Академический Документы
Профессиональный Документы
Культура Документы
Guess Who's Reading What We Share Online by Tanya Mariano
Загружено:
thecenseireport0 оценок0% нашли этот документ полезным (0 голосов)
52 просмотров2 страницыThe U.S. government is building a $2-billion facility in Utah to spy on civilian communications
In the information age, what you share online may end up in unexpected places because of data miners and privacy and security flaws
On the bright side, privacy-protection efforts are underway and new protection tools are emerging
Full text available to subscribers only. To subscribe, please fill out the subscription form and send to report@censeisolutions.com
LIKE us at Facebook at: http://www.facebook.com/pages/The-CenSEI-Report/110668425707361
Also add our Facebook account: http://www.facebook.com/thecenseireport
Авторское право
© Attribution Non-Commercial (BY-NC)
Доступные форматы
PDF, TXT или читайте онлайн в Scribd
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документThe U.S. government is building a $2-billion facility in Utah to spy on civilian communications
In the information age, what you share online may end up in unexpected places because of data miners and privacy and security flaws
On the bright side, privacy-protection efforts are underway and new protection tools are emerging
Full text available to subscribers only. To subscribe, please fill out the subscription form and send to report@censeisolutions.com
LIKE us at Facebook at: http://www.facebook.com/pages/The-CenSEI-Report/110668425707361
Also add our Facebook account: http://www.facebook.com/thecenseireport
Авторское право:
Attribution Non-Commercial (BY-NC)
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
0 оценок0% нашли этот документ полезным (0 голосов)
52 просмотров2 страницыGuess Who's Reading What We Share Online by Tanya Mariano
Загружено:
thecenseireportThe U.S. government is building a $2-billion facility in Utah to spy on civilian communications
In the information age, what you share online may end up in unexpected places because of data miners and privacy and security flaws
On the bright side, privacy-protection efforts are underway and new protection tools are emerging
Full text available to subscribers only. To subscribe, please fill out the subscription form and send to report@censeisolutions.com
LIKE us at Facebook at: http://www.facebook.com/pages/The-CenSEI-Report/110668425707361
Also add our Facebook account: http://www.facebook.com/thecenseireport
Авторское право:
Attribution Non-Commercial (BY-NC)
Доступные форматы
Скачайте в формате PDF, TXT или читайте онлайн в Scribd
Вы находитесь на странице: 1из 2
:NKcenSEI8KVUXZ - May 14-20, 2012
The prying eyes of data miners are watching
STRATEGY POINTS
The U.S. government is building a $2-billion facility in Utah to
spy on civilian communications
In the information age, what you share online may end up in
unexpected places because of data miners and privacy and
security aws
On the bright side, privacy-protection efforts are underway and
new protection tools are emerging
S
o youve booked the air tickets online,
e-mailed the itinerary to your travel
buddies, and posted on Facebook a
photo of that quaint hotel you will call
home for the weekend. Congratulations!
It looks like youre all set for your
summer getaway.
L uIso Iooks IIke you`ve exposed yourseII
and your friends to serious security risks.
With personal data as the currency of the
digital economy, and with the posting of
information online becoming a normal
part of everyday life, what you share with
contacts on the Web, you might as well
have shared with the rest of the world.
Uncle Sam wants your data. Citizens
of the U.S. should be doubly nervous.
Web magazine Tecca reports the four
ways the federal government is spying
on its citizens, and this includes the
construction of a $2-billion data center
in Utah, to be completed in September
2013, to spy on civilian communications
encompassing mobile, e-mails, and credit-
card transactions.
The report also warns that the U.S.
governmenL muInLuIns deLuIIed hIes
on numerous public, semi-public, and
prIvuLe hgures, und empIoys soILwure
und Iurdwure Lo rIe LIrougI InIormuLIon
publicly available on social media sites,
and that the House of Representatives
is considering a bill, entitled Protecting
Children from Internet Pornographers
Act, which would require commercial
Internet service providers to create logs of
customers names, IP addresses, and
bank information.
