Академический Документы
Профессиональный Документы
Культура Документы
Isaca CISA: Exam Name: Isaca CISA Q & A: 240 Q&As
Загружено:
Hareesh KarakkalИсходное описание:
Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Isaca CISA: Exam Name: Isaca CISA Q & A: 240 Q&As
Загружено:
Hareesh KarakkalАвторское право:
Доступные форматы
Isaca CISA Braindumps Exams -TestSoon
Isaca CISA
Exam Name: Isaca CISA Q & A : 240 Q&As
Pdf Demo
Quality and Value for the CISA Exam
TestSoon Practice Exams for Isaca Isaca Certification CISA are written to the highest standards of technical accuracy, using only certified subject matter experts and published authors for development.
100% Guarantee to Pass Your CISA Exam
If you do not pass the Isaca Certification CISA exam on your first attempt using our TestSoon testing engine, we will give you a FULL REFUND of your purchasing fee.
Downloadable, InteractiveCISA Testing engines and PDF Version
Our Isaca Certification Exam Preparation Material provides you everything you will need to take a Isaca Certification certification n examination. Details are researched and produced by Isaca Certification Experts who are constantly using industry experience to produce precise, and logical. Free CISA Exams
Exam : Isaca CISA Title : CISA Certified Information Systems Auditor
1. Structured programming is BEST described as a technique that: A. provides knowledge of program functions to other programmers via peer reviews. B. reduces the maintenance time of programs by the use of small-scale program modules. C. makes the readable coding reflect as closely as possible the dynamic execution of the program. D. controls the coding and testing of the high-level functions of the program in the development process. Answer: B 2. Which of the following is a dynamic analysis tool for the purpose of testing software modules? A. Blackbox test
B. Desk checking C. Structured walk-through D. Design and code Answer: A 3. An offsite information processing facility having electrical wiring, air conditioning and flooring, but no computer or communications equipment is a: A. cold site. B. warm site. C. dial-up site. D. duplicate processing facility. Answer: A 4. Which of the following would be the BEST method for ensuring that critical fields in a master record have been updated properly? A. Field checks B. Control totals C. Reasonableness checks D. A before-and-after maintenance report Answer: D 5. Which of the following is MOST likely to result from a business process reengineering (BPR) project? A. An increased number of people using technology B. Significant cost savings, through a reduction in the complexity of information technology C. A weaker organizational structures and less accountability D. Increased information protection (IP) risk will increase Answer: A 6. Which of the following devices extends the network and has the capacity to store frames and act as a storage and forward device? A. Router B. Bridge C. Repeater D. Gateway Answer: B 7. Which of the following data validation edits is effective in detecting transposition and transcription errors? A. Range check B. Check digit C. Validity check D. Duplicate check Answer: B 8. IS management has decided to rewrite a legacy customer relations system using fourth generation languages (4GLs). Which of the following risks is MOST often associated with system development using 4GLs? A. Inadequate screen/report design facilities B. Complex programming language subsets C. Lack of portability across operating systems D. Inability to perform data intensive operations Answer: D 9. A call-back system requires that a user with an id and password call a remote server through a dial-up line, then the