Академический Документы
Профессиональный Документы
Культура Документы
Globalprotect
Загружено:
Rambell John RodriguezОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Globalprotect
Загружено:
Rambell John RodriguezАвторское право:
Доступные форматы
GlobalProtect
GlobalProtect extends the protection of the Palo Alto Networks
Next-Generation Firewall to the members of your mobile
workforce, no matter where they go.
The world you need to secure continues to expand as users and applications
shift to locations outside the traditional network perimeter. Security teams
face challenges with maintaining visibility into network traffic and enforcing
security policies to stop threats. Traditional technologies used to protect
mobile endpoints, such as host endpoint antivirus software and remote
access virtual private networks (VPNs), cannot stop the advanced techniques
employed by today’s sophisticated attackers.
GlobalProtect™ network security for endpoints enables you to protect your
mobile workforce by extending the Palo Alto Networks Next-Generation
Firewall to all users, regardless of location. It secures traffic by applying the
platform’s capabilities to understand application use, associate the traffic
with users and devices, and enforce security policies with next-generation
technologies.
Strata by Palo Alto Networks | GlobalProtect | Datasheet 1
Key Usage Scenarios and Benefits Bring-Your-Own-Device Policies
Remote Access VPN • Supports app-level VPN for user privacy.
• Provides secure access to internal and cloud-based • Enables secure, clientless access for partners,
business applications. business associates, and contractors.
Advanced Threat Prevention • Supports automated identification of
unmanaged devices.
• Secures internet traffic.
• Supports customized authentication
• Stops threats from reaching the endpoint. mechanisms for managed and unmanaged
• Protects against phishing and credential theft. devices.
• Quarantines compromised devices by leveraging Zero Trust Implementation
immutable characteristics.
• Delivers reliable user identification.
URL Filtering
• Delivers immediate and accurate host
• Enforces acceptable use policies. information for visibility and policy enforcement.
• Filters access to malicious domains and adult content. • Enforces step-up multi-factor authentication
• Prevents the use of avoidance and evasion tools. to access sensitive resources.
• Secures access to SaaS applications.
• Controls access and enforces policies for SaaS
applications while blocking unsanctioned
applications.
Extending the Platform In addition, GlobalProtect enables you to quarantine com-
Protection Externally
promised devices by utilizing an endpoint’s immutable char-
acteristics. This will allow administrators to restrict network
GlobalProtect safeguards your mobile workforce by inspect- access as well as prevent the compromised endpoint from
ing all traffic using your Next-Generation Firewalls deployed infecting other users and devices. Quarantine restrictions
as internet gateways, whether at the perimeter, in the Demil- can apply whether the compromised device is external or on
itarized Zone (DMZ), or in the cloud. Laptops, smartphones, the internal network.
and tablets with the GlobalProtect app automatically establish
a secure IPsec/SSL VPN connection to the Next-Generation
Firewall using the best gateway, thus providing full visibili-
Inspection of Traffic and
ty of all network traffic, applications, ports, and protocols. By Enforcement of Security Policies
eliminating the blind spots in mobile workforce traffic, your
organization can maintain a consistent view into applications. GlobalProtect enables security teams to build policies that are
consistently enforced whether the user is internal or remote.
Security teams can prevent successful cyberattacks by bring-
Implementing Zero Trust in Your ing all of the platform’s capabilities to bear:
Network • App-ID™ technology identifies application traffic, regard-
less of port number, and enables organizations to establish
Not all users need access to all assets inside your corporate net- policies to manage application usage based on users and
work. Security teams are adopting Zero Trust principles to seg- devices.
ment their networks and enforce precise controls for access to
• User-ID™ technology identifies users and group member-
internal resources. GlobalProtect provides the fastest, most au-
ships for visibility as well as the enforcement of role-based
thoritative user identification for the platform, enabling you to
network security policies.
write precise policies that allow or restrict access based on busi-
ness need. Furthermore, GlobalProtect provides host informa- • SSL Decryption inspects and controls applications that are
tion that establishes device compliance criteria associated with encrypted with SSL/TLS/SSH traffic and stops threats with-
security policies. These measures allow you to take preventive in the encrypted traffic.
steps to secure your internal networks, adopt Zero Trust net- • WildFire® malware prevention service automates the
work controls, and reduce the risk of attack. analysis of content to identify new, previously unknown,
When GlobalProtect is deployed in this manner, the inter- and highly targeted malware by its behavior and generates
nal network gateways may be configured with or without a the threat intelligence to stop it in near-real time.
