significant 30%
Very significant 28%
Total 100%
Essential and very important responses. Pct%
Q21a. How important is the ability to access and examine deep packet
data in cybersecurity analytics? 56%
Q21b. How important is the ability to examine user behavior analytics
(UBA) for cybersecurity? 54%
Following are key features of certain cybersecurity analytic tools in the
market today. Please rate each feature using the importance scale. Then
select the extent to which this feature is being deployed within your
organization.
Q22a. Provide unified data repository for “all” security data. Pct%
Essential and very important responses 65%
Fully and partially deployed responses 44%
Q22b. Enable powerful analytic frameworks that enable insider and
advanced persistent threat detection Pct%
Essential and very important responses 69%
Fully and partially deployed responses 40%
Q22c. Give threat analysts powerful visual analysis toolsets that slice
across multiple data sources at petabyte scale to identify outliers. Pct%
Essential and very important responses 63%
Fully and partially deployed responses 39%
Q22d. Supply full entity-centered contextual information at security
responders’ fingertips—to speed investigation and support development
of comprehensive mitigation strategies. Pct%
Essential and very important responses 60%
Fully and partially deployed responses 41%
Attributions: Please rate each statement using the agreement scale
provided below each item. Strongly agree and Agree responses. Pct%
Q23a. Leveraging big data and advanced analytics to get ahead of threats
is impossible with traditional systems. 72%
Q23b. Security operations must constantly offload data as budget
constraints and system limits are reached. 66%
Q23c. It takes days or weeks to access complementary data incident
responders need in order to respond to flagged events. 59%
Q23d. Threat analysts can’t perform advanced analytics (e.g. machine
learning) against TBs worth of data in short order. 61%
Q24. Would you be inclined to recommend your organization’s analytic
tools for cybersecurity to an acquaintance, colleague or friend? Pct%
Strongly recommend 40%
Recommend 35%
Do not recommend 25%
Total 100%
Ponemon Institute: Private & Confidential Report 20
Q25. How much does it cost to store one terabyte (TB) of your
organization’s security data? Pct%
Less that $500 per TB 19%
$500 to $1,000 per TB 23%
$1,001 to $5,000 per TB 36%
More than $5,000 per TB 22%
Total 100%
Extrapolated value 2,510
Q26a. Which are the primary data sources used to identify incidents?
Please select all that apply. Pct%
SIEM alerts 33%
Third party notifications 15%
Network data analysis 30%
File/executable analysis 18%
User behavior anomalies 44%
Threat intelligence 42%
Forensic investigation 59%
IT operations alerts/outages 12%
Endpoint analytics 34%
Total 287%
Q26b. Which are the secondary data sources used to identify incidents?
Please select all that apply. Pct%
SIEM alerts 46%
Third party notifications 60%
Network data analysis 46%
File/executable analysis 21%
User behavior anomalies 34%
Threat intelligence 70%
Forensic investigation 23%
IT operations alerts/outages 34%
Endpoint analytics 39%
Total 373%
Ponemon Institute: Private & Confidential Report 21
D1. What best describes your position level within the organization? Pct%
Executive 2%
Vice president 3%
Director 17%
Manager 23%
Supervisor 16%
Staff/technician 39%
Other 0%
Total 100%
D2. What best describes your direct reporting channel? Pct%
CEO/executive committee 0%
COO or head of operations 0%
CFO, controller or head of finance 2%
CIO or head of corporate IT 45%
General counsel or head of corporate legal 3%
Business unit leader or general manager 21%
Head of compliance or internal audit 4%
Head of IT security 18%
Head of security 2%
Other 5%
Total 100%
D3. What range best describes the full-time headcount of your global
organization? Pct%
< 1,000 23%
1,000 to 5,000 21%
5,001 to 10,000 20%
10,001 to 25,000 17%
25,001 to 75,000 11%
> 75,000 8%
Total 100%
D4. What best describes your organization’s primary industry
classification? Pct%
Agriculture & food services 1%
Communications 2%
Consumer products 5%
Defense & aerospace 1%
Education & research 2%
Energy & utilities 6%
Entertainment & media 3%
Financial services 17%
Health & pharmaceutical 11%
Hospitality 3%
Industrial & manufacturing 9%
Public sector 10%
Retail 10%
Services 9%
Technology & software 8%
Transportation 3%
Other 0%
Total 100%
Ponemon Institute: Private & Confidential Report 22
Please contact research@ponemon.org or call us at 800.877.3118 if you have any questions.