server disconnects and: A. dials back to the user machine based on the user id and password using a telephone number from its database. B. dials back to the user machine based on the user id and password using a telephone number provided by the user during this connection. C. waits for a redial back from the user machine for reconfirmation and then verifies the user id and password using its database. D. waits for a redial back from the user machine for reconfirmation and then verifies the user id and password using the sender's database. Answer: A 10. Which of the following is a benefit of using callback devices? A. Provide an audit trail B. Can be used in a switchboard environment C. Permit unlimited user mobility
D. Allow call forwarding Answer: A More CISA Braindumps Information
Related CISA Exams
CISA
Other Isaca Exams
CISA
Вам также может понравиться
- Soal Dan Jawaban Quiz CISA (Trial)Документ8 страницSoal Dan Jawaban Quiz CISA (Trial)Audrie ClarissaОценок пока нет
- CISA Chapter 3 - Questions OnlyДокумент9 страницCISA Chapter 3 - Questions OnlyJoeFSabaterОценок пока нет
- 05.2 - 2020 - CISA-50Q - Additional - Questions - v1Документ8 страниц05.2 - 2020 - CISA-50Q - Additional - Questions - v1ckuestersОценок пока нет
- CISA Exam Prep - Practice Exam Questions PDFДокумент36 страницCISA Exam Prep - Practice Exam Questions PDFHendro Try Widianto50% (2)
- Actualtests: Topping Certification Exam Prep, Test Dumps Materials - ActualtestsitДокумент8 страницActualtests: Topping Certification Exam Prep, Test Dumps Materials - ActualtestsitFaim HasanОценок пока нет
- Select The Correct AnswerДокумент25 страницSelect The Correct Answershehzaib tariq100% (1)
- CISA Practice Questions IT GovernanceДокумент4 страницыCISA Practice Questions IT GovernanceJoeFSabaterОценок пока нет
- CISA Exam PreparationДокумент6 страницCISA Exam PreparationrushicОценок пока нет
- Chapter 3 - Problems With AnswersДокумент31 страницаChapter 3 - Problems With AnswersJoeFSabater100% (1)
- Test Questions - Com Test QuestionsДокумент3 страницыTest Questions - Com Test QuestionsAO ENERGYINFORM ASTANAОценок пока нет
- CISA Domain 2 QuestionsДокумент14 страницCISA Domain 2 QuestionseliОценок пока нет
- CISA 30 QuestionsДокумент6 страницCISA 30 QuestionsajitОценок пока нет
- Certified Information Systems Auditor CISA Exam Simulator Software 2400 QuestionsДокумент6 страницCertified Information Systems Auditor CISA Exam Simulator Software 2400 Questionsng_gillian123Оценок пока нет
- CISA Exam Dates 2022 2023 and Other Information PDFДокумент9 страницCISA Exam Dates 2022 2023 and Other Information PDFMohammed AhmedОценок пока нет
- CISA-mock Test - Domain 2 (100 Questions)Документ45 страницCISA-mock Test - Domain 2 (100 Questions)Sweeto SaniОценок пока нет
- Cisa 1 10% The Is Audit Process 82 Q OnlyДокумент16 страницCisa 1 10% The Is Audit Process 82 Q Onlypgupta101Оценок пока нет
- Test 6Документ113 страницTest 6Krishna TОценок пока нет
- Syllabus CISAДокумент9 страницSyllabus CISAPRATEEKОценок пока нет
- How Does A Disaster Recovery (DR) Plan Work?Документ12 страницHow Does A Disaster Recovery (DR) Plan Work?tricia quilangОценок пока нет
- CISA - Domain 1 - The Process of Auditing Information SystemsДокумент3 страницыCISA - Domain 1 - The Process of Auditing Information Systemsabhilasha_yadav_10% (1)
- CISA - Practice.questions.2009.2a It GovernanceДокумент27 страницCISA - Practice.questions.2009.2a It Governancemgdawodu50% (2)
- 02 CISA Training Notes Is Audit Process P12Документ9 страниц02 CISA Training Notes Is Audit Process P12cameo001Оценок пока нет
- CISA QuestionsДокумент4 страницыCISA QuestionsMd Kamrul Hassan KhanОценок пока нет