VPN tunnel.
Strata by Palo Alto Networks | GlobalProtect | Datasheet 2
• Threat Prevention for IPS and antivirus blocks network- • Machine certificates present on device
based exploits targeting vulnerable applications and op- • Device information received from mobile device manager
erating systems, denial-of-service (DoS) attacks, and port
• Operating system and application patch level
scans. Antivirus profiles stop malware and spyware from
reaching the endpoint using a stream-based engine. • Host anti-malware version and state
• URL Filtering with PAN-DB categorizes URLs based on their • Host firewall version and state
content at the domain, file, and page level, and receives up- • Disk encryption configuration
dates from WildFire so that when web content changes, so • Data backup product configuration
do categorizations.
• Customized host conditions (e.g., registry entries, running
• File blocking stops the transfer of unwanted and dangerous software)
files while further scrutinizing allowed files with WildFire.
• Data filtering enables administrators to implement poli- Control Access to Applications and Data
cies that can be used to stop the unauthorized movement of Security teams can establish policies based on application,
data, such as the transfer of customer information or other user, content, and host information to maintain granular
confidential content. control over access to a given application. These policies
may be associated with specific users or groups defined in
Secure Access Control a directory to ensure that organizations provide the correct
User Authentication levels of access based on business need. The security team
can further establish policies for step-up MFA to provide ad-
GlobalProtect supports all existing PAN-OS® authentication ditional proof of identity before accessing particularly sen-
methods, including Kerberos, RADIUS, LDAP, SAML 2.0, cli- sitive resources and applications.
ent certificates, biometric sign-in, and a local user database.
Once GlobalProtect authenticates the user, it immediately
provides the Next-Generation Firewall with a user-to-IP- Enhanced Troubleshooting and
address mapping for User-ID.
Visibility
Strong Authentication Options GlobalProtect Application Command Center (ACC) widgets,
GlobalProtect supports a range of third-party multi-factor reports, and the new GlobalProtect log provide full visibility
authentication (MFA) methods, including one-time pass- into GlobalProtect usage in your deployment. Detailed log-
word tokens, certificates, and smart cards, through RADIUS ging of the connection workflow in stages greatly simplifies
and SAML integration. troubleshooting of user connection issues. This logging al-
These options help organizations strengthen the proof of lows administrators to easily identify the stage/event in the
identity for access to internal data center or software-as-a- connection process where a given user has an issue.
service (SaaS) applications.
GlobalProtect has options to make strong authentication even Secure and Enabled BYOD
easier to use and deploy:
The effects of bring-your-own-device (BYOD) policies are
• Cookie-based authentication: After authentication, you changing the number of use case permutations that security
may choose to use an encrypted cookie for subsequent teams need to support. It is necessary to provide application
access to a portal or gateway for the lifetime of that cookie. access to a broader spectrum of employees and contractors
• Simplified certificate enrollment protocol support: using a wide range of mobile devices.
GlobalProtect can automate the interaction with an
Integration with mobile device management offerings,
enterprise public key infrastructure (PKI) for managing, is- such as AirWatch® and MobileIron®, can help you deploy
suing, and distributing certificates to GlobalProtect clients. GlobalProtect as well as provide additional security measures
• MFA: Before a user can access an application, he or she can through the exchange of intelligence and host configuration.
be required to present an additional form of authentication. Using these in conjunction with GlobalProtect, your organi-
zation can maintain visibility and the enforcement of security
Host Information Profile policy on a per-app basis while maintaining data separation
GlobalProtect checks the endpoint to get an inventory of from personal activities to honor the user’s expectations of
how it’s configured and builds a host information profile privacy in BYOD scenarios.
