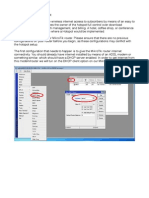
Академический Документы
Профессиональный Документы
Культура Документы
VPN: The Pros and Cons: What Is A VPN?
Загружено:
Hassan MohamedИсходное описание:
Оригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
VPN: The Pros and Cons: What Is A VPN?
Загружено:
Hassan MohamedАвторское право:
Доступные форматы
1.
VPN: The Pros and Cons
The Virtual Private Network - VPN - has attracted the attention of many organizations looking to both expand their networking capabilities and reduce their costs. What is a VPN? A VPN (Virtual Private Network) enables a specific group of users to access private network data and resources securely over the Internet or other networks. Although often using public networks, a VPN inherits the characteristics of a private network, hence the acronym of "Virtual" Private Network. It's the concurrent use of tunneling, encryption, authentication, and access control over a public network that basically characterizes a VPN. What is a VPN made of? VPNs may connect an individual machine and a private network (client-to-server) or a remote LAN (Local Area Network) and a private network (server-to-server). To do so VPNs need: a routed network (to transport data packets), optionally a tunnel switch (to increase security and versatility) , and tunnel terminators (acting like virtual cable terminators). How do VPNs work? VPNs create "virtual" point-to-point connections using a technique called 'tunneling'. As the name suggests, tunneling acts like a 'pipe' which bores through a network cloud to connect two points. Typically started by a remote user, the tunneling process encapsulates data and encrypts it into standard TCP/IP packets, which can then safely travel across the Internet. What types of VPN exist? One must bear in mind that the VPN market has tremendously expanded these last years. As it evolves the lines between various classifications and architectures blur out. Hardware manufacturers now provide software clients that offer features historically available only through software or firewallbased solutions, while stand-alone applications on the other hand may support encrypting routers to improve performance. Emerging standards such as IPsec provide a standard to create custom solutions. From a broad standpoint, one can identify three basic types of VPN: Intranet VPN: this type of VPN is "client transparent". It is usually implemented for networks within a common network infrastructure but across various physical locations. For instance several buildings may be connected to a data center, or a common mainframe application that they can access securely through private lines. Those VPNs need to be especially secure with strong encryption and meet strict performance and bandwidth requirements. They must remain easily upgradeable since many users may be added to the load down the road (additional locations or applications).
Remote Access VPN : here VPN is "client initiated". It is intended for remote users that need to connect to their corporate LAN from various point of connections. It is intended for salesmen equipped with laptops and telecommuters that will connect intermittently from vary diverse locations (homes, hotels, conference halls...). The key factor here is flexibility as performance and bandwidth are usually minimal and less of an issue. More than encryption, authentication will be the main security concern. Extranet VPN : in this case VPN uses the Internet as main backbone. It usually addresses a wider scale of users and locations, enabling customers, suppliers and branch offices to access corporate resources across various network architectures. They rely on VPN standards such as IPsec to ensure maximum compatibility while trying not to overly compromise security.
What Exactly Is A VPN? A VPN supplies network connectivity over a possibly long physical distance. In this respect, a VPN is a form of Wide Area Network (WAN). Pros:: 1. Cost Savings - By leveraging third party networks, with VPN, organizations no longer have to use expensive leased or frame relay lines and are able to connect remote users to their corporate networks via a local Internet service provider (ISP) instead of via expensive 800-numberor long distance calls to resource-consuming modem banks. 2.Security - VPNs provide the highest level of security using advanced encryption and authentication protocols that protect data from unauthorized access. 3.Scalability - VPNs allow corporations to utilize remote access infrastructure within ISPs. Therefore, corporations are able to add a virtually unlimited amount of capacity without adding significant infrastructure. 4.Compatibility with Broadband Technology - VPNs allow mobile workers, telecommuters and day extenders to take advantage of high-speed, broadband connectivity, such as DSL and Cable, when gaining access to their corporate networks, providing workers significant flexibility and efficiency. 5.VPNs enble you to create secure, business-critical communication links over the Internet.