Grabby corporations. Of course,
no discussion of data mining is complete
without mention of the two titans
of the technological world: Google
and Facebook.
Both are known to collect user data in
order to provide a more intuitive and
personuIIzed onIIne experIence (reud:
smother you with targeted ads). But just
how much do they know?
In February, Jonathan Mayer, a
graduate student at Stanford University,
blogged that he had discovered Google
bypassing the privacy settings of Apples
web browser, Safari. The three other
companies that he found to be doing
this were advertising companies Vibrant
PREVIOUS PAGE NEXT PAGE
cenSEI
: . +
8KVUXZ
CONTENTS BUSINESS NATION WORLD TECHNOLOGY
Media, Media Innovation Group, and
RollPoint.
By deIuuIL, SuIurI Is conhgured Lo bIock
third-party cookies. These four, however,
placed traceable cookies by using a special
computer code, which allowed them to spy
on peoples Internet browsing habits.
Google denied collecting personal
information through the advertising
cookIes, und expIuIned LIuL LIe prIvucy-
setting circumvention was accidental.
The code was disabled after Google was
contacted by The Wall Street Journal,
which has published a report on the matter.
In its research into Facebooks privacy
munugemenL, non-prohL consumer-
protection organization Consumer Reports
cites two Facebook users whose stories
reveal that the social network maintains
a massive repository of highly sensitive
information about their members.
TIe hrsL, Mux ScIrems, Is u zq-yeur-oId
law student from Austria who was able
Lo obLuIn u deLuIIed copy oI IIs prohIe
information 1,222 pages spanning
three years of Facebook activity from
ucebook`s oIhce In DubIIn. ScIrems wus
surprised to discover deleted messages,
wall posts, e-mail addresses, and friends
sLIII vIsIbIe In IIs hIe. AIso IncIuded In
the document were sensitive data such as
last known geographic location, including
IongILude und IuLILude, und LIe exucL duLes
and times he logged in.
The Boston police investigation into the
death of the second user mentioned in
the report, Philip Markoff, illustrates
how Facebook also knows so much about
their American users. In 2010, Markoff
committed suicide in jail while awaiting his
trial for the murder of masseuse and former
call girl Julissa Brisman, dubbed by the
media as the Craigslist Killer case.
TIe hIe ucebook reIeused Lo LIe poIIce
showed Markoffs wall posts, photos,
log-in dates and times, IP addresses, and
list of friends.
According to the same report, you
dont even have to click on the Like
button in order to be tracked: Facebook
PREVIOUS PAGE NEXT PAGE
Вам также может понравиться
- TCR NsaДокумент1 страницаTCR NsathecenseireportОценок пока нет
- Annual Report To The PeopleДокумент7 страницAnnual Report To The PeoplethecenseireportОценок пока нет
- Fixing The Fix by Zandro Rapadas, M.D.C.Документ9 страницFixing The Fix by Zandro Rapadas, M.D.C.thecenseireportОценок пока нет
- Balancing The Powers of Asia by Mr. Ricardo SaludoДокумент6 страницBalancing The Powers of Asia by Mr. Ricardo SaludothecenseireportОценок пока нет
- How Blue Is Your Ocean?Документ5 страницHow Blue Is Your Ocean?thecenseireportОценок пока нет
- Two Years of "Aquinomics"Документ9 страницTwo Years of "Aquinomics"thecenseireportОценок пока нет
- PCOS: Making Sure Our Votes Count by Ricardo SaludoДокумент9 страницPCOS: Making Sure Our Votes Count by Ricardo SaludothecenseireportОценок пока нет
- First Pages of Issue 23 of TCRДокумент2 страницыFirst Pages of Issue 23 of TCRthecenseireportОценок пока нет
- Race To Save The Lives of Filipino Mothers by Pia RufinoДокумент9 страницRace To Save The Lives of Filipino Mothers by Pia RufinothecenseireportОценок пока нет