(HIP) that’s shared with the Next-Generation Firewall. The
GlobalProtect supports clientless SSL VPN for secure access to
Next-Generation Firewall uses the HIP to enforce application
applications in the data center and the cloud from unmanaged
policies that only permit access when the endpoint is properly
devices. This approach allows customers to enable secure ac-
configured and secured. These principles help enforce com-
cess for third-party users and employees connecting from
pliance with policies that govern the amount of access a given
BYOD devices by providing access to specific applications
user should have with a particular device.
through a web interface, both without requiring users to in-
HIP policies can be based on a number of attributes, including: stall a client and without setting up a VPN tunnel.
• Managed/Unmanaged device identification
Strata by Palo Alto Networks | GlobalProtect | Datasheet 3
Architecture Matters companies evolve, whether on a temporary basis (e.g., follow-
ing a natural disaster) or a permanent one (e.g., when entering
The flexible architecture for GlobalProtect provides many
new markets).
capabilities that can help you solve an array of security chal-
lenges. At the most basic level, you can use GlobalProtect as Prisma™ Access by Palo Alto Networks provides a co-managed
a replacement for the traditional VPN gateway, eliminating option for deploying coverage in the locations organizations
the complexity and headaches of administering a stand- need, using your security policies. It can be used in conjunction
alone, third-party VPN gateway. with your existing firewalls, making your architecture adapt-
able to changing conditions.
Options for manual connections and gateway selection en-
able you to tailor the configuration to support business re- Prisma Access supports auto-scaling, which d ynamically allo-
quirements as needed. cates new firewalls based on load and demand in a given region.
In a more comprehensive deployment for securing traffic,
GlobalProtect can be deployed with an always-on VPN con- Conclusion
nection with a full tunnel, ensuring that protection is always
present and transparent to the user experience. Exceptions The Palo Alto Networks Next-Generation Firewall plays a
can be defined for latency-sensitive traffic by application, critical role in preventing breaches. Use GlobalProtect to ex-
domain names and routes, or video traffic. tend the protection of the platform to users wherever they go.
By using GlobalProtect, you can get consistent enforcement
Cloud-Based Gateways of security policy so that even when users leave the building,
Workforces shift from one location to another, creating chang- their protection from cyberattacks remains in place.
es in traffic load. This is especially true when considering how
Table 1: GlobalProtect Features
Category Specification
IPsec
SSL
VPN Connection
Clientless VPN
Per-app VPN on Android, iOS
Automatic selection
Manual selection
Gateway Selection Preferred gateway selection
External gateway selection by source location
Internal gateway selection by source IP
User logon (always-on)
On-demand
Connection Methods Pre-logon (always-on)
Pre-logon, then on-demand
User-initiated pre-logon
Internal mode
Connection Mode
External mode
IPv4
Layer 3 P
rotocols
IPv6
SSO (Windows credential provider)
Single Sign-On Kerberos SSO
SSO for macOS
Include routes, domains, applications
Split Tunneling
Exclude routes, domains, applications
Strata by Palo Alto Networks | GlobalProtect | Datasheet 4
Table 1: GlobalProtect Features (continued)
SAML 2.0
LDAP
Client certificates
Authentication Methods Kerberos
RADIUS
Two-factor authentication
Authentication method selection based on operating system or device ownership
Patch management
Host anti-spyware
Host anti-malware
HIP Reporting, Policy Host firewall
Enforcement, and Notifications Disk encryption
Disk backup
Data loss prevention
Customized HIP conditions (e.g., registry entries, r unning software)
By machine certificates
Managed Device Identification
By hardware serial number
MFA At connect time and resource access time
User-ID
IPsec to SSL VPN fallback
Enforce GlobalProtect connection for network access
Tunnel configuration based on user location
HIP report redistribution
Certificate checks in HIP
SCEP-based automatic user certificate management
Script actions that run before and after sessions
Dynamic GlobalProtect app customization
App configuration based on users, groups, and/or operating systems
Automatic internal/external detection
Manual/automatic upgrade of GlobalProtect app
Certificate selection by OID
Other Features
Blocking of access by lost, stolen, or unknown devices
Smart card support for connection/disconnection
Transparent distribution of trusted root CAs for SSL decryption
Disabling of direct access to local networks
Customizable welcome and help pages
RDP connection to a remote client
Operating system-native notifications
User sign-out restriction
Proxy support
Enforcement of GlobalProtect exclusions
Connection with SSL only
RSA software token integration
Device Quarantine
Strata by Palo Alto Networks | GlobalProtect | Datasheet 5
Table 1: GlobalProtect Features (continued)
AirWatch
MDM/EMM Integration MobileIron
Microsoft Intune
Palo Alto Networks Next-Generation Firewalls, including physical and virtual appliances
Management Tools and APIs Prisma Access
Panorama network security management
Microsoft Windows and Windows UWP
Apple macOS
Apple iOS and iPadOS
GlobalProtect App Supported Plat-
Google Chrome OS
forms
Android OS
Linux OS (Red Hat, CentOS, Ubuntu)
IoT devices
Apple iOS IPsec client
IPsec XAuth Android OS IPsec client
Third-party VPNC and strongSwan client
GlobalProtect App Localization Chinese, English, French, German, Japanese, Spanish
3000 Tannery Way © 2020 Palo Alto Networks, Inc. Palo Alto Networks is a registered
Santa Clara, CA 95054 trademark of Palo Alto Networks. A list of our trademarks can be found at
https://www.paloaltonetworks.com/company/trademarks.html. All other
Main: +1.408.753.4000 marks mentioned herein may be trademarks of their respective companies.
