Академический Документы
Профессиональный Документы
Культура Документы
Monitoring The Security Infrastructure
Загружено:
Pham Duc NhonОригинальное название
Авторское право
Доступные форматы
Поделиться этим документом
Поделиться или встроить документ
Этот документ был вам полезен?
Это неприемлемый материал?
Пожаловаться на этот документАвторское право:
Доступные форматы
Monitoring The Security Infrastructure
Загружено:
Pham Duc NhonАвторское право:
Доступные форматы
Monitoring the Security Infrastructure
Scan for Vulnerabilities
Monitor for Intruders
Set Up a Honeypot
Respond to Security Incidents
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 1
The Hacking Process
Footprinting Scanning Enumerating Attacking
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 2
Ethical Hacking
Ethical hacker
Report on
security flaws
Footprinting Scanning Enumerating Attacking
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 3
Security Utilities
Vulnerability scanning tools
Port scanning tools
Password scanning and cracking tools
Exploits and stress testers
Intrusion detection systems
Network monitors
Network and security administration
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 4
Types of Vulnerability Scans
General vulnerabilities
Application-specific vulnerabilities
Tools for different scan types
General scan
Man-in-the-middle scan
Port scan
Password scan
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 5
Vulnerable Port Ranges
Well-Known Ports: 0 to 1,023
Specific port numbers are most vulnerable to attack
Registered Ports: 1,024 to 49,151
Too system-specific for direct target by attackers
Attackers might scan for open ports in this range
Dynamic or Private Ports: 49,152 to 65,535
Constantly changing, cant be targeted by number
Attackers might scan for open ports in this range
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 6
An IDS
Sensors scan for signs
of attack
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 7
Categories of IDS
Host-based Application-based
Network-based
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 8
Passive and Active IDS
Passive IDS Active IDS
Detects Detects
Logs Logs
Alerts Alerts
Blocks
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 9
IDS Analysis Methods
Signature-based
Activity matches known attacks
Anomaly-based
Compares changes to pre-set parameters
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 10
A Honeypot
Attacker lured to honeypot Detects and logs attack
Insecure honeypot Secure internal
system Blocks access to
system
secure systems
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 11
Types of Honeypots
Software-based Hardware-based
Composite or
network-based
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 12
An IRP
Who verifies
incident
Who is notified
Who determines
response
Who implements response
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 13
Reflective Questions
1. What type of intrusion detection software are you familiar with, and
how have you used it to detect attacks?
2. What do you feel is the most important part of the infrastructure to
monitor? Why?
Copyright 2005 Element K Content LLC. All rights reserved. OV 9 - 14
Вам также может понравиться
- We All Are DevSecOpsДокумент54 страницыWe All Are DevSecOpsqv56xvb2bcОценок пока нет
- Acer Cyber Talk - Materi Chris KuoДокумент17 страницAcer Cyber Talk - Materi Chris KuoAyОценок пока нет
- BRKSEC2004Документ214 страницBRKSEC2004DC FanОценок пока нет
- Check Point Sandblast Zero-Day Protection: September 2015Документ20 страницCheck Point Sandblast Zero-Day Protection: September 2015masterlinh2008Оценок пока нет
- IPS50SL10Документ47 страницIPS50SL10api-3699464Оценок пока нет
- Security Analytics Architecture For APT: Dale Long, Sr. Technology Consultant, RSA SecurityДокумент33 страницыSecurity Analytics Architecture For APT: Dale Long, Sr. Technology Consultant, RSA SecurityDodo winyОценок пока нет
- F5Документ38 страницF5Luis DiazОценок пока нет
- Managing Data, Application, and Host SecurityДокумент56 страницManaging Data, Application, and Host SecurityBob Polo0% (1)
- Slide DeckДокумент122 страницыSlide DeckGolas KingОценок пока нет
- NFV Update: Vienna, February 2018Документ14 страницNFV Update: Vienna, February 2018pritish keneОценок пока нет
- Program SecurityДокумент126 страницProgram SecurityRAJ TAPASEОценок пока нет
- Redinent Brochure V5Документ1 страницаRedinent Brochure V5Ferdinand dela CruzОценок пока нет
- IPS50SL02Документ56 страницIPS50SL02api-3699464100% (1)
- Fireeye Isight Intelligence: Robert Żelazo - Regional Director, Eastern Europe, Fireeye Prague, Sep 14, 2016Документ36 страницFireeye Isight Intelligence: Robert Żelazo - Regional Director, Eastern Europe, Fireeye Prague, Sep 14, 2016Saul Vilca VillenaОценок пока нет
- F5Документ38 страницF5sofien100% (1)
- 6a. Mobile Application SecurityДокумент77 страниц6a. Mobile Application SecurityEvanson KarimiОценок пока нет
- Core SlidesДокумент44 страницыCore SlidesSérgio Locatelli JúniorОценок пока нет
- 02lec - 10 OWASP VulnerabilitiesДокумент40 страниц02lec - 10 OWASP Vulnerabilitiesmanju kakkarОценок пока нет
- Deep Security Container Protection Customer PresentationДокумент42 страницыDeep Security Container Protection Customer PresentationsaurabhbectorОценок пока нет
- 00 - Ethical Hacking and PentestingДокумент27 страниц00 - Ethical Hacking and PentestingSabrine AydiОценок пока нет
- Ibm QradarДокумент39 страницIbm QradarManojОценок пока нет
- 4-1 iOS Applications Hands-OnДокумент107 страниц4-1 iOS Applications Hands-Onshiva kumarОценок пока нет
- 02lec - 10 OWASP Vulnerabilities (1) (6 Files Merged)Документ153 страницы02lec - 10 OWASP Vulnerabilities (1) (6 Files Merged)manju kakkarОценок пока нет
- Security Issues and Challenges in Vehicular Big Data Network (VBDN) : A SurveyДокумент24 страницыSecurity Issues and Challenges in Vehicular Big Data Network (VBDN) : A SurveyDr.Irshad Ahmed SumraОценок пока нет
- HTTP Request SmugglingДокумент4 страницыHTTP Request SmugglingDaleep BaisОценок пока нет
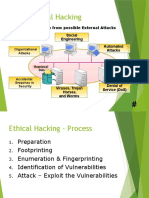
- Why - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksДокумент14 страницWhy - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksfaizaОценок пока нет
- Enclosure PUF Hardwear Io NL 2019Документ64 страницыEnclosure PUF Hardwear Io NL 2019ascascdОценок пока нет
- 做好Web及Api安全以維持營運持續Документ23 страницы做好Web及Api安全以維持營運持續Eric JW HuangОценок пока нет
- Module 26 Penetration TestingДокумент112 страницModule 26 Penetration Testingabel pecinaОценок пока нет
- F5 Web Application Security: Radovan GibalaДокумент73 страницыF5 Web Application Security: Radovan GibalaLuis DiazОценок пока нет
- Awake Basic Training v1.1Документ60 страницAwake Basic Training v1.1Micja PavicОценок пока нет
- Hacking Tips & Tricks: OwaspДокумент15 страницHacking Tips & Tricks: OwaspIT SAAPLОценок пока нет
- Webinar Mastering 4G - 5G Telecom Threat IntelligenceДокумент40 страницWebinar Mastering 4G - 5G Telecom Threat IntelligencecontactОценок пока нет
- Overcoming The Failures of Prevention: Allan Carey Director, Rsa Netwitness Cyber Security Summit July 25, 2011Документ24 страницыOvercoming The Failures of Prevention: Allan Carey Director, Rsa Netwitness Cyber Security Summit July 25, 2011Thu Lang HoangОценок пока нет
- GEMS Phoenix SliceДокумент26 страницGEMS Phoenix SliceSenthil NathanОценок пока нет
- Ips 2Документ45 страницIps 2fshahzad79Оценок пока нет
- AlienVault What Is Log Correlation WhitepaperДокумент16 страницAlienVault What Is Log Correlation WhitepaperKonsantinos PapadopoulosОценок пока нет
- Filippo Cassini - FOS - 6.0Документ25 страницFilippo Cassini - FOS - 6.0habib kamaieОценок пока нет
- Build A Small NetworkДокумент39 страницBuild A Small Networksofyankp mtmОценок пока нет
- F23 CST8804 Lab1 PresentationДокумент20 страницF23 CST8804 Lab1 PresentationReham BakounyОценок пока нет
- Cyber Security VAPT v1.0 Published - CompressedДокумент29 страницCyber Security VAPT v1.0 Published - Compressedasamad54100% (2)
- Port SecurityДокумент12 страницPort SecurityItronix MohaliОценок пока нет
- Risk Assessment & IT Security in ManufacturingДокумент12 страницRisk Assessment & IT Security in Manufacturingpreeti mohantyОценок пока нет
- Chapter 1 - IntroductionДокумент18 страницChapter 1 - IntroductionAníbal CalleОценок пока нет
- (22JUNE) Combined DataheetsДокумент19 страниц(22JUNE) Combined Dataheetsmp3.kurawa12Оценок пока нет
- Slide f5 PDFДокумент65 страницSlide f5 PDFNeikos TenkoseiОценок пока нет
- OpShield From Wurldtech DatasheetДокумент5 страницOpShield From Wurldtech DatasheetitobinhОценок пока нет
- Generation of SQL-injection Free Secure Algorithm To Detect and Prevent SQL-injection AttacksДокумент7 страницGeneration of SQL-injection Free Secure Algorithm To Detect and Prevent SQL-injection AttacksPramono PramonoОценок пока нет
- Pitch Deck - FortiMail and FortiMail CloudДокумент76 страницPitch Deck - FortiMail and FortiMail CloudHector VelazquezОценок пока нет
- F5 Advanced WAF Customer DeckДокумент37 страницF5 Advanced WAF Customer Deckmemo_fdzsОценок пока нет
- NSE Insider - Learn How FortiSIEM's New Security Analytics Can Extend Threat Visibility August 11, 2020Документ35 страницNSE Insider - Learn How FortiSIEM's New Security Analytics Can Extend Threat Visibility August 11, 2020fathanОценок пока нет
- Iot Security: Narudom Roongsiriwong, CisspДокумент42 страницыIot Security: Narudom Roongsiriwong, CisspmeenakshiОценок пока нет
- Traffic Shield: Rainer SingerДокумент30 страницTraffic Shield: Rainer SingerNew ComersОценок пока нет
- Bug Bounty ToolsДокумент1 страницаBug Bounty ToolsxixiyОценок пока нет
- Self-Defending Networks: Cisco Integrated SecurityДокумент26 страницSelf-Defending Networks: Cisco Integrated SecuritySurya NarayanaОценок пока нет
- Chapter11 Security On ZOS SlidesДокумент40 страницChapter11 Security On ZOS SlidesakdenizerdemОценок пока нет
- FortiOS 5.4.1 - How ToДокумент39 страницFortiOS 5.4.1 - How ToAnonymous YLI2wFОценок пока нет
- Cortex XDR Investigating&threat HuntingДокумент26 страницCortex XDR Investigating&threat Huntingdbf75Оценок пока нет
- Managing Public Key Infrastructure (PKI)Документ17 страницManaging Public Key Infrastructure (PKI)Pham Duc NhonОценок пока нет
- Request Secure Connection Web Server With CertificateДокумент1 страницаRequest Secure Connection Web Server With CertificatePham Duc NhonОценок пока нет
- VTN PresentДокумент17 страницVTN PresentPham Duc NhonОценок пока нет
- DataCenter - OverviewДокумент62 страницыDataCenter - OverviewPham Duc Nhon100% (1)
- Introduction To HackingДокумент11 страницIntroduction To HackingFasahalОценок пока нет
- ASTRIDE BasedThreatModelforTelehealthSystemsДокумент16 страницASTRIDE BasedThreatModelforTelehealthSystemsfernando PalloОценок пока нет
- Quiz - Introduction To Cybersecurity - Attempt ReviewДокумент2 страницыQuiz - Introduction To Cybersecurity - Attempt ReviewPonceОценок пока нет
- ResumeДокумент3 страницыResumeVinod Yadav NakkalaОценок пока нет
- Web Security: Prepared By, R.S.Rampriya/CseДокумент46 страницWeb Security: Prepared By, R.S.Rampriya/CseVishalini ChinnathuraiОценок пока нет
- 6 and 7 1Документ14 страниц6 and 7 1Muhammad AliОценок пока нет
- CND Exam Blueprint v2.0: EC-CouncilДокумент6 страницCND Exam Blueprint v2.0: EC-CouncilAditya AdiОценок пока нет
- Internet ThreatsДокумент17 страницInternet Threatskidd psychoОценок пока нет
- EMV IssuerSecurityGuidelinesДокумент82 страницыEMV IssuerSecurityGuidelineshakilicОценок пока нет
- CEH v10 Module 07 - Malware Threats PDFДокумент35 страницCEH v10 Module 07 - Malware Threats PDFLuser AnomousОценок пока нет
- SHA-1 Message Digest AlgorithmДокумент16 страницSHA-1 Message Digest AlgorithmShaheer ArshadОценок пока нет
- Otway Rees ProtocolДокумент4 страницыOtway Rees Protocolhannahade1Оценок пока нет
- Secure Access 6.2 Sample QuestionsДокумент6 страницSecure Access 6.2 Sample QuestionsAlfonso CastroОценок пока нет
- VPN IpsecДокумент2 024 страницыVPN IpsecIftikhar JavedОценок пока нет
- Exhibit B - Security PolicyДокумент4 страницыExhibit B - Security Policyom668704Оценок пока нет
- CEUSA CH 1 Intro To Cyber SecurityДокумент9 страницCEUSA CH 1 Intro To Cyber SecurityEbenezer KobОценок пока нет
- Zero Day AttackДокумент6 страницZero Day AttackWerda FarooqОценок пока нет
- PGP GPG Openssl Frontend Script: Public - Private Key Encryption Using OpensslДокумент5 страницPGP GPG Openssl Frontend Script: Public - Private Key Encryption Using OpensslbedorlehackerОценок пока нет
- Art of Lock PickingДокумент18 страницArt of Lock PickingTruco El Martinez100% (2)
- API Pentesting Mindmap ATTACKДокумент1 страницаAPI Pentesting Mindmap ATTACKBondОценок пока нет
- Digital Resilience Seven Practices in Cybersecurity Digital McKinseyДокумент3 страницыDigital Resilience Seven Practices in Cybersecurity Digital McKinseyJohn evansОценок пока нет
- E-Wallet Security Controls 1.0Документ5 страницE-Wallet Security Controls 1.0SadeОценок пока нет
- Pcissc OverviewДокумент2 страницыPcissc OverviewgcarreongОценок пока нет
- Public-Key Cryptography and Message Authentication: Cryptographicandnetwork Security Chapter-3 MessageauthenticationДокумент27 страницPublic-Key Cryptography and Message Authentication: Cryptographicandnetwork Security Chapter-3 MessageauthenticationZoe KhanОценок пока нет
- Advance Network Security: Assignment No: - 1 Question 1.1:-What Is OSI Security Architecture?Документ7 страницAdvance Network Security: Assignment No: - 1 Question 1.1:-What Is OSI Security Architecture?meharОценок пока нет
- Xtream Iptv CodesДокумент7 страницXtream Iptv CodesFawzi KsarОценок пока нет
- Professional Practices: Free Powerpoint TemplatesДокумент22 страницыProfessional Practices: Free Powerpoint Templateswarda rashidОценок пока нет
- VERNER AssignmentДокумент8 страницVERNER AssignmentFaithОценок пока нет
- CEH v10 Module 06 System HackingДокумент73 страницыCEH v10 Module 06 System HackingSajad ChowdhuryОценок пока нет
- Lesson 7 - Hardware and Software Theft, Vandalism and FailureДокумент3 страницыLesson 7 - Hardware and Software Theft, Vandalism and FailureJambres Delacruz100% (1)