- CISA-Item-Development-Guide Bro Eng 0219 PDFДокумент15 страницCISA-Item-Development-Guide Bro Eng 0219 PDFnaushad73Оценок пока нет
- Continuing Professional Education (CPE) Policy: Updated: 2014 JanuaryДокумент10 страницContinuing Professional Education (CPE) Policy: Updated: 2014 JanuarydfsfdsfОценок пока нет
- Test 1Документ121 страницаTest 1JeejuОценок пока нет
- CISA-mock Test - Domain 4 (100 Questions) : What Is Recovery Time Objective (RTO) ?Документ46 страницCISA-mock Test - Domain 4 (100 Questions) : What Is Recovery Time Objective (RTO) ?Sweeto Sani0% (1)
- Certified Information Systems Auditor (CISA) - Mock Exam 3Документ8 страницCertified Information Systems Auditor (CISA) - Mock Exam 3Nishant KulshresthaОценок пока нет
- CISA FAQs AdДокумент12 страницCISA FAQs AdBK MathivananОценок пока нет
- Production Control Group Copy The Source Program To Production LibrariesДокумент7 страницProduction Control Group Copy The Source Program To Production LibrariesrushicОценок пока нет
- Cisa Exam Prep Domain 1 2019Документ76 страницCisa Exam Prep Domain 1 2019Joel Isabirye100% (1)
- SkillFront Certification ExaminationДокумент9 страницSkillFront Certification Examinationrangel24Оценок пока нет
- RIPEMDДокумент26 страницRIPEMDEswin Angel100% (1)
- Cism 2020 Cat 1Документ15 страницCism 2020 Cat 1Benjamin_nziboОценок пока нет
- Application of CISM PDFДокумент10 страницApplication of CISM PDFedwardscpeОценок пока нет
- CISA Simulation-5Документ22 страницыCISA Simulation-5shehzaib tariqОценок пока нет
- CIA Practice QuestionsДокумент11 страницCIA Practice QuestionsAlex StoianОценок пока нет
- Auditing Business Continuity PlanДокумент2 страницыAuditing Business Continuity PlanRAJESH UPADHYAYОценок пока нет
- CISA QAESupp2014Документ2 страницыCISA QAESupp2014bharatmoghe100% (1)
- CISAДокумент82 страницыCISAMd.Mongul rayhan0% (1)
- CISA Question Bank-1Документ15 страницCISA Question Bank-1adityaОценок пока нет
- CISA Exam 100 Practice QuestionДокумент22 страницыCISA Exam 100 Practice Questionharsh100% (1)
- QuestionДокумент80 страницQuestionRodalie Vale CruzОценок пока нет
- IT AuditДокумент9 страницIT AuditxjammerОценок пока нет
- ECCouncil Pass4sureexam 312-50 v2019-02-16 by Donna 335qДокумент153 страницыECCouncil Pass4sureexam 312-50 v2019-02-16 by Donna 335qEphrem AlemuОценок пока нет
- DISA 3.0 Mod1 Day 1 Quiz 1Документ3 страницыDISA 3.0 Mod1 Day 1 Quiz 1Jackson Abraham ThekkekaraОценок пока нет
- COBIT 5 Foundation-Sample Paper - Answer KeyДокумент2 страницыCOBIT 5 Foundation-Sample Paper - Answer KeyFardan Ahmed ButtОценок пока нет
- IIA - Selftestengine.iia CFSA.v2015!03!19.by - Dayton.490qДокумент202 страницыIIA - Selftestengine.iia CFSA.v2015!03!19.by - Dayton.490qRahib JaskaniОценок пока нет
- It ExamДокумент258 страницIt ExamNitinОценок пока нет
- Section 4: System Infrastructure and ControlДокумент72 страницыSection 4: System Infrastructure and ControlAbdullah AlrimawiОценок пока нет
- 9781604204018-Questions - Answers - Explanations-by-Domain - 1 PDFДокумент17 страниц9781604204018-Questions - Answers - Explanations-by-Domain - 1 PDFEnvisage12390% (10)
- CISA - Domain 3 - IS Acquisition, Development and ImplementationДокумент153 страницыCISA - Domain 3 - IS Acquisition, Development and ImplementationPremdeepakHulagbali100% (2)
- ISACA Code of Professional EthicsДокумент1 страницаISACA Code of Professional EthicsEdmart Manila FajardoОценок пока нет
- Auditing Rpa SystemДокумент40 страницAuditing Rpa SystemPalak AggarwalОценок пока нет
- Cisa 100 PracticequestionДокумент102 страницыCisa 100 PracticequestionNerma NermaОценок пока нет
- CRISC BrochureДокумент2 страницыCRISC Brochuremankrish6314Оценок пока нет
- Bluetooth Based Home AutomationДокумент17 страницBluetooth Based Home AutomationShruthiNayerОценок пока нет