Ponemon Institute
Advancing Responsible Information Management
Ponemon Institute is dedicated to independent research and education that advances responsible
information and privacy management practices within business and government. Our mission is to conduct
high quality, empirical studies on critical issues affecting the management and security of sensitive
information about people and organizations.
As a member of the Council of American Survey Research Organizations (CASRO), we uphold strict
data confidentiality, privacy and ethical research standards. We do not collect any personally identifiable
information from individuals (or company identifiable information in our business research). Furthermore, we
have strict quality standards to ensure that subjects are not asked extraneous, irrelevant or improper
questions.
Ponemon Institute: Private & Confidential Report 23
Вам также может понравиться
- Cybersecurity (IoT)Документ72 страницыCybersecurity (IoT)Ainul NasihaОценок пока нет
- Pengantar Teknik Kimia Sesi 1 Peralatan Proses: Ir. Abdul Wahid Surhim, MTДокумент14 страницPengantar Teknik Kimia Sesi 1 Peralatan Proses: Ir. Abdul Wahid Surhim, MTAinul NasihaОценок пока нет
- TRIZ AssignmentДокумент4 страницыTRIZ AssignmentAinul NasihaОценок пока нет
- Tabulation Data and Calculation Exp1Документ3 страницыTabulation Data and Calculation Exp1Ainul NasihaОценок пока нет
- Explain The Meaning of Total DerivativeДокумент4 страницыExplain The Meaning of Total DerivativeAinul NasihaОценок пока нет
- Graph of Reciprocal of Precision Velocity Against Rotor VelocityДокумент5 страницGraph of Reciprocal of Precision Velocity Against Rotor VelocityAinul NasihaОценок пока нет
- Guangyu Mu and Xiaozhen MiДокумент5 страницGuangyu Mu and Xiaozhen MiAinul NasihaОценок пока нет
- Martin Spur GearsДокумент39 страницMartin Spur GearsrukahuaОценок пока нет
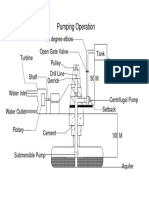
- Pumping Operation: Open Gate Valve 90 Degree Elbow Turbine Drill LineДокумент1 страницаPumping Operation: Open Gate Valve 90 Degree Elbow Turbine Drill LineAinul NasihaОценок пока нет
- Kedudukan Vvip N VipДокумент1 страницаKedudukan Vvip N VipAinul NasihaОценок пока нет
- Cover CL 1224Документ1 страницаCover CL 1224Ainul NasihaОценок пока нет
- Project Proposal Form SampleДокумент3 страницыProject Proposal Form SampleAinul NasihaОценок пока нет
- To Metals & Alloys: Mariyam Jameelah Ghazali, Phd. 2015/201 6Документ72 страницыTo Metals & Alloys: Mariyam Jameelah Ghazali, Phd. 2015/201 6Ainul NasihaОценок пока нет
- Chapter 2 Force Vectors Ver.1Документ59 страницChapter 2 Force Vectors Ver.1Ainul NasihaОценок пока нет
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5795)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (345)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (400)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1091)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (121)
- The Big Book of BitTorrent PDFДокумент28 страницThe Big Book of BitTorrent PDFAlex NessОценок пока нет
- Rundown Pembukaan (Kamis Siang) AДокумент3 страницыRundown Pembukaan (Kamis Siang) ARizky JPОценок пока нет
- E24000-2!10!14 Control Modules EHCD Product RangeДокумент64 страницыE24000-2!10!14 Control Modules EHCD Product RangeSergiy SydorenkoОценок пока нет
- More Sample Ques 2Документ284 страницыMore Sample Ques 2Gagan RajОценок пока нет
