Академический Документы
Профессиональный Документы
Культура Документы
Lecture # 44: Selector
Загружено:
api-3812413Исходное описание:
Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Lecture # 44: Selector
Загружено:
api-3812413Авторское право:
Доступные форматы
System Programming Course Code: CS609
Cs609@vu.edu.pk
Lecture # 44
Selector
• A Selector is called a Selector because it acts as an
index into the Descriptor Table to select a GDT or LDT
entry.
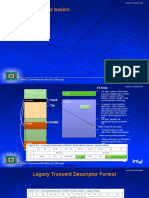
Segment Register
15 2 1 0
TI RPL
TI = 0 Global
TI = 1 Local
Selector Index Requested Privilege Level
Selects a Descriptor Table entry 00 (Highest)
From LDT or GDT 11 (Lowest)
Address Translation in
Protected Mode
• All the tables are maintained in Main Memory.
• Segment Registers are used as Selectors.
• The Descriptor Entry selected from the Descriptor Table
is placed in a hidden cache to optimize address
translation.
Virtual University of Pakistan 92
System Programming Course Code: CS609
Cs609@vu.edu.pk
The hidden cache is illustrated in the slide below. The registers in dotted lines are hidden
i.e. are not accessible to any application directly.
Base Address Limit Access Rights
CS
DS
ES
SS
FS
GS
TR
LDTR
Ba se Limit GDTR
IDTR
Address Translation in
Protected Mode
• Whenever a Selector is assigned a new value, the hardware looks up into the
Descriptor Table and loads the Base Address, Limit and Access Rights into the
hidden cache.
• Whenever an instruction is issued the address referred is translating into Physical
address using the effective Offset within the instruction and the Base Address in the
corresponding Segment Cache, e.g.
mov AX, [1234H]
effective offset = 1234H
base = base within the cache of DS
abs. address = base +1234H
Or in instruction
mov DL, [EBP]
effective offset address = EBP
base address = base address in cache of SS register
abs. address = base address + EBP
• Hence the absolute address cannot be calculated directly from the Segment address
value.
Virtual University of Pakistan 93
System Programming Course Code: CS609
Cs609@vu.edu.pk
Control Register
• 80386 and above have 4 Control Registers CR0 ~ CR3.
• These Control Registers are used for conveying certain
control information for Protected Mode Addressing and
Co-Processors.
• Here we will illustrate only the least significant bit of
CR0.
PE
CR0
• The least significant bit of CR0 is PE-bit which can be
set to enable Protected Mode Addressing and can be
cleared to enter Real Mode.
Moving to Protected Mode
• Protected Mode can be entered by setting the PE bit of CR0, but
before this some other initialization must be done. The following
steps accomplish the switching from Real to Protected Mode
correctly.
1. Initialize the Interrupt Descriptor Table, so it contains valid Interrupt
gates for at least the first 32 Interrupt type numbers. The IDT may
contain up to 256, 8-byte interrupt gates defining all 256 interrupt
types.
2. Initialize the GDT, so it contains a NULL Descriptor, at Descriptor 0
and valid Descriptor for at least one Data and one Stack.
3. Switch to Protected by setting the PE-bit in CR0.
4. Perform a IntraSegment (near) JMP to flush the Internal Pre-fetch
Queue.
5. Load all the Data Selectors (Segment Registers) with their initia l
Selectors Values.
6. The 80386 is now in Protected Mode.
Virtual University of Pakistan 94
System Programming Course Code: CS609
Cs609@vu.edu.pk
Viruses
Viruses
• Viruses are special program having ability to embed
themselves in a system resources and there on propagate
themselves.
State of Viruses
• Dormant State: A Virus in dormant state has
embedded itself within and is observing system activities.
• Activation State: A Virus when activated would
typically perform some unwanted tasks causing data loss.
This state may triggered as result of some event.
• Infection State: A Virus is triggered into this
state typically as a result of some disk operation. In this
state, the Virus will infect some media or file in order to
propagate itself.