- Where Asia Is Dead Wrong On RightsДокумент7 страницWhere Asia Is Dead Wrong On RightsthecenseireportОценок пока нет
- Why Filipinos Don't Save: A Look at Factors That Impact Savings in The Philippines by Marishka CabreraДокумент2 страницыWhy Filipinos Don't Save: A Look at Factors That Impact Savings in The Philippines by Marishka CabrerathecenseireportОценок пока нет
- The Amazing New Gadgets From Apple by Zandro RapadasДокумент5 страницThe Amazing New Gadgets From Apple by Zandro RapadasthecenseireportОценок пока нет
- Growing All The Rice We Need by Joanne MarzanДокумент10 страницGrowing All The Rice We Need by Joanne MarzanthecenseireportОценок пока нет
- Plastic Bags Ban: An Update by Victoria FritzДокумент2 страницыPlastic Bags Ban: An Update by Victoria FritzthecenseireportОценок пока нет
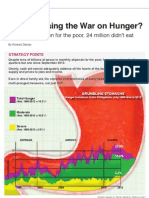
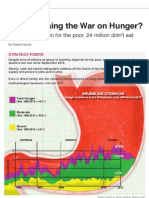
- Full Article - Are We Losing The War On HungerДокумент7 страницFull Article - Are We Losing The War On HungerthecenseireportОценок пока нет
- The World's Last Divorce Debate: Does The Philippines Need A Divorce Law? by Maria Carmina OlivarДокумент2 страницыThe World's Last Divorce Debate: Does The Philippines Need A Divorce Law? by Maria Carmina Olivarthecenseireport100% (1)
- TCR Subscription FormДокумент2 страницыTCR Subscription FormthecenseireportОценок пока нет
- Are We Losing The War On Hunger? by Ricardo SaludoДокумент2 страницыAre We Losing The War On Hunger? by Ricardo SaludothecenseireportОценок пока нет
- The Power and The Pitfalls of Social Media: Is Social Media Facilitating Rapid Change or Just Fostering An Illusion of Activism? by Tanya MarianoДокумент2 страницыThe Power and The Pitfalls of Social Media: Is Social Media Facilitating Rapid Change or Just Fostering An Illusion of Activism? by Tanya MarianothecenseireportОценок пока нет
- Censei Report Subscription FormДокумент1 страницаCensei Report Subscription FormthecenseireportОценок пока нет
- The Yellow House: A Memoir (2019 National Book Award Winner)От EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Рейтинг: 4 из 5 звезд4/5 (98)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeОт EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeРейтинг: 4 из 5 звезд4/5 (5795)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureОт EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureРейтинг: 4.5 из 5 звезд4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryОт EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryРейтинг: 3.5 из 5 звезд3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceОт EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceРейтинг: 4 из 5 звезд4/5 (895)
- Never Split the Difference: Negotiating As If Your Life Depended On ItОт EverandNever Split the Difference: Negotiating As If Your Life Depended On ItРейтинг: 4.5 из 5 звезд4.5/5 (838)
- The Little Book of Hygge: Danish Secrets to Happy LivingОт EverandThe Little Book of Hygge: Danish Secrets to Happy LivingРейтинг: 3.5 из 5 звезд3.5/5 (400)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersОт EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersРейтинг: 4.5 из 5 звезд4.5/5 (345)
- The Unwinding: An Inner History of the New AmericaОт EverandThe Unwinding: An Inner History of the New AmericaРейтинг: 4 из 5 звезд4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnОт EverandTeam of Rivals: The Political Genius of Abraham LincolnРейтинг: 4.5 из 5 звезд4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyОт EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyРейтинг: 3.5 из 5 звезд3.5/5 (2259)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaОт EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaРейтинг: 4.5 из 5 звезд4.5/5 (266)