6. Give telecommuters and mobile workers secure access to your LAN 7. Share resources with partners Limitations of a VPN Despite their popularity, VPNs are not perfect and limitations exist as is true for any technology. Organizations should consider issues like the below when deploying and using virtual private networks in their operations: 1. VPNs require detailed understanding of network security issues and careful installation / configuration to ensure sufficient protection on a public network like the Internet. 2. The reliability and performance of an Internet-based VPN is not under an organization's direct control. Instead, the solution relies on an ISP and their quality of service. 3. Historically, VPN products and solutions from different vendors have not always been compatible due to issues with VPN technology standards. Attempting to mix and match equipment may cause technical problems, and using equipment from one provider may not give as great a cost savings.
2. What are some of the pros and cons of the three general network topologies (bus, ring, and star)?
Ring Topology A ring topology is like a circle of computers connected together. Each
computer has a network card and the cable from computer 1 connects to computer 2 and so on until you connect back to computer 1. This creates the ring. Less expensive network because you dont need a switch or router. However not very flexible because you can only get to nodes on the ring. Unless one of the nodes was a router which would then connect you to another ring or topology. A ring topology is mostly used in a token ring environment. IBM developed token ring. Token Rings popularity has dwindled to a very low percentage of topologies used in todays market.
Pros
1. Very orderly network where every device has access to the token and the opportunity to transmit. 2. Performs better than a star topology under heavy network load. Can create much larger network using Token Ring. 3. Does not require network server to manage the connectivity between the computers.
Cons
1. One malfunctioning workstation or bad port in the MAU can create problems for the entire network 2. Moves, adds and changes of devices can affect the network 3. Network adapter cards and MAU's are much more expensive than Ethernet cards and hubs
4. Much slower than an Ethernet network under normal load
Bus Topology - A bus topology is a network of computers connected in a straight line or
cable with a termination connector at both ends. These computers all share the same communications path called a bus. Again not as pricy because you dont need a router or switch to build a bus topology network. You can have 10 or so PCs connected in one long line of cable with a printer or a server somewhere in the bus. You would need a router or layer 3 switch to get outside of the bus topology.
Pros
1. Easy to implement and extend 2.Requires less cable length than a star topology 3. Well suited for temporary or small networks not requiring high speeds(quick setup) 4. Cheaper than other topologies
Cons
1. Limited cable length and number of stations. 2. If there is a problem with the cable, the entire network goes down. Maintenance costs may be higher in the long run. 3. Performance degrades as additional computers are added or on heavy traffic. Proper termination is required (loop must be in closed path). 4. Significant Capacitive Load (each bus transaction must be able to stretch to most distant link). 5. It works best with limited number of nodes. 6. It is slower than the other topologies.
Star Topology
A star topology is like a hub and spoke layout. The star topology is the most widely used and recognized topology in todays market place. A Star Topology is more expensive because a router, switch, or hub is required to route the network across to all nodes on the hub and spoke technology. The switch or hub is used to connect clients (computers), printers, servers etc. The router is used to connect more than one hub and spoke network together. In addition, the router can do things like DHCP giving out dynamic IP addresses and routing the clients to the Internet if connected to an Internet Service Provider (ISP).
Pros
1. Performance: Data packets do not travel through any unnecessary nodes. Communication between any two devices on the network involves at most three devices and two links. The isolation of traffic between nodes means that heavy utilization from one device is invisible to other devices on the network, provided that the central hub retains adequate capacity. 2. Isolation: Each device is isolated on its own link. This makes it easy to isolate individual devices from the network by disconnecting them from the hub. Any non-centralized failure will have very little effect on the network.
3. Centralization: The network can easily be scaled or expanded by adding to the capacity of the hub node, or by adding additional devices to the star. The fact that all traffic passes through the central hub means that the hub can easily be used to inspect or control traffic through the network. 4. Simplicity: The topology is easy to understand, establish, and navigate. Complex routing or message passing protocols is generally unnecessary. Individual nodes can easily be added or removed, and fault detection is simplified, as each link/device can be probed individually.