Virtual University of Pakistan 95
Вам также может понравиться
- Addressing Modes 8086Документ19 страницAddressing Modes 8086Infinity Star GamingОценок пока нет
- Systems Programming For The Intel ArchitectureДокумент14 страницSystems Programming For The Intel ArchitectureDebashish PalОценок пока нет
- Protected Address Mode Software Architecture of 80386dxДокумент29 страницProtected Address Mode Software Architecture of 80386dxSanjivanee KumbharОценок пока нет
- Question Bank CPIT 210Документ8 страницQuestion Bank CPIT 210ABDULRAHIM ABBAS BAZIОценок пока нет
- Load and Store InstructionsДокумент32 страницыLoad and Store Instructionsmkollam100% (1)
- The Various x86 Modes': On Understanding Key Differences Among The Processor's Several Execution-ArchitecturesДокумент19 страницThe Various x86 Modes': On Understanding Key Differences Among The Processor's Several Execution-ArchitecturesKarthik KeyanОценок пока нет
- The Memory Management Real Mode: Lecture Note 5Документ9 страницThe Memory Management Real Mode: Lecture Note 5Gunjan VermaОценок пока нет
- PLDI Week 04 LLVMДокумент62 страницыPLDI Week 04 LLVMVictor ZhaoОценок пока нет
- Slide TienganhHДокумент34 страницыSlide TienganhHHoàngNguyễnОценок пока нет
- Chap17 Lect15 Segmentation PDFДокумент14 страницChap17 Lect15 Segmentation PDFDenise NelsonОценок пока нет
- Processing Unit - Data PathДокумент14 страницProcessing Unit - Data PathDarsh GuptaОценок пока нет
- 6 - Embedded System ProgrammingДокумент117 страниц6 - Embedded System ProgrammingWarenya RanminiОценок пока нет
- MIL Lab Manual NewДокумент97 страницMIL Lab Manual NewAmit Sangale100% (1)
- Unit 2 CaoДокумент8 страницUnit 2 CaoZamal AhmedОценок пока нет
- ARM Instruction SetДокумент5 страницARM Instruction SetArijit BoseОценок пока нет
- ARM Instructions - Part D Memory Access InstructionsДокумент20 страницARM Instructions - Part D Memory Access InstructionsBob BobОценок пока нет
- 4 - 3 - Modified - Code GenerationДокумент31 страница4 - 3 - Modified - Code GenerationAkula SandeepОценок пока нет
- Constant Propagation: CS 701 Fall 2007Документ18 страницConstant Propagation: CS 701 Fall 2007SahilОценок пока нет
- Week 6Документ33 страницыWeek 6aroosa naheedОценок пока нет
- Lab 5 - Assembly Language Fundamentals 2Документ15 страницLab 5 - Assembly Language Fundamentals 2mahmoud.badry100Оценок пока нет
- Memory & Segmentation - PpsДокумент12 страницMemory & Segmentation - Ppsppat2006Оценок пока нет
- 13.3 Reading A System Status List or Partial List With SFC 51 "Rdsysst"Документ6 страниц13.3 Reading A System Status List or Partial List With SFC 51 "Rdsysst"Daniel RGОценок пока нет
- Lecture05 - 8086 AssemblyДокумент43 страницыLecture05 - 8086 Assemblytesfu zewduОценок пока нет
- Kinco VFD Communication ManualДокумент11 страницKinco VFD Communication ManualNATHANEASTBOUNDОценок пока нет
- Chapter 4 Assembly Language and ProgrammingДокумент85 страницChapter 4 Assembly Language and ProgrammingPetra Kalasa100% (1)
- CE302 Microprocessors: Levent Eren Izmir University of EconomicsДокумент26 страницCE302 Microprocessors: Levent Eren Izmir University of EconomicsFet hiОценок пока нет
- Embedded System - Interfacing With 8051Документ69 страницEmbedded System - Interfacing With 8051DevashishОценок пока нет