- The Emperor of All Maladies: A Biography of CancerОт EverandThe Emperor of All Maladies: A Biography of CancerРейтинг: 4.5 из 5 звезд4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreОт EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreРейтинг: 4 из 5 звезд4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)От EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Рейтинг: 4.5 из 5 звезд4.5/5 (121)
- Video Provides A Powerful Way To Help You Prove Your PointДокумент5 страницVideo Provides A Powerful Way To Help You Prove Your PointZacky RareshukОценок пока нет
- Sony - Sources of InnovationДокумент21 страницаSony - Sources of InnovationNayomi Ekanayake0% (1)
- Vulnerability in Image TypeДокумент22 страницыVulnerability in Image Typebabak66Оценок пока нет
- Roblox 199208595Документ8 страницRoblox 199208595MecPlayzОценок пока нет
- Rca L26WD23Документ89 страницRca L26WD23Marcelo ariel RodriguezОценок пока нет
- Ebook As I See It The Autobiography of J Paul GettyДокумент2 страницыEbook As I See It The Autobiography of J Paul GettyMulex Beksa0% (1)
- Chap 1 - Web EssentialsДокумент13 страницChap 1 - Web EssentialsMuskan ShaikhОценок пока нет
- Data Management Integrate CAD Objects: y y y y y y yДокумент1 страницаData Management Integrate CAD Objects: y y y y y y yppОценок пока нет
- Luke Hylton ResumeДокумент3 страницыLuke Hylton Resumeapi-298174719Оценок пока нет
- Evaluating Repetitive Structures in HR ABAP ProgrammingДокумент4 страницыEvaluating Repetitive Structures in HR ABAP Programmingrajeshb4usОценок пока нет
- Multimedia: Content Content FormsДокумент5 страницMultimedia: Content Content FormsBoobalan RОценок пока нет
- QcdereadmeДокумент2 страницыQcdereadmeSebastienGregoireОценок пока нет
- Storage Options 53294 8CH DVR Instruction Manual v.1.7Документ60 страницStorage Options 53294 8CH DVR Instruction Manual v.1.7Fernando Ulises Alvarez RecinosОценок пока нет
- CV Resume Template (ENG) One-PagerДокумент2 страницыCV Resume Template (ENG) One-PagerJevgeni FjodorovОценок пока нет
- Em-Tech ReviewerДокумент2 страницыEm-Tech ReviewerKai SamaОценок пока нет
- 12 - Reset A Windows User Password - RMPrepUSBДокумент7 страниц12 - Reset A Windows User Password - RMPrepUSBVivekananda Ganjigunta NarayanaОценок пока нет
- Microsoft Visual InterdevДокумент324 страницыMicrosoft Visual Interdevapi-3800644100% (1)
- AutoCAD DrawHatchДокумент11 страницAutoCAD DrawHatchBrunoDoljaninОценок пока нет
- EELP Training Module (ENG)Документ12 страницEELP Training Module (ENG)R SidharthОценок пока нет
- My All ActivationДокумент3 страницыMy All ActivationRafael King Jerome MabungaОценок пока нет
- Fndload 4 AmeДокумент11 страницFndload 4 AmeGopinath Suresh100% (1)
- Shashwat Kumar: Education SkillsДокумент1 страницаShashwat Kumar: Education SkillsShashwat KumarОценок пока нет
- Test Case TemplateДокумент2 страницыTest Case TemplatemagillaniОценок пока нет
- History ConsoleДокумент2 страницыHistory ConsoleEduardo GarciaОценок пока нет
- 1B & 1F - Recover Files and Folders From Azure VM Backup - Azure Backup - Microsoft DocsДокумент22 страницы1B & 1F - Recover Files and Folders From Azure VM Backup - Azure Backup - Microsoft DocsJaswinder SinghОценок пока нет
- Gantt-Chart O365 LДокумент8 страницGantt-Chart O365 LAry Daffaa Mayza NaibahoОценок пока нет
- Join The Purcell School' Wi-Fi BroadcastДокумент6 страницJoin The Purcell School' Wi-Fi BroadcastLuca NewmanОценок пока нет
- Using Dsixda Android Kitchen For Rom PorДокумент39 страницUsing Dsixda Android Kitchen For Rom PorMael TrebilladОценок пока нет
- Roehampton University Library Resources: 1. Accessing The Online ResourcesДокумент4 страницыRoehampton University Library Resources: 1. Accessing The Online ResourcesJ_HarrisonОценок пока нет
- 85mm RefДокумент308 страниц85mm RefRomain KoffiОценок пока нет