Cons
The primary disadvantage of a star topology is the high dependence of the system on the functioning of the central hub. While the failure of an individual link only results in the isolation of a single node, the failure of the central hub renders the network inoperable, immediately isolating all nodes. The performance and scalability of the network also depend on the capabilities of the hub. The number of connections that can be made to the hub or switch limits network size, and performance for the entire network is capped by its throughput. While in theory traffic between the hub and a node is isolated from other nodes on the network, other nodes may see a performance drop if traffic to another node occupies a significant portion of the central node's processing capability or throughput.
3.VLANs
What is a VLAN?
As I said, a VLAN is a virtual LAN. In technical terms, a VLAN is a broadcast domain created by switches. Normally, it is a router creating that broadcast domain. With VLANs, a switch can create the broadcast domain.
Are VLANs required?
It is important to point out that you dont have to configure a VLAN until your network gets so large and has so much traffic that you need one. Many times, people are simply using VLANs because the network they are working on was already using them.
When do I need a VLAN?
You need to consider using VLANs in any of the following situations:
You have more than 200 devices on your LAN You have a lot of broadcast traffic on your LAN Groups of users need more security or are being slowed down by too many broadcasts? Groups of users need to be on the same broadcast domain because they are running the same applications. An example would be a company that has VoIP phones. The users using the phone could be on a different VLAN, not with the regular users. Or, just to make a single switch into multiple virtual switches.
As networks have grown in size and complexity, many companies have turned to virtual local area networks (VLANs) to provide some way of structuring this growth logically. Basically, a VLAN is a collection of nodes that are grouped to gather in a single broadcast domain that is based on something other than physical location. You learned about broadcasts earlier, and how a router does not pass along broadcasts. A broadcast domain is a network (or portion of a network) that will receive a broadcast packet from any node located within that network. In a typical network, everything on the same side of the router is all part of the same broadcast domain. A switch that you have implemented VLANs on has multiple broadcast domains, similar to a router. But you still need a router (or Layer 3 routing engine) to route from one VLAN to another -- the switch can't do this by itself. Here are some common reasons why a company might have VLANs:
Security - Separating systems that have sensitive data from the rest of the network
decreases the chances that people will gain access to information they are not authorized to see.
Projects/Special applications - Managing a project or working with a specialized
application can be simplified by the use of a VLAN that brings all of the required nodes together.
Performance/Bandwidth - Careful monitoring of network use allows the network
administrator to create VLANs that reduce the number of router hops and increase the apparent bandwidth for network users.
Broadcasts/Traffic flow - Since a principle element of a VLAN is the fact that it does not
pass broadcast traffic to nodes that are not part of the VLAN, it automatically reduces broadcasts. Access lists provide the network administrator with a way to control who sees what network traffic. An access list is a table the network administrator creates that lists which addresses have access to that network.
Departments/Specific job types - Companies may want VLANs set up for
departments that are heavy network users (such as multimedia or engineering), or a VLAN across departments that is dedicated to specific types of employees (such as managers or sales people).
You can create a VLAN using most switches simply by logging into the switch via Telnet and entering the parameters for the VLAN (name, domain and port assignments). After you have created the VLAN, any network segments connected to the assigned ports will become part of that VLAN. While you can have more than one VLAN on a switch, they cannot communicate directly with one another on that switch. If they could, it would defeat the purpose of having a VLAN, which is to isolate a part of the network. Communication between VLANs requires the use of a router. VLANs can span multiple switches, and you can have more than one VLAN on each switch. For multiple VLANs on multiple switches to be able to communicate via a single link between the switches, you must use a process called trunking -- trunking is the technology that allows information from multiple VLANs to be carried over a single link between switches.
What do VLANs offer?