- STK673-010 3-Phase Stepping Motor Driver (Sine Wave Drive) Output Current 2.4AДокумент16 страницSTK673-010 3-Phase Stepping Motor Driver (Sine Wave Drive) Output Current 2.4AMzsenna Opcional MzsennaОценок пока нет
- TV TheoryДокумент33 страницыTV TheoryKrithika VenkatanathОценок пока нет
- PDS - II Lecture NotesДокумент303 страницыPDS - II Lecture NotesVinitha.s SaravananОценок пока нет
- Where Is Linux Being UsedДокумент2 страницыWhere Is Linux Being UsedFrancis Angel LuceroОценок пока нет
- Epicor10 MigrationGuide SQL 100700 PDFДокумент115 страницEpicor10 MigrationGuide SQL 100700 PDFVictor MotoliniaОценок пока нет
- Beyond UVM Registers Better, Faster, Smarter: Rich Edelman, Bhushan Safi Mentor Graphics, US, IndiaДокумент17 страницBeyond UVM Registers Better, Faster, Smarter: Rich Edelman, Bhushan Safi Mentor Graphics, US, Indiapinakin4uОценок пока нет
- Dell Vostro 34603560Документ8 страницDell Vostro 34603560Dương Tấn QuốcОценок пока нет
- Changong 860-Alz-M713w-F Power Supply For LCD Monitors With Bit3193 Inverter Lien Chang Ai-0088 Board (ET)Документ1 страницаChangong 860-Alz-M713w-F Power Supply For LCD Monitors With Bit3193 Inverter Lien Chang Ai-0088 Board (ET)Cristina NistorОценок пока нет
- An6668 PDFДокумент18 страницAn6668 PDFCarlos OtzoyОценок пока нет
- LB# 820-1372 - 051-6278 - A000.schematicДокумент44 страницыLB# 820-1372 - 051-6278 - A000.schematicLuis SanchezОценок пока нет
- Ieee802 Hetnet TutorialДокумент75 страницIeee802 Hetnet TutorialPayal PriyaОценок пока нет
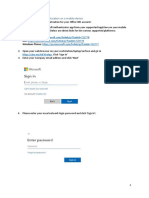
- Office 365 Multi Factor Authentication Setup GuideДокумент7 страницOffice 365 Multi Factor Authentication Setup Guideit cleancoОценок пока нет
- Oracle DB Se2 Brief 2680836Документ4 страницыOracle DB Se2 Brief 2680836Ankur GuptaОценок пока нет
- Computer GensДокумент4 страницыComputer Genssiva_aelОценок пока нет
- 03 - Exceptional HandlingДокумент41 страница03 - Exceptional HandlingRahulОценок пока нет
- Lab 5 Long RepotДокумент24 страницыLab 5 Long RepotAzie BasirОценок пока нет
- FILE 20210113 151059 Vdocuments - Site 01-Ua5000-Technical-Manual PDFДокумент107 страницFILE 20210113 151059 Vdocuments - Site 01-Ua5000-Technical-Manual PDFThanh LeОценок пока нет
- Genius Publications ListДокумент5 страницGenius Publications ListArun Trichal25% (4)
- 5620 SAM Part Number ListingДокумент109 страниц5620 SAM Part Number ListingSa VahidiОценок пока нет
- ODA E85592Документ278 страницODA E85592Mohamed SamiОценок пока нет
- Simple Network Management Protocol: by - Suparna SriДокумент64 страницыSimple Network Management Protocol: by - Suparna SriMayank GoyalОценок пока нет
- Lab No.3 CCNДокумент2 страницыLab No.3 CCNMaham AkramОценок пока нет
- Azure DevOps Explained Get Started With Azure DevOps and Develop Your DevOps PracticesДокумент497 страницAzure DevOps Explained Get Started With Azure DevOps and Develop Your DevOps Practicesvishal jain100% (1)
- Blamberger Ti ProjectДокумент47 страницBlamberger Ti ProjectsangdewaОценок пока нет
- 1 - Computer Basics Final ExamДокумент9 страниц1 - Computer Basics Final ExamArup SurОценок пока нет
- Features General Description: High Performance Single Synchronous Buck Converter GS7317Документ1 страницаFeatures General Description: High Performance Single Synchronous Buck Converter GS7317Imma Real Pcy50% (2)
- SO65790Документ5 страницSO65790Julius NkrumahОценок пока нет
- Mazak Fusion 640 Series How To Create A Backup Using RS232Документ5 страницMazak Fusion 640 Series How To Create A Backup Using RS232sunhuynh100% (2)
- Active Front EndДокумент5 страницActive Front EndDaleel LillaОценок пока нет