Sales: +1.866.320.4788 strata-globalprotect-ds-060120
Support: +1.866.898.9087
www.paloaltonetworks.com
Вам также может понравиться
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (121)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (400)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5795)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2259)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (345)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- Discord: Onlyfans Money Method by DarkcoderДокумент3 страницыDiscord: Onlyfans Money Method by DarkcoderJulius Baldivino50% (2)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- Systems SecurityДокумент257 страницSystems SecurityMuriithi MurageОценок пока нет
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- Unstable Unicorns RuledlkfkfДокумент4 страницыUnstable Unicorns RuledlkfkfRambell John RodriguezОценок пока нет
- Performance Tuning Guidelines Windows Server 2012Документ182 страницыPerformance Tuning Guidelines Windows Server 2012Leonardo HernandezОценок пока нет
- Jira BrochureДокумент2 страницыJira BrochureCandice H.Оценок пока нет
- Reference Architecture For Cisco ACI - Rel 2 - Jul 2018Документ39 страницReference Architecture For Cisco ACI - Rel 2 - Jul 2018Umit ArslanОценок пока нет
- Rambell Rodriguez PDS (Nov)Документ4 страницыRambell Rodriguez PDS (Nov)Rambell John RodriguezОценок пока нет
- Book ReferencesДокумент5 страницBook ReferencesRambell John RodriguezОценок пока нет
- PremiumContributionTable PDFДокумент1 страницаPremiumContributionTable PDFRambell John RodriguezОценок пока нет
- Rodriguez, Rambell John A.: 909 Hilerang Kawayan ST., Lawa, Obando, Bulacan 3021Документ3 страницыRodriguez, Rambell John A.: 909 Hilerang Kawayan ST., Lawa, Obando, Bulacan 3021Rambell John RodriguezОценок пока нет
- Quiz4-Responsibilityacctg TP BalscoreДокумент5 страницQuiz4-Responsibilityacctg TP BalscoreRambell John RodriguezОценок пока нет
- College of Accountancy and Business Administration College of Accountancy and Business AdministrationДокумент1 страницаCollege of Accountancy and Business Administration College of Accountancy and Business AdministrationRambell John RodriguezОценок пока нет
- Good Gov and Soc. ResДокумент4 страницыGood Gov and Soc. ResRambell John RodriguezОценок пока нет
- Festival 2018: Sta Maria ChoralДокумент1 страницаFestival 2018: Sta Maria ChoralRambell John RodriguezОценок пока нет
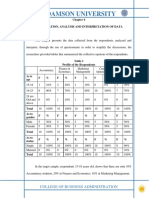
- Adamson University: Presentation, Analysis and Interpretation of DataДокумент1 страницаAdamson University: Presentation, Analysis and Interpretation of DataRambell John RodriguezОценок пока нет
- Nips at Heart Jingle LyricsДокумент1 страницаNips at Heart Jingle LyricsRambell John RodriguezОценок пока нет
- Baby SharkfffДокумент2 страницыBaby SharkfffRambell John RodriguezОценок пока нет
- Table 4 Nila PAtrickДокумент1 страницаTable 4 Nila PAtrickRambell John RodriguezОценок пока нет
- Complaint AGUSM Med School BelizeДокумент10 страницComplaint AGUSM Med School BelizeMarty SchwimmerОценок пока нет