- Xibo Open Source Digital SignageДокумент1 страницаXibo Open Source Digital SignageRalph Vincent IIIОценок пока нет
- Buying Purchasing Hardware Software WorkstationДокумент9 страницBuying Purchasing Hardware Software WorkstationYadu Priya DeviОценок пока нет
- Unit 1Документ18 страницUnit 1ÇHÅÍTÛ MØVÏÈ LØVÊRОценок пока нет
- B0700FCДокумент176 страницB0700FCfadhelОценок пока нет
- TWS EAERBUDS Price List From HOPORA CompanyДокумент15 страницTWS EAERBUDS Price List From HOPORA CompanySindy JimenezОценок пока нет
- nGeniusPULSE Virtual Install GuideДокумент23 страницыnGeniusPULSE Virtual Install Guidemodather nadyОценок пока нет
- How To Make An Online Donation To CMCCKL Online AccountДокумент4 страницыHow To Make An Online Donation To CMCCKL Online AccountEdwin NgОценок пока нет
- Oracle® E-Business Suite: Concepts Release 12.2Документ214 страницOracle® E-Business Suite: Concepts Release 12.2Shaik MujeebОценок пока нет
- Cresume Simral ChaudharyДокумент2 страницыCresume Simral Chaudharyapi-271251357Оценок пока нет
- Organisasi Dan Arsitektur Komputer: CPU Execution Time Amil A. IlhamДокумент19 страницOrganisasi Dan Arsitektur Komputer: CPU Execution Time Amil A. IlhamcharlesОценок пока нет
- Ey Amit Kumar Pandey CV - Jan 2015Документ6 страницEy Amit Kumar Pandey CV - Jan 2015amitom_pandeyОценок пока нет
- Andriod Progemming All in OneДокумент46 страницAndriod Progemming All in OneBnaren NarenОценок пока нет
- 1 Gradeabc: Technology Skill Rubric I BimesterДокумент4 страницы1 Gradeabc: Technology Skill Rubric I BimesterDiplomado UCRISHОценок пока нет
- DSS-019 Digital Video DatasheetДокумент10 страницDSS-019 Digital Video DatasheetCoach-Julio CruzОценок пока нет
- Lab ExerciseДокумент9 страницLab ExerciseSheila Mae FajutaganaОценок пока нет
- 8.4.1.2 Packet Tracer - Skills Integration Challenge InstructionsДокумент2 страницы8.4.1.2 Packet Tracer - Skills Integration Challenge InstructionsTyshaun Moore Eit0% (1)
- Chapter 22Документ80 страницChapter 22Kushagra TiwaryОценок пока нет
- Windows ADADДокумент26 страницWindows ADADankitОценок пока нет
- Dummies - Hack How To Create Keygens PDFДокумент6 страницDummies - Hack How To Create Keygens PDFRexal Mundri Bhasa IIОценок пока нет
- Project TemplateДокумент17 страницProject TemplateMazhar MahadzirОценок пока нет
- Lesson 1: Introduction To MATLAB: Akos Ledeczi and Mike FitzpatrickДокумент9 страницLesson 1: Introduction To MATLAB: Akos Ledeczi and Mike FitzpatrickSamuel TesfayОценок пока нет
- Geit-20219 Dmsgoseries enДокумент4 страницыGeit-20219 Dmsgoseries ensolrac4371Оценок пока нет
- Jnan Chandra Ghosh Polytechnic Revised Online Class Routine of Electronics & Telecommunication Engg. Department W.E.F 12th May, 2021Документ3 страницыJnan Chandra Ghosh Polytechnic Revised Online Class Routine of Electronics & Telecommunication Engg. Department W.E.F 12th May, 2021SubdeyОценок пока нет
- Laguna Northwestern College: San Lorenzo Ruiz Montessori CenterДокумент6 страницLaguna Northwestern College: San Lorenzo Ruiz Montessori CentermikedrewОценок пока нет
- Automatic Accident Detection and Ambulance Rescue SystemДокумент3 страницыAutomatic Accident Detection and Ambulance Rescue SystemEditor IJRITCCОценок пока нет
- Advanced SQL Presentation TemplateДокумент29 страницAdvanced SQL Presentation Templateamit kumarОценок пока нет