VLANs offer higher performance for medium and large LANs because they limit broadcasts. As the amount of traffic and the number of devices grow, so does the number of broadcast packets. By using VLANs you are containing broadcasts. VLANs also provide security because you are essentially putting one group of devices, in one VLAN, on their own network.
Article Summary
Here is what we have learned:
A VLAN is a broadcast domain formed by switches Administrators must create the VLANs then assign what port goes in what VLAN, manually. VLANs provide better performance for medium and large LANs. All devices, by default, are in VLAN 1. A trunk port is a special port that runs ISL or 802.1q so that it can carry traffic from more than one VLAN. For devices in different VLANs to communicate, you must use a router or Layer 3 switch. Even if you've worked on Cisco networks for a while, be sure to check out TrainSignal's
Вам также может понравиться
- Sample-Business-Plan PDFДокумент19 страницSample-Business-Plan PDFregistros14450% (6)
- VPN ProposalДокумент5 страницVPN ProposalKamran Khan100% (1)
- VPN AbstractДокумент11 страницVPN AbstractVijay KarthikОценок пока нет
- VPN-Virtual Private Networks - Full ReportДокумент26 страницVPN-Virtual Private Networks - Full ReportamarОценок пока нет
- CSE VPN ReportДокумент16 страницCSE VPN Reportlokesh repalaОценок пока нет
- NGN Assignment (Ritik Yadav-07010102818)Документ10 страницNGN Assignment (Ritik Yadav-07010102818)Anirudh KawОценок пока нет
- Virtual Private NetworksДокумент10 страницVirtual Private Networksnakovsk1Оценок пока нет
- VPN Seminar ReportДокумент22 страницыVPN Seminar ReportKumar BharadwajОценок пока нет
- Chapter 3 Network Design and VPN TechnologiesДокумент9 страницChapter 3 Network Design and VPN Technologiesمحمد محمدОценок пока нет
- Client Server Network EssayДокумент11 страницClient Server Network Essayconcep12Оценок пока нет
- NetworkingДокумент16 страницNetworkingAmit ThubeОценок пока нет
- Intranets and Virtual Private Networks (VPNS)Документ14 страницIntranets and Virtual Private Networks (VPNS)Vulpe FlorianОценок пока нет
- VPN Tutorial: An Introduction To VPN Software, VPN Hardware and ProtocolsДокумент7 страницVPN Tutorial: An Introduction To VPN Software, VPN Hardware and Protocolscoolcurrent4uОценок пока нет
- 04-Virtual Private Network - Arun T RaviДокумент6 страниц04-Virtual Private Network - Arun T RaviAnnonymous963258Оценок пока нет
- Intranet: What Exactly Is A VPN?Документ22 страницыIntranet: What Exactly Is A VPN?varunikakhareОценок пока нет
- Internet WorkingДокумент70 страницInternet Workingvarunsaiammula258Оценок пока нет
- VPN AssignmentДокумент13 страницVPN AssignmentSheanopa MunatsiОценок пока нет
- Introduction To Computer Network: DisadvantagesДокумент4 страницыIntroduction To Computer Network: DisadvantagesSaamridh SihagОценок пока нет
- 172 VPNДокумент25 страниц172 VPNbanstyle123456789Оценок пока нет
- Unit 4: Types of NetworksДокумент17 страницUnit 4: Types of NetworksSJ ShahidОценок пока нет
- Virtual Private Networks (VPNS)Документ0 страницVirtual Private Networks (VPNS)Toto CutugnoОценок пока нет
- VPNДокумент18 страницVPNVikas SoniОценок пока нет
- INTRODUCTIONДокумент7 страницINTRODUCTIONMazen NabeelОценок пока нет
- Computer NetworksДокумент38 страницComputer NetworksP PОценок пока нет