- LAB3-Implementation of Mov and XCHNGДокумент6 страницLAB3-Implementation of Mov and XCHNGalihassan009669Оценок пока нет
- Computer Organization and Assembly Lan-Guage Lab Manual (Lab 01)Документ7 страницComputer Organization and Assembly Lan-Guage Lab Manual (Lab 01)Huzaifa IrfanОценок пока нет
- Xps Central DmaДокумент23 страницыXps Central DmaRadu BlanaruОценок пока нет
- Chap2 RISC5 ISAДокумент31 страницаChap2 RISC5 ISAAmanda Judy AndradeОценок пока нет
- AVR32 Architecture Document: Feature SummaryДокумент378 страницAVR32 Architecture Document: Feature SummaryByron Paul CajamarcaОценок пока нет
- 0.1 Segment/Interrupt DescriptorsДокумент8 страниц0.1 Segment/Interrupt DescriptorsGregory BergschneiderОценок пока нет
- Lecture#2 Fut Microprocessor PDFДокумент81 страницаLecture#2 Fut Microprocessor PDFAhmedGamalОценок пока нет
- INTEL 8086 MicroprocessorДокумент85 страницINTEL 8086 MicroprocessorsaiОценок пока нет
- VLSI Presentation1Документ187 страницVLSI Presentation1migadОценок пока нет
- T5L DWIN OS Development Guide 20220518Документ18 страницT5L DWIN OS Development Guide 20220518ZillaIllozОценок пока нет
- CSCI3420 Computer System Architectures Project Phase 2Документ6 страницCSCI3420 Computer System Architectures Project Phase 2Nic02417Оценок пока нет
- 04 8051 Instruction SetДокумент76 страниц04 8051 Instruction SetharinkhedetОценок пока нет
- Lecture-1-2-3 UEC859 PDFДокумент63 страницыLecture-1-2-3 UEC859 PDFJaskaran SinghОценок пока нет
- Cortex-M3/M4 ArchitectureДокумент37 страницCortex-M3/M4 Architecturesuhaskakade0075745Оценок пока нет
- V HDL TutorialДокумент74 страницыV HDL Tutorialanmol123454Оценок пока нет
- Intel x86 Architecture 1326950278 Phpapp02 120118231851 Phpapp02Документ71 страницаIntel x86 Architecture 1326950278 Phpapp02 120118231851 Phpapp02krishnadevanur100% (1)
- COA Unit 1 Lecture 6Документ10 страницCOA Unit 1 Lecture 6Pratibha SОценок пока нет
- The 80x86 Microprocessor: Dara RahmatiДокумент31 страницаThe 80x86 Microprocessor: Dara Rahmatimohammadreza aminiОценок пока нет
- 80186Документ24 страницы80186a_charaniaОценок пока нет
- Unit - 3Документ29 страницUnit - 3ayush bansalОценок пока нет
- CS401 - Short Notes Chapter 15 PDFДокумент5 страницCS401 - Short Notes Chapter 15 PDFmalikОценок пока нет
- CS401 - Short Notes Chapter 15 PDFДокумент5 страницCS401 - Short Notes Chapter 15 PDFmalikОценок пока нет
- 4 - Processor FundanmentalsДокумент9 страниц4 - Processor FundanmentalsAayan AhmadОценок пока нет
- Addressing Modes in Computer OrganizationДокумент8 страницAddressing Modes in Computer OrganizationArchana R gopinathОценок пока нет
- MPL - Assignment No 6-Protected mode-LDTR GDTR IDTRДокумент8 страницMPL - Assignment No 6-Protected mode-LDTR GDTR IDTRVidya Ashok NemadeОценок пока нет
- Ethernet Flow BasicsДокумент14 страницEthernet Flow Basicssrjadhav248Оценок пока нет
- Comm 471: Digital Circuit Design Lab1Документ31 страницаComm 471: Digital Circuit Design Lab1Mina AdelОценок пока нет
- 8086 Microprocessor Programming & Instruction Sets:: Immediate AddressingДокумент8 страниц8086 Microprocessor Programming & Instruction Sets:: Immediate AddressingbiniamОценок пока нет
- Lab 2Документ59 страницLab 2J JAYDONОценок пока нет
- COA Unit 1 Lecture 4Документ35 страницCOA Unit 1 Lecture 4Pratibha SОценок пока нет
- Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and ObfuscationОт EverandPractical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and ObfuscationОценок пока нет
- Lecture # 43Документ6 страницLecture # 43api-3812413Оценок пока нет
- Lecture # 41: System Programming Course Code: CS609 Cs609@vu - Edu.pkДокумент7 страницLecture # 41: System Programming Course Code: CS609 Cs609@vu - Edu.pkapi-3812413Оценок пока нет
- Lecture # 38: System Programming Course Code: CS609 Cs609@vu - Edu.pkДокумент11 страницLecture # 38: System Programming Course Code: CS609 Cs609@vu - Edu.pkapi-3812413Оценок пока нет
- Lecture # 40: Creation of A File On NTFSДокумент6 страницLecture # 40: Creation of A File On NTFSapi-3812413Оценок пока нет
- 42Документ9 страниц42api-3812413Оценок пока нет
- 45Документ7 страниц45api-3812413Оценок пока нет
- Lecture # 39: User Data User Data MFT (Mirror) MFTДокумент5 страницLecture # 39: User Data User Data MFT (Mirror) MFTapi-3812413Оценок пока нет
- Lecture # 37: Long FilenameДокумент8 страницLecture # 37: Long Filenameapi-3812413Оценок пока нет
- Lecture # 34: Another Example With FAT16 Bit SystemДокумент6 страницLecture # 34: Another Example With FAT16 Bit Systemapi-3812413Оценок пока нет
- Lecture # 33Документ6 страницLecture # 33api-3812413Оценок пока нет
- Lecture # 36: System Programming Course Code: CS609 Cs609@vu - Edu.pkДокумент10 страницLecture # 36: System Programming Course Code: CS609 Cs609@vu - Edu.pkapi-3812413Оценок пока нет
- 32Документ8 страниц32api-3812413Оценок пока нет
- 35Документ7 страниц35api-3812413Оценок пока нет
- 30Документ9 страниц30api-3812413Оценок пока нет
- 24Документ7 страниц24api-3812413Оценок пока нет
- Lecture # 31: Inside A Boot BlockДокумент5 страницLecture # 31: Inside A Boot Blockapi-3812413Оценок пока нет
- Lecture # 28: Extended PartitionsДокумент6 страницLecture # 28: Extended Partitionsapi-3812413Оценок пока нет
- 27Документ8 страниц27api-3812413Оценок пока нет
- Lecture # 21Документ9 страницLecture # 21api-3812413Оценок пока нет
- 29Документ7 страниц29api-3812413Оценок пока нет
- 26Документ9 страниц26api-3812413Оценок пока нет
- Lecture # 23: DMA CascadingДокумент5 страницLecture # 23: DMA Cascadingapi-3812413Оценок пока нет
- Lecture # 25: Char ST (2048) "Hello U Whats Up?/0"Документ9 страницLecture # 25: Char ST (2048) "Hello U Whats Up?/0"api-3812413Оценок пока нет
- 22Документ6 страниц22api-3812413Оценок пока нет
- Lecture # 18: Status Register BДокумент9 страницLecture # 18: Status Register Bapi-3812413Оценок пока нет
- 17Документ13 страниц17api-3812413Оценок пока нет
- Lecture # 19: System Programming Course Code: CS609 Cs609@vu - Edu.pkДокумент9 страницLecture # 19: System Programming Course Code: CS609 Cs609@vu - Edu.pkapi-3812413100% (1)
- Lecture # 20Документ6 страницLecture # 20api-3812413Оценок пока нет
- Lecture # 16: ExampleДокумент9 страницLecture # 16: Exampleapi-3812413Оценок пока нет
- Provision of Ramp With Shed (See Blow-Up Detail)Документ1 страницаProvision of Ramp With Shed (See Blow-Up Detail)Adrian PachecoОценок пока нет
- Group Policy Adobe Acrobat Reader - Spiceworks PDFДокумент5 страницGroup Policy Adobe Acrobat Reader - Spiceworks PDFEmilio MartinezОценок пока нет
- The Leading Productivity App Is Now Available For Apple Iphone and Ipad!Документ3 страницыThe Leading Productivity App Is Now Available For Apple Iphone and Ipad!Abdullah Khairul AfnanОценок пока нет
- Explanation of One Way and Two Way Slab ActionДокумент17 страницExplanation of One Way and Two Way Slab Actionxckwzr100% (4)
- Hormann Gate OperatorsДокумент24 страницыHormann Gate OperatorsMihai-Catalin GoguОценок пока нет
- Wave BrochureДокумент120 страницWave BrochureRahil Tasawar60% (5)
- Load Propelling Trolley Design ReportДокумент45 страницLoad Propelling Trolley Design Reporthafizheykal0% (1)
- Normas de Referencia - Fibra de VidroДокумент12 страницNormas de Referencia - Fibra de Vidroricardobor100% (1)
- MyVGL30 System Requirements enДокумент10 страницMyVGL30 System Requirements enedgartepe4324Оценок пока нет
- Sab4323 Ocw Topic 2Документ39 страницSab4323 Ocw Topic 2Eduardo Millas100% (1)
- Tips For Successful Citrus Grafting PDFДокумент11 страницTips For Successful Citrus Grafting PDFiban0% (1)
- Networking ReportДокумент25 страницNetworking ReportyogeshОценок пока нет
- Boysen EstimatesДокумент36 страницBoysen Estimatesdasmin anne depacaquiboОценок пока нет
- Automating Manufacturing Systems Presentation Rev 4Документ89 страницAutomating Manufacturing Systems Presentation Rev 4tarekamininfoОценок пока нет
- TerrariumsДокумент29 страницTerrariumsAmruta Patil25% (4)
- Industrial Automation AcronymsДокумент3 страницыIndustrial Automation AcronymsPlatin1976Оценок пока нет
- Case StudiesДокумент7 страницCase Studiesnikhita0412100% (1)
- Background To The General Method of Shear DesignДокумент14 страницBackground To The General Method of Shear Designyyanan1118Оценок пока нет
- New River Trail SouthДокумент2 страницыNew River Trail SouthDavid OsborneОценок пока нет
- Bob Smeets Network Virtualisation and Cloud OrchestrationДокумент11 страницBob Smeets Network Virtualisation and Cloud OrchestrationAndrea StefanelliОценок пока нет
- Analysis of The FLUTE Data Carousel PaperДокумент4 страницыAnalysis of The FLUTE Data Carousel PaperShifaiz MohamedОценок пока нет
- Network Security and CryptographyДокумент11 страницNetwork Security and CryptographyRajesh Kumar JoshОценок пока нет
- Basic Concepts and Computer EvolutionДокумент56 страницBasic Concepts and Computer EvolutionDaWheng VargasОценок пока нет
- AnuragДокумент2 страницыAnuragGaurav SachanОценок пока нет
- Granular PilesДокумент16 страницGranular Pilessgaluf5Оценок пока нет
- Archivematica: Using Micro-Services and Open-Source Software To Deliver A Comprehensive Digital Curation SolutionДокумент5 страницArchivematica: Using Micro-Services and Open-Source Software To Deliver A Comprehensive Digital Curation SolutiondejanbogОценок пока нет
- DDR ChecklistДокумент27 страницDDR Checklistluvrasmi0% (2)
- Vicidial Multi-Server Manual by Poundteam v1 1Документ25 страницVicidial Multi-Server Manual by Poundteam v1 1Elyin Martinez0% (1)
- Wso2 Whitepaper Enterprise Integration Patterns With Wso2 Esb PDFДокумент206 страницWso2 Whitepaper Enterprise Integration Patterns With Wso2 Esb PDFMrProkeskaОценок пока нет