- BULATS Reading Part 1 Section 3Документ3 страницыBULATS Reading Part 1 Section 3mari roxanОценок пока нет
- Emerging Technologies For The Provision of Access To Archives: Issues, Challenges and IdeasДокумент29 страницEmerging Technologies For The Provision of Access To Archives: Issues, Challenges and IdeasTim SherrattОценок пока нет
- Jio Digitization Survey On Small and Medium BusinessesДокумент26 страницJio Digitization Survey On Small and Medium BusinessesManajit BhowmikОценок пока нет
- Coral Iris Ivdx Media Gateway 3u CabinetДокумент4 страницыCoral Iris Ivdx Media Gateway 3u CabinetShubham KumarОценок пока нет
- Cambridge English b1 Preliminary For Schools Poster and Activity PackДокумент3 страницыCambridge English b1 Preliminary For Schools Poster and Activity PackIoana IvancuОценок пока нет
- 4CCNP Security Secure 642-637 Quick Reference - Cisco Layer 2 Security - Types of Layer 2 Attacks PDFДокумент3 страницы4CCNP Security Secure 642-637 Quick Reference - Cisco Layer 2 Security - Types of Layer 2 Attacks PDFAbdulkerim SeidОценок пока нет
- Sim300c Atc V2.00Документ214 страницSim300c Atc V2.00van_dung90Оценок пока нет
- Cincinnati Police Department Body-Camera Policy.Документ8 страницCincinnati Police Department Body-Camera Policy.KHOUОценок пока нет
- Osama Aaloul CVДокумент2 страницыOsama Aaloul CVNatalie HobbsОценок пока нет
- Brand Rex 2016 Catalogue-WebДокумент96 страницBrand Rex 2016 Catalogue-WebjuliosieteОценок пока нет
- Mobile Services: Your Account Summary This Month'S ChargesДокумент3 страницыMobile Services: Your Account Summary This Month'S ChargesVintageОценок пока нет
- 7050 Series 1/10G BASE-T Data Center Switches: Product HighlightsДокумент6 страниц7050 Series 1/10G BASE-T Data Center Switches: Product Highlightschalapathi pОценок пока нет
- Sample StoryДокумент2 страницыSample StoryLara Mae Gonzales100% (1)
- Ethical, Social, and Political Issues in E-CommerceДокумент25 страницEthical, Social, and Political Issues in E-CommerceAlan PeakОценок пока нет
- Configure VPNДокумент10 страницConfigure VPNAnonymous 47X0OmSkipОценок пока нет
- WebMethods AdaptersДокумент4 страницыWebMethods AdaptersFrancescoОценок пока нет
- RSW Help Guide PDFДокумент64 страницыRSW Help Guide PDFChema Don GarОценок пока нет
- GV-POE2401 User Manual (POE2401-A-EN)Документ48 страницGV-POE2401 User Manual (POE2401-A-EN)Stiven RomezОценок пока нет
- Tariq CV IBSДокумент4 страницыTariq CV IBSTariq MahmoodОценок пока нет
- DSDH Ipc Hfw4231en Se 0360bДокумент3 страницыDSDH Ipc Hfw4231en Se 0360bChristian Camilo Pedraza OlayaОценок пока нет
- What Why and Where of Backlinks, List of Dofollow Sites.Документ78 страницWhat Why and Where of Backlinks, List of Dofollow Sites.Bulbul SharmaОценок пока нет
- Four51 PunchOut User GuideДокумент7 страницFour51 PunchOut User GuidefabhiveОценок пока нет
- BTC - AUTOPILOT - METHOD - Make 700$-1000$Документ4 страницыBTC - AUTOPILOT - METHOD - Make 700$-1000$john renoldОценок пока нет
- Complete Guide - Proper Shimming - Filipino Airsoft (FAS) - ForumДокумент8 страницComplete Guide - Proper Shimming - Filipino Airsoft (FAS) - ForumAmeer Marco LawanОценок пока нет