- Computer Unit 5Документ52 страницыComputer Unit 5Jayesh BoroleОценок пока нет
- Private Use of Public Networks For Enterprise Customers: 3com Technical PapersДокумент22 страницыPrivate Use of Public Networks For Enterprise Customers: 3com Technical PapersRajeev KumarОценок пока нет
- IT As Level Chapter 6Документ5 страницIT As Level Chapter 6Vex Davies BanningОценок пока нет
- Unit-1 (Part-A)Документ55 страницUnit-1 (Part-A)LEKHAОценок пока нет
- Intro. To Networking & Network DevicesДокумент33 страницыIntro. To Networking & Network DevicesAyodeleОценок пока нет
- LAN (Local Area Network) : LAN Stands For Local Area Network. It's A Group of Computers Which All Belong To TheДокумент7 страницLAN (Local Area Network) : LAN Stands For Local Area Network. It's A Group of Computers Which All Belong To TheIas Aspirant AbhiОценок пока нет
- N+ GuideДокумент15 страницN+ Guidescribdacct123Оценок пока нет
- Abstract:-Virtual Private Network: HistoryДокумент2 страницыAbstract:-Virtual Private Network: HistoryDhanjj YadavОценок пока нет
- Administer Network HardwareДокумент62 страницыAdminister Network HardwareMintesnot AdeОценок пока нет
- NetworkДокумент14 страницNetworkAmit ChaurasiaОценок пока нет
- Chapter-5-Computer 9th ClassДокумент8 страницChapter-5-Computer 9th ClassMudassar NaseemОценок пока нет
- Cse VPNДокумент19 страницCse VPNRadheshyam SinghОценок пока нет
- Ecom Unit2notesДокумент19 страницEcom Unit2notesmahaОценок пока нет
- NETWORKДокумент80 страницNETWORKMargaret PhanОценок пока нет
- LAN DocumentДокумент13 страницLAN DocumentSandeep MahajanОценок пока нет
- Virtual Private Networks (VPN)Документ38 страницVirtual Private Networks (VPN)Anuj OmarОценок пока нет
- Lesson 8 Router Switch and Access Point Hand OutДокумент24 страницыLesson 8 Router Switch and Access Point Hand OutCed RickОценок пока нет
- NRS2 Last Two PartДокумент32 страницыNRS2 Last Two PartAriful HaqueОценок пока нет
- Administrate Network and Hardware PeripheralsДокумент14 страницAdministrate Network and Hardware PeripheralsGizaw TadesseОценок пока нет
- Virtual Private Network: Project ReportДокумент80 страницVirtual Private Network: Project ReportAnirudh KvОценок пока нет
- Demystifying VPN'S: A White Paper Created by Mohit MadhokДокумент7 страницDemystifying VPN'S: A White Paper Created by Mohit Madhokkirangs029Оценок пока нет
- CompTIA Network+Документ262 страницыCompTIA Network+Abhijit SarkarОценок пока нет
- Set-Up Computer Networks Install Network Cables Learning Outcome 01: Installing Network Cables Assessment CriteriaДокумент12 страницSet-Up Computer Networks Install Network Cables Learning Outcome 01: Installing Network Cables Assessment CriteriaSheena FondavillaОценок пока нет
- CN Exp1 60004200044 PDFДокумент16 страницCN Exp1 60004200044 PDFbhavik shahОценок пока нет
- CSE VPN ReportДокумент29 страницCSE VPN ReportbelgiumОценок пока нет
- Unit 1Документ12 страницUnit 1Priyanshu KanaldekarОценок пока нет
- Administrate Net Work and Hard WarwДокумент19 страницAdministrate Net Work and Hard WarwAbdissaTadeseОценок пока нет
- Computer Networks and Management Open Book ExamДокумент6 страницComputer Networks and Management Open Book ExammukeshОценок пока нет
- Mblevins NTC242 Week 4 AssignmentДокумент4 страницыMblevins NTC242 Week 4 AssignmentmdblevinsОценок пока нет
- Intoduction of NetworkingДокумент5 страницIntoduction of NetworkingEincop Netwax LabОценок пока нет
- Unit 1Документ14 страницUnit 1Amruta ShingoteОценок пока нет
- Internet Routing and Switching EquipmentДокумент17 страницInternet Routing and Switching EquipmentKarandeep SinghОценок пока нет
- Topic-2 - Networks ICT A LEVELДокумент116 страницTopic-2 - Networks ICT A LEVELD S A DHAKA SPACE AGENCYОценок пока нет
- REMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicОт EverandREMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicРейтинг: 5 из 5 звезд5/5 (1)
- PC Hardware & Networking Syllabus PDFДокумент2 страницыPC Hardware & Networking Syllabus PDFHassan MohamedОценок пока нет
- Course Outline Hardware and Software: Curriculum ObjectivesДокумент7 страницCourse Outline Hardware and Software: Curriculum ObjectivesHassan MohamedОценок пока нет
- WHO 2017-Hepatitis B & C PDFДокумент204 страницыWHO 2017-Hepatitis B & C PDFkyuhyun oppaОценок пока нет
- Basics of Computers - Input - Output Ports - TutorialspointДокумент3 страницыBasics of Computers - Input - Output Ports - TutorialspointHassan MohamedОценок пока нет
- Windows 10 in 10 Minutes 150730165455 Lva1 App6891 PDFДокумент12 страницWindows 10 in 10 Minutes 150730165455 Lva1 App6891 PDFHassan MohamedОценок пока нет
- Itprojectpresentstion 161204104616Документ19 страницItprojectpresentstion 161204104616Hassan MohamedОценок пока нет
- Structure and Function of The Expansion BusДокумент13 страницStructure and Function of The Expansion BusHassan MohamedОценок пока нет
- A Plus Student PackageДокумент4 страницыA Plus Student PackageHassan MohamedОценок пока нет
- 59 Fabc 887808 DДокумент2 страницы59 Fabc 887808 DHassan MohamedОценок пока нет
- Overview of Network ManagementДокумент6 страницOverview of Network ManagementAhmed Alzahrani100% (1)
- EntrepreneurshipДокумент4 страницыEntrepreneurshipHassan MohamedОценок пока нет
- Chap10 DataCommunicationДокумент36 страницChap10 DataCommunicationHassan MohamedОценок пока нет
- EconimicsДокумент1 страницаEconimicsHassan MohamedОценок пока нет
- Overview of Network ManagementДокумент6 страницOverview of Network ManagementAhmed Alzahrani100% (1)
- MikroTik Hotspot TutorialДокумент16 страницMikroTik Hotspot TutorialMgciniNcubeОценок пока нет
- Overview of Network ManagementДокумент6 страницOverview of Network ManagementAhmed Alzahrani100% (1)
- 483 HamedДокумент23 страницы483 Hamedniren4u1567Оценок пока нет
- 483 HamedДокумент23 страницы483 Hamedniren4u1567Оценок пока нет
- Mba Programme Structure - AllДокумент22 страницыMba Programme Structure - AllHassan MohamedОценок пока нет
- Regression StatisticsДокумент2 страницыRegression StatisticsAntonache FlorinОценок пока нет
- 483 HamedДокумент23 страницы483 Hamedniren4u1567Оценок пока нет
- IT Security PubДокумент23 страницыIT Security PubHassan MohamedОценок пока нет
- Statement Death Somali PresidentДокумент2 страницыStatement Death Somali PresidentHassan MohamedОценок пока нет
- WP - Protecting The EnterpriseДокумент5 страницWP - Protecting The EnterpriseHassan MohamedОценок пока нет
- 727Документ23 страницы727Hassan MohamedОценок пока нет
- Agriculture Farm Business PlanДокумент37 страницAgriculture Farm Business PlanHassan MohamedОценок пока нет
- BMST5103 Assignment May 2015Документ2 страницыBMST5103 Assignment May 2015Hassan MohamedОценок пока нет
- E-Commerce Start-Up Business PlanДокумент45 страницE-Commerce Start-Up Business PlanHassan Mohamed100% (1)
- IceDreams LiveДокумент29 страницIceDreams LiveDuaa Al-HasanОценок пока нет
- MQTT - Introduction, Working, Advantages, Implementation in IoTДокумент5 страницMQTT - Introduction, Working, Advantages, Implementation in IoTTrần Việt DũngОценок пока нет
- Core Timers T305 T308 FinalДокумент14 страницCore Timers T305 T308 FinalSana UllahОценок пока нет
- Broadband Power LevelsДокумент2 страницыBroadband Power LevelsvargasОценок пока нет
- GPW Sie Mpi Mh01eaДокумент52 страницыGPW Sie Mpi Mh01eaFathi MusaОценок пока нет
- DHCP EmulationДокумент24 страницыDHCP Emulation김승유Оценок пока нет
- Cover SheetДокумент1 страницаCover SheetJoco MartinОценок пока нет
- World Fip ProtocolДокумент47 страницWorld Fip Protocolimad el-ghayouryОценок пока нет
- JohnsonДокумент38 страницJohnsonFelipe Andres Moreno BallesterosОценок пока нет
- BBU5900A Hardware Description (V100R016C00 - 02) (PDF) - enДокумент73 страницыBBU5900A Hardware Description (V100R016C00 - 02) (PDF) - enИнженер - проектировщикОценок пока нет
- LTE Handover OptimizationДокумент75 страницLTE Handover OptimizationCamilo Bazan Heredia100% (3)
- Add-On Packs/Groups Choose at Least 3 Groups: Premieres 6 August, Every Thurs, 9pmДокумент2 страницыAdd-On Packs/Groups Choose at Least 3 Groups: Premieres 6 August, Every Thurs, 9pmmaryjashly0328Оценок пока нет
- RW 2050 0100Документ3 страницыRW 2050 0100mvasquez2011Оценок пока нет
- Overview of Billing and Price Models: Open Telekom CloudДокумент14 страницOverview of Billing and Price Models: Open Telekom Cloudthe_matrix1Оценок пока нет
- Chapter 5-7Документ25 страницChapter 5-7Temesgen100% (1)
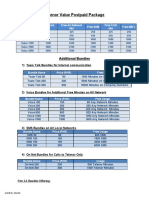
- Telenor Value Postpaid PackageДокумент3 страницыTelenor Value Postpaid PackageImeNОценок пока нет
- SWH-2009F Switch ManualДокумент12 страницSWH-2009F Switch ManualdragosGSXОценок пока нет
- m9700 Users ManualДокумент44 страницыm9700 Users ManualMed Medy FehemОценок пока нет
- Sonoff Product Catalogue 2019Документ7 страницSonoff Product Catalogue 2019Iury CaretaОценок пока нет
- Session3 IoT SharingДокумент19 страницSession3 IoT SharingRamcharanОценок пока нет
- Troubleshooting - MPLSДокумент81 страницаTroubleshooting - MPLSkmadОценок пока нет
- Sliding Window PptsДокумент26 страницSliding Window PptsNeelima SaxenaОценок пока нет
- Report On Telecom Sector in IndiaДокумент8 страницReport On Telecom Sector in IndiaSaurabh Paharia100% (2)
- Brother MFC-L2752DWДокумент8 страницBrother MFC-L2752DWbogtudorОценок пока нет
- Wireless Communications: Uniforum Chicago Bill LaturaДокумент48 страницWireless Communications: Uniforum Chicago Bill Laturaadi_risingsun100% (1)
- RC3000 Antenna Controller With An Idirect 7000 Satellite RouterДокумент7 страницRC3000 Antenna Controller With An Idirect 7000 Satellite Routermaksi1Оценок пока нет
- CISCO ASA Firewall Quick Configuration GuideДокумент24 страницыCISCO ASA Firewall Quick Configuration GuideMoïse GuilavoguiОценок пока нет
- Merger Final 1Документ18 страницMerger Final 1vgh nhytfОценок пока нет
- Wildwood Media List 9 9Документ4 страницыWildwood Media List 9 9api-254328174Оценок пока нет
- RIL and ModemДокумент2 страницыRIL and ModemRohit Pathania100% (1)