- The Dark Net: Inside the Digital UnderworldОт EverandThe Dark Net: Inside the Digital UnderworldРейтинг: 3.5 из 5 звезд3.5/5 (104)
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityОт EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityРейтинг: 5 из 5 звезд5/5 (1)
- The Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellОт EverandThe Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellРейтинг: 5 из 5 звезд5/5 (6)
- How to Do Nothing: Resisting the Attention EconomyОт EverandHow to Do Nothing: Resisting the Attention EconomyРейтинг: 4 из 5 звезд4/5 (421)
- More Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingОт EverandMore Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingРейтинг: 3.5 из 5 звезд3.5/5 (23)
- The Wires of War: Technology and the Global Struggle for PowerОт EverandThe Wires of War: Technology and the Global Struggle for PowerРейтинг: 4 из 5 звезд4/5 (34)
- The Internet Con: How to Seize the Means of ComputationОт EverandThe Internet Con: How to Seize the Means of ComputationРейтинг: 5 из 5 звезд5/5 (6)
- Branding: What You Need to Know About Building a Personal Brand and Growing Your Small Business Using Social Media Marketing and Offline Guerrilla TacticsОт EverandBranding: What You Need to Know About Building a Personal Brand and Growing Your Small Business Using Social Media Marketing and Offline Guerrilla TacticsРейтинг: 5 из 5 звезд5/5 (32)
- React.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)От EverandReact.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)Оценок пока нет
- So You Want to Start a Podcast: Finding Your Voice, Telling Your Story, and Building a Community That Will ListenОт EverandSo You Want to Start a Podcast: Finding Your Voice, Telling Your Story, and Building a Community That Will ListenРейтинг: 3.5 из 5 звезд3.5/5 (24)
- Grokking Algorithms: An illustrated guide for programmers and other curious peopleОт EverandGrokking Algorithms: An illustrated guide for programmers and other curious peopleРейтинг: 4 из 5 звезд4/5 (16)
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTОт EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTОценок пока нет
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsОт EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsРейтинг: 5 из 5 звезд5/5 (1)
- An Internet in Your Head: A New Paradigm for How the Brain WorksОт EverandAn Internet in Your Head: A New Paradigm for How the Brain WorksОценок пока нет
- Python for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldОт EverandPython for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldОценок пока нет
- How to Start a Blog with WordPress: Beginner's Guide to Make Money by Writing OnlineОт EverandHow to Start a Blog with WordPress: Beginner's Guide to Make Money by Writing OnlineРейтинг: 3.5 из 5 звезд3.5/5 (2)
- Web Copy That Sells: The Revolutionary Formula for Creating Killer Copy That Grabs Their Attention and Compels Them to BuyОт EverandWeb Copy That Sells: The Revolutionary Formula for Creating Killer Copy That Grabs Their Attention and Compels Them to BuyРейтинг: 4 из 5 звезд4/5 (13)
- Articulating Design Decisions: Communicate with Stakeholders, Keep Your Sanity, and Deliver the Best User ExperienceОт EverandArticulating Design Decisions: Communicate with Stakeholders, Keep Your Sanity, and Deliver the Best User ExperienceРейтинг: 4 из 5 звезд4/5 (19)
- HTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)От EverandHTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)Оценок пока нет
- Kill All Normies: Online Culture Wars From 4Chan And Tumblr To Trump And The Alt-RightОт EverandKill All Normies: Online Culture Wars From 4Chan And Tumblr To Trump And The Alt-RightРейтинг: 3.5 из 5 звезд3.5